
Major Cyber Attacks in Review: August 2024
August 2024 witnessed a series of impactful cyber attacks targeting industries from airport services in Canada to key financial institutions in the U.S. This month’s notable incidents exposed the personal data of millions, revealing significant vulnerabilities across various sectors.
High-profile breaches by a certain threat group, RansomHub, at Park’N Fly, Patelco Credit Union, and Halliburton highlighted the growing sophistication of ransomware attacks, affecting over a million individuals. Large corporations like Toyota also faced disruptions that challenged their operations and security measures.
Additionally, this month marked the conclusion of the SEC’s investigations into the MOVEit Transfer issues at Progress Software, which had previously led to widespread data breaches.
Park’N Fly Suffered Data Breach Affecting 1 Million Customers
Park’N Fly, Canada’s largest off-airport parking provider, fell victim to a data breach orchestrated by the ransomware group RansomHub. This breach, reported in late August 2024, compromised sensitive customer information from its operations.
The breach specifically exposed the contact details, Aeroplan numbers, and CAA numbers of approximately 1 million customers. Fortunately, no financial data or payment card information was accessed.
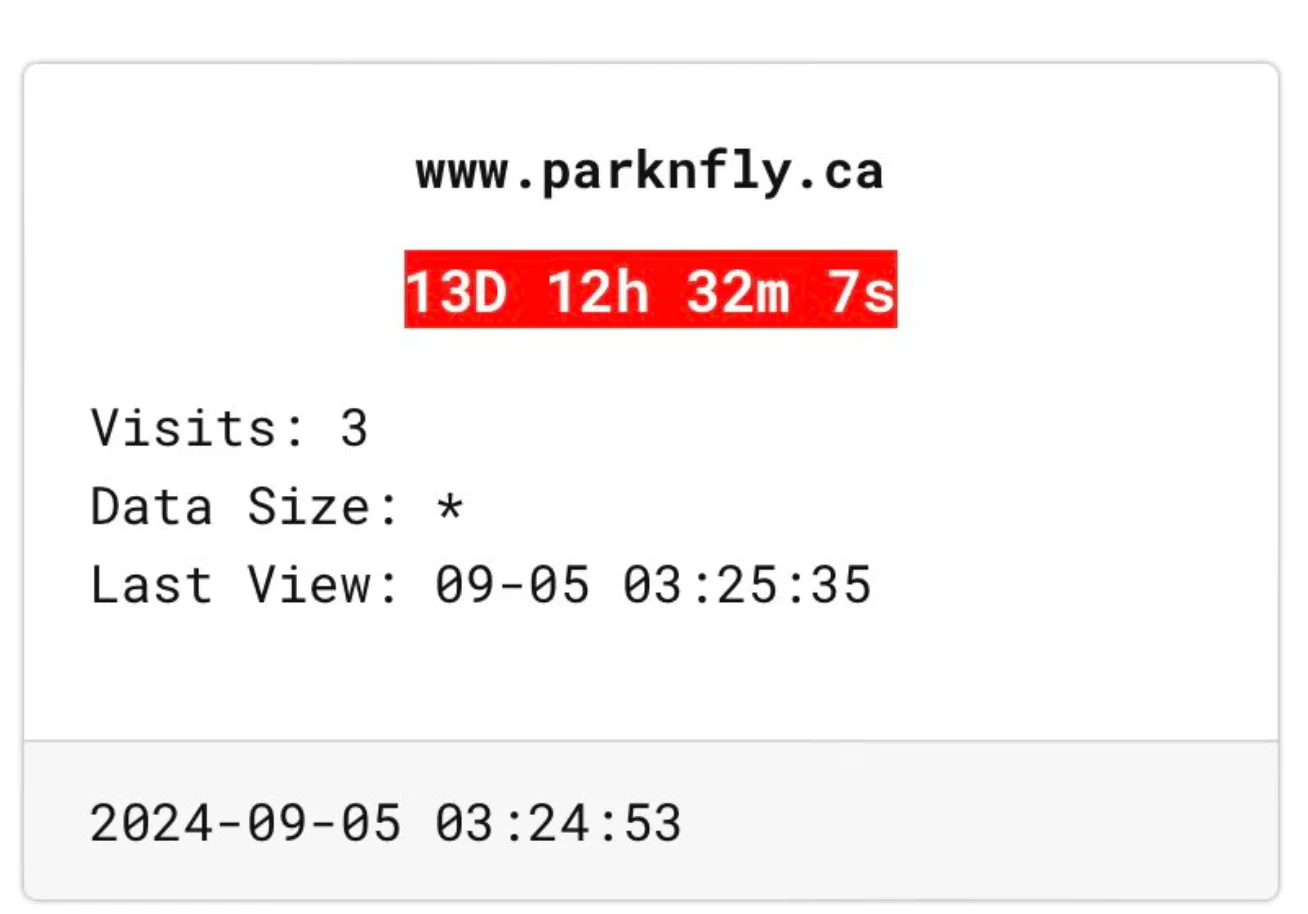
RansomHub listing for Park’N Fly
The threat group alleged that the negotiations with the company failed, leading them to attempt selling the stolen data to third parties. Park’N Fly managed to restore the affected systems within five days, but the exact method used by the attackers to penetrate Park’N Fly’s network remains unclear.
BlackSuit Ransomware Compromised Data of Nearly 1 Million Young Consulting Customers
Young Consulting, a prominent US software provider specializing in employer stop-loss insurance, confirmed that the BlackSuit ransomware group compromised the personal data of nearly a million customers.
Occurring in April, the breach involved unauthorized access and subsequent data encryption by the attackers. The compromised data included full names, Social Security numbers (SSNs), birth dates, and insurance claim details of clients, notably affecting Blue Shield of California subscribers.
Moreover, BlackSuit claims to have leaked extensive corporate data on its extortion site, including contracts, financial records, and personal employee information, heightening the risk of further illicit use of the exposed information.

Learn more about the threat actor: BlackSuit Dark Web Profile
Young Consulting urged vigilance against phishing and fraud, as the leaked data’s full extent remains uncertain and could lead to additional security challenges for those impacted.
Patelco Credit Union Responds to Major Data Breach Impacting Over 726,000 Individuals
Patelco Credit Union, a key financial institution serving Northern California, has reported a significant data breach after falling victim to a ransomware attack by the RansomHub group. This breach, which came to light following unauthorized access detected on June 29, compromised sensitive personal information across its member base.
The attackers had infiltrated Patelco’s systems from May 23 to June 29, accessing databases that contained names, Social Security numbers, driver’s license details, birth dates, and email addresses. Although not all data elements were affected for each individual, the breach’s scope is extensive, impacting an estimated 726,000 customers and employees – far exceeding initial estimates of 450,000.
In response, Patelco has engaged with the Maine Attorney General’s Office and has begun offering two years of free identity protection services to those affected. Moreover, California’s Department of Financial Protection and Innovation has issued a consumer alert due to the incident’s severity.
Ultimately, RansomHub listed Patelco’s data for auction on their website, with samples showcasing the depth of information available. This development underscores the critical need for vigilance among all affected parties to mitigate potential fraud and identity theft risks.
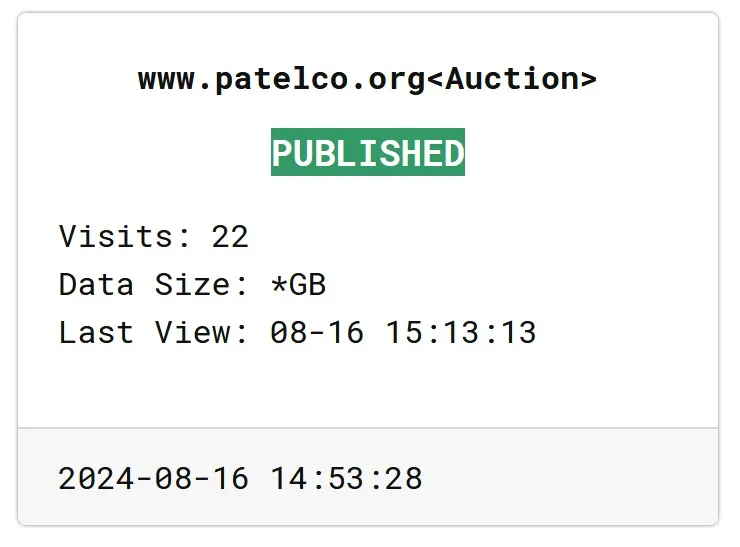
RansomHub’s listing for Patelco
Halliburton Cyber Attack by RansomHub Disrupted Operations
Halliburton, a global leader in energy and oil services, reported a significant cyber attack that led to the shutdown of key systems, as detailed in a filing with the U.S. Securities and Exchange Commission (SEC).

SEC filing of Halliburton, see the full version here
The incident, identified in late August 2024, involved unauthorized access to the company’s IT systems, prompting a swift cybersecurity response.
Upon discovery, Halliburton shut down affected systems to mitigate the breach and initiated an in-depth investigation with external advisors, while law enforcement was notified to assist.
The breach impacted essential business functions, preventing customers from generating invoices or processing purchase orders. Halliburton is diligently working towards system restoration and evaluating the attack’s broader implications on its operations.
The RansomHub ransomware gang claimed responsibility for this attack as well. This breach is part of a larger pattern of RansomHub activities targeting the US critical infrastructure, with over 200 entities affected since February 2024.
Find out more about cyber threat actors through SOCRadar’s Threat Actor Intelligence module. Try the free version of the module on SOCRadar LABS.
Toyota Addresses Alleged Data Breach Involving Third-Party
Toyota responded to reports of a significant data breach involving 240GB of stolen data, clarifying that the incident did not directly affect its systems but rather a third-party associated with the automotive giant.
This Toyota breach was confirmed in August 2024, sparking concerns over the potential exposure of sensitive information. Details of the incident remain somewhat vague, with Toyota stating that the situation involves limited scope and is not indicative of a broader system-wide issue. Contrary to initial reports, Toyota Motor North America emphasized that its own systems were not breached or compromised, addressing misconceptions about the direct involvement of its network.
ZeroSevenGroup, the entity claiming responsibility for the breach, alleged that the stolen data included comprehensive details about Toyota’s employees, customers, contracts, and financial records. They also claimed to have accessed network infrastructure information using the ADRecon tool, suggesting that the breach’s impact could be extensive.
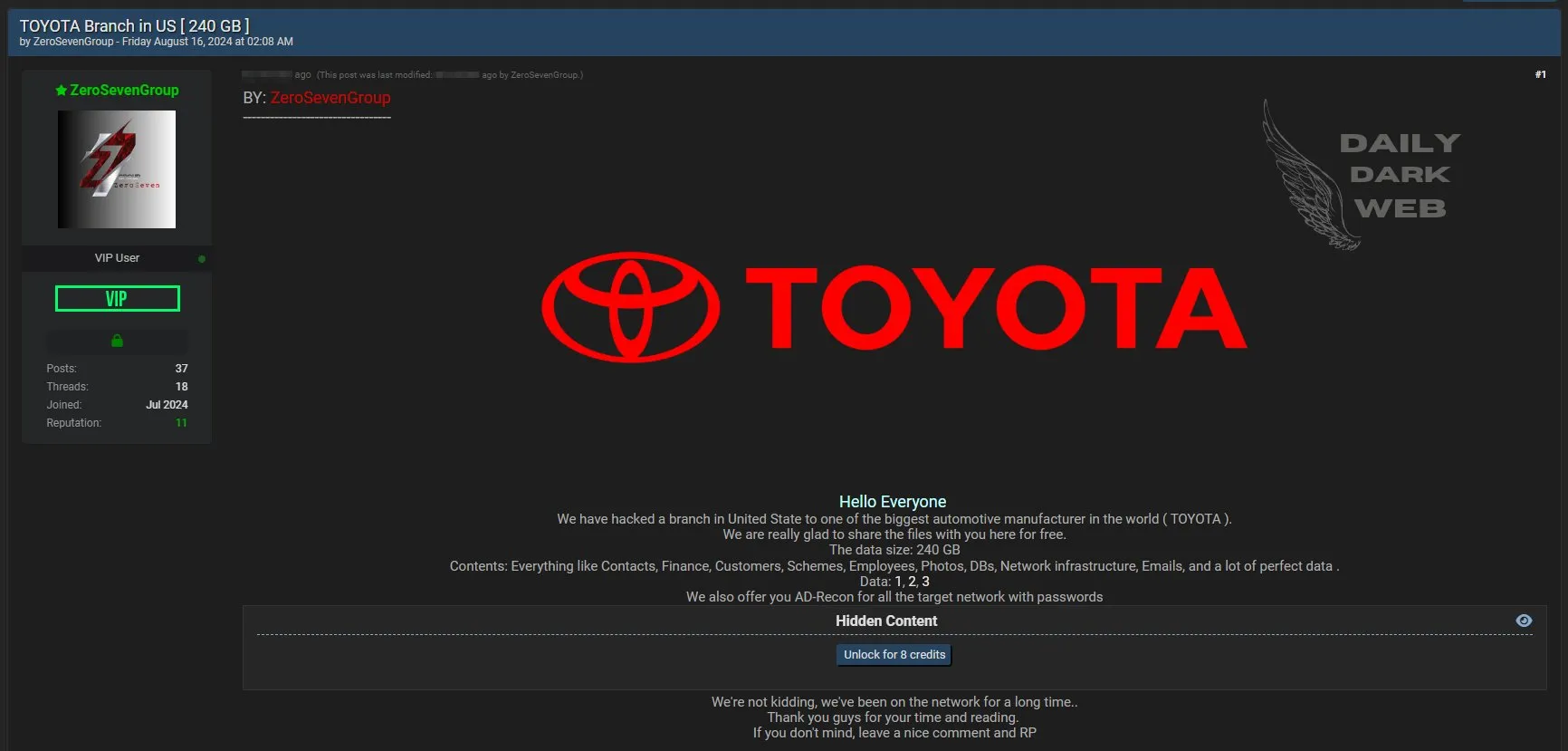
Threat actor’s post about the Toyota breach
National Public Data Breach Exposed Millions of Social Security Numbers
National Public Data (NPD) reported a severe data breach that resulted in the unauthorized disclosure of millions of Social Security numbers (SSNs) and other personal details. This breach, initially stemming from a hacking attempt in late 2023, led to significant data leaks in both April and August 2024.
The exposed data encompassed a wide range of personal information, including names, email addresses, phone numbers, SSNs, and mailing addresses. The leakage of such sensitive information has heightened risks of identity theft, particularly as partial copies of the database started circulating on the Dark Web.
For more detailed guidance on protecting your identity, resources such as the IRS Identity Theft Central are available here. Additionally, SOCRadar offers Advanced Dark Web Monitoring services to help track ongoing threats and vulnerabilities related to your data.
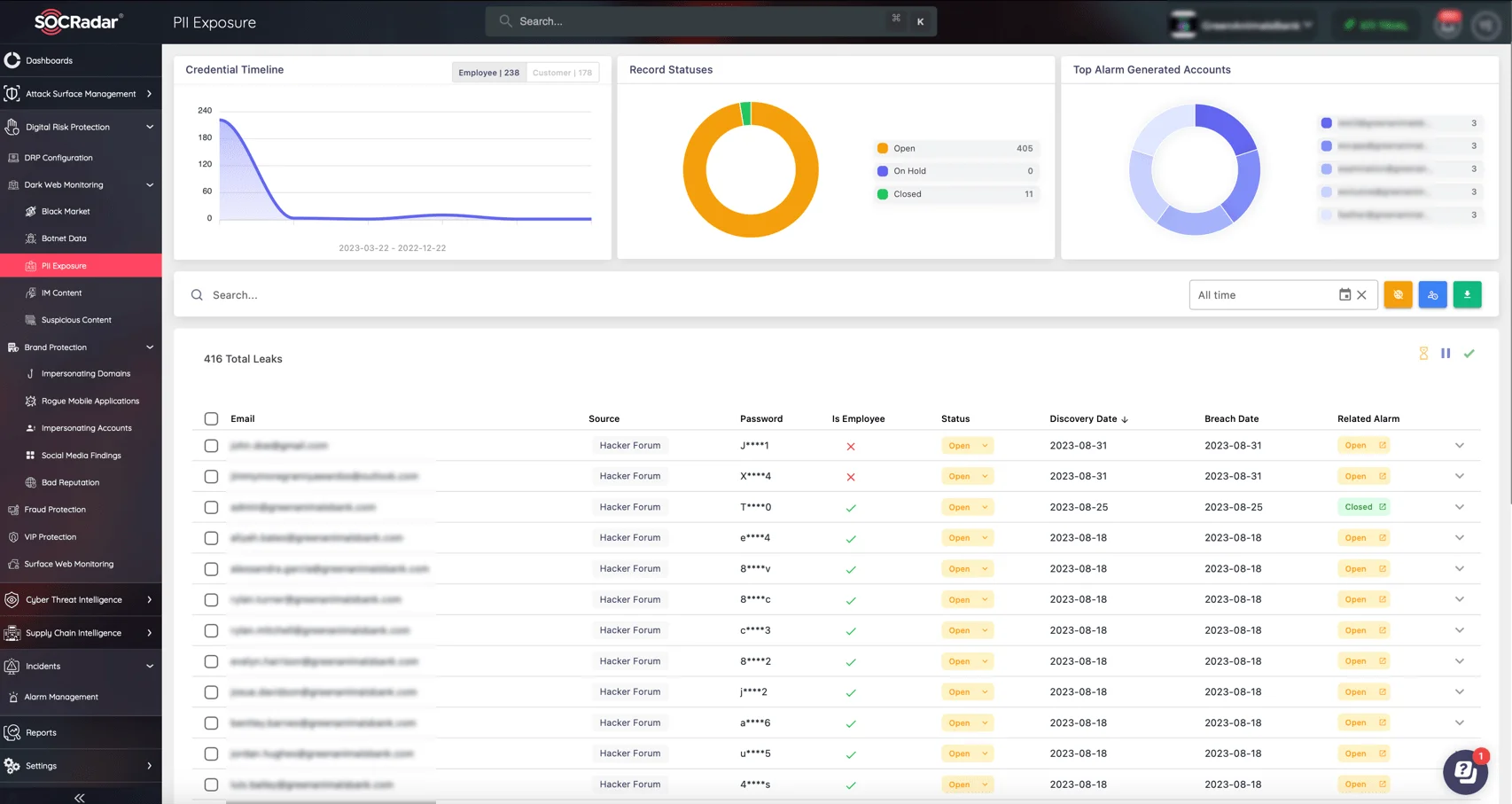
Monitor for PII exposure on the Dark Web (SOCRadar Dark Web Monitoring)
SEC Concludes Inquiry into Progress Software’s MOVEit Transfer Incident
The U.S. Securities and Exchange Commission (SEC) has completed its investigation into Progress Software’s handling of a zero-day vulnerability in its MOVEit Transfer software. This flaw was exploited to launch significant data breaches, impacting over 95 million individuals and 2,770 companies globally.
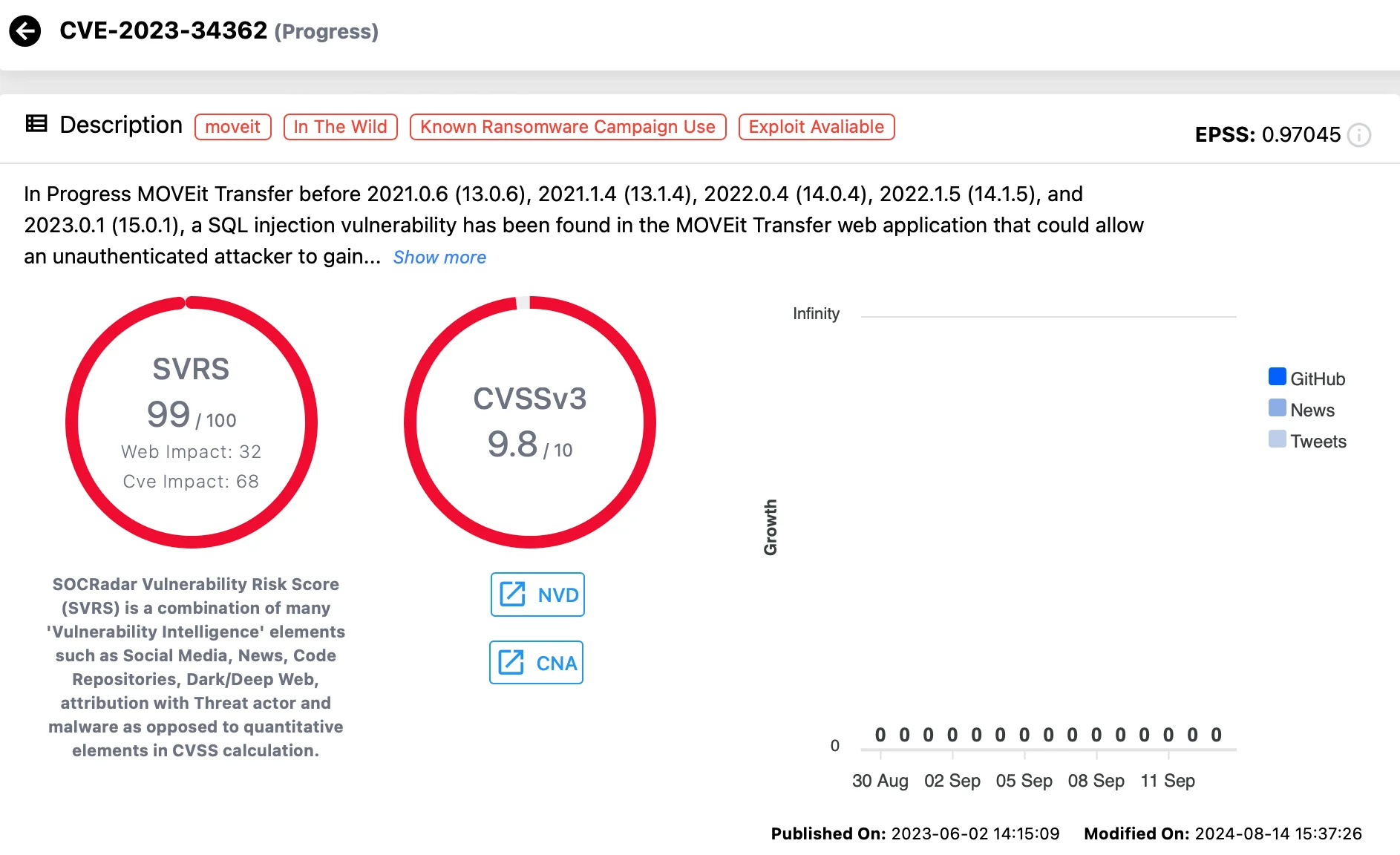
Progress MOVEit Transfer SQL Injection Vulnerability: CVE-2023-34362 (SOCRadar Vulnerability Intelligence)
Despite the Clop ransomware gang leveraging this vulnerability to secure ransom payments estimated between $75-100 million, the SEC has decided not to take any enforcement action against Progress Software.
Still, Progress Software continues to face considerable legal challenges. Numerous class-action lawsuits have been centralized in Massachusetts federal courts, highlighting the widespread repercussions of the breach across diverse sectors such as government, finance, healthcare, aviation, and education.
Keytronic Faced Significant Operational Disruption Following Black Basta Ransomware Attack
Manufacturing firm Keytronic disclosed a data breach involving an alleged leak of 530 GB of sensitive data by the Black Basta ransomware group.
The breach, which came to light in June after the group claimed to have stolen a vast array of data including HR, finance, engineering documents, and corporate data, forced Keytronic to halt operations in the U.S. and Mexico for two weeks.
The incident was initially detected on May 6, 2024, prompting an immediate investigation with cybersecurity experts and notification to law enforcement.
According to a form 8-K/A filing with the SEC, the breach impacted various business applications and restricted access to crucial financial and operational reporting systems.

SEC filing of Keytronic, see the full version here
Financial repercussions from the attack have been severe, with Keytronic reporting over $17 million in losses due to additional expenses and lost revenue during the fourth quarter of 2024.





































