
Critical Vulnerability in Ivanti Cloud Services Appliance (CSA) Exploited in Attacks: CVE-2024-8963
Ivanti has disclosed a critical vulnerability identified as CVE-2024-8963, affecting its Cloud Services Appliance (CSA), which is already being exploited in targeted attacks.
Ivanti Cloud Services Appliance (CSA) serves as a gateway for enterprise users to securely access internal network resources, making this flaw particularly concerning. According to Ivanti’s advisory, this vulnerability was incidentally addressed in the CSA 4.6 Patch 519, which was released on September 10, 2024.
In response to the active exploitation, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added CVE-2024-8963 to its Known Exploited Vulnerabilities (KEV) Catalog, highlighting the urgency of applying the available patch.
What is CVE-2024-8963?
CVE-2024-8963 is a critical path traversal vulnerability in Ivanti’s Cloud Services Appliance (CSA) that allows remote, unauthenticated attackers to access restricted functionality on vulnerable systems.
Successful exploitation of this vulnerability could enable attackers to bypass administrative controls and gain unauthorized access.
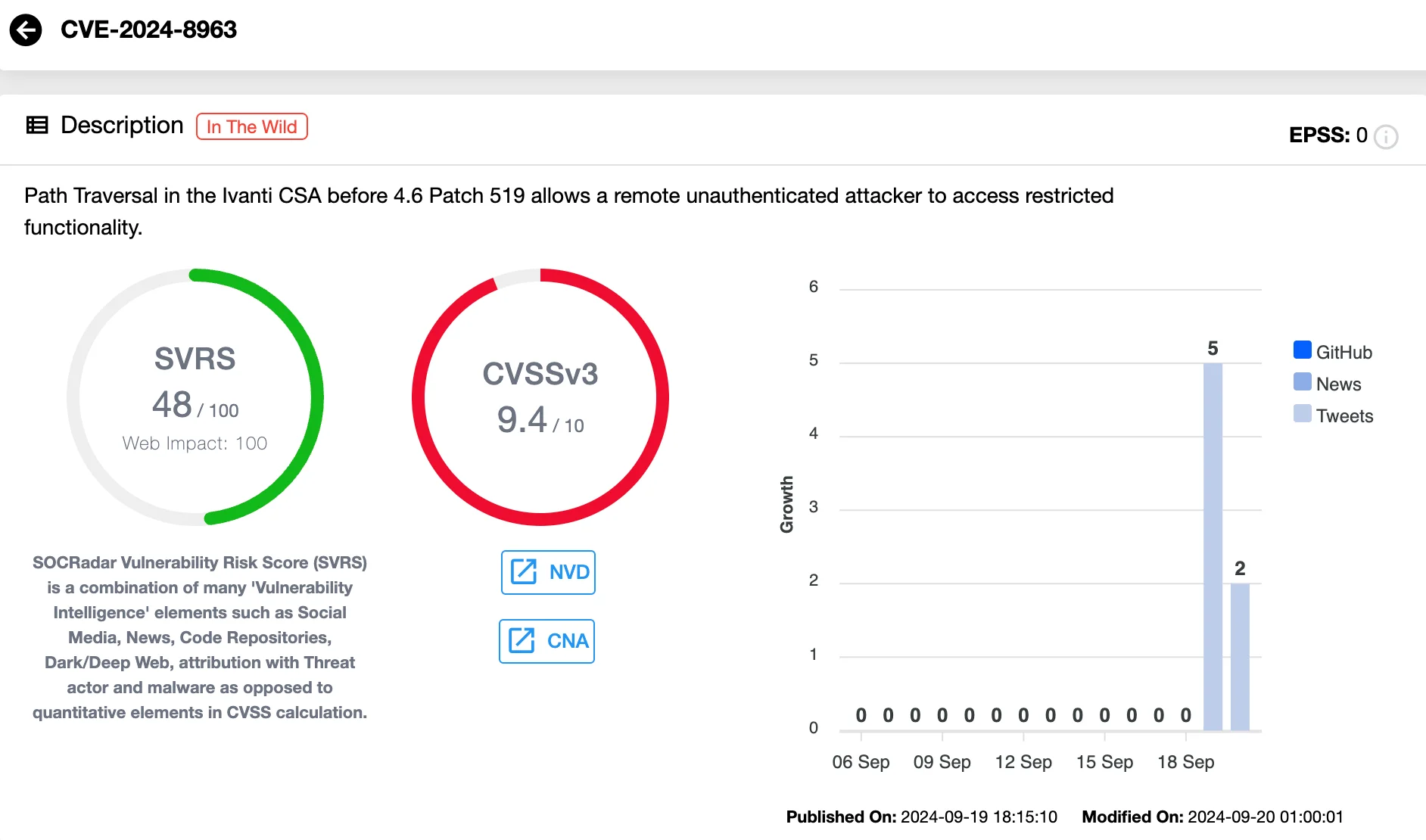
Details of the Ivanti CSA Admin Bypass Vulnerability, CVE-2024-8963 (SOCRadar Vulnerability Intelligence)
Due to its active exploitation, CISA has issued an alert, adding this vulnerability to its Known Exploited Vulnerabilities (KEV) catalog. Federal agencies are required to apply the necessary fixes by October 10, 2024.
Further complicating the situation, CVE-2024-8963 can be used in an exploit chain with the previously disclosed vulnerability CVE-2024-8190 (CVSS: 7.2), allowing attackers to bypass admin authentication and execute arbitrary commands on the appliance.
According to Ivanti’s official advisory, the new vulnerability (CVE-2024-8963) was identified during an investigation into the previous exploitation, which was disclosed on September 13. During the evaluation of its root cause, the company found that Patch 519 had incidentally addressed the issue by removing some functionality that contributed to the vulnerability.
Exploitation of Previous Ivanti CSA Vulnerability (CVE-2024-8190)
The last patch from Ivanti addressed CVE-2024-8190, a high-severity command injection flaw in the Cloud Services Appliance (CSA). The vulnerability continues to be actively exploited, and this week, Horizon3.ai released a Proof-of-Concept (PoC) exploit for CVE-2024-8190 on GitHub, accompanied by an analysis in their blog.
CVE-2024-8190 has also been added to CISA’s Known Exploited Vulnerabilities (KEV) Catalog, with a patch deadline set for October 4, 2024. Ivanti urges users to apply the patch immediately and reduce exploitation risk by configuring dual-homed CSA setups with eth0 as the internal network.
Ivanti has confirmed that some customers have already been targeted with CVE-2024-8190. Shortly after the public disclosure of its exploitation, the new vulnerability, CVE-2024-8963, also started being targeted. The fact that the two vulnerabilities can be chained for exploitation, allowing attackers to gain access and execute commands, makes it even more urgent to patch them.
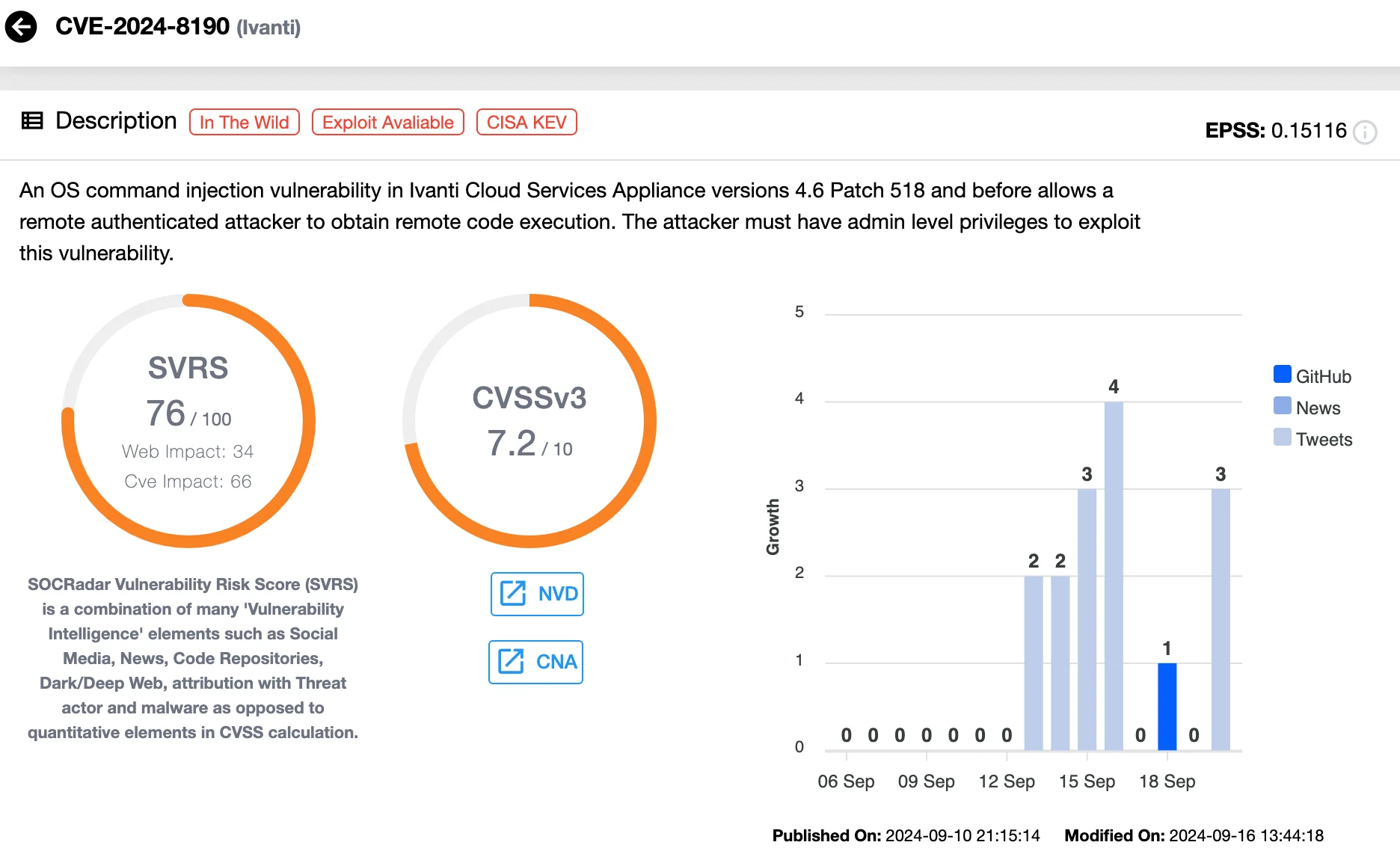
Details of the Ivanti CSA OS Command Injection Vulnerability, CVE-2024-8190 (SOCRadar Vulnerability Intelligence)
With SOCRadar’s Vulnerability Intelligence module, you can keep track of the latest CVEs, exploitation trends, and vulnerabilities affecting your systems. The module provides extensive updates and analyses on disclosed vulnerabilities, helping security teams prioritize and address critical vulnerabilities before they can be exploited.
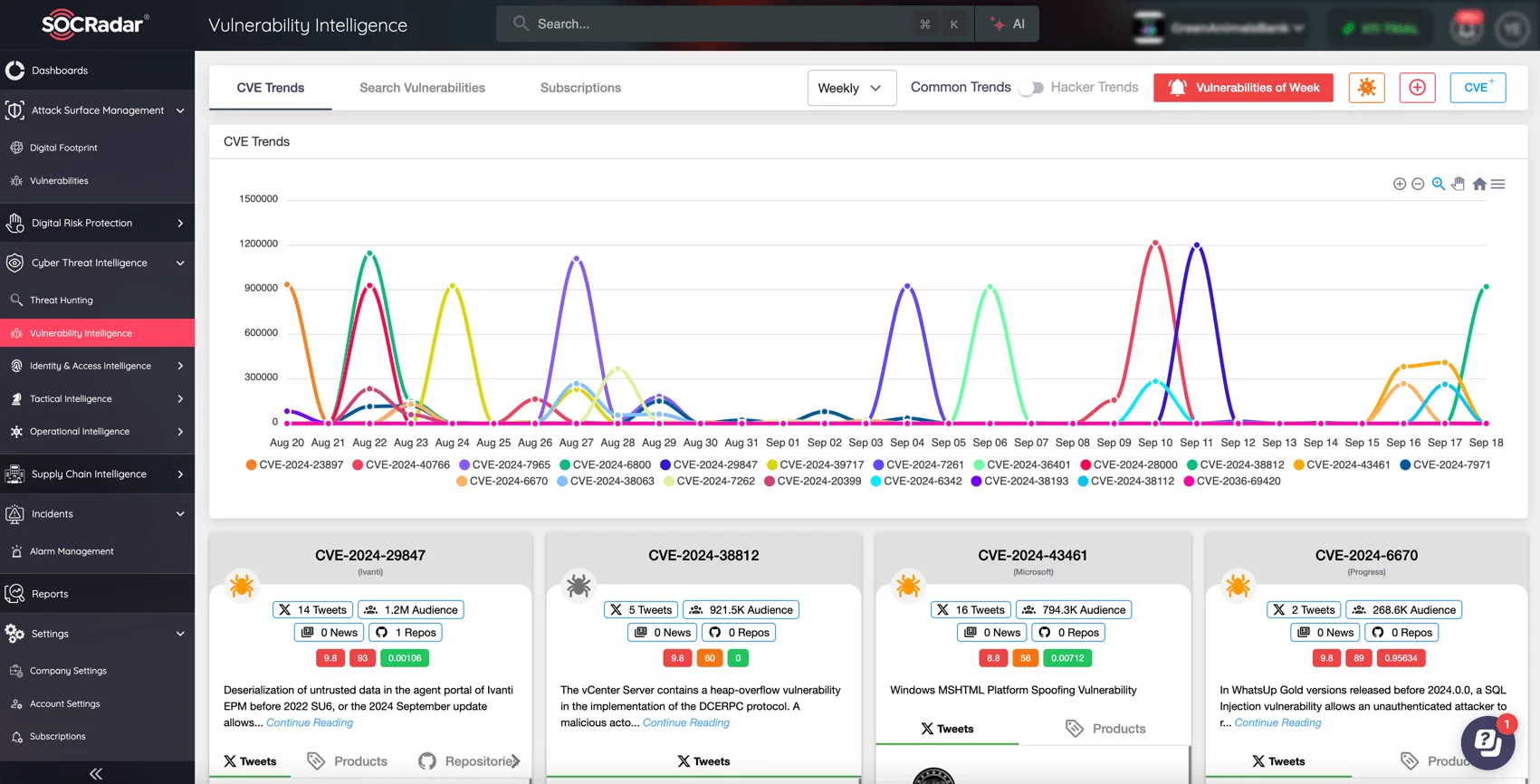
Keep up with exploitation trends with SOCRadar’s Vulnerability Intelligence module
With detailed reports and actionable insights, SOCRadar’s Vulnerability Intelligence ensures that your organization is always one step ahead in patch management and threat mitigation.
Affected Versions and End-of-Life Notice for Ivanti CSA 4.6
Ivanti has confirmed that all versions of Cloud Services Appliance (CSA) 4.6 prior to Patch 519 are affected by the CVE-2024-8963 vulnerability.
Notably, Ivanti CSA 4.6 has reached its End-of-Life (EoL) status, meaning it no longer receives updates or patches. The company emphasized that the patch released on September 10, 2024, is the last fix that will be backported to CSA 4.6.
Given the active exploitation of this vulnerability, it is important for organizations using CSA 4.6 to apply the patch immediately to avoid potential security breaches.
How to Address CVE-2024-8963 in Ivanti Cloud Services Appliance (CSA)
To ensure continued support and protection, customers are urged to upgrade to Ivanti Cloud Services Appliance (CSA) 5.0.
With CSA 4.6 reaching its End-of-Life, users should transition to version 5.0 as soon as possible to avoid exposure. In addition to upgrading, Ivanti recommends thoroughly reviewing your CSA for any newly added or modified administrative users. While not always consistent, suspicious activities may appear in the broker logs, which are stored locally.
For those using Endpoint Detection and Response (EDR) or other security tools, it’s recommended to monitor alerts. As CSA operates as an edge device, Ivanti advises using a layered security approach, including the installation of EDR tools on your CSA for enhanced protection.
For more details on the vulnerability and update guidance, refer to the Ivanti advisory.
Continuously monitor your external-facing digital assets for vulnerabilities with SOCRadar’s Attack Surface Management (ASM) module. Enable proactive defense and efficient management of your security posture with real-time alerts on newly discovered risks and security issues.
With visibility into exposed endpoints, shadow IT, and potential attack vectors, SOCRadar’s ASM helps reduce your attack surface and protect your organization from evolving cyber threats.
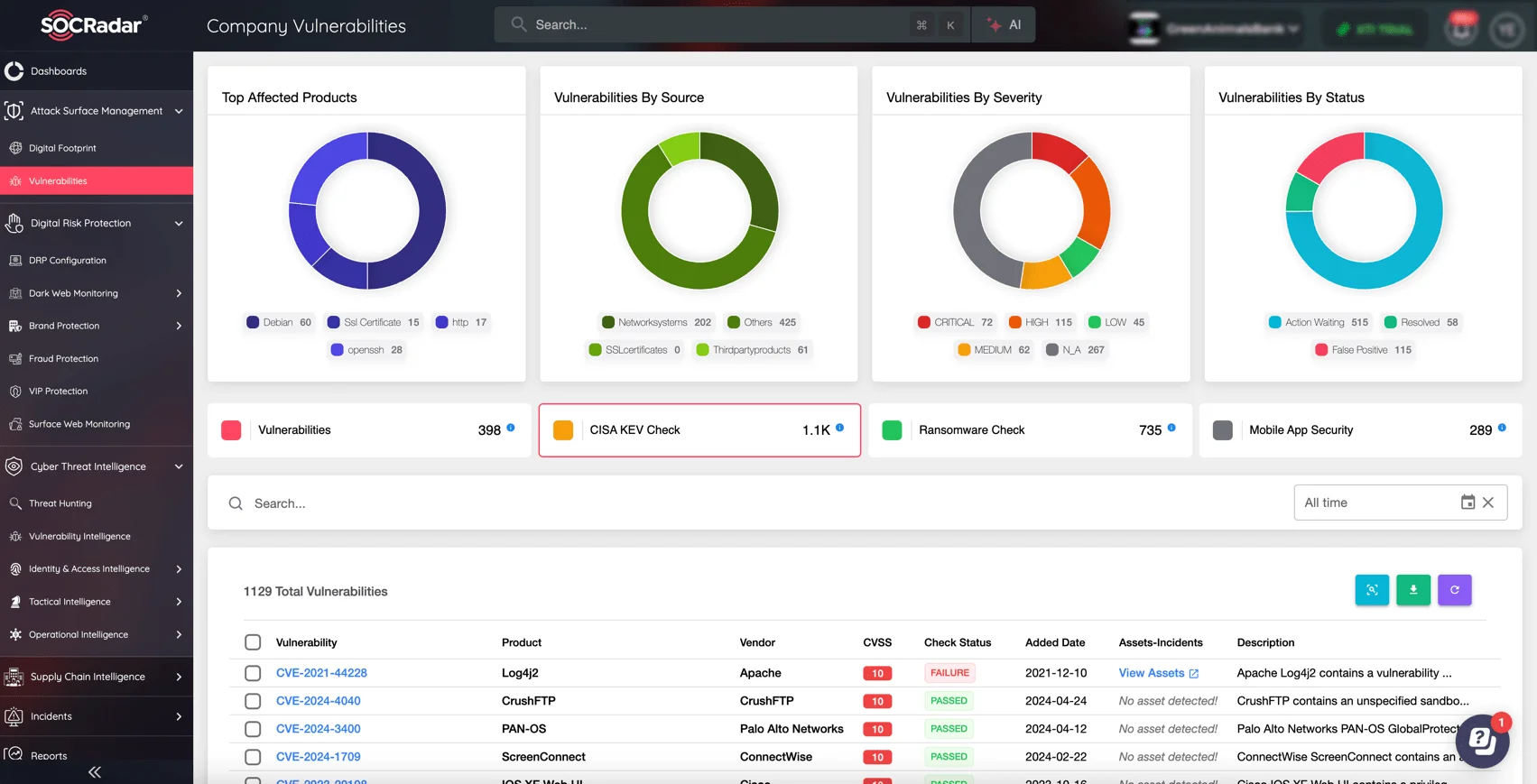
Monitor your digital assets and vulnerabilities via SOCRadar’s ASM module
Another feature of SOCRadar’s ASM is the integrated CISA KEV Check, which compares your system’s vulnerabilities to those published in the CISA KEV Catalog, helping you in meeting compliance requirements.




































