
RISK:STATION (CVE-2024-10443) – Unpatched Synology Devices at Risk of RCE
Researchers have identified a zero-click vulnerability impacting Synology’s DiskStation and BeeStation devices, posing a significant risk to millions of users. Dubbed RISK:STATION and tracked as CVE-2024-10443, this flaw enables attackers to achieve root-level remote code execution without requiring any user interaction.
Demonstrated during the recent Pwn2Own Ireland 2024 contest as a zero-day, this vulnerability shows the necessity for device owners to apply patches promptly to prevent exploitation. Ensuring up-to-date protections on vulnerable Synology NAS (Network-Attached Storage) devices is essential, as attackers can exploit this flaw to compromise devices.
What is RISK:STATION? Details of CVE-2024-10443
CVE-2024-10443, also known as RISK:STATION, is a zero-click, unauthenticated flaw that impacts Synology’s DiskStation and BeeStation devices. This vulnerability allows attackers to remotely gain root-level privileges without any user interaction, potentially enabling them to access or modify sensitive data, install malware, or carry out additional attacks on compromised systems.
The vulnerability was discovered by security researcher Rick de Jager (@rdjgr) at Midnight Blue.
With millions of Synology devices in use globally, this vulnerability poses a significant security risk. As technical specifics are still undisclosed, users are urged to apply the available patches promptly to protect their devices from potential exploitation.
With vulnerabilities like CVE-2024-10443, timely patching and proactive monitoring are vital. Using advanced tools for Vulnerability Intelligence helps ensure your organization is protected against exploitation and other evolving cyber threats.
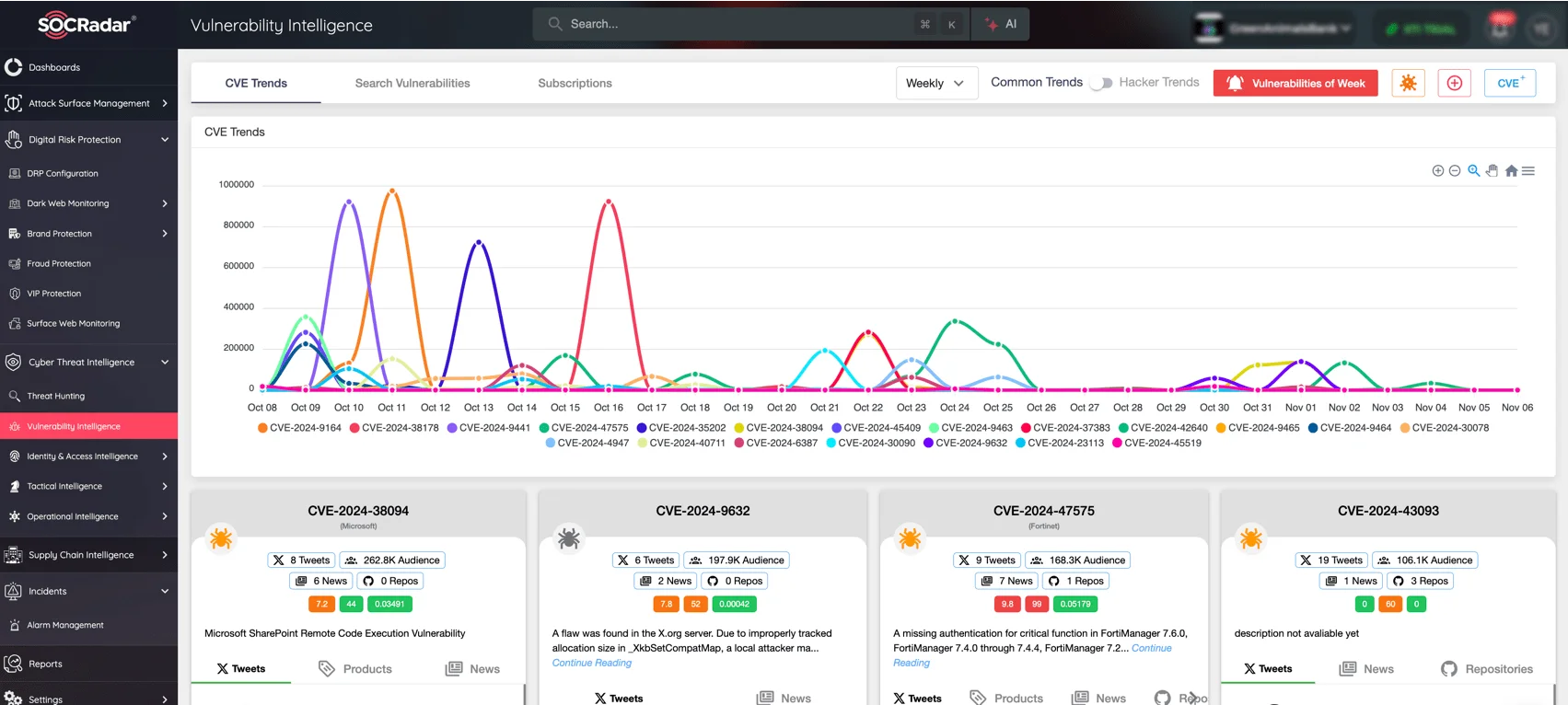
SOCRadar’s Vulnerability Intelligence, CVE and hacker trends
SOCRadar’s Vulnerability Intelligence provides real-time alerts and detailed insights into the latest vulnerabilities and exploits impacting your products. This tool enables you to prioritize patches and effectively mitigate risks by staying informed of threats as they emerge.
Affected Synology Product Versions
The following releases are affected by the RISK:STATION vulnerability and require immediate patching to mitigate security risks:
- BeePhotos on BeeStation OS 1.0
- BeePhotos on BeeStation OS 1.1
- Synology Photos 1.6 on DSM 7.2
- Synology Photos 1.7 on DSM 7.2
In addition, Synology advisories highlight several other high-severity vulnerabilities demonstrated at Pwn2Own 2024. Notable products impacted include Replication Service, Synology Drive Server, and DSM, each posing significant security risks. These advisories are marked as “ongoing,” emphasizing the need for users to stay vigilant and monitor for updates.
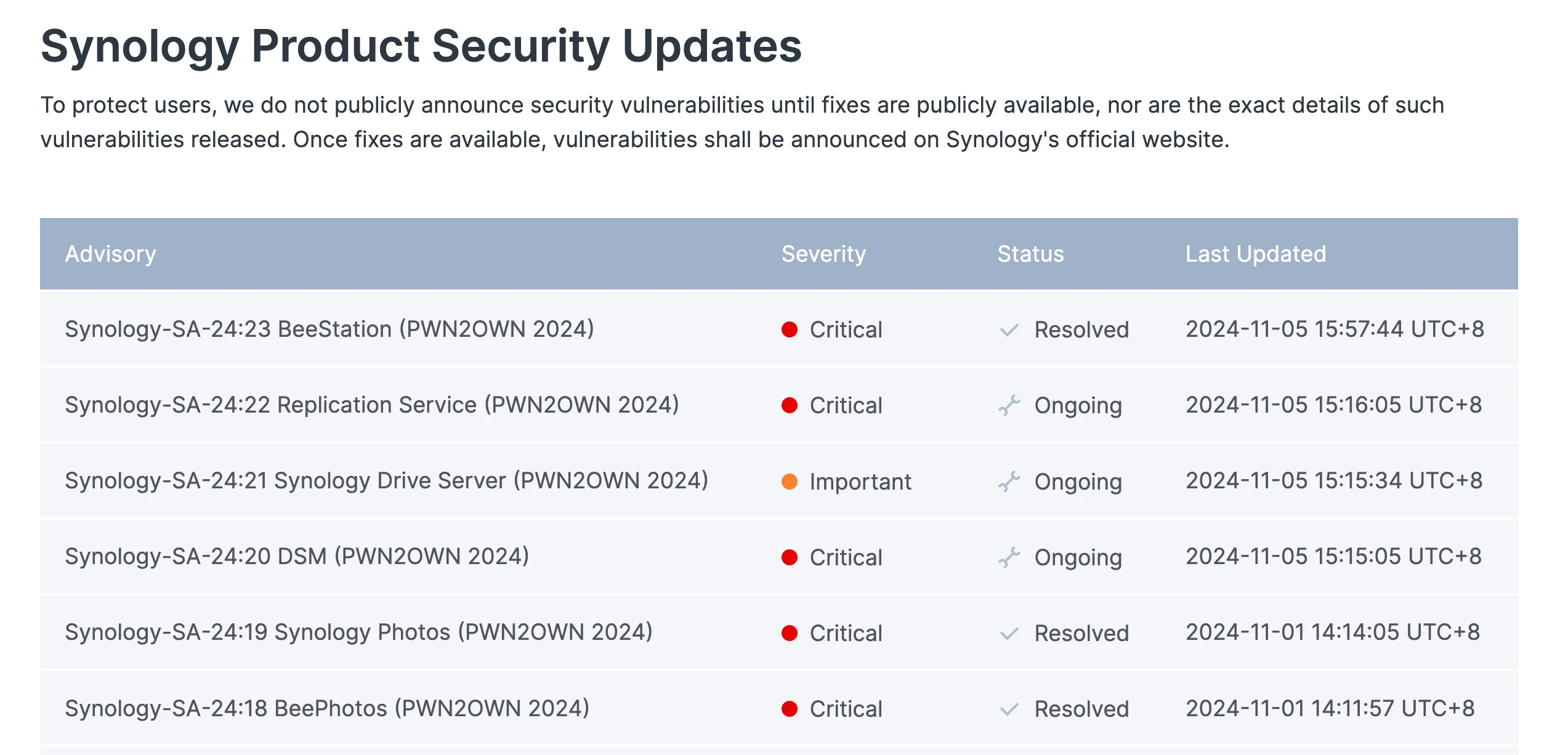
Synology’s Product Security Updates page
Similarly, three critical vulnerabilities affecting QNAP products were also exploited during Pwn2Own, impacting QuRouter (CVE-2024-50389), SMB Service (CVE-2024-50387), and HBS 3 Hybrid Backup Sync (CVE-2024-50388). These flaws have been patched in recent versions, but their discovery reinforces the urgent need for all QNAP users to apply updates without delay.
How Can You Address RISK:STATION Vulnerability?
To mitigate this vulnerability, Synology users need to ensure their devices are updated to the following versions:
- BeePhotos on BeeStation OS 1.0: Upgrade to version 1.0.2-10026 or later.
- BeePhotos on BeeStation OS 1.1: Upgrade to version 1.1.0-10053 or later.
- Synology Photos 1.6 on DSM 7.2: Upgrade to version 1.6.2-0720 or later.
- Synology Photos 1.7 on DSM 7.2: Upgrade to version 1.7.0-0795 or later.
To learn more about the vulnerability and access Synology’s related advisories, visit its research page.
To strengthen defense against such vulnerabilities in the long run, your organization needs continuous visibility over digital assets and potential exposures. SOCRadar’s Attack Surface Management (ASM) offers a solution by thoroughly monitoring your assets in real time, identifying security gaps, and providing alerts on emerging threats.
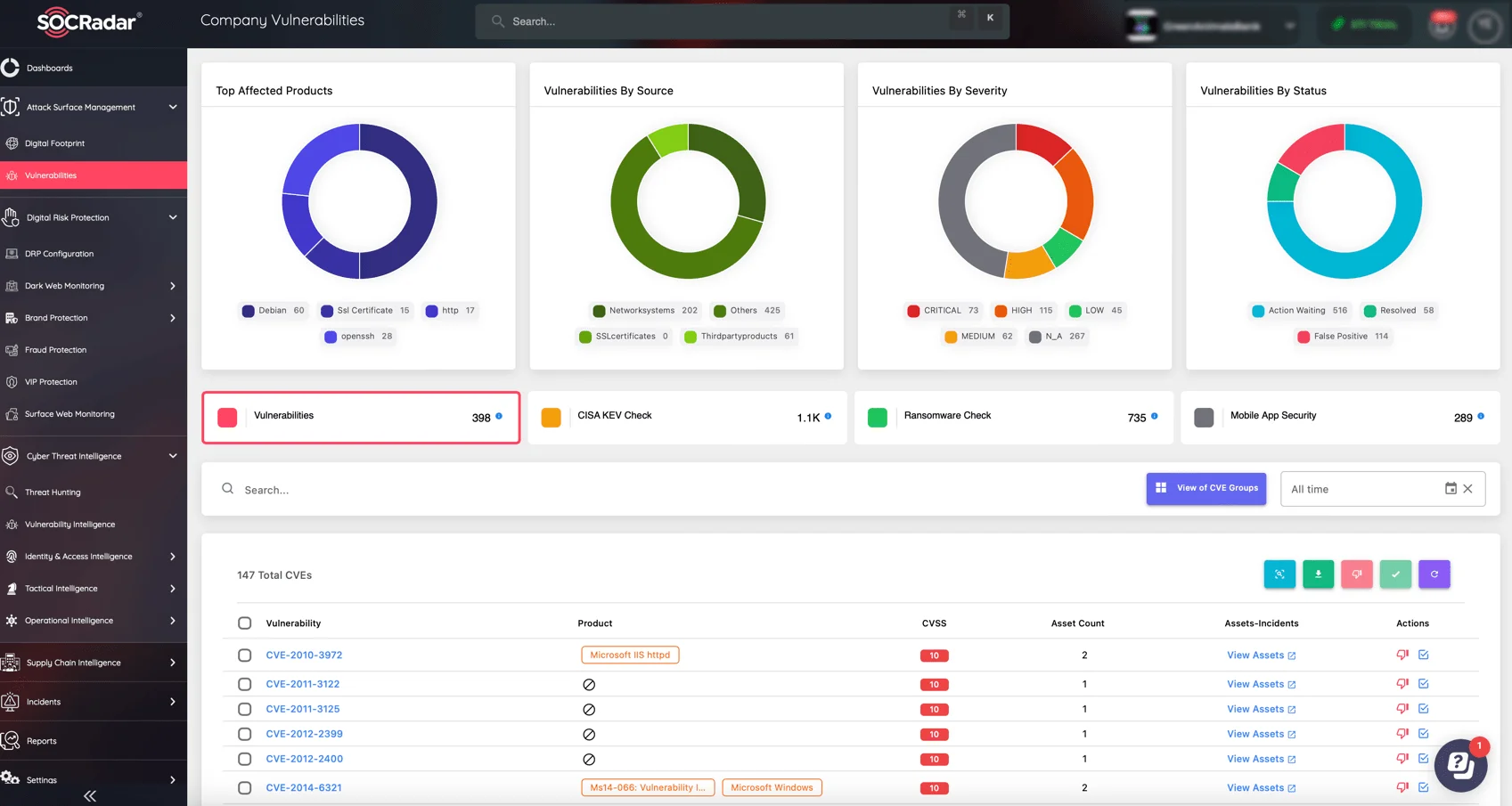
Monitor assets and company vulnerabilities with SOCRadar ASM module
With ASM, you can gain critical insights into your organization’s attack surface, enabling proactive measures to secure assets and prevent exploitation before vulnerabilities can be targeted.




































