
Microsoft’s April 2024 Patch Tuesday, 149 Vulnerabilities Patched, including 2 Zero-Day Vulnerabilities
Microsoft’s April 2024 Patch Tuesday was a substantial release addressing a total of 149 security vulnerabilities across various products, including 2 Zero-Day vulnerabilities. Among these, 67 were classified as remote code execution (RCE) vulnerabilities, highlighting the critical nature of the patches. This marks Microsoft’s most extensive release of the year and its most significant since at least 2017.
Overview of the Vulnerabilities
Patch Tuesday saw the resolution of three critical vulnerabilities, alongside more than sixty-seven remote code execution bugs. A significant portion of these RCE flaws is concentrated within Microsoft SQL drivers, indicating a potential common underlying issue. Out of the patches unveiled today, just three hold a Critical rating, while 142 are classified as Important, and two fall under Moderate severity. Furthermore, this month’s Patch Tuesday also addressed two zero-day vulnerabilities that were actively being exploited in malware attacks.
Critical Vulnerabilities
While the overall count of security flaws was significant, what stood out were the three critical vulnerabilities addressed in this release. These critical flaws, if exploited, could potentially lead to severe consequences, emphasizing the importance of timely patching and system updates. All of critical vulnerabilities were in Microsoft Defender for IoT Remote Code Execution Vulnerability:
Microsoft Defender for IoT, formerly known as Azure Defender for IoT, which is responsible for monitoring IoT devices for security vulnerabilities. These mentioned vulnerabilities in this tool are categorized as remote-code execution vulnerabilities.
Among these vulnerabilities, CVE-2024-29053 stands out as particularly dangerous with an 8.8 CVSS rating. According to Microsoft’s CVE notes, “Any authenticated attacker could exploit this vulnerability without requiring admin or other elevated privileges.”
Additionally, Microsoft addressed three other flaws in Microsoft Defender for IoT this month: CVE-2024-21324, CVE-2024-29054, and CVE-2024-29055, all of which are elevation-of-privilege vulnerabilities rated as important.
Azure Kubernetes Service Confidential Containers (AKSCC) Vulnerabilities:
CVE-2024-29990 is an Elevation of Privilege (EoP) vulnerability in AKSCC with a CVSSv3 score of 9. It allows attackers to steal credentials and affect resources outside AKSCC’s security scope.
This vulnerability marks the third consecutive month where AKSCC flaws have been patched as part of Patch Tuesday. The previous two months addressed CVE-2024-21400 and CVE-2024-21376, both with CVSSv3 scores of 9.
Microsoft ODBC Driver, WDAC OLE DB Driver, and SQL Server OLE DB Driver Vulnerabilities:
This month’s release includes 41 CVEs affecting various drivers, mostly with CVSSv3 scores of 8.8. While the Microsoft Exploitability Index rates them as “Exploitation Less Likely,” they cover remote code execution (RCE) vulnerabilities in SQL Server, ODBC Driver, WDAC OLE DB Driver, and SQL Server OLE DB Driver.
Secure Boot Vulnerabilities:
Microsoft addressed 24 CVEs related to Secure Boot security feature bypasses in Windows. These vulnerabilities range in severity, with CVSSv3 scores from 4.1 to 8.0. Exploiting these flaws typically requires physical access or local administrator privileges on the target device.
This batch of 24 CVEs is the first significant release of Secure Boot vulnerabilities since May 2023, highlighting the importance of maintaining security in boot processes.
Zero-Day Vulnerabilities
The first vulnerability, known as CVE-2024-26234 and categorized as a proxy driver spoofing vulnerability, was discovered in a malicious driver signed with a valid Microsoft Hardware Publisher Certificate.
CVE-2024-26234 which is a late-breaking zero-day spoofing vulnerability related to Windows Proxy Driver. Initially, the advisory did not mention any awareness of exploitation or public disclosure. However, Microsoft later updated the advisory to acknowledge both aspects.
According to BleepingComputer’s post, this driver, flagged by researchers in December 2023 and reported, was named “Catalog Authentication Client Service” under “Catalog Thales,” appearing to impersonate Thales Group. However, subsequent investigation revealed its association with LaiXi Android Screen Mirroring marketing software, leading to suspicions of a malicious backdoor.
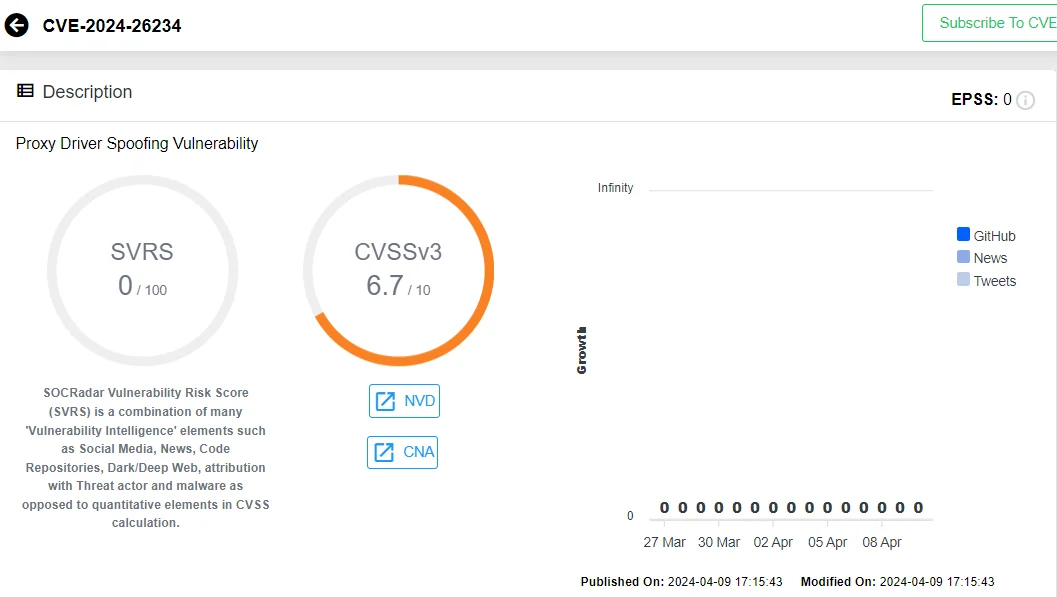
CVE-2024-26234 in SOCRadar Vulnerability Intelligence
Despite the inability to verify the authenticity of LaiXi software, researchers expressed confidence in identifying it as a malicious backdoor and promptly reported the findings to the Microsoft Security Response Center, leading to the addition of relevant files to the revocation list.
On the same day, Microsoft addressed another zero-day vulnerability, CVE-2024-29988, described as a SmartScreen prompt security feature bypass vulnerability linked to a protection mechanism failure. This flaw, a bypass for CVE-2024-21412, was flagged as actively used in attacks by Zero Day Initiative, targeting Windows systems to deploy malware like DarkMe RAT after evading detection mechanisms.
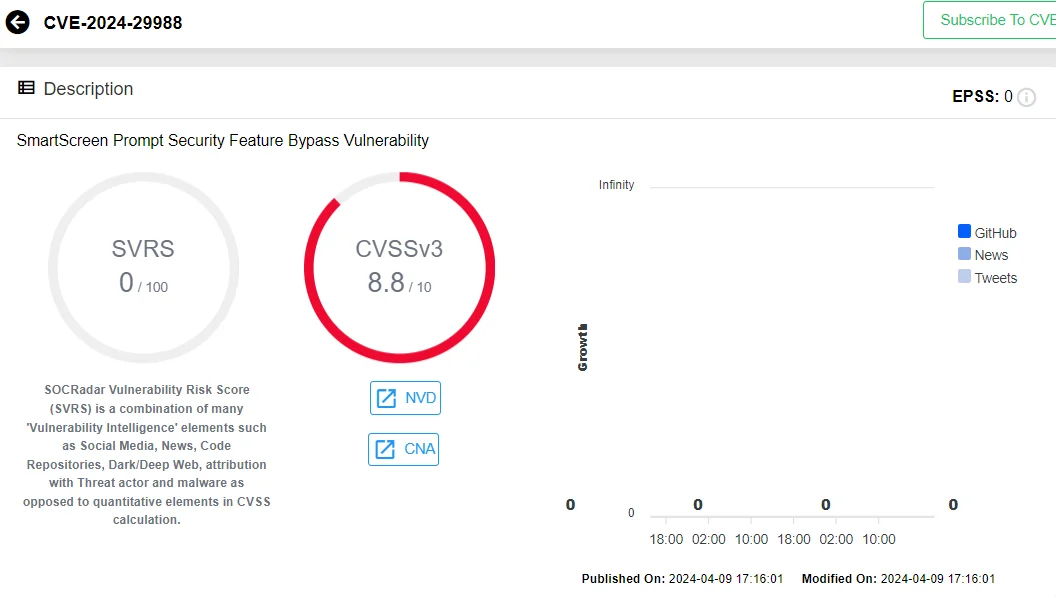
CVE-2024-29988 in SOCRadar Vulnerability Intelligence
The Water Hydra hacking group, financially motivated, leveraged CVE-2024-29988 along with CVE-2024-21412 in spear phishing attacks on forex and stock trading forums, deploying the DarkMe RAT. CVE-2024-21412 itself bypassed another Defender SmartScreen vulnerability patched in November 2023 (CVE-2023-36025), exploited earlier as a zero-day to distribute Phemedrone malware.
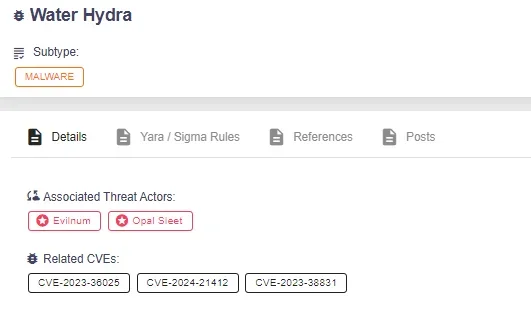
You can find details about Water Hydra and many other threats, including the vulnerabilities they target, on SOCRadar’s Threat Actor/Malware page.
Vulnerability Defense with SOCRadar XTI
SOCRadar XTI provides a range of modules that are instrumental in addressing security challenges and safeguarding system integrity and brand reputation effectively. The External Attack Surface Management module empowers organizations with tools to swiftly detect, evaluate, and mitigate vulnerabilities. Concurrently, the Vulnerability Intelligence feature enhances security protocols by consistently monitoring security vulnerabilities.
Through the Vulnerability Intelligence module, users can search for vulnerabilities, access comprehensive details about them, and monitor associated activities like exploitation and hacker behaviors.
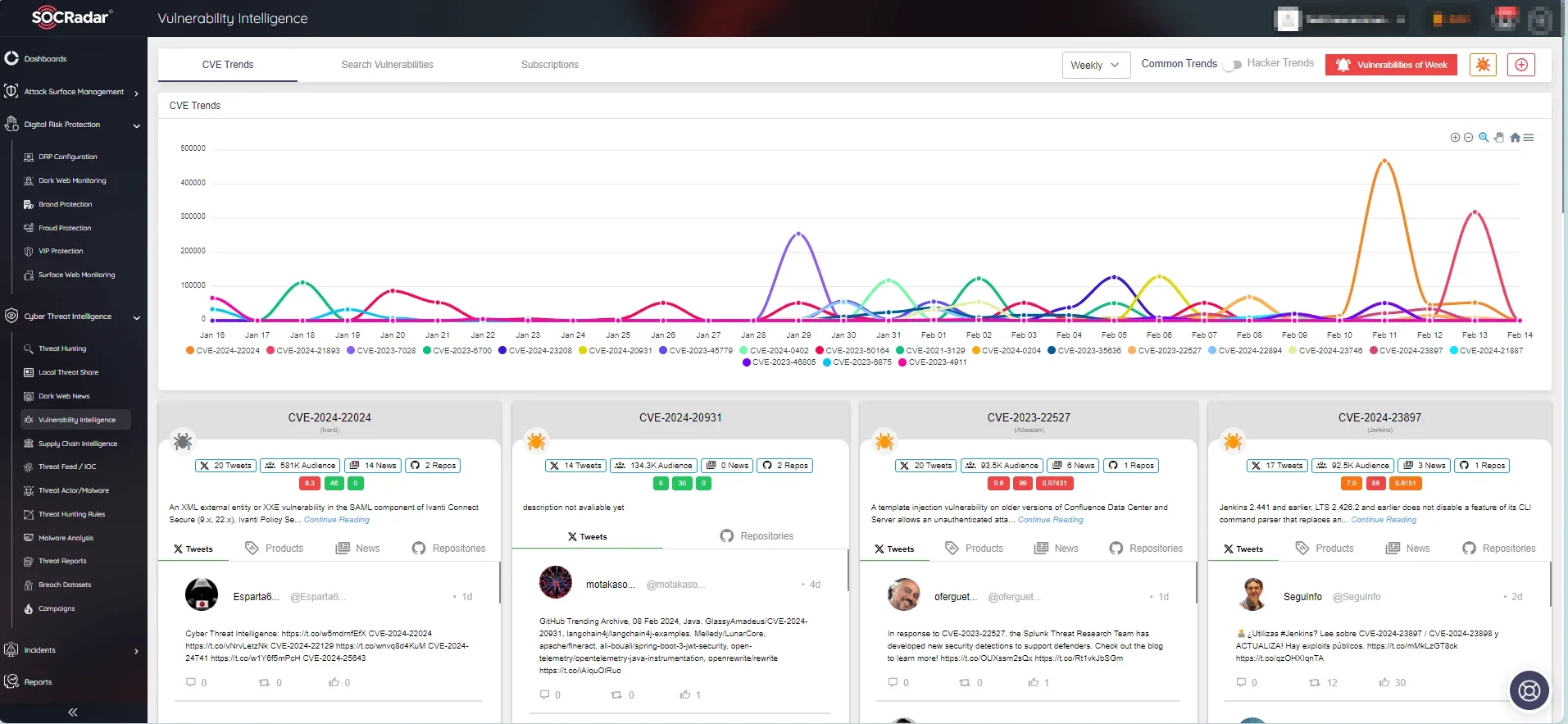
SOCRadar Vulnerability Intelligence


































