
Critical CVE-2024-21899 Vulnerability in QNAP Products; Upcoming PoC Exploit for Outlook Vulnerability, CVE-2024-21378
QNAP recently addressed three vulnerabilities affecting their QTS, QuTS hero, QuTScloud, and myQNAPcloud products. One of these vulnerabilities is of critical severity, marking a concerning development in the vulnerability landscape.
These vulnerabilities have the potential to expose Network-Attached Storage (NAS) devices to unauthenticated access. The affected versions and their respective fixed versions are as follows:
| Affected Versions | Fixed Versions |
| QTS 5.1.x | QTS 5.1.3.2578 build 20231110 and later |
| QTS 4.5.x | QTS 4.5.4.2627 build 20231225 and later |
| QuTS hero h5.1.x | QuTS hero h5.1.3.2578 build 20231110 and later |
| QuTS hero h4.5.x | QuTS hero h4.5.4.2626 build 20231225 and later |
| QuTScloud c5.x | QuTScloud c5.1.5.2651 and later |
| myQNAPcloud 1.0.x | myQNAPcloud 1.0.52 (2023/11/24) and later |
CVE-2024-21899: Critical QNAP Vulnerability Demands Immediate Action
The critical vulnerability, identified as CVE-2024-21899 and carrying a CVSS score of 9.8, stems from improper authentication. According to QNAP’s advisory, this vulnerability could potentially allow unauthorized access to the system via a network. It affects QTS, QuTS hero, and QuTScloud products.
CVE-2024-21899 poses a significant risk as it could enable attackers to gain unauthorized access to sensitive information or disrupt system operations.
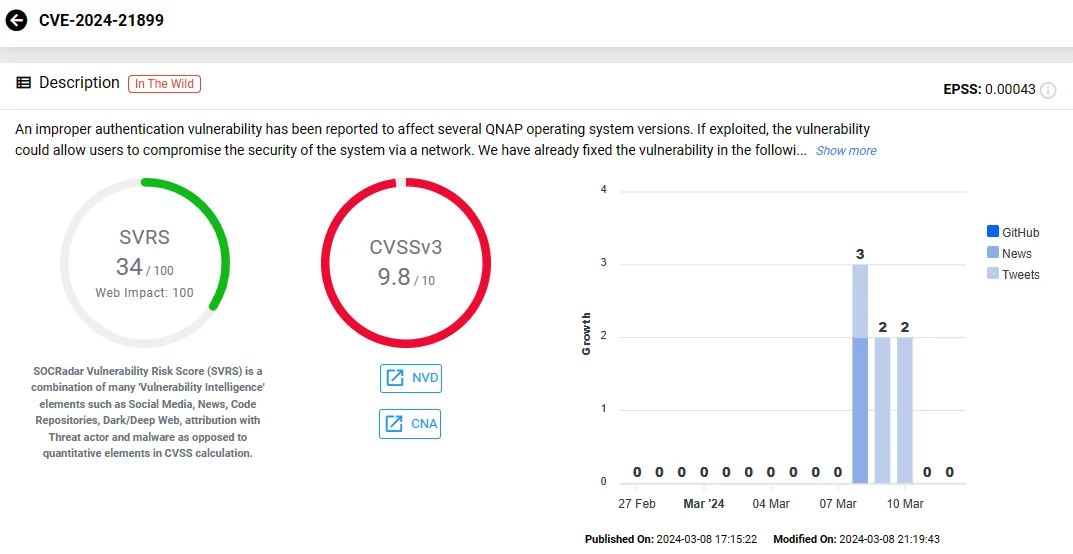
SOCRadar vulnerability card of CVE-2024-21899 (QNAP)
The advisory also addresses two other vulnerabilities, namely CVE-2024-21900 and CVE-2024-21901. These vulnerabilities have medium CVSS scores of 4.3 and 4.7, respectively. They affect the same products mentioned earlier, as well as myQNAPcloud. If exploited, these vulnerabilities could allow authenticated users to execute commands or inject malicious code through a network.
Of the two medium severity vulnerabilities, the latter, CVE-2024-21901, is an SQL injection vulnerability and further necessitates the user to be an administrator for exploitation to be possible.
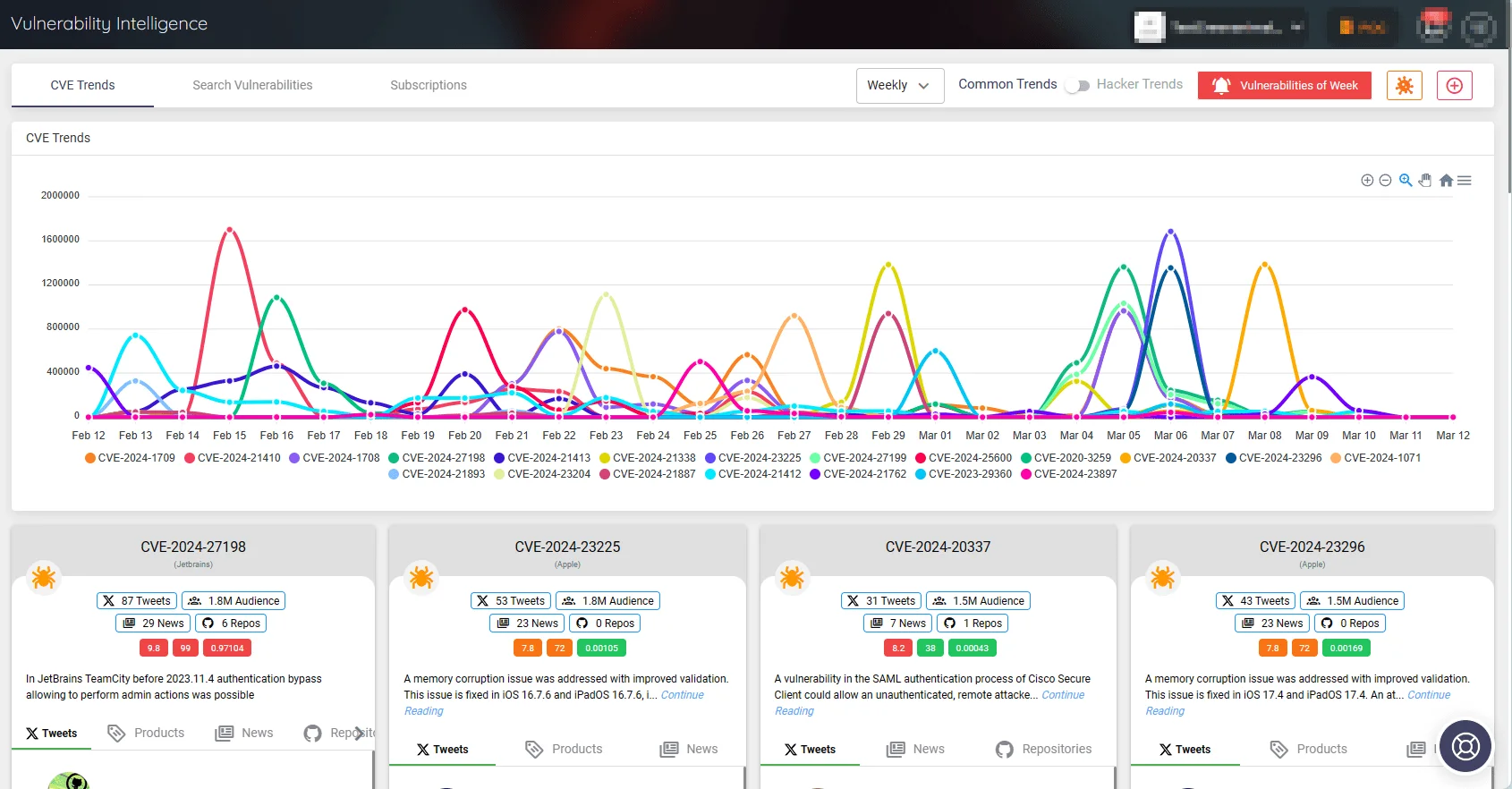
To stay up-to-date with CVE trends, you can use SOCRadar. SOCRadar provides a window into worldwide vulnerability and exploitation trends by monitoring various sources.
DEVCORE was credited with the discovery of these vulnerabilities, as the QNAP advisory cites the identifiers ZDI-CAN-22493/22494 in acknowledgements.
While no reports of these vulnerabilities being exploited have been received, it is important to note that threat actors have previously targeted QNAP NAS devices in malware and ransomware attacks like QSnatch, Deadbolt, and Qlocker.
It is recommended that users promptly apply the available updates to protect against potential exploitation. You can find a guidance for updating QNAP products in the official QNAP security advisory.
PoC Exploit for Outlook Vulnerability CVE-2024-21378 Is to Be Released Soon
Another concerning development in the vulnerability landscape involves a high-severity vulnerability, which Microsoft fixed as part of the February 2024 Patch Tuesday updates.
The vulnerability in our focus, CVE-2024-21378, has a CVSS score of 8.0 and could lead to Remote Code Execution (RCE) in Outlook.
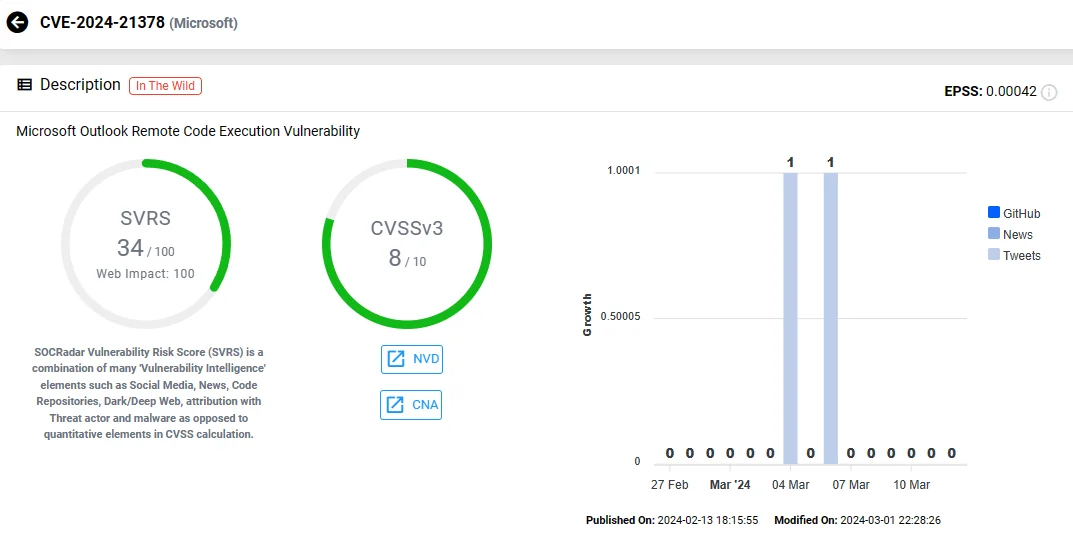
SOCRadar vulnerability card of CVE-2024-21378 (Microsoft Outlook)
What is particularly concerning about this vulnerability is that a Proof-of-Concept (PoC) exploit for it will soon be available. Researchers have detailed their discovery and weaponization of the CVE-2024-21378 vulnerability in a recent blog post. They have also announced the upcoming release of a PoC, but have stated their intention to wait for organizations to properly address the vulnerability before making it available.
To weaponize CVE-2024-21378, the researchers modified an Outlook penetration testing tool, Ruler, and used compromised access tokens to authenticate to Exchange Online and sync a form with properties that would launch an arbitrary COM-compliant native DLL.
The Scope of the Outlook Vulnerability, CVE-2024-21378
ZoomEye returns approximately 518,000 results when searching for Outlook WebApp, reflecting the number of instances exposed over the internet.
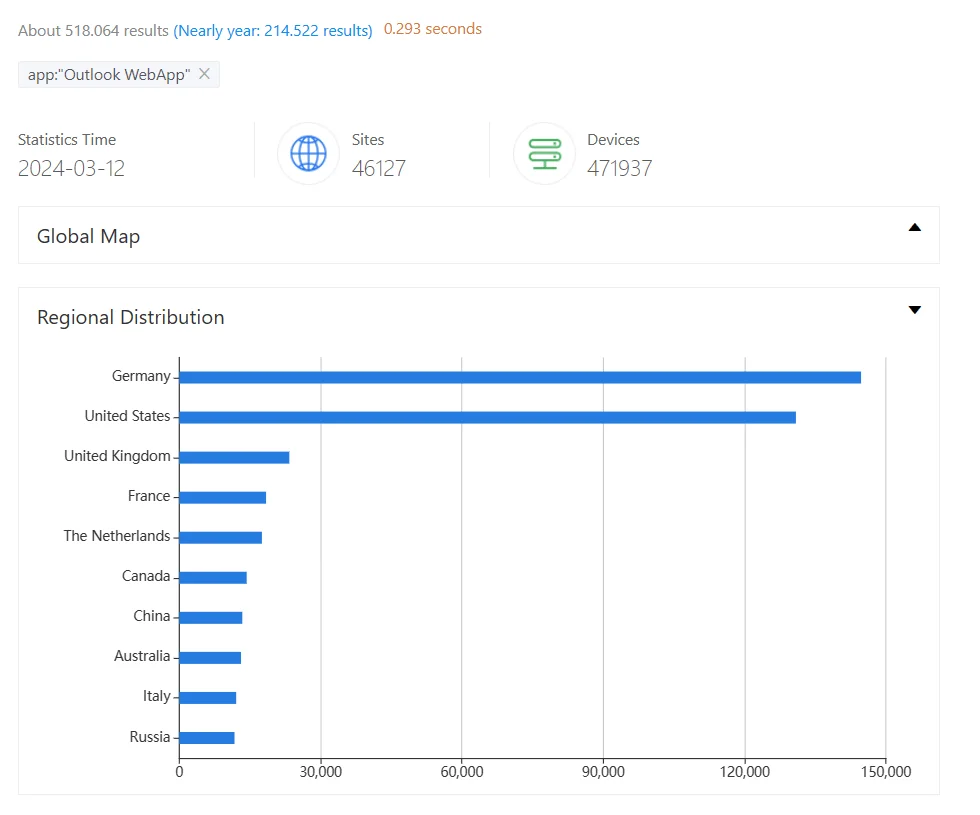
Outlook instances exposed and potentially vulnerable to CVE-2024-21378 (ZoomEye)
The majority of these Outlook instances appear to be in Germany and the United States.
You can keep track of vulnerabilities and be notified when exploits become available by using SOCRadar’s Vulnerability Intelligence.
SOCRadar’s Vulnerability Intelligence, Subscriptions page
Using the SOCRadar XTI platform, you can maintain complete control over your digital footprint while also gaining valuable intelligence to stay ahead of threat actors. The platform also provides alerts for emerging security issues within your organization, allowing for more effective patch management and a stronger overall security posture.
With the Attack Surface Management module, you can monitor your asset inventory and vulnerabilities that affect your organization.
With Freemium, you can test out the features of the SOCRadar XTI platform:




































