
High-Severity Vulnerability in Popular WordPress Plugin ‘File Manager’ Could Lead to CSRF Attacks (CVE-2024-1538)
A high-severity security vulnerability, identified as CVE-2024-1538, has recently come to light in the widely used File Manager plugin for WordPress. Its exploitation poses a significant risk of Cross-Site Request Forgery (CSRF) attacks.
The File Manager plugin, with a remarkable 1 million active installations, provides website administrators with several capabilities for handling files and folders.
File Manager Plugin page (WordPress.org)
As described in its WordPress page, the File Manager plugin allows users to edit, delete, upload, download, compress, copy, and paste files and folders through the WordPress dashboard, without the need for FTP access.
What Is the CVE-2024-1538 Vulnerability About? Which Versions of File Manager Are Affected?
The CVE-2024-1538 vulnerability carries a high CVSS score of 8.8 and stems from inadequate nonce validation within the plugin’s wp_file_manager page, particularly when handling the ‘lang’ parameter.
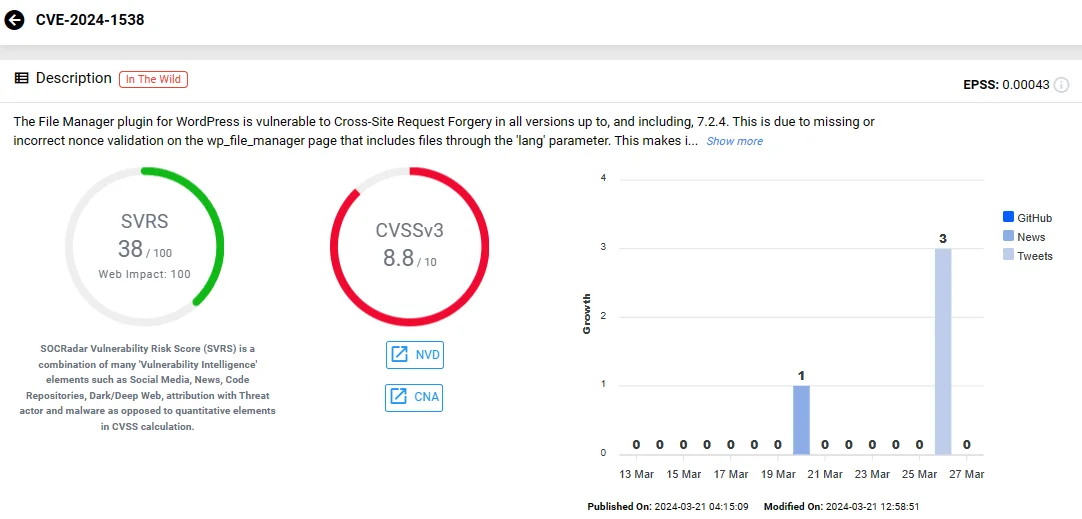
Vulnerability card of CVE-2024-1538 (SOCRadar Vulnerability Intelligence)
By exploiting this security vulnerability, attackers can inject local JavaScript files into the webpage. If successful in deceiving the site admin into clicking their malicious link, attackers can achieve RCE (Remote Code Execution).
The consequences of a successful attack include potential malware infection, data theft, and website compromise, posing significant risks to site integrity and visitors’ security.
CVE-2024-1538 impacts all versions of the File Manager plugin up to, and including, 7.2.4.
You can obtain thorough information about identified vulnerabilities, such as updates, exploits, and lifecycle data, with SOCRadar’s Vulnerability Intelligence.
The module makes it easier for organizations to proactively monitor and prioritize vulnerabilities, provides alerts when attackers target them and helps minimize the attack surface.
Follow CVE trends via SOCRadar’s Vulnerability Intelligence
Has CVE-2024-1538 Been Exploited?
While no active exploits have been discovered at the time of writing, it is important to recognize that threat actors frequently share exploits for WordPress vulnerabilities on the dark web.
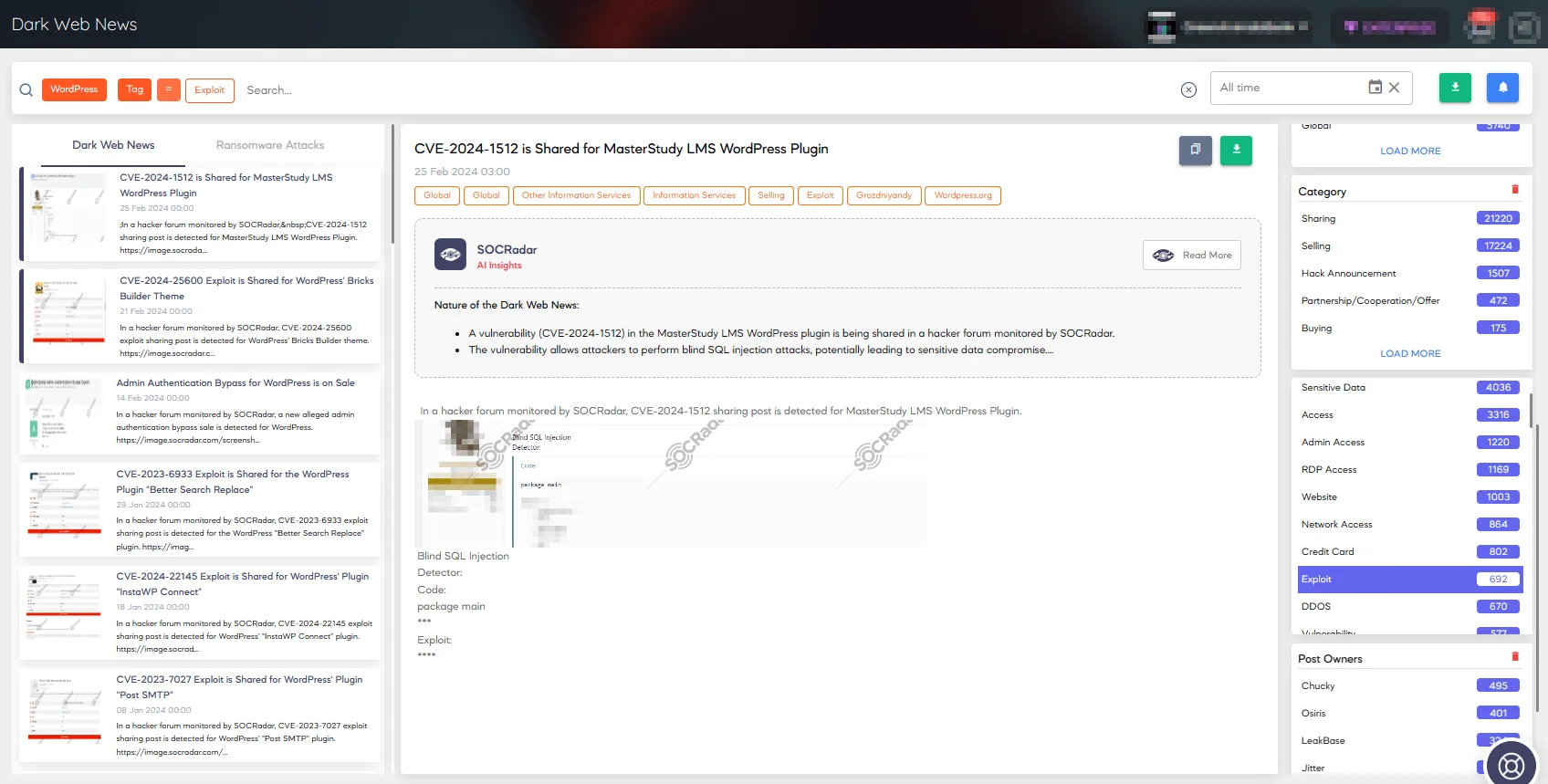
WordPress exploits shared across the dark web (SOCRadar Dark Web News)
Given the widespread use of the File Manager plugin, it is best to remain vigilant and anticipate possible exploitation of the CVE-2024-1538 vulnerability in the near future.
Is There a Patch Available for CVE-2024-1538 in File Manager WordPress Plugin?
To remediate the vulnerability, authors of the plugin released version 7.2.5.
It is critical that users of the File Manager plugin update to version 7.2.5 or later as soon as possible to enhance their site’s and visitors’ security.
How Can You Be Safe From Vulnerabilities in WordPress Plugins?
Some of the best practices for mitigating CVE-2024-1538 and similar WordPress and plugin vulnerabilities include:
- Keep WordPress Core, plugins, and themes updated.
- Use a Web Application Firewall (WAF) to filter and monitor HTTP traffic to your WordPress site, protecting it from common web-based attacks like SQL injection and Cross-site Scripting (XSS).
- Regularly back up your WordPress site, including files and databases, to quickly restore it in case of a security incident or data loss.
Furthermore, with SOCRadar’s Attack Surface Management, you can retain total control over your digital presence while also acquiring invaluable insights to outpace threat actors.
The platform sends alerts for emerging security concerns within your organization, which promotes better patch management and a stronger security posture.
Digital Footprint page, SOCRadar Attack Surface Management module



































