
LottieFiles Supply Chain Attack: Compromised npm Package Targets Cryptocurrency Wallets
LottieFiles recently disclosed a major supply chain attack affecting its open-source JavaScript library, lottie-player. This npm package, widely used by developers to embed animations on websites, was compromised, creating serious security risks for users.
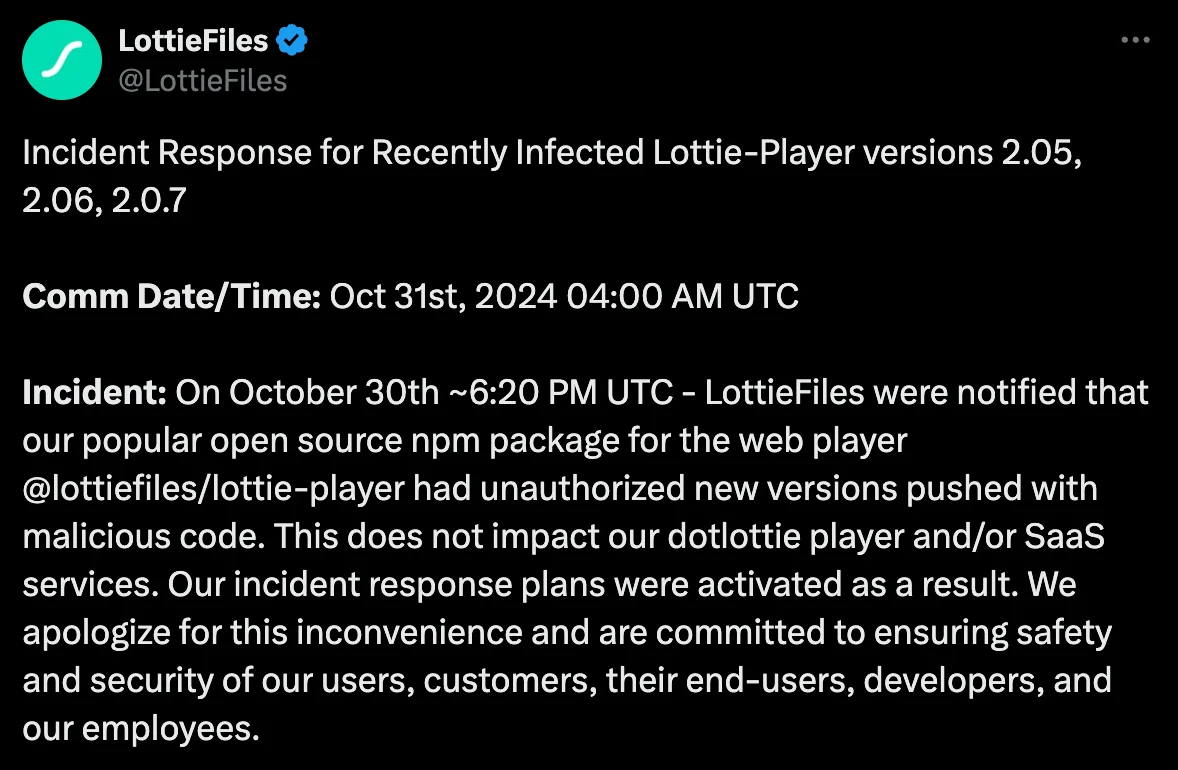
On October 31, 2024, LottieFiles issued a statement on the social platform X regarding the supply chain attack, confirming that unauthorized versions of the package were uploaded with malicious code and assured users that its incident response plan was promptly activated.
Tweet by LottieFiles (X)
The injected code in unauthorized versions aimed to exploit users by prompting cryptocurrency wallet connections, potentially draining users’ funds. This incident has raised alarm over the security of the software supply chain and its implications for millions of users relying on the lottie-player library for web integrations.
How Did the LottieFiles Supply Chain Attack Happen?
The LottieFiles supply chain attack unfolded when unauthorized new versions (2.0.5, 2.0.6, and 2.0.7) of the npm package “@lottiefiles/lottie-player” were uploaded with malicious code, exploiting a compromised developer access token.
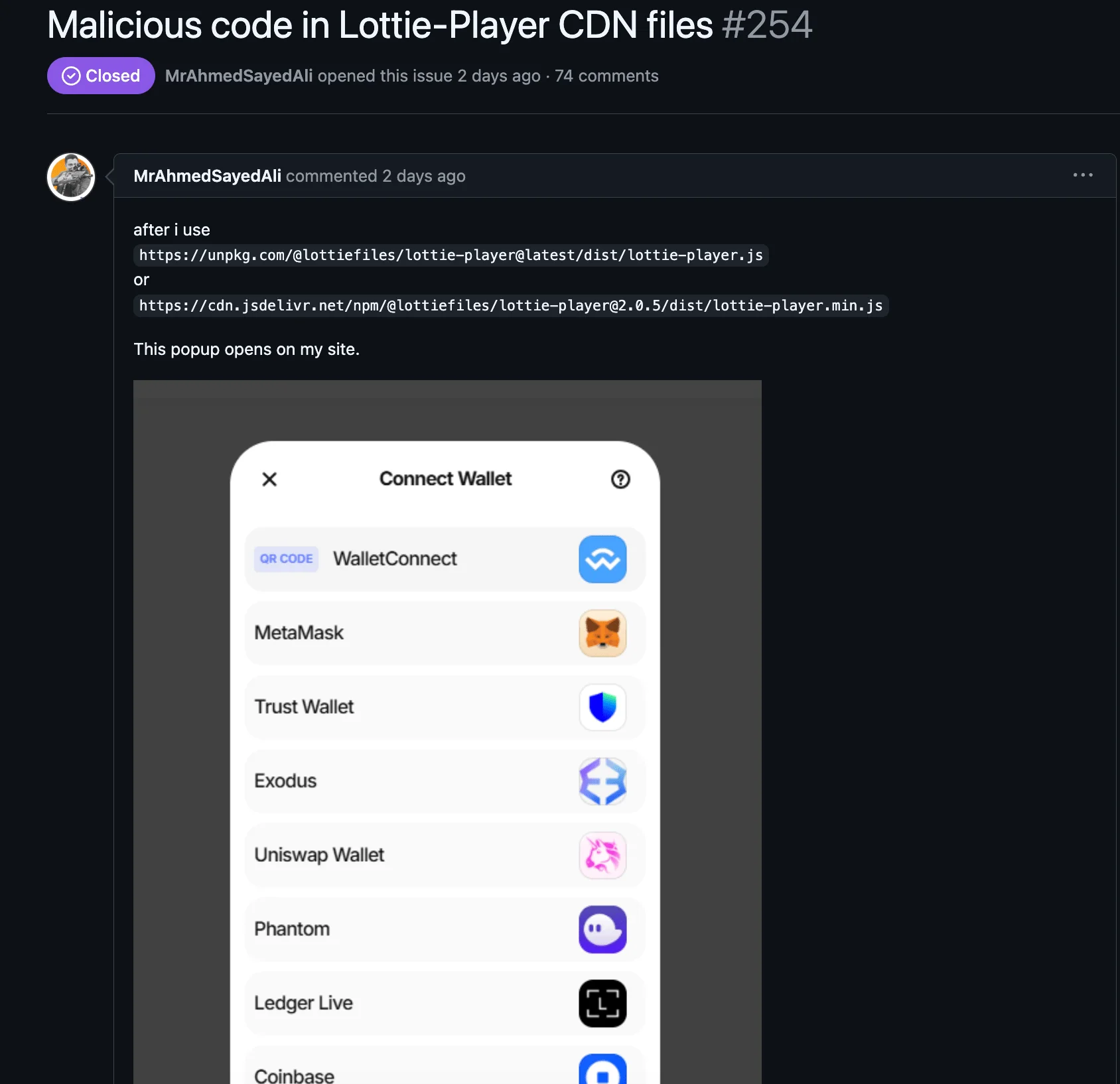
The issue was initially brought up on a GitHub thread on October 30, where a user reported about the malicious pop up. (GitHub)
This code injection targeted websites using the lottie-player package to serve animations, specifically embedding a crypto wallet drainer to prompt users into connecting their cryptocurrency wallets. Once connected, the malicious script attempted to siphon funds from users’ wallets.
A significant aspect of the attack was its ability to reach a broad user base through third-party CDNs. According to LottieFiles, many developers using lottie-player had not set pinned versions, meaning they were automatically served the compromised update when it was released. This allowed the attack to proliferate quickly across multiple sites, unknowingly delivering the harmful code to countless users.
The advanced monitoring capabilities of SOCRadar Extended Threat Intelligence (XTI) provide real-time alerts on potential threats, giving your organization critical lead time to respond. When unusual activity or possible security breaches, such as supply chain attacks, are detected within a monitored environment, SOCRadar generates immediate alarms.
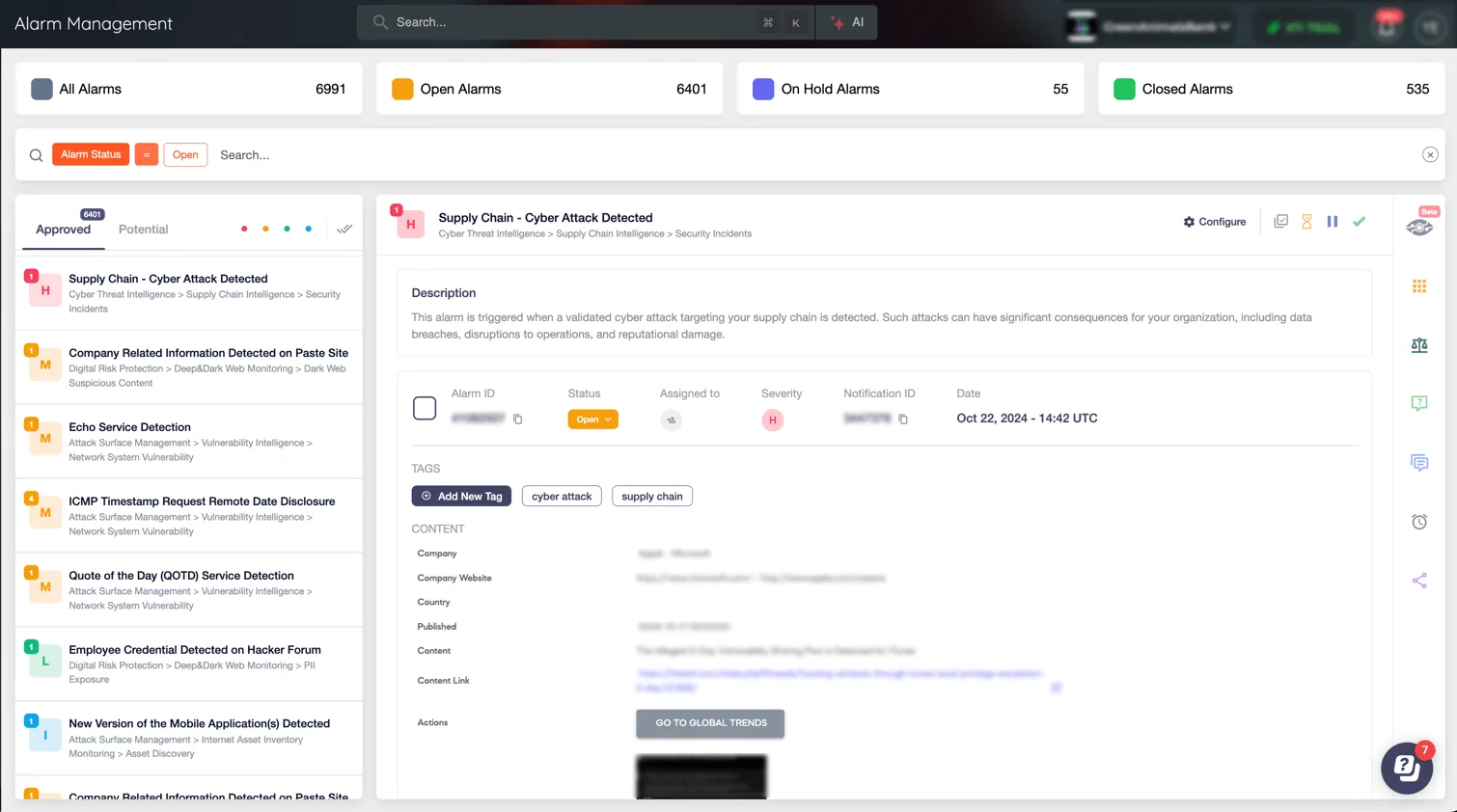
Alarm: Supply Chain Cyber Attack Detected (SOCRadar Alarm Management page)
This proactive approach allows your security team to swiftly investigate and mitigate risks before they escalate, ensuring protection for users and assets.
Details of the Malicious Code
The malicious code embedded in the compromised versions of the lottie-player package was designed to prompt users visiting affected websites to connect their cryptocurrency wallets. These versions are 2.0.5, 2.0.6, and 2.0.7.
Once connected, the injected script initiated a wallet-draining scheme, transferring assets directly from users’ wallets. Reportedly, one user lost 10 Bitcoins (which is roughly $723,000) as a result of this attack.
The compromised package versions included code that established a callback to known phishing sites, such as castleservices01[.]com, previously linked to crypto-targeted scams. This site served as the Command and Control (C2) server for the wallet-drainer, facilitating the unauthorized transfer of cryptocurrency assets.
![Log shows that the client attempted to establish a connection with the server at wss://castleservices01[.]com/ws/ (GitHub)](https://socradar.io/wp-content/uploads/2024/11/websocket-connection-failed.png.webp)
Log shows that the client attempted to establish a connection with the server at wss://castleservices01[.]com/ws/ (GitHub)
LottieFiles’ Response and Security Measures
The company quickly responded to the incident by releasing a safe version of the lottie-player package, 2.0.8, which was based on the last verified clean version, 2.0.4. They removed the compromised versions from npm while working with CDN providers to eliminate any infected files in circulation. Affected devices within the company have also been isolated, and the company has revoked compromised access tokens, enlisting external experts to help with further investigation.
Additionally, they confirmed that other open-source libraries, GitHub repositories, and the SaaS platform remained unaffected, suggesting that the impact was limited to the compromised npm package.
The company is actively sharing updates through a Twitter thread as they work to completely ensure users’ security.
What Was the Root Cause of the LottieFiles Supply Chain Attack?
The root cause of the LottieFiles breach was traced back to an email phishing attack that led to an Account Takeover (ATO) of a developer’s npm account. With unauthorized access, the threat actors were able to upload compromised versions of the lottie-player package, injecting malicious code into the supply chain.
This incident emphasizes how important it is to have strong access controls and secure key management, especially in open-source environments where a single security lapse can affect a vast user base. Enforcing Multi-Factor Authentication (MFA) and routinely rotating access tokens, and limiting permissions are key practices that can help mitigate the risk of such attacks.
Recommendations to Prevent Supply Chain Attacks
Mitigating future supply chain attacks requires practical, proactive steps from both developers and end users.
Developers can start by securing npm dependencies: this includes pinning package versions to prevent unintentional updates, closely monitoring dependencies for suspicious changes, and using static code analysis and supply chain security tools to detect any malicious code introduced into libraries.
Following the LottieFiles compromise, the company advised anyone using compromised versions 2.0.5, 2.0.6, or 2.0.7 to update immediately to the secure version, 2.0.8, and verify the integrity of the update using the provided SHA-512 hash:
sha512-PWfm8AFyrijfnvGc2pdu6avIrnC7UAjvvHqURNk0DS748/ilxRmYXGYkgdU1z/BIl3fbHCZJ89Zqjwg/9cx6NQ==
For those unable to upgrade right away, LottieFiles advises notifying users not to engage with cryptocurrency wallet prompts, which could be fraudulent.
In an era of rising supply chain threats, SOCRadar’s Supply Chain Intelligence Module provides organizations with advanced tools to secure their digital ecosystems. Through features like third-party risk scoring, real-time monitoring, and instant alerts for emerging threats, your security team can ensure a clear view of vendor exposure, and promptly reinforce defenses.
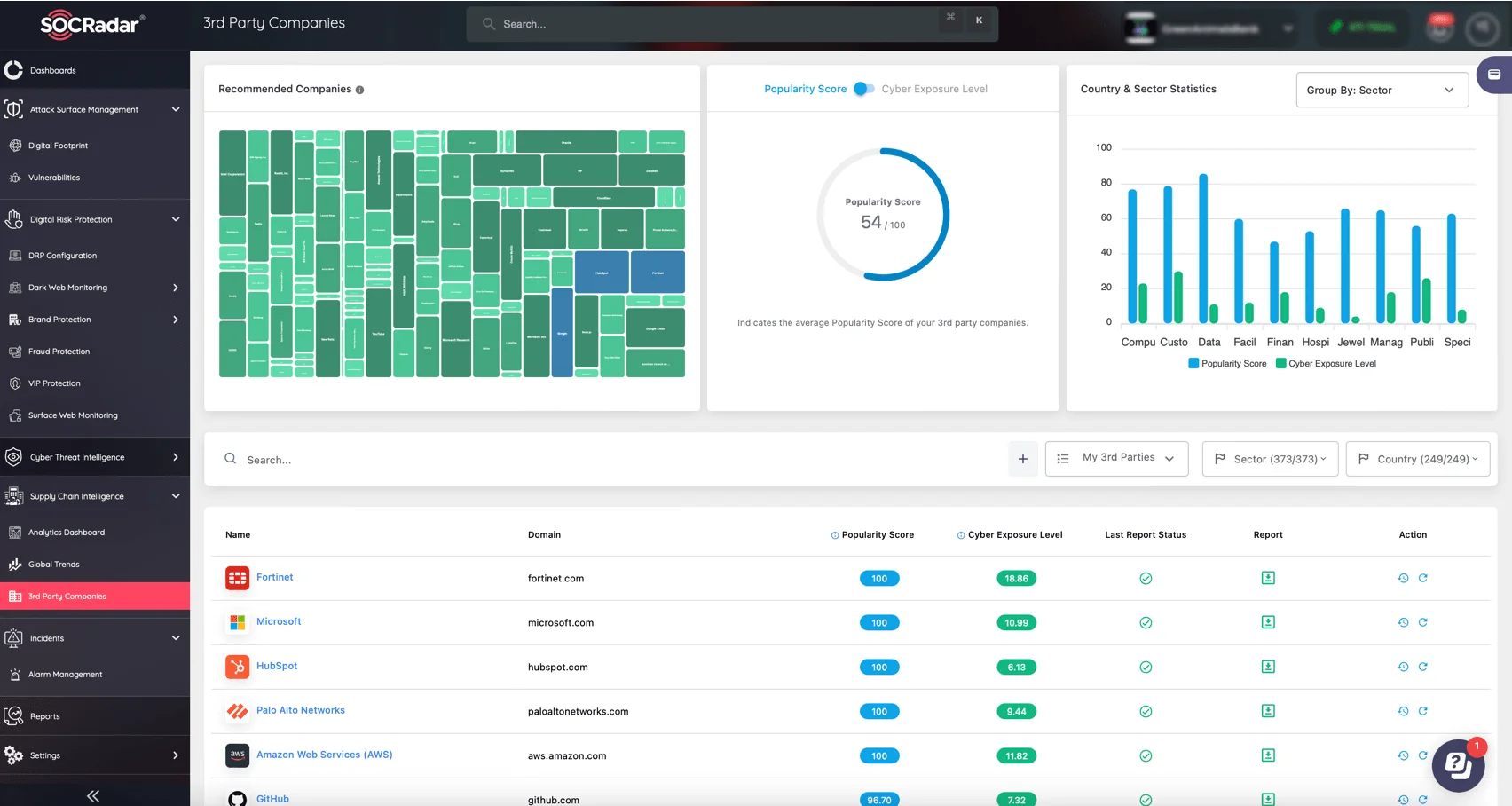
Monitor the exposure of your supply chain and receive alerts with SOCRadar’s Supply Chain Intelligence
For more insights on securing your supply chain, check out5 Supply Chain Intelligence Use Cases with SOCRadar.




































