
TeamCity On-Premises Vulnerabilities Threaten Supply Chains (CVE-2024-27198, CVE-2024-27199); Android March 2024 Updates
[Update] March 12, 2024: “BianLian Exploits JetBrains TeamCity Vulnerabilities for Extortion”
[Update] March 8, 2024: “CISA Adds the Critical TeamCity On-Premises Vulnerability (CVE-2024-27198) to the KEV Catalog”
Two new security vulnerabilities have been discovered in the JetBrains TeamCity On-Premises, a widely used CI/CD solution. These vulnerabilities, identified as CVE-2024-27198 and CVE-2024-27199, were initially reported to JetBrains in February 2024 and have recently been made public.
A full technical analysis of these vulnerabilities has been released by researchers, who coordinated with JetBrains during the disclosure process. They emphasize the critical nature of these vulnerabilities, warning that exploitation could grant attackers full control over TeamCity projects, builds, agents, and artifacts. This level of access opens the door to potential supply chain attacks, posing significant risks to affected systems and organizations.
What Are the Latest TeamCity On-Premises Vulnerabilities? Which Versions Are Impacted?
The vulnerabilities, which allow for authentication bypass, are located in the web component of TeamCity and impact all TeamCity On-Premises versions up to 2023.11.3.
The first vulnerability, CVE-2024-27198, poses a critical risk with a CVSS score of 9.8. It arises from an alternative path issue, enabling remote unauthenticated attackers to seize control of the TeamCity server with administrative permissions.
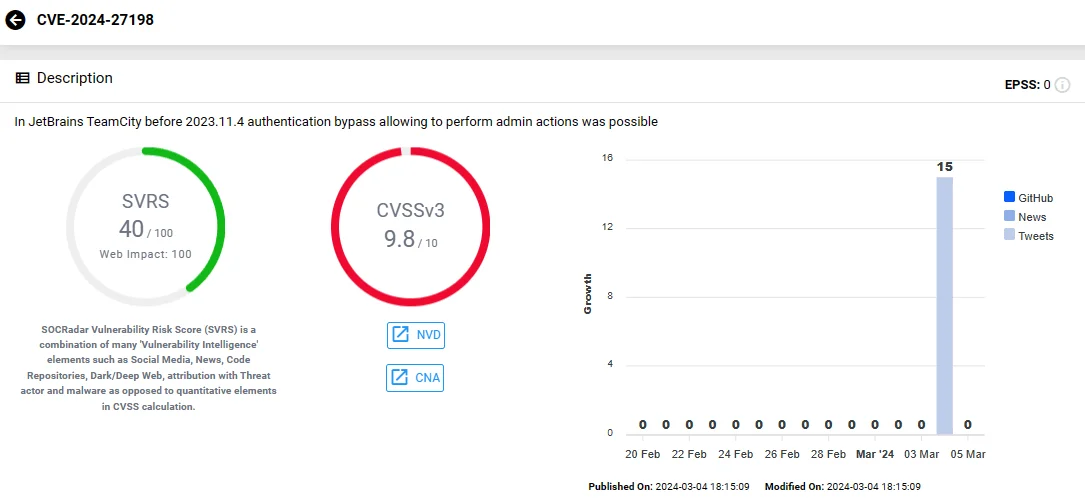
Vulnerability card of CVE-2024-27198 (SOCRadar)
On the other hand, the second vulnerability, CVE-2024-27199, carries a lower severity with a CVSS score of 7.3, attributed to a path traversal.
CVE-2024-27199 allows for limited information disclosure and system modification, as well as unauthorized replacement of an HTTPS certificate on a vulnerable TeamCity server. Thereby, it poses a threat of Denial-of-Service (DoS), as it allows manipulating the HTTPS port number or uploading an unvalidated certificate.
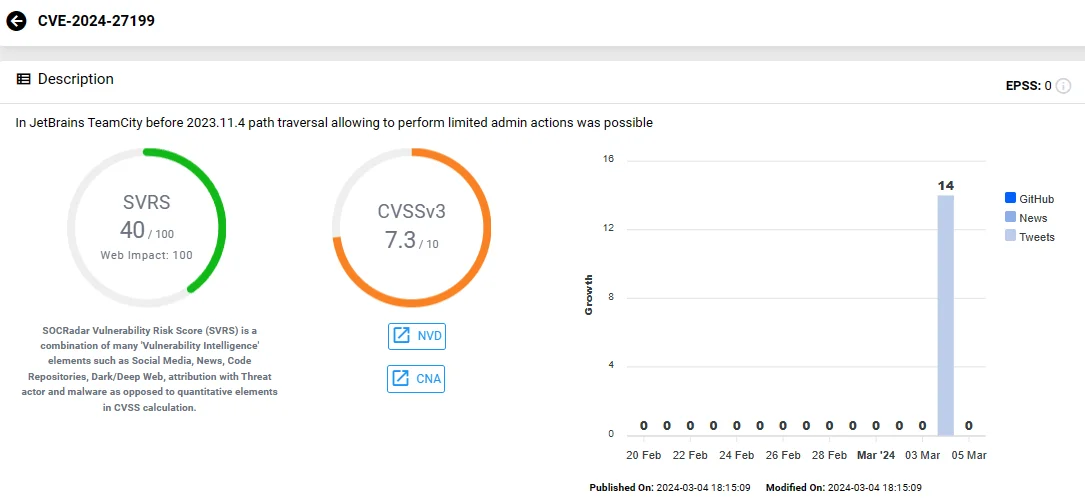
Vulnerability card of CVE-2024-27199 (SOCRadar)
The technical analysis offers a comprehensive breakdown of the vulnerabilities’ exploitation methods, detailing how attackers could create new administrator accounts or generate administrator access tokens to gain full control over the targeted server.
Attackers can leverage this technical guidance to attempt exploitation on unpatched TeamCity On-Premises instances; henceforth administrators must implement security updates promptly.
Apply the Update for TeamCity On-Premises to Mitigate Exploitation Risks
According to a Shodan search, there are presently around 2,300 TeamCity instances accessible on the internet, which may become targeted by threat actors.
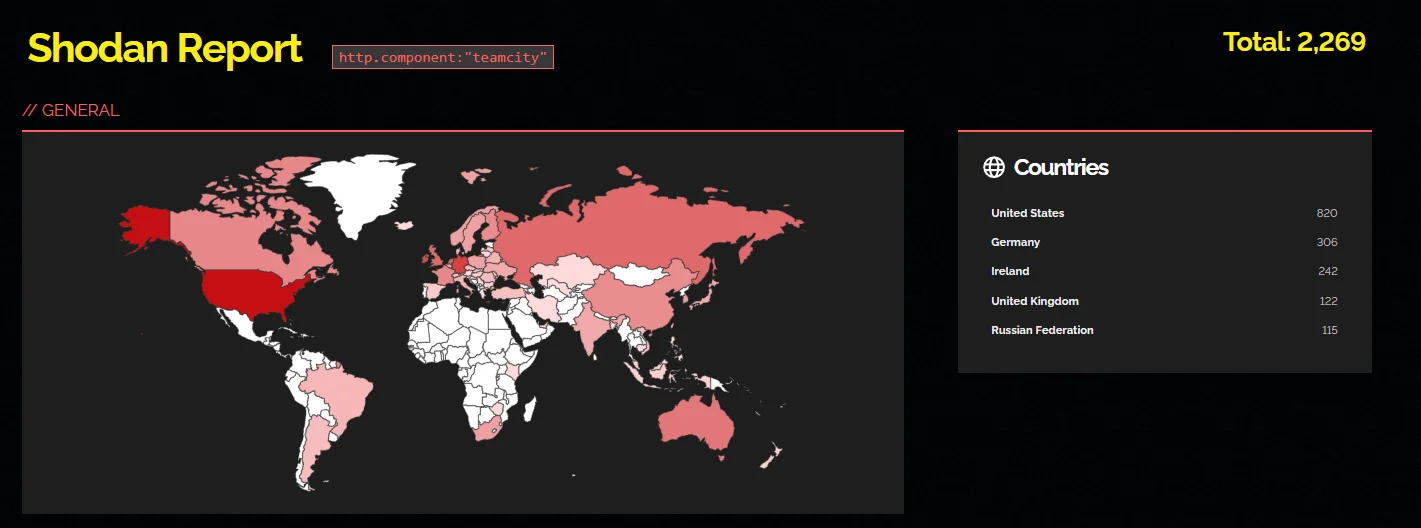
Shodan search for TeamCity
To mitigate the risks, administrators must promptly apply security updates. Upgrading to TeamCity On-Premises version 2023.11.4 addresses CVE-2024-27198 and CVE-2024-27199. Alternatively, a security patch plugin is available for TeamCity 2018.2 and later versions, as well as for TeamCity 2018.1 and older versions.
SOCRadar, with its Attack Surface Management (ASM) module, offers ongoing monitoring of digital assets, promptly issuing alerts whenever a vulnerability surfaces in your organization’s digital environment. Using ASM, you can remain vigilant regarding the latest security vulnerabilities and better prioritize patches for products and software.
SOCRadar’s Attack Surface Management
CISA Adds the Critical TeamCity On-Premises Vulnerability (CVE-2024-27198) to the KEV Catalog
CISA has added the critical CVE-2024-27198 vulnerability in TeamCity, which allows for authentication bypass, to its Known Exploited Vulnerabilities (KEV) Catalog due to confirmation of active exploitation.
The agency emphasizes that organizations should take action to address the most recent JetBrains vulnerabilities, CVE-2024-27198 and CVE-2024-27199.
It is also stated that these vulnerabilities pose significant threats to the federal enterprise. Federal Civilian Executive Branch (FCEB) agencies are expected to patch the critical vulnerability by March 28, 2024.
BianLian Exploits JetBrains TeamCity Vulnerabilities for Extortion
Researchers revealed that BianLian ransomware threat actors have turned their attention to exploiting vulnerabilities in JetBrains TeamCity servers. In an observed incident, threat actors exploited either the recently identified CVE-2024-27198 or the previous auth bypass vulnerability CVE-2023-42793 to deploy a PowerShell implementation of BianLian’s Go backdoor, facilitating extortion schemes.
Notably, since the release of an Avast decryptor for BianLian in January 2023, the group’s primary focus has shifted to extortion activities.
According to researchers’ depictions of the attack chain, the threat actor gained initial access to the victim’s system by abusing a known TeamCity vulnerability, CVE-2024-27198 or CVE-2023-42793. Subsequently, they created new user accounts on the build server and used commands to traverse the network, compromising two build servers.

You can explore BianLian’s operations and tactics through our Threat Actor Profile.
Although it is unclear which vulnerability was specifically exploited by BianLian, researchers point to the threat actor’s shift to Living-Off-the-Land (LOTL) tactics after experiencing difficulties executing their standard Go backdoor.
Instead, they used a PowerShell implementation of their backdoor, which has similar functionality. This obfuscated PowerShell backdoor, web.ps1, establishes a TCP socket for communication with the attackers’ Command and Control (C2) server, allowing further malicious actions.
Indicators of Compromise (IoCs)
The IoCs related to BianLian’s exploitation of TeamCity servers are as follows:
BianLian C2 Infrastructure
- hxxp://136[.]0[.]3[.]71:8001/win64[.]exe
- hxxp://136[.]0[.]3[.]71:8001/64.dll
- 136[.]0[.]3[.]71
Web.ps1 Hashes
- MD5: 977ff17cd1fbaf0753d4d5aa892af7aa
- SHA1: 1af5616fa3b4d2a384000f83e450e4047f04cb57
- SHA256: 7981cdb91b8bad8b0b894cfb71b090fc9773d830fe110bd4dd8f52549152b448
IP addresses linked to malicious authentication attempts
- 88[.]169[.]109[.]111
- 165[.]227[.]151[.]123
- 77[.]75[.]230[.]164
- 164[.]92[.]243[.]252
- 64[.]176[.]229[.]97
- 164[.]92[.]251[.]25
- 126[.]126[.]112[.]143
- 38[.]207[.]148[.]147
- 101[.]53[.]136[.]60
- 188[.]166[.]236[.]38
- 185[.]174[.]137[.]26
March 2024 Android Security Bulletin Lists Three Critical Security Vulnerabilities
Google released the March 2024 Android Security Bulletin on March 4, 2024, which fixes a total of 38 vulnerabilities. The update addresses three critical severity vulnerabilities, as well as a number of high-severity vulnerabilities.
The vulnerabilities affect numerous elements of the Android OS, such as the framework, system, and components from AMLogic, MediaTek, and Qualcomm.
CVE-2024-0039 poses a critical threat to Android Open Source Project (AOSP) versions 12 through 14, enabling attackers to execute Remote Code Execution (RCE) without additional execution privileges.
Similarly, CVE-2024-23717, affecting the same system component, introduces the risk of remote privilege escalation within the same AOSP versions. The two vulnerabilities are known to reside in Bluetooth functionality.
Researcher Marc Newlin announced via Twitter the impending release of detailed information and a Proof-of-Concept (PoC) exploit for the first vulnerability, CVE-2024-23717, at NullCon.
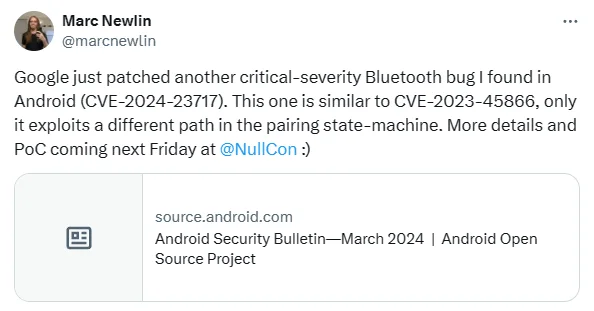
News of the upcoming PoC for CVE-2024-23717 (X)
Furthermore, Qualcomm’s closed-source components reveal another critical vulnerability, CVE-2023-28578, with a CVSS score of 9.3. This flaw, initially disclosed in Qualcomm’s March 2024 bulletin, and subsequently in Android’s bulletin, originates from improper input validation, leading to memory corruption in Core Services when executing commands to remove event listeners.
The Android security bulletin underscores the importance of updating to security patch levels of 2024-03-05 or later, which address all newly disclosed vulnerabilities. Users are urged to check their device’s security patch level and apply updates to avoid exploitation.
For a full list of vulnerabilities addressed in the latest Android update, refer to the official bulletin.
SOCRadar’s Vulnerability Intelligence aids organizations in effective vulnerability management. On the SOCRadar platform’s Vulnerability Intelligence page, you can search for vulnerabilities and access detailed information about them, including the availability of exploits and their full lifecycle with updates.
SOCRadar Vulnerability Intelligence Module
Sign up for a Freemium to test the full capabilities of SOCRadar XTI in improving your vulnerability management strategy:



































