Microsoft’s November 2023 Patch Tuesday Tackles Exploited Zero-Day Vulnerabilities, Now Listed in CISA KEV
Microsoft recently rolled out its Patch Tuesday for November 2023, tackling a total of 63 security vulnerabilities. Of these, three carry a critical rating, and five are identified as zero-day vulnerabilities.
Three zero-day vulnerabilities are currently under active exploitation. Microsoft indicates these vulnerabilities with the “Exploitation Detected” label in the release note. Additionally, the Cybersecurity and Infrastructure Security Agency (CISA) has promptly included these vulnerabilities in the Known Exploited Vulnerabilities (KEV) catalog, cautioning organizations about the inherent dangers and emphasizing the imperative need for immediate patching.
The vulnerability types addressed in the November 2023 Patch Tuesday include:
- 18 Elevation of Privilege (EoP) Vulnerabilities
- 17 Remote Code Execution (RCE) Vulnerabilities
- 7 Spoofing Vulnerabilities
- 6 Information Disclosure Vulnerabilities
- 6 Security Feature Bypass Vulnerabilities
- 5 Denial of Service (DoS) Vulnerabilities
- 3 Cross-Site Scripting (XSS) Vulnerability
- 1 Memory Corruption Vulnerability
In the November 2023 Patch Tuesday, a notable change from recent updates is evident. Unlike before, Remote Code Execution (RCE) vulnerabilities do not dominate the list. Instead, there is a noticeable increase in Elevation of Privilege (EoP) vulnerabilities.
Without delay, let’s outline the addressed vulnerabilities and the risks associated with the ongoing zero-day exploitations.
The Zero-Day Vulnerabilities of November 2023 Patch Tuesday
First, let’s explore the details of the fixed zero-day vulnerabilities which are currently undergoing exploitation.
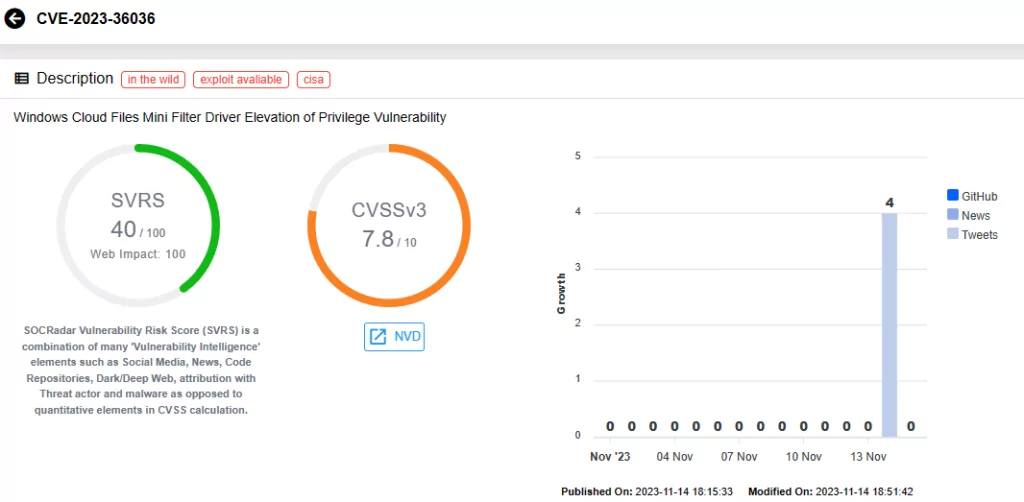
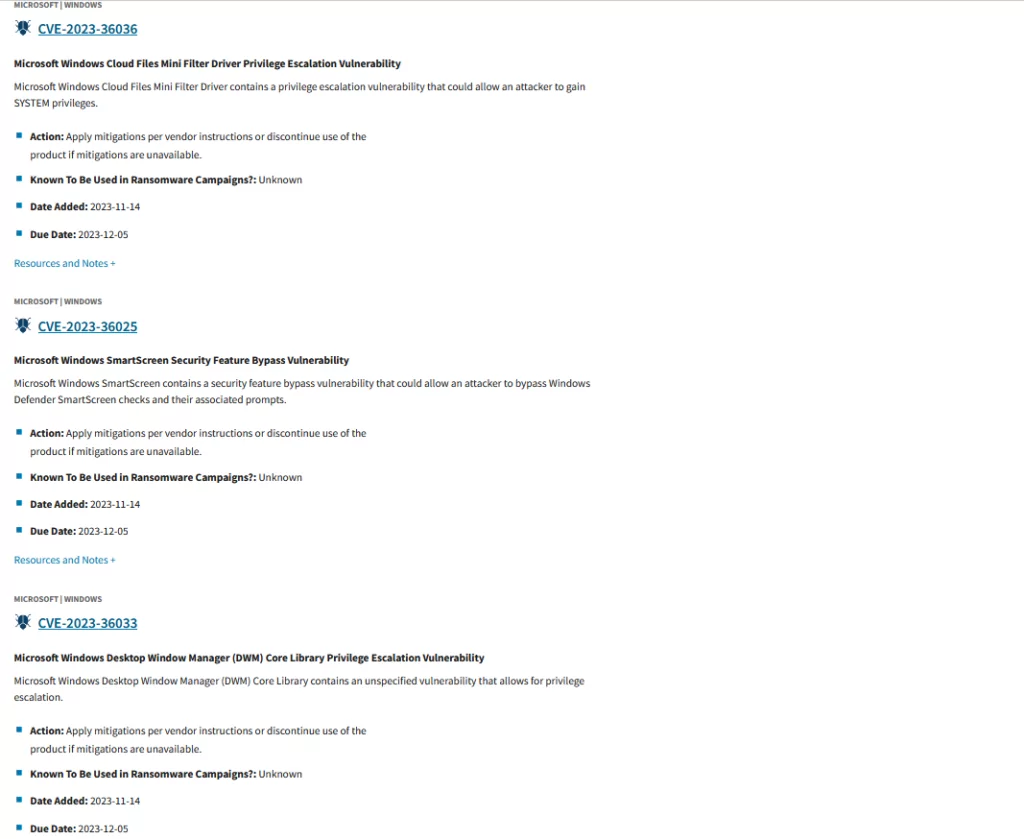
CVE-2023-36025 (CVSS Score: 8.8, High severity):
This vulnerability is identified as a Security Feature Bypass Vulnerability, impacting Windows SmartScreen. Upon successful exploitation, the attacker can bypass Windows Defender SmartScreen checks and associated prompts. However, user interaction is necessary; the user must click on a specially crafted Internet Shortcut (.URL) or a hyperlink pointing to an Internet Shortcut file to be compromised.
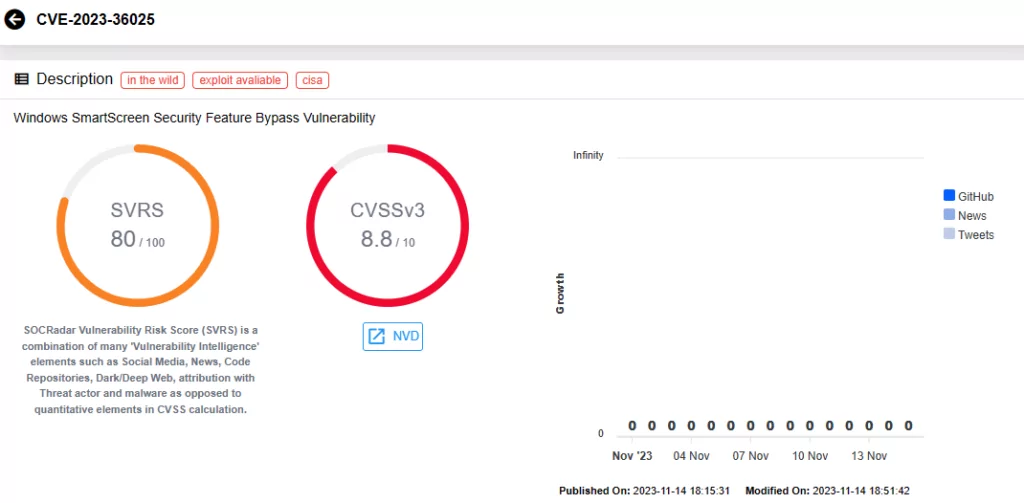
CVE-2023-36033 (CVSS Score: 7.8, High severity):
Described as an Elevation of Privilege Vulnerability, CVE-2023-36033 affects the Windows DWM Core Library. According to Microsoft, an attacker who successfully exploits this vulnerability could gain SYSTEM privileges.
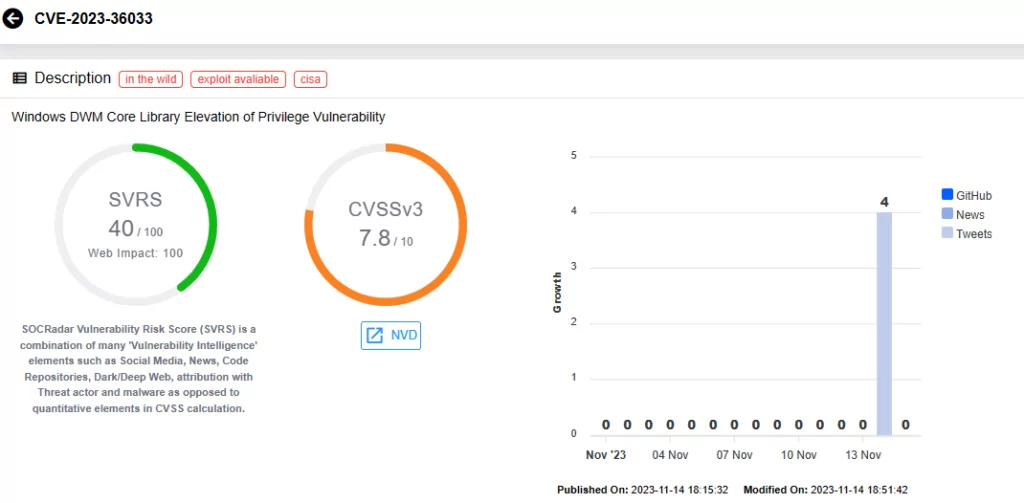
CVE-2023-36036 (CVSS Score: 7.8, High severity):
CVE-2023-36036 is another Elevation of Privilege Vulnerability. It impacts the Windows Cloud Files Mini Filter Driver. An attacker who successfully exploits this vulnerability could also gain SYSTEM privileges.
Microsoft and the discoverers of these vulnerabilities have not yet disclosed how the zero-days were exploited or if a known threat actor is behind their exploitation.
It is likely that as patching efforts commence and a certain number of users mitigate these vulnerabilities, more information will be disclosed. This serves as a heads-up for organizations affected by these vulnerabilities, signaling the importance of initiating patching efforts as soon as possible.
As previously mentioned, these three zero-day vulnerabilities have been added to the Known Exploited Vulnerabilities Catalog by CISA, emphasizing the urgency of prompt patching.
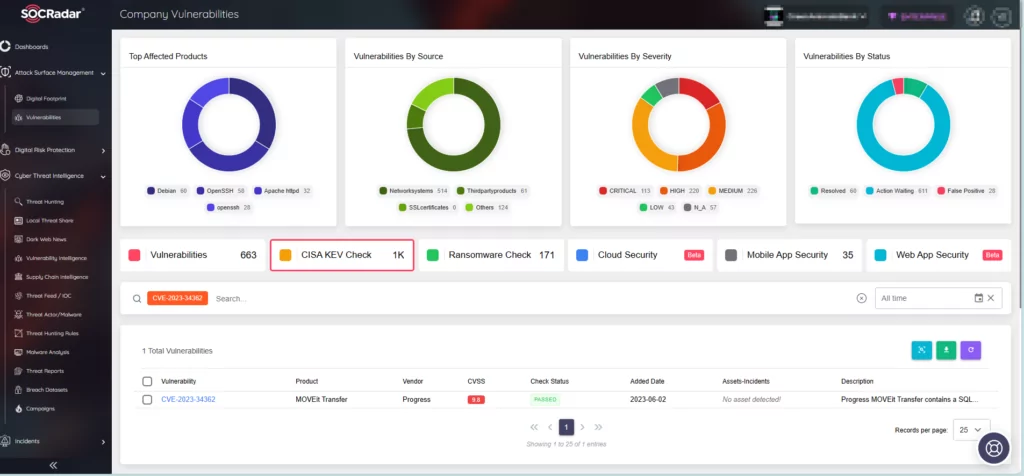
SOCRadar’s Company Vulnerabilities page within Attack Surface Management (ASM) provides crucial information on vulnerabilities impacting your assets. Through the integration of SOCRadar into your security strategy, you can enhance your defense mechanisms and proactively address emerging threats.
Additionally, by leveraging the CISA KEV Check feature, you can identify which vulnerabilities within your assets have been included in the Known Exploited Vulnerabilities Catalog by CISA. This ensures alignment with the agency’s initiatives in combating vulnerabilities and promotes compliance with their efforts.
The two remaining zero-day vulnerabilities that have not been exploited are tracked as CVE-2023-36413 and CVE-2023-36038. These vulnerabilities were disclosed before patches were made available, thereby Microsoft has categorized them as zero-day issues.
CVE-2023-36413 (CVSS Score: 6.5, Medium severity):
CVE-2023-36413 is identified as a Microsoft Office Security Feature Bypass Vulnerability. To exploit this vulnerability, an attacker must send the user a malicious file and persuade them to open it. Successful exploitation enables the attacker to bypass the Office Protected View, opening the file in editing mode rather than protected mode. The vulnerability can potentially be used in phishing scams.
CVE-2023-36038 (CVSS Score: 8.2, High severity):
The CVE-2023-36038 vulnerability is an ASP.NET Core Denial-of-Service (DoS) Vulnerability. It could be exploited if HTTP requests to .NET 8 RC 1 running on IIS InProcess hosting model are canceled. This action would cause an increase in thread counts, and an OutOfMemoryException becomes possible. Microsoft warns that successful exploitation could result in complete loss of availability.
Details of the Critical Vulnerabilities Addressed in November 2023 Patch Tuesday
CVE-2023-36052 (CVSS Score: 8.6, High severity):
Exploiting this Azure CLI REST Command Information Disclosure Vulnerability could allow attackers to recover plaintext passwords and usernames from log files created by affected CLI commands, subsequently published by Azure DevOps and/or GitHub Actions. Unauthenticated attackers can actively search for and discover credentials within log files stored in open-source repositories. The impact of this vulnerability extends beyond the security scope managed by the security authority of the vulnerable component, as the vulnerable component and the impacted component are different and managed by distinct security authorities.
CVE-2023-36400 (CVSS Score: 8.8, High severity):
CVE-2023-36400 is a Windows HMAC Key Derivation Elevation of Privilege Vulnerability that can allow attackers, originating from a low privilege Hyper-V guest, to traverse the guest’s security boundary. This enables them to execute code on the Hyper-V host execution environment, gaining SYSTEM privileges. Exploiting this vulnerability requires the attacker to first log on to the system. Subsequently, running a specially crafted application is necessary to exploit the vulnerability and take control of the affected system.
CVE-2023-36397 (CVSS Score: 9.8, Critical):
CVE-2023-36397 is a critical Windows Pragmatic General Multicast (PGM) Remote Code Execution (RCE) Vulnerability. When a Windows message queuing service is running in a PGM Server environment, attackers can send a specially crafted file over the network, leading to remote code execution. Microsoft specifies that the Windows message queuing service must be enabled for a system to be vulnerable to CVE-2023-36397.
Apply the Patches Provided by Microsoft
We highly recommend applying the patches promptly to safeguard your environment and enhance your security posture. For additional details on the vulnerabilities addressed in the November 2023 Patch Tuesday update, refer to Microsoft’s Release Note.
Combat Vulnerability Exploitation with SOCRadar
SOCRadar XTI can aid in addressing security challenges and effectively safeguard the integrity of systems, as well as brand reputation through its many modules.
The External Attack Surface Management module provides organizations with the tools to quickly identify, assess, and mitigate vulnerabilities, while with the Vulnerability Intelligence feature, the platform strengthens security measures by consistently tracking security vulnerabilities. The Vulnerability Intelligence module allows you to search for vulnerabilities, access detailed information about them, and monitor associated activities, including hacker trends.