
How to Overcome Dark Web Risks in Your Industry – CISO Edition
The dark web has evolved into a vast and thriving marketplace for stolen data, illicit services, and cybercrime tools. For Chief Information Security Officers (CISOs), addressing the risks emanating from this hidden realm is no longer optional—it is a necessity. Industries from finance to healthcare face unique challenges as cybercriminals exploit dark web platforms to trade stolen information, execute malicious campaigns, and target organizational vulnerabilities.
This article delves into the actionable steps CISOs can take to combat dark web threats, reduce exposure, and secure their organizations from the unseen dangers lurking in the shadows.
Understanding the Threat Landscape
The dark web serves as a breeding ground for cybercrime, enabling the distribution of stolen data, malware, and tools for cyberattacks. For CISOs, understanding the specific risks to their industry is essential for crafting a defense strategy tailored to evolving threats. Key risks include:
- Data Exposure: Stolen credentials, trade secrets, and sensitive customer data are frequently sold or auctioned on dark web forums, enabling identity theft, fraud, and corporate espionage.
- Reputation Damage: Dark web marketplaces are often hubs for phishing kits and impersonation campaigns targeting brands, leading to customer distrust and financial loss.
- Advanced Malware Distribution: Custom malware and Ransomware-as-a-Service (RaaS) offerings are openly marketed, allowing attackers to deploy highly targeted campaigns with minimal effort.
- Insider Threats: Employees or external contractors may be tempted to sell access credentials, trade secrets, or operational information, compromising an organization’s integrity.
- Industry-Specific Targeting: Threat actors often focus on industries with high-value data, tailoring their attack vectors to exploit sector-specific vulnerabilities, such as healthcare patient records or financial PII.
By identifying these risks and leveraging industry-specific intelligence, CISOs can build a layered defense strategy that includes proactive monitoring of dark web activity, employee education programs, and robust threat detection tools. Proactive measures not only mitigate immediate risks but also strengthen an organization’s resilience against future attacks.
Industries Most Vulnerable to Dark Web Threats
Certain industries face heightened risks from dark web activity due to the value of their data and unique vulnerabilities. Healthcare, finance, public administration, and the information sector are prime targets, as cybercriminals exploit stolen records, credentials, and other assets sold on hidden platforms. CISOs in these sectors must recognize these specific risks and adopt tailored strategies to mitigate breaches, safeguard sensitive data, and strengthen their defenses against ever-evolving threats.
Healthcare
Medical records remain highly valuable on the dark web, often fetching premium prices due to the sensitive and exploitable nature of the data. Hospitals, clinics, and healthcare providers continue to be prime targets, facing threats fueled by outdated systems and sprawling repositories of patient information. According to the IBM 2024 Cost of a Data Breach Report, the healthcare industry sustained the highest breach costs of any sector for the 13th consecutive year, with an average cost of $9.77 million per breach.
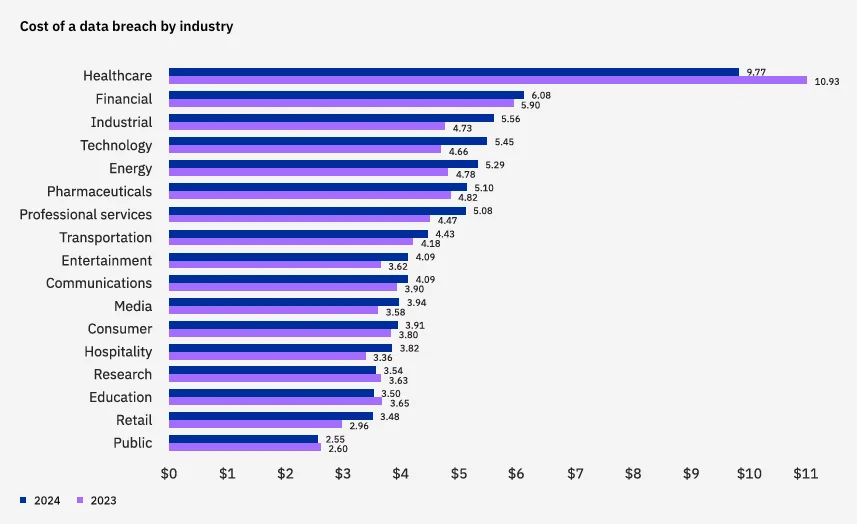
Average cost of data breach in different industries (IBM 2024 Cost of a Data Breach Report)
These high costs stem from regulatory fines, remediation expenses, and long-term reputational damage. Ransomware attacks targeting Electronic Health Records (EHRs) remain a significant threat, often paralyzing healthcare institutions and delaying critical patient care. For CISOs, addressing these risks requires implementing advanced endpoint protection, secure EHR management, and comprehensive dark web monitoring to proactively mitigate threats.
Finance
The financial sector remains a frequent target for cybercriminals, driven by the high value of customer Personally Identifiable Information (PII), payment data, and banking credentials. These assets are commonly sold on dark web marketplaces, enabling identity theft, financial fraud, and corporate espionage.
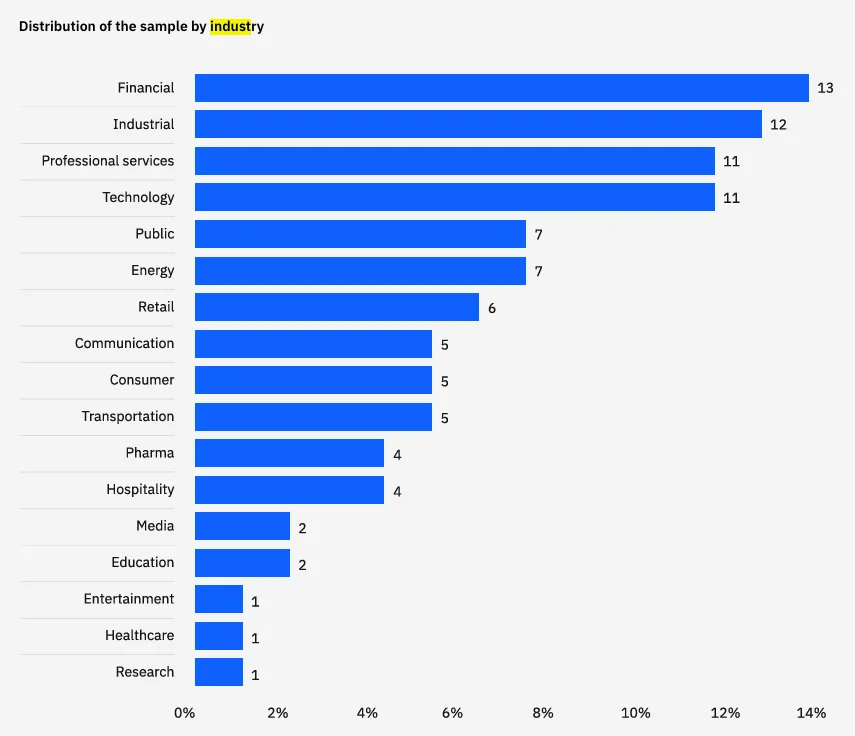
Industry demographics of 604 organizations studied in the IBM 2024 Cost of a Data Breach Report
According to the IBM 2024 Cost of a Data Breach Report, financial services remain one of the top industries impacted by data breaches, with an average cost of $6.08 million per breach, accounting for a significant share of global incidents. Cybercriminals exploit vulnerabilities in banking systems, fintech platforms, and payment processors using phishing, credential theft, and social engineering tactics. CISOs in the financial sector must adopt proactive measures to mitigate these escalating threats.
Public Administration
The public administration sector faces the highest volume of data breaches, making it a prominent target for cybercriminals. According to the 2024 Verizon Data Breach Investigations Report, 41% of breaches in this sector involved external actors, with financially motivated attackers and state-affiliated espionage being significant threats. When error-related breaches are excluded, 67% of external attacks were attributed to organized crime, primarily ransomware campaigns, while 29% involved state-affiliated actors engaging in espionage. Notably, financially motivated attacks saw a slight increase, signaling a growing interest in exploiting government systems for profit.
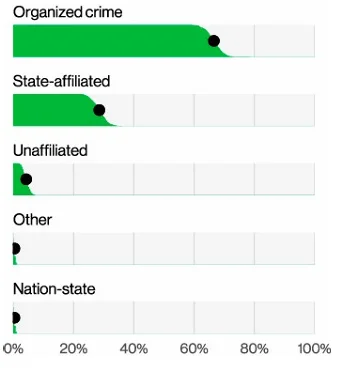
Types of external attacks targeting public administration (2024 Verizon Data Breach Investigations Report)
Information
The information sector continues to face relentless attacks from external hackers, primarily targeting its extensive repositories of valuable data. The 2024 Verizon Data Breach Investigations Report reveals that 79% of breaches in this industry involved external actors, with financial motives driving 87% of incidents and espionage accounting for 14%. System Intrusion, Basic Web Application Attacks, and Social Engineering were the dominant attack patterns, responsible for 79% of breaches. Given this landscape, CISOs in the information sector must focus on strengthening vulnerability management, securing web applications, and implementing robust dark web monitoring to mitigate the risks posed by external threats effectively.
Enhanced Actionable Steps for CISOs to Combat Dark Web Risks
- Continuous Monitoring
- Approach: Deploy real-time monitoring solutions to detect mentions of your organization, leaked credentials, compromised data, or indicators of imminent threats on dark web platforms.
- Solution: Utilize SOCRadar’s Dark Web Monitoring to track threats across forums, marketplaces, and social media channels. SOCRadar scans for references to your brand, employees, or vendors to identify risks proactively.
Monitoring marketplaces with SOCRadar’s Dark Web Monitoring
-
- Benefit: Immediate notifications enable swift response to potential compromises, reducing the risk of significant breaches or reputation damage.
- Enforce Multi-Factor Authentication (MFA)
- Approach: Implement MFA across all critical accounts to add an additional layer of security, ensuring that credentials alone cannot be used to access sensitive systems.
- Solution: SOCRadar’s insights into compromised credentials can help prioritize enforcing MFA in high-risk accounts.
- Key Metric: Track MFA adoption rates within your organization to measure progress and effectiveness.
- Benefit: Reduces the likelihood of account compromise, even if passwords are leaked on the dark web.
- Threat Intelligence Integration
- Approach: Enrich your organization’s threat intelligence by incorporating insights from dark web activity. Analyze data for connections between online chatter and active threats targeting your industry.
- Solution: Leverage SOCRadar’s Extended Threat Intelligence to unify dark web findings with other intelligence sources. Detect malware trends, credential breaches, or potential attack vectors.
- Example: If ransomware targeting your sector is advertised on the dark web, SOCRadar’s real-time intelligence can guide preemptive defense measures.
- Benefit: Proactive insights help organizations prepare for emerging threats before they escalate.
- Employee Awareness
- Approach: Regularly educate employees about phishing schemes, social engineering, and tactics that originate from the dark web to minimize insider vulnerabilities.
- Strategy: Use SOCRadar’s Alarm Management to identify phishing campaigns targeting your organization and simulate similar attacks during employee training sessions.
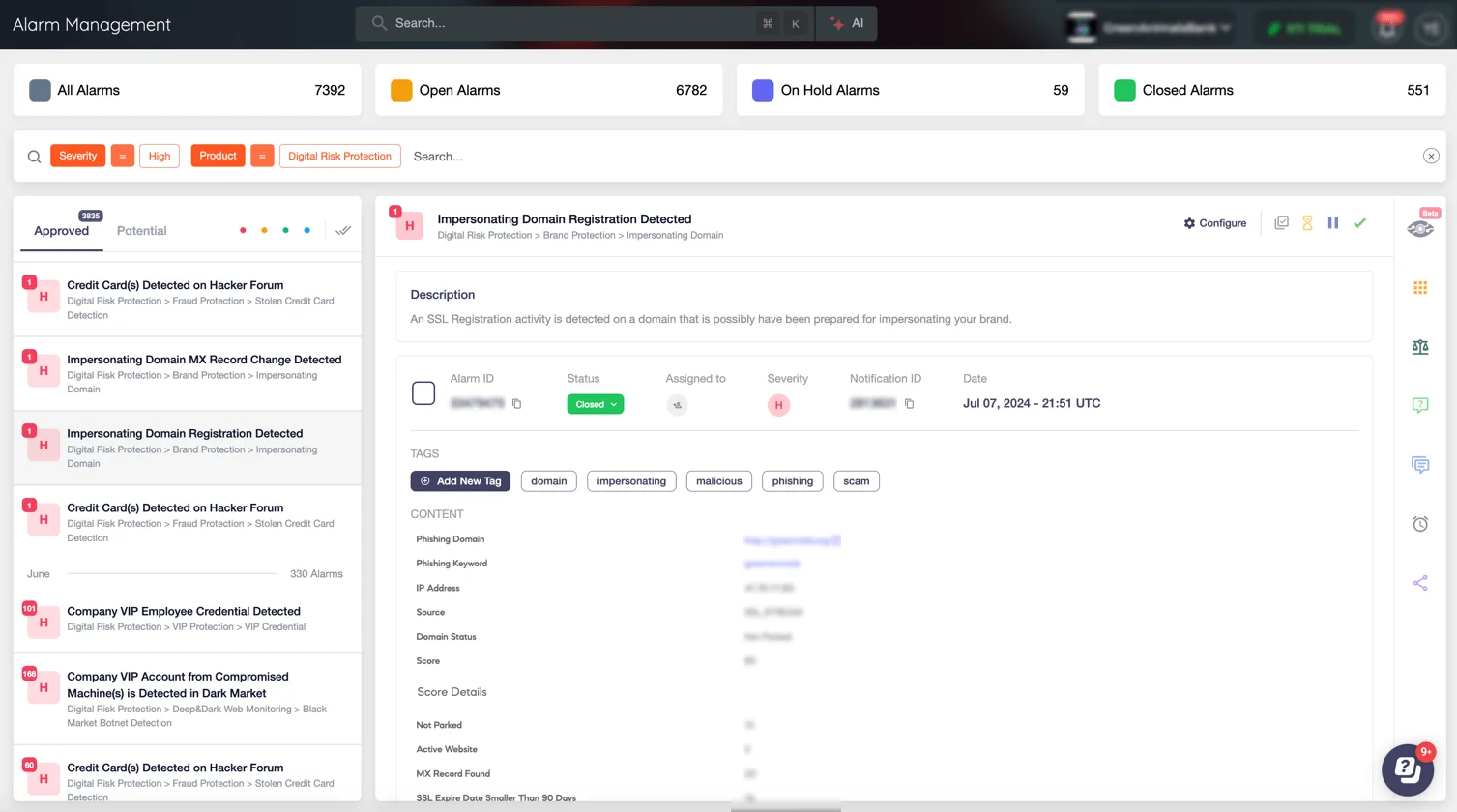
SOCRadar’s Alarm Management
-
- Benefit: Increased employee vigilance and improved ability to identify and report phishing attempts reduces the success rate of social engineering attacks.
- Supply Chain Security
- Approach: Monitor third-party vendors for dark web activity that might signal a compromise in your supply chain.
- Solution: SOCRadar’s Supply Chain Intelligence evaluates third-party risks by scanning for vendor-related threats, such as compromised credentials or leaked proprietary information.
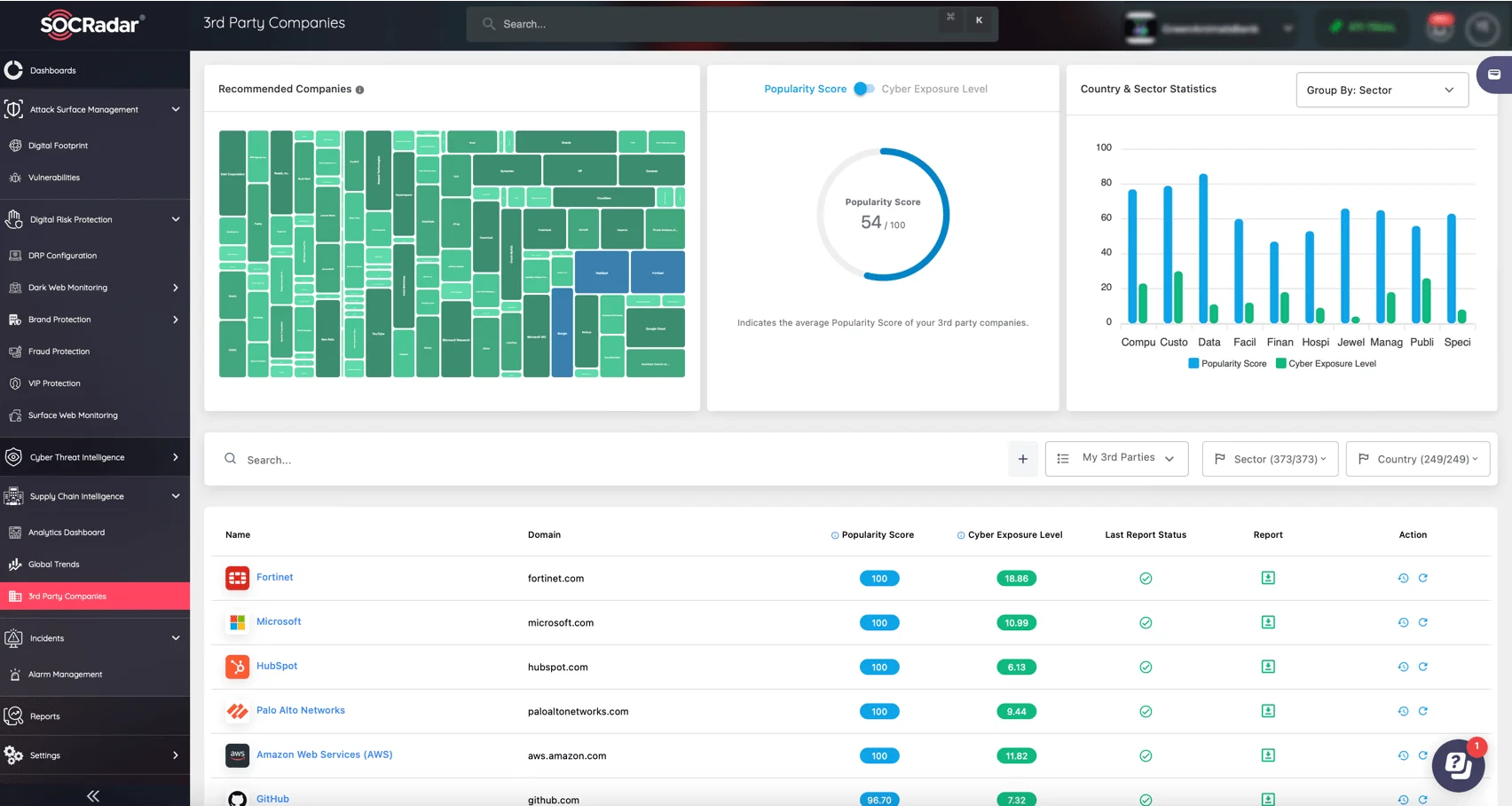
Third-Party Monitoring with SOCRadar’s Supply Chain Intelligence
-
- Benefit: Identifying and mitigating vulnerabilities in your supply chain strengthens your overall security posture, preventing indirect breaches.
- Take Down Malicious Domains
- Approach: Proactively identify and eliminate phishing domains and fake websites that impersonate your organization or customers to mitigate fraud and reputational harm.
- Solution: Utilize SOCRadar’s Integrated Takedown Service to detect and remove fraudulent domains efficiently. This service automates the process, providing end-to-end management of takedown requests, ensuring swift action against malicious domains targeting your organization.
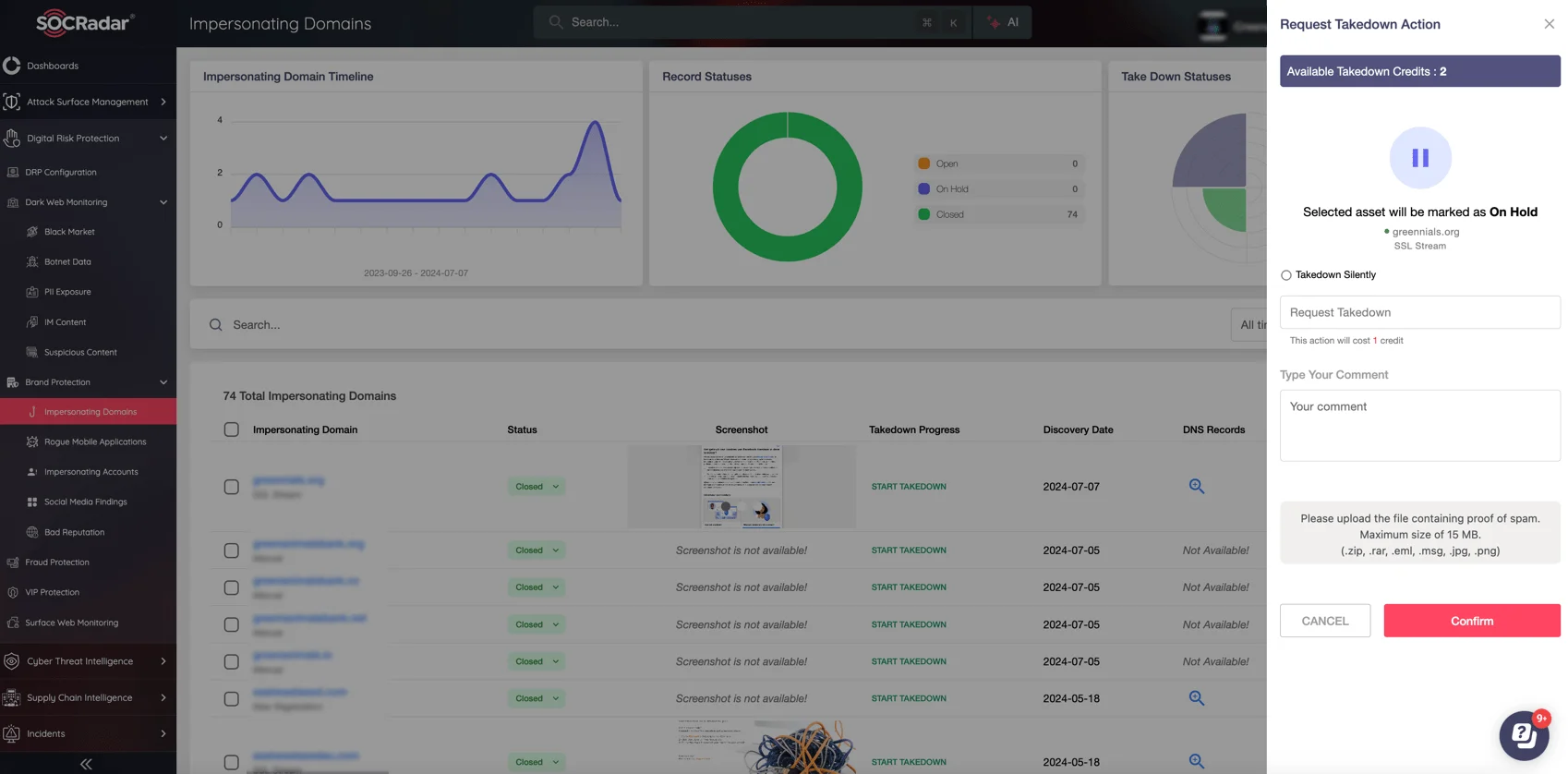
SOCRadar’s Integrated Takedown Service
-
- Benefit: Protects brand integrity and customer trust while reducing the risk of phishing and impersonation attacks. SOCRadar’s streamlined approach ensures quicker resolution with minimal operational disruption.
- Incident Response Planning
- Approach: Develop a comprehensive incident response plan tailored to address dark web-related risks, including breach containment, data recovery, and public communication strategies.
- Solution: Use SOCRadar to inform response strategies with real-time threat intelligence. Access historical data to analyze past threats and refine response measures.
- Benefit: Faster and more coordinated responses minimize the impact of breaches and enable effective recovery.
By incorporating SOCRadar’s capabilities into your cybersecurity framework, you can take the lead in mitigating dark web threats, ensuring your organization remains secure, resilient, and prepared for emerging challenges.
Conclusion
Dark web risks are pervasive across industries, but CISOs can mitigate them through proactive monitoring, employee education, and leveraging threat intelligence. By integrating tools like SOCRadar into your cybersecurity framework, you can identify threats early, respond effectively, and safeguard your organization’s assets.
Staying ahead of dark web threats requires vigilance, adaptability, and a commitment to continuous improvement. With the right strategies and tools, CISOs can transform dark web challenges into opportunities for strengthening their security posture.




































