
APT Profile: Who is Lazarus Group?
By SOCRadar Research
[Update] December 12, 2023: See the subheading: “Lazarus Uses Log4Shell in Operation Blacksmith, Deploys New Malware: NineRAT, DLRAT, and BottomLoader.”
[Update] September 1, 2023: See the subheading: “VMConnect Campaign Unveiled: Lazarus Group is the Culprit.”
[Update] August 24, 2023: The FBI warns that the Lazarus Group plans to convert stolen cryptocurrency, potentially valued at over $40 million, into cash. Added the subheading “FBI Warns Of Lazarus Plan To Cash Out $40 Million In Stolen Cryptocurrency.”
[Update] August 8, 2023: North Korean state-backed hackers breached Russia’s leading missile manufacturer, NPO Mashinostroyeniya (NPO Mash). Added the subheading: “Lazarus and ScarCruft Breach Leading Missile Manufacturer NPO Mash.”
Nation-state threat actors are cyber threat groups operating in states’ interests. They sabotage, engage in espionage, and steal sensitive information to supply strategic and economic information to their home countries for political or national security reasons. While financial gain is among their motivations, it is not usually at the top of the list. Lazarus group, apart from the majority of other nation-state threat actors, is an Advanced Persistent Threat (APT) actor that prioritizes financial gain as well as political objectives.
Lazarus Group 101
The Lazarus Group is known by many names, including Hidden Cobra, Zinc, APT-C-26, Guardians of Peace, Group 77, Who Is Hacking Team, Stardust Chollima, and Nickel Academy, among other titles. The Lazarus Group is attributed to the Reconnaissance General Bureau (RGB) of the Democratic People’s Republic of Korea (DPRK). In 2017, the U.S. government issued a joint technical alert (TA17-164A), based on analysis by the Federal Bureau of Investigation (FBI) and the Department of Homeland Security (DHS), that identified Hidden Cobra as a “North Korean state-sponsored malicious cyber organization.”
Lazarus group was first identified and named in the ‘Operation BlockBuster’ report (2016) published by a consortium of security firms led by Novetta to investigate the Sony Pictures Entertainment attack in 2014. During the investigation, various malware was found associated with the malware used in the Sony Pictures attack. By tracking the malware and the attackers’ modus operandi, researchers could identify the activities of the Lazarus group as far back as 2009 (possibly 2007).
Because North Korean threat actors tend to share their infrastructure, code, and resources, defining the Lazarus group’s boundaries is challenging. Uncertainties exist over the Lazarus group’s composition due to clusters like “Bluenoroff” and “Andariel,” which are classified as sub-groups, “TEMP.Hermit,” with which it shares code, and “Kimsuky,” with which its operations overlap.
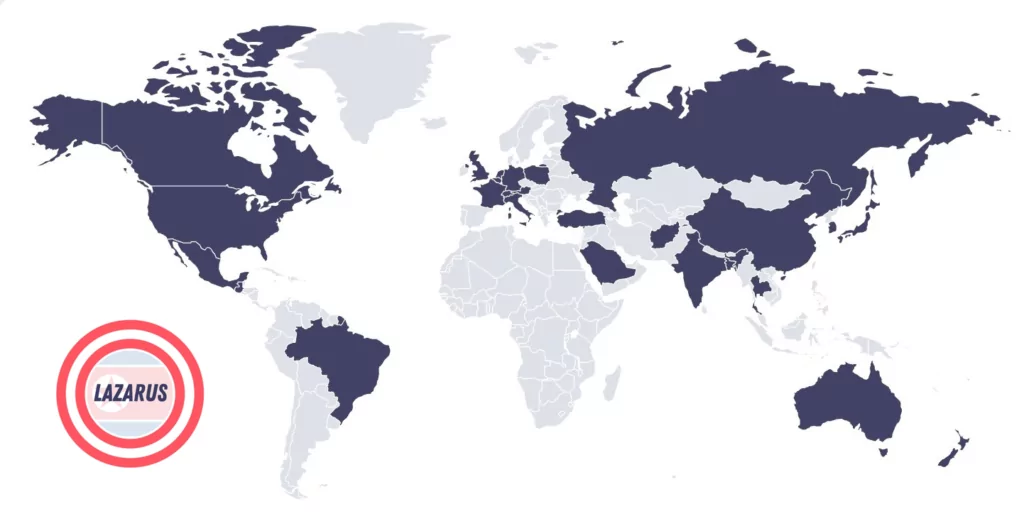
Lazarus group’s activities are aligned with North Korea’s political interests. Therefore, South Korea and the U.S. are the main focus. Other countries among its targets are Afghanistan, Australia, Austria, Bangladesh, Belgium, Brazil, Brazil, Canada, China, France, Germany, Guatemala, Hong Kong, India, Italy, Japan, Mexico, Netherlands, New Zealand, Poland, Russian Federation, Saudi Arabia, Spain, Switzerland, Thailand, Türkiye and the United Kingdom.
Lazarus group has a broader range of operations than other nation-state threat actors. Its primary objectives include information theft, money extortion, espionage, sabotage, and disruption. In addition to bank robberies, cryptocurrency theft, and ransomware attacks for financial gain, it carries out attacks against precisely selected targets in areas where it can obtain strategically important intelligence, such as energy, aviation, and defense.
- Justice, Public Order, and Safety Activities
- Space Research and Technology
- National Security and International Affairs
- Finance and Insurance
- Educational Services
- Health Care and Social Assistance
- Public Administration
- Computer and Electronic Product Manufacturing
- Commodity Contracts Intermediation (CryptoCurrency & NFT Market)
- Publishing Industries (except Internet)
- Utilities
- Manufacturing
They also target journalists, human rights organizations, North Korean defectors, and any group that might criticize the DPRK.
How Does the Lazarus Group Attack
Lazarus group has evolved its strategy over time since its first attacks, which consisted of DDoS operations against various organizations in different industries. Attacks became more destructive due to an ever-evolving arsenal of malware and TTPs.
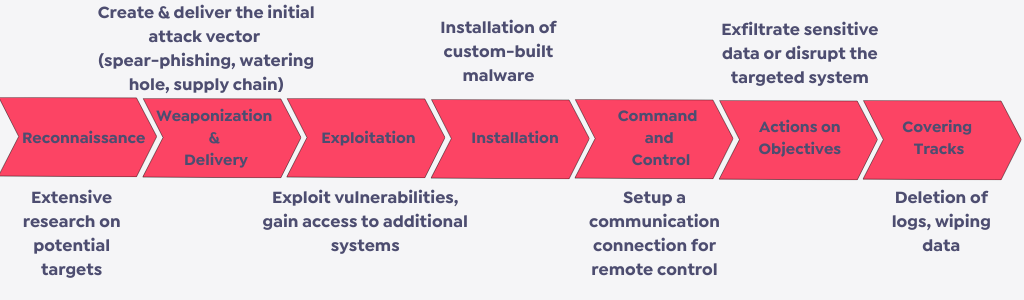
Lazarus group’s attack pattern can vary depending on the specific attacks, although they generally follow similar steps.
- Lazarus group plans sophisticated and focused attacks against potential victims. The group determines potential targets and gathers information about their infrastructure, security posture, and employees. They observe the targets’ activities and find the best attack time.
- They use various technics, including spear phishing, supply-chain attacks, waterhole attacks, and zero-day vulnerability exploitation. To access targeted networks, exfiltrate sensitive data, and maintain persistence, they also use a range of custom-built malware, such as remote access trojans (RATs), backdoors, and botnets.
To hide their tracks and prevent detection, they delete logs and data and infect the victim with malware or ransomware. Once detected, acting swiftly, they try to avoid forensic investigations by immediately repackaging malware and switching encryption keys and algorithms.
Which Tools and Vulnerabilities Does Lazarus Group Use
Over the years, the Lazarus group has carried out several activities, mostly involving disruption, sabotage, financial theft, and espionage. It has a reputation for employing aggressive strategies, such as disk-wiping malware, to damage its targets as much as possible.
Lazarus group is known for creating custom malware for operations and quickly modifying, upgrading, and developing existing malware. Lazarus Group has utilized a variety of tools in the attacks, some of which are:
- Backdoors: Appleseed, HardRain, BadCall, Hidden Cobra, Destroyer, and Duuzer
- Remote Access Trojans (RATs): Fallchill, Joanap, Brambul, and
- Ransomware: Wannacry
Lazarus group has used many zero-day vulnerabilities they purchased or discovered. They also use several known vulnerabilities in their attacks, including:
- Adobe Flash Player vulnerabilities
- Microsoft Office vulnerabilities
- Vulnerabilities in local software of South Korea (Exp. Hangul Word Processor (HWP))
- Vulnerabilities in the SWIFT (The Society for Worldwide Interbank Financial Telecommunication) software
Notable Attacks of the Lazarus Group
In 2016, after being identified and named, the retrospective activities of the Lazarus group were tracked. Large-scale DDoS attacks against the U.S. and South Korea (2009), espionage attacks against U.S. and South Korean websites “Operation Troy” (2009-2013), “Ten Days of Rain,” which included DDoS attacks against South Korean media and financial institutions and U.S. military facilities (2011), “Operation 1Million/Dark Seoul” attack against a South Korean bank and broadcast organization (2013) were all attributed to the Lazarus group.
The “Operation Flame” (2007), which was eventually connected to the “Dark Seoul” attack (2013), can qualify as the group’s first attack.
The 2014 Sony Picture Entertainment attack and a series of SWIFT-targeted campaigns in 2015-2016 (especially the 2016 Bangladesh Bank heist) are among the significant attacks linked to the Lazarus group.
The ‘Wannacry’ ransomware attack in 2017—the biggest ransomware attack to date—affected 300,000 systems across 150 countries.
The “Operation AppleJeus” attack was discovered in 2018 but has been ongoing since at least 2017, targeting cryptocurrency users. Another financially motivated attack is the “FastCash” operation, founded in 2018 but has been ongoing since at least 2016. “FastCash” is a series of attacks targeting (Automated Teller Machines) ATMs of various banks in several countries.
Lazarus group conducted several campaigns in 2020, including attacks on pharmaceutical companies, “Operation ThreatNeddle” against the defense and security sector, “Operation In(ter)ception” against military and aerospace firms, particularly in Europe, and “Operation Dreamjob” against multiple individuals globally in the defense industry and various governmental organizations using social media.
In 2022, the Lazarus group targeted energy providers around the world. The campaign involved the exploitation of the vulnerability in VMware Horizon to gain initial access. 2022 cryptocurrency attacks also drew attention.
Recent Attacks of the Lazarus Group
As the concern of the entire world, the Covid-19 pandemic has also been on the Lazarus group’s agenda, and they targeted pharmaceutical corporations. In 2020, the group attacked pharmaceutical companies and research facilities working on Covid-19 vaccines. Lazarus group members attempted to steal crucial information about the vaccine development process by posing as medical professionals and contacting pharmaceutical business personnel with messages that contained malicious attachments.
The “Dream Job” operation from 2020 reappeared in 2022. The group specifically used social media attacks with fraudulent job offers for researchers working for chemical and information security companies.
Another recurring campaign was “Operation AppleJeus.” The U.S. government published an advisory attributing the cryptocurrency stealing campaign “AppleJeus” to the Lazarus Group (AA21-048A) in 2021. In 2022, cryptocurrency attacks continued to increase. The group targeted organizations in the finance industry with phishing emails containing malware that was used to steal cryptocurrency.
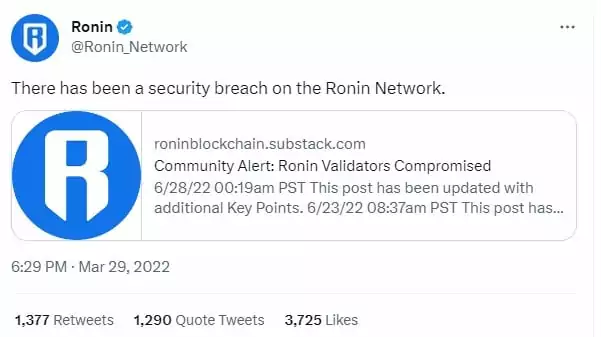
On April 12, 2022, the U.S. Treasury Department accused the Lazarus group of carrying out the “Ronin Bridge” attack, the largest cryptocurrency attack ever, and held them responsible for a $620 million Ethereum heist.
On April 18, 2022, The FBI, CISA, and the Department of the Treasury published a joint Cybersecurity Advisory highlighting the cyber threat associated with bitcoin thefts and techniques utilized by Lazarus group as a North Korean state-sponsored advanced persistent threat (AA22-108A). In addition, the FBI, in its statement on February 6, 2023, claimed the Lazarus group was responsible for “Harmony’s Horizon Bridge Currency Theft” and $100M heist.
Lazarus and ScarCruft Breach Leading Missile Manufacturer NPO Mash
North Korean state-backed hackers breached Russia’s leading missile manufacturer, NPO Mashinostroyeniya (NPO Mash). The breach has been attributed to at least two distinct North Korean nation-state threat groups, including Lazarus. The attackers maintained their access for several months before discovery.
NPO Mash, renowned for its contribution to Soviet missile development, was founded during World War II. The manufacturer faced sanctions after Russia’s annexation of Crimea in 2014. Nowadays, Russia employs missiles produced by NPO Mash to target Ukraine.
The full impact of the breach and Pyongyang’s use of compromised information is uncertain. However, it underscores potential tensions between North Korea and its close ally.
The Possible Motive Behind the NPO Mash Cyberattack
The hack was linked to two North Korean cyberespionage groups: ScarCruft, for breaching the email server, and the notorious Lazarus, for implanting backdoors into systems. SentinelLabs researchers found that the incident began in late 2021 and lasted until May of the following year.
Researchers highlighted NPO Mash’s appeal as a target for nation-state hackers due to its possession of highly classified intellectual property associated with sensitive missile technology.
The breach is described as a “highly desirable strategic espionage mission” to support North Korea’s contentious missile program, as researchers suggest that the cyberattack could likely serve as a covert means for the country to advance its missile development goals.
OpenCarrot Backdoor and ScarCruft Compromise
In May 2022, the company found a suspicious file in its systems, later identified as a version of the OpenCarrot backdoor linked to Lazarus.
This OpenCarrot variant comes with capabilities like reconnaissance, file/process manipulation, and reconfiguration with connectivity features. Additionally, SentinelLabs found ScarCruft compromising Mash’s Linux email server.
ScarCruft is linked to North Korea’s state activities, focusing on high-value individuals. In contrast, Lazarus is known for cryptocurrency heists, allegedly amassing over $2 billion. It’s unclear if the groups collaborated, but this attack indicates possible resource sharing.
FBI Warns Of Lazarus Plan To Cash Out $40 Million In Stolen Cryptocurrency
The FBI has issued a warning indicating that individuals affiliated with the Lazarus Group are preparing to convert stolen cryptocurrency, potentially valued at over $40 million, into cash.
This announcement comes after the FBI’s tracking of around 1,580 bitcoins, taken in previous cryptocurrency heists, to six specific cryptocurrency wallets.
The agency has listed these wallet addresses and urged cryptocurrency companies to carefully analyze blockchain data and take steps to prevent transactions involving these addresses:
- 3LU8wRu4ZnXP4UM8Yo6kkTiGHM9BubgyiG
- 39idqitN9tYNmq3wYanwg3MitFB5TZCjWu
- 3AAUBbKJorvNhEUFhKnep9YTwmZECxE4Nk
- 3PjNaSeP8GzLjGeu51JR19Q2Lu8W2Te9oc
- 3NbdrezMzAVVfXv5MTQJn4hWqKhYCTCJoB
- 34VXKa5upLWVYMXmgid6bFM4BaQXHxSUoL
VMConnect Campaign Unveiled: Lazarus Group is the Culprit
In early August, researchers uncovered the VMConnect campaign, which featured roughly two dozen malicious Python packages on the Python Package Index (PyPI). These packages included backdoors and info-stealing capabilities, masquerading as popular open-source Python tools like vConnector, eth-tester, and databases.
Recently, researchers identified three more malicious Python packages tied to the VMConnect campaign – tablediter, request-plus, and requestspro, attributing this malicious activity to the Lazarus Group.
About the New Malicious PyPI Packages
To conceal these malicious PyPI packages, the threat actors used typosquatting, copied the description of legitimate packages, and updated package names in the fake packages’ documentation references accordingly.
tablediter:
One of the Python packages researchers identified is tablediter. This package mimics “prettytable,” a Python tool for visually appealing table printing, boasting over 9 million monthly downloads. Interestingly, the malicious functionality within tablediter remains dormant during installation; it activates only when utilized in a project. Researchers found that the decrypted code’s functionality closely resembles what was extracted from a previous malicious package in the VMConnect campaign.
request-plus, requestspro:
The packages named request-plus and requestspro target the highly popular requests library on PyPI. Requests is an HTTP library that garners thousands of monthly downloads and over 2.3 million dependencies. The attackers duplicated the files from the legitimate requests package within their fake packages. Furthermore, just like with tablediter, these packages were meticulously crafted to evade detection, both pre and post-installation.
For more information about these packages, and their IoCs, refer here.
For a deeper understanding of the threat posed by malicious packages to DevOps environments, we invite you to explore our related blog post.
How Did Researchers Attribute This Campaign to Lazarus?
Researchers have uncovered py_QRcode, a package featuring a builder.py file with notably similar malicious functionality to the VMConnect package. Both manipulate file paths based on architecture, employ a base64-encoded variable for the next-level payload, and share similar code for decoding and local file writing.
JPCERT/CC previously published a blog about py_QRcode, attributing it to DangerousPassword, a Lazarus subgroup. Moreover, the py_QRcode package mirrors QRLog’s functionality, as outlined in this research. Both QRLog and py_QRcode malware samples utilize the same C2 domain. Mauro Eldritch, the researcher who discovered the malicious QRLog package, shared his findings with cybersecurity firm Crowdstrike, which confidently attributed the malware to Labyrinth Chollima, another Lazarus subgroup.
These attributions, along with shared code similarities between the VMConnect campaign and JPCERT/CC’s research, lead researchers to connect both attacks to the Lazarus Group.
Lazarus Uses Log4Shell in Operation Blacksmith, Deploys New Malware: NineRAT, DLRAT, and BottomLoader
Lazarus has been observed exploiting the Log4Shell RCE vulnerability (CVE-2021-44228) in a recent campaign, deploying three new malware written in DLang: remote access trojans NineRAT and DLRAT, and a malware downloader named BottomLoader.
Cisco Talos has noted a significant change in the tactics of the Lazarus group. In the last eighteen months, Talos has revealed three distinct remote access trojans developed using ‘uncommon’ technologies such as QtFramework, PowerBasic, and most recently in this campaign, DLang.
In the campaign named “Operation Blacksmith,” Lazarus targets manufacturing, agricultural, and physical security companies. According to the researchers, the campaign includes ongoing opportunistic targeting of global enterprises that publicly host and expose vulnerable infrastructure to n-day vulnerability exploitation, like the Log4j vulnerability.
NineRAT:
NineRAT utilizes the Telegram API for C2 communication, facilitating the transfer of files and evasion of detection. This RAT also employs a dropper, aiding threat actors in establishing persistence and executing additional binaries. The commands associated with NineRAT are as follows:
| /info | Gather preliminary information about the infected system. |
| /setmtoken | Set a token value. |
| /setbtoken | Set a new Bot token. |
| /setinterval | Set time interval between malware polls to the Telegram channel. |
| /setsleep | Set a time period for which the malware should sleep/lie dormant. |
| /upgrade | Upgrade to a new version of the implant. |
| /exit | Exit execution of the malware. |
| /uninstall | Uninstall self from the endpoint. |
| /sendfile | Send a file to the C2 server from the infected endpoint. |
DLRAT:
DLRAT is a downloader RAT that Lazarus can utilize to deploy additional malware and retrieve commands from the C2. Upon infiltrating a device, DLRAT executes hard-coded commands for reconnaissance, collecting system information, and exfiltrates it to the C2 server.
Researchers discovered that the session information ID used by DLRAT in its communication with the C2 server is “23wfow02rofw391ng23,” same as a value identified in a previous research into MagicRAT.
The C2 reply includes the external IP address of the implant. The malware recognizes specific command codes/names sent by the C2 to execute actions on the infected system.
| deleteme | Delete itself from the system using a BAT file. |
| download | Download files from a specified remote location. |
| rename | Rename files on the system. |
| iamsleep | Instructs the implant to go to sleep for a specified amount of time. |
| upload | Upload files to C2. |
| showurls | Empty command (Not implemented yet). |
BottomLoader:
BottomLoader is a malware downloader that retrieves and executes next-stage payloads from a remote host, like HazyLoad. Researchers note that it can download the payload from a hardcoded remote URL and upload files to the C2 using PowerShell commands. Additionally, BottomLoader can establish persistence for newer versions or new payloads by modifying the Startup directory.
Lazarus’ Attack Scheme in ‘Operation Blacksmith’ Campaign
In ‘Operation Blacksmith,’ Lazarus initiates access by exploiting the Log4j vulnerability discovered in 2021. Although fixed, the vulnerability continues to pose a threat, with Lazarus sub-groups extensively exploiting it for malicious activities. The threat actor targets VMWare Horizon servers exposed to the public, utilizing a vulnerable Log4j logging library version.
After exploiting the vulnerability, Lazarus establishes persistent access using the HazyLoad proxy tool, runs reconnaissance commands, creates admin-privileged user accounts, and deploys credential-stealing tools such as ProcDump and MimiKatz. Microsoft previously identified HazyLoad in Lazarus attacks exploiting a critical security vulnerability in JetBrains TeamCity (CVE-2023-42793). HazyLoad is downloaded and executed by the loader malware known as BottomLoader.
NineRAT is launched in the second phase, initially observed in use by Lazarus as early as March 2023. Upon activation, NineRAT receives commands via its Telegram-based C2 channel, enabling the fingerprinting of infected systems. Researchers suggest that re-fingerprinting indicates that data collected by Lazarus through NineRAT may be shared with other APT groups, residing in a different repository from the initial fingerprint data collected during Lazarus’ initial access.
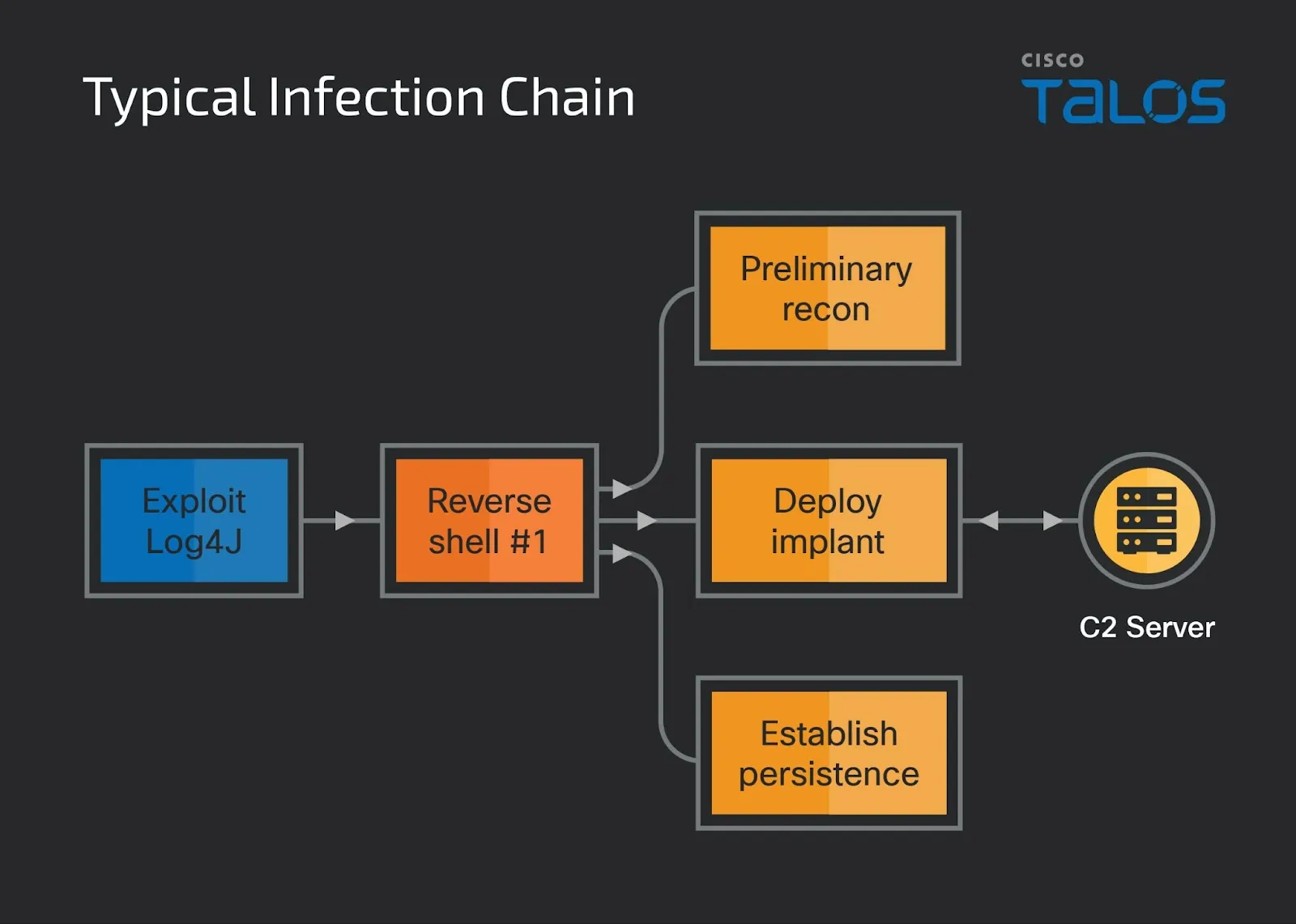
Operation Blacksmith’s infection Chain (Cisco Talos)
Additionally, Talos notes overlap between Lazarus’ ‘Operation Blacksmith’ and the North Korean state-sponsored group Onyx Sleet (PLUTIONIUM), also known as the Andariel APT group. Onyx Sleet is widely considered an APT sub-group under the Lazarus umbrella, exhibiting consistent TTPs.
More information about the Operation Blacksmith campaign and the IOCs for NineRAT, DLRAT, BottomLoader, HazyLoad, and network-related indicators are accessible here.
How Can SOCRadar Help?
Lazarus group has been active for over a decade and has launched attacks in various industries. In their attacks, they have shown high proficiency and flexibility, utilizing custom-built and publicly accessible tools and exploiting various vulnerabilities to achieve their goals. Due to its capabilities and operations, the group is currently one of the most powerful North Korean threat actors.
Reviewing the cases reveals that the group typically uses phishing attacks to gain initial access. In particular, spear phishing attacks against the defense and aerospace sector and ‘dreamjob’ attacks against security researchers, which include fake job offers, make it necessary for companies in these sectors to be sensitive about the cybersecurity awareness of their employees.
SOC Tools on SOCRadar XTI Labs provide a free analysis of suspicious emails.
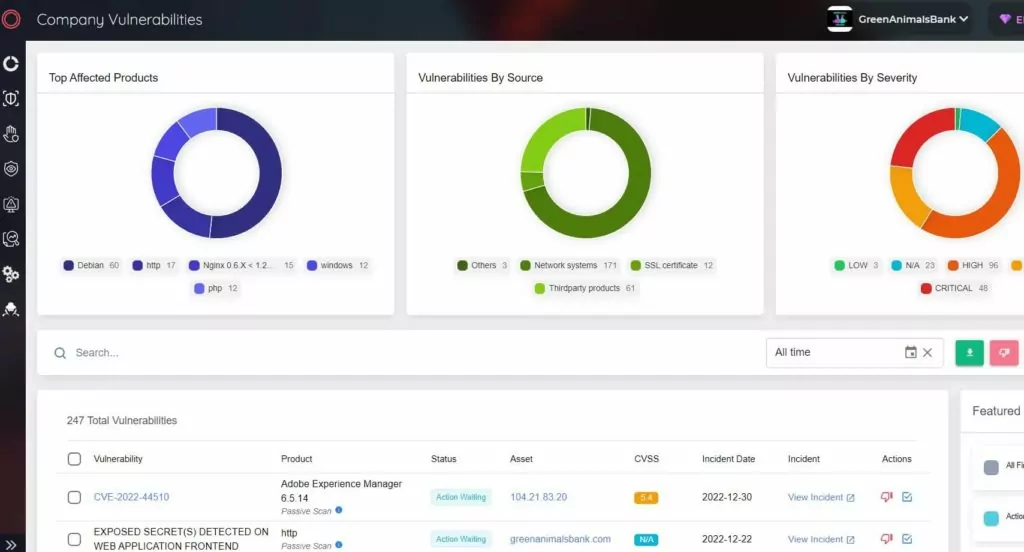
Lazarus group effectively exploits some well-known system vulnerabilities in their numerous attacks. SOCRadar Extended Threat Intelligence provides an Attack Surface Management (ASM) solution for continuous discovery, inventory, classification, and prioritization with real-time monitoring to help gain comprehensive visibility into external-facing digital assets. Security teams can keep track of the vulnerabilities in the network using the SOCRadar XTI ASM solution. Understanding which vulnerabilities exist in the company can help to minimize the attack surface that nation-state threat actors may exploit.
Lazarus group frequently uses supply-chain attacks. SOCRadar XTI provides organizations 360-degree visibility across the entire digital ecosystem by including third-party/supply chain partners in their digital footprint.
Appendixes
Appendix 1.
MITRE ATT&CK Techniques
| Techniques | Name |
| T1134.002 | Access Token Manipulation: Create Process with Token |
| T1087.002 | Account Discovery: Domain Account |
| T1098 | Account Manipulation |
| T1583.001 | Acquire Infrastructure: Domains |
| T1583.004 | Acquire Infrastructure: Server |
| T1583.006 | Acquire Infrastructure: Web Services |
| T1557.001 | Adversary-in-the-Middle: LLMNR/NBT-NS Poisoning and SMB Relay |
| T1071.001 | Application Layer Protocol: Web Protocols |
| T1010 | Application Window Discovery |
| T1560 | Archive Collected Data |
| T1560.002 | Archive via Library |
| T1560.003 | Archive via Custom Method |
| T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| T1547.009 | Boot or Logon Autostart Execution: Shortcut Modification |
| T1110 | Brute Force |
| T1110.003 | Password Spraying |
| T1059.001 | Command and Scripting Interpreter: PowerShell |
| T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| T1059.005 | Command and Scripting Interpreter: Visual Basic |
| T1584.001 | Compromise Infrastructure: Domains |
| T1584.004 | Compromise Infrastructure: Server |
| T1543.003 | Create or Modify System Process: Windows Service |
| T1485 | Data Destruction |
| T1132.001 | Data Encoding: Standard Encoding |
| T1005 | Data from Local System |
| T1001.003 | Data Obfuscation: Protocol Impersonation |
| T1074.001 | Data Staged: Local Data Staging |
| T1491.001 | Defacement: Internal Defacement |
| T1140 | Deobfuscate/Decode Files or Information |
| T1587.001 | Develop Capabilities: Malware |
| T1561.001 | Disk Wipe: Disk Content Wipe |
| T1561.002 | Disk Wipe: Disk Structure Wipe |
| T1189 | Drive-by Compromise |
| T1573.001 | Encrypted Channel: Symmetric Cryptography |
| T1585.001 | Establish Accounts: Social Media Accounts |
| T1585.002 | Establish Accounts: Email Accounts |
| T1048.003 | Exfiltration Over Alternative Protocol: Exfiltration Over Unencrypted Non-C2 Protocol |
| T1041 | Exfiltration Over C2 Channel |
| T1567.002 | Exfiltration Over Web Service: Exfiltration to Cloud Storage |
| T1203 | Exploitation for Client Execution |
| T1008 | Fallback Channels |
| T1083 | File and Directory Discovery |
| T1589.002 | Gather Victim Identity Information: Email Addresses |
| T1591 | Gather Victim Org Information |
| T1591.004 | Identify Roles |
| T1564.001 | Hide Artifacts: Hidden Files and Directories |
| T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| T1574.013 | Hijack Execution Flow: KernelCallbackTable |
| T1562.001 | Impair Defenses: Disable or Modify Tools |
| T1562.004 | Impair Defenses: Disable or Modify System Firewall |
| T1070 | Indicator Removal |
| T1070.003 | Clear Command History |
| T1070.004 | File Deletion |
| T1070.006 | Timestomp |
| T1202 | Indirect Command Execution |
| T1105 | Ingress Tool Transfer |
| T1056.001 | Input Capture: Keylogging |
| T1534 | Internal Spearphishing |
| T1036 | Masquerading |
| T1036.003 | Rename System Utilities |
| T1036.004 | Masquerade Task or Service |
| T1036.005 | Match Legitimate Name or Location |
| T1104 | Multi-Stage Channels |
| T1106 | Native API |
| T1046 | Network Service Discovery |
| T1571 | Non-Standard Port |
| T1027 | Obfuscated Files or Information |
| T1027.002 | Software Packing |
| T1027.007 | Dynamic API Resolution |
| T1588.002 | Obtain Capabilities: Tool |
| T1588.003 | Obtain Capabilities: Code Signing Certificates |
| T1588.004 | Obtain Capabilities: Digital Certificates |
| T1566.001 | Phishing: Spearphishing Attachment |
| T1566.002 | Phishing: Spearphishing Link |
| T1566.003 | Phishing: Spearphishing via Service |
| T1542.003 | Pre-OS Boot: Bootkit |
| T1057 | Process Discovery |
| T1055.001 | Process Injection: Dynamic-link Library Injection |
| T1090.001 | Proxy: Internal Proxy |
| T1090.002 | Proxy: External Proxy |
| T1012 | Query Registry |
| T1620 | Reflective Code Loading |
| T1021.001 | Remote Services: Remote Desktop Protocol |
| T1021.002 | Remote Services: SMB/Windows Admin Shares |
| T1021.004 | Remote Services: SSH |
| T1053.005 | Scheduled Task/Job: Scheduled Task |
| T1593.001 | Search Open Websites/Domains: Social Media |
| T1489 | Service Stop |
| T1608.001 | Stage Capabilities: Upload Malware |
| T1608.002 | Stage Capabilities: Upload Tool |
| T1553.002 | Subvert Trust Controls: Code Signing |
| T1218 | System Binary Proxy Execution |
| T1218.005 | Mshta |
| T1218.01 | Regsvr32 |
| T1218.011 | Rundll32 |
| T1082 | System Information Discovery |
| T1614.001 | System Location Discovery: System Language Discovery |
| T1016 | System Network Configuration Discovery |
| T1049 | System Network Connections Discovery |
| T1033 | System Owner/User Discovery |
| T1529 | System Shutdown/Reboot |
| T1124 | System Time Discovery |
| T1221 | Template Injection |
| T1204.001 | User Execution: Malicious Link |
| T1204.002 | User Execution: Malicious File |
| T1078 | Valid Accounts |
| T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| T1102.002 | Web Service: Bidirectional Communication |
| T1047 | Windows Management Instrumentation |
| T1220 | XSL Script Processing |
| T0865 | Spearphishing Attachment |
Appendix 2.
Lazarus Group crypto Ethereum address:
0x098B716B8Aaf21512996dC57EB0615e2383E2f96
0xa0e1c89Ef1a489c9C7dE96311eD5Ce5D32c20E4B
0x3Cffd56B47B7b41c56258D9C7731ABaDc360E073
0x53b6936513e738f44FB50d2b9476730C0Ab3Bfc1
Appendix 3.
IoCs of Wannacry
IP Addresses and Domains
IPv4 197(.)231.221.211
IPv4 128(.)31.0.39
IPv4 149(.)202.160.69
IPv4 46(.)101.166.19
IPv4 91(.)121.65.179
URL hxxp://www(.)btcfrog(.)com/qr/bitcoinpng(.)php?address
URL hxxp://www(.)rentasyventas(.)com/incluir/rk/imagenes(.)html
URL hxxp://www(.)rentasyventas(.)com/incluir/rk/imagenes(.)html?retencion=081525418
URL hxxp://gx7ekbenv2riucmf(.)onion
URL hxxp://57g7spgrzlojinas(.)onion
URL hxxp://xxlvbrloxvriy2c5(.)onion
URL hxxp://76jdd2ir2embyv47(.)onion
URL hxxp://cwwnhwhlz52maqm7(.)onion
URL hxxp://197.231.221(.)211 Port:9001
URL hxxp://128.31.0(.)39 Port:9191
URL hxxp://149.202.160(.)69 Port:9001
URL hxxp://46.101.166(.)19 Port:9090
URL hxxp://91.121.65(.)179 Port:9001
Hashes
https://gist.github.com/Blevene/42bed05ecb51c1ca0edf846c0153974a
| Hash-MD5 | 5a89aac6c8259abbba2fa2ad3fcefc6e |
| Hash-MD5 | 05da32043b1e3a147de634c550f1954d |
| Hash-MD5 | 8e97637474ab77441ae5add3f3325753 |
| Hash-MD5 | c9ede1054fef33720f9fa97f5e8abe49 |
| Hash-MD5 | f9cee5e75b7f1298aece9145ea80a1d2 |
| Hash-MD5 | 638f9235d038a0a001d5ea7f5c5dc4ae |
| Hash-MD5 | 80a2af99fd990567869e9cf4039edf73 |
| Hash-MD5 | c39ed6f52aaa31ae0301c591802da24b |
| Hash-MD5 | db349b97c37d22f5ea1d1841e3c89eb4 |
| Hash-MD5 | f9992dfb56a9c6c20eb727e6a26b0172 |
| Hash-MD5 | 46d140a0eb13582852b5f778bb20cf0e |
| Hash-MD5 | 5bef35496fcbdbe841c82f4d1ab8b7c2 |
| Hash-MD5 | 3c6375f586a49fc12a4de9328174f0c1 |
| Hash-MD5 | 246c2781b88f58bc6b0da24ec71dd028 |
| Hash-MD5 | b7f7ad4970506e8547e0f493c80ba441 |
| Hash-MD5 | 2b4e8612d9f8cdcf520a8b2e42779ffa |
| Hash-MD5 | c61256583c6569ac13a136bfd440ca09 |
| Hash-MD5 | 31dab68b11824153b4c975399df0354f |
| Hash-MD5 | 54a116ff80df6e6031059fc3036464df |
| Hash-MD5 | d6114ba5f10ad67a4131ab72531f02da |
| Hash-MD5 | 05a00c320754934782ec5dec1d5c0476 |
| Hash-MD5 | f107a717f76f4f910ae9cb4dc5290594 |
| Hash-MD5 | 7f7ccaa16fb15eb1c7399d422f8363e8 |
| Hash-MD5 | 84c82835a5d21bbcf75a61706d8ab549 |
| Hash-MD5 | bec0b7aff4b107edd5b9276721137651 |
| Hash-MD5 | 86721e64ffbd69aa6944b9672bcabb6d |
| Hash-MD5 | 509c41ec97bb81b0567b059aa2f50fe8 |
| Hash-MD5 | 8db349b97c37d22f5ea1d1841e3c89eb |
| Hash-SHA1 | 6fbb0aabe992b3bda8a9b1ecd68ea13b668f232e |
| Hash-SHA256 | 0a73291ab5607aef7db23863cf8e72f55bcb3c273bb47f00edf011515aeb5894 |
| Hash-SHA256 | 21ed253b796f63b9e95b4e426a82303dfac5bf8062bfe669995bde2208b360fd |
| Hash-SHA256 | 228780c8cff9044b2e48f0e92163bd78cc6df37839fe70a54ed631d3b6d826d5 |
| Hash-SHA256 | 2372862afaa8e8720bc46f93cb27a9b12646a7cbc952cc732b8f5df7aebb2450 |
| Hash-SHA256 | 2ca2d550e603d74dedda03156023135b38da3630cb014e3d00b1263358c5f00d |
| Hash-SHA256 | 3ecc7b1ee872b45b534c9132c72d3523d2a1576ffd5763fd3c23afa79cf1f5f9 |
| Hash-SHA256 | 43d1ef55c9d33472a5532de5bbe814fefa5205297653201c30fdc91b8f21a0ed |
| Hash-SHA256 | 49fa2e0131340da29c564d25779c0cafb550da549fae65880a6b22d45ea2067f |
| Hash-SHA256 | 4a468603fdcb7a2eb5770705898cf9ef37aade532a7964642ecd705a74794b79 |
| Hash-SHA256 | 616e60f031b6e7c4f99c216d120e8b38763b3fafd9ac4387ed0533b15df23420 |
| Hash-SHA256 | 66334f10cb494b2d58219fa6d1c683f2dbcfc1fb0af9d1e75d49a67e5d057fc5 |
| Hash-SHA256 | 8b52f88f50a6a254280a0023cf4dc289bd82c441e648613c0c2bb9a618223604 |
| Hash-SHA256 | 8c3a91694ae0fc87074db6b3e684c586e801f4faed459587dcc6274e006422a4 |
| Hash-SHA256 | aae9536875784fe6e55357900519f97fee0a56d6780860779a36f06765243d56 |
| Hash-SHA256 | b9c5d4339809e0ad9a00d4d3dd26fdf44a32819a54abf846bb9b560d81391c25 |
| Hash-SHA256 | ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa |
| Hash-SHA256 | f7c7b5e4b051ea5bd0017803f40af13bed224c4b0fd60b890b6784df5bd63494 |
| Hash-SHA256 | 09a46b3e1be080745a6d8d88d6b5bd351b1c7586ae0dc94d0c238ee36421cafa |
| Hash-SHA256 | 149601e15002f78866ab73033eb8577f11bd489a4cea87b10c52a70fdf78d9ff |
| Hash-SHA256 | 190d9c3e071a38cb26211bfffeb6c4bb88bd74c6bf99db9bb1f084c6a7e1df4e |
| Hash-SHA256 | 24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c |
| Hash-SHA256 | 2584e1521065e45ec3c17767c065429038fc6291c091097ea8b22c8a502c41dd |
| Hash-SHA256 | 4186675cb6706f9d51167fb0f14cd3f8fcfb0065093f62b10a15f7d9a6c8d982 |
| Hash-SHA256 | 593bbcc8f34047da9960b8456094c0eaf69caaf16f1626b813484207df8bd8af |
| Hash-SHA256 | 5ad4efd90dcde01d26cc6f32f7ce3ce0b4d4951d4b94a19aa097341aff2acaec |
| Hash-SHA256 | 7c465ea7bcccf4f94147add808f24629644be11c0ba4823f16e8c19e0090f0ff |
| Hash-SHA256 | 9b60c622546dc45cca64df935b71c26dcf4886d6fa811944dbc4e23db9335640 |
| Hash-SHA256 | 9fb39f162c1e1eb55fbf38e670d5e329d84542d3dfcdc341a99f5d07c4b50977 |
| Hash-SHA256 | b47e281bfbeeb0758f8c625bed5c5a0d27ee8e0065ceeadd76b0010d226206f0 |
| Hash-SHA256 | b66db13d17ae8bcaf586180e3dcd1e2e0a084b6bc987ac829bbff18c3be7f8b4 |
| Hash-SHA256 | c365ddaa345cfcaff3d629505572a484cff5221933d68e4a52130b8bb7badaf9 |
| Hash-SHA256 | d8a9879a99ac7b12e63e6bcae7f965fbf1b63d892a8649ab1d6b08ce711f7127 |
| Hash-SHA256 | f8812f1deb8001f3b7672b6fc85640ecb123bc2304b563728e6235ccbe782d85 |
| Hash-SHA256 | 11d0f63c06263f50b972287b4bbd1abe0089bc993f73d75768b6b41e3d6f6d49 |
| Hash-SHA256 | 16493ecc4c4bc5746acbe96bd8af001f733114070d694db76ea7b5a0de7ad0ab |
| Hash-SHA256 | 6bf1839a7e72a92a2bb18fbedf1873e4892b00ea4b122e48ae80fac5048db1a7 |
| Hash-SHA256 | b3c39aeb14425f137b5bd0fd7654f1d6a45c0e8518ef7e209ad63d8dc6d0bac7 |
| Hash-SHA256 | e14f1a655d54254d06d51cd23a2fa57b6ffdf371cf6b828ee483b1b1d6d21079 |
| Hash-SHA256 | e8450dd6f908b23c9cbd6011fe3d940b24c0420a208d6924e2d920f92c894a96 |
Appendix 4.
IoCs of BADCALL
| Indicator | Description |
|---|---|
| d1f3b9372a6be9c02430b6e4526202974179a674ce94fe22028d7212ae6be9e7 | Proxy server (32-bit EXE) |
| 4257bb11570ed15b8a15aa3fc051a580eab5d09c2f9d79e4b264b752c8e584fc | Proxy server (32-bit DLL) |
| 93e13ffd2a2f1a13fb9a09de1d98324f75b3f0f8e0c822857ed5ca3b73ee3672 | Implant loader (32-bit EXE) |
| da353b2845a354e1a3f671e4a12198e2c6f57a377d02dfaf90477869041a044f | Decrypted implant (Zip Archive) |
| 91650e7b0833a34abc9e51bff53cc05ef333513c6be038df29929a0a55310d9c | Proxy server (32-bit DLL) |
| edd2aff8fad0c76021adc74fe3cb3cb1a02913a839ad0f2cf31fdea8b5aa8195 | Remote access tool (Android APK) |
Appendix 5.
IoCs of FastCash
| Indicator | Description |
|---|---|
| D465637518024262C063F4A82D799A4E40FF3381014972F24EA18BC23C3B27EE | Trojan.Fastcash Injector |
| CA9AB48D293CC84092E8DB8F0CA99CB155B30C61D32A1DA7CD3687DE454FE86C | Trojan.Fastcash DLL |
| 10AC312C8DD02E417DD24D53C99525C29D74DCBC84730351AD7A4E0A4B1A0EBA | Trojan.Fastcash DLL |
| 3A5BA44F140821849DE2D82D5A137C3BB5A736130DDDB86B296D94E6B421594C | Trojan.Fastcash DLL |




































