RomCom Backdoor Attacks Use Zero-Day Exploits in Mozilla and Windows (CVE-2024-9680 & CVE-2024-49039)
Recent research has revealed how the RomCom cyber threat group exploited two zero-day vulnerabilities in Mozilla and Microsoft products to deploy their namesake backdoor. These vulnerabilities, CVE-2024-9680 and CVE-2024-49039, allowed zero-click exploitation, enabling attackers to deliver malicious payloads without user interaction. The campaign leveraged fake websites and a highly sophisticated attack chain to target victims worldwide.
This blog post outlines the details of the exploitation and attack techniques, providing insights to help organizations understand and mitigate such advanced threats.
Details of the Zero-Day Vulnerabilities Exploited by RomCom
RomCom’s recent campaign showcased their advanced exploitation capabilities by chaining two zero-day vulnerabilities in Mozilla and Microsoft Windows products.
The first vulnerability, CVE-2024-9680 (CVSS 9.8), is a critical Use-After-Free flaw in Firefox’s animation timeline feature. This issue allowed attackers to execute arbitrary code in the restricted context of the browser, affecting not only Firefox but also browsers like Thunderbird and Tor.
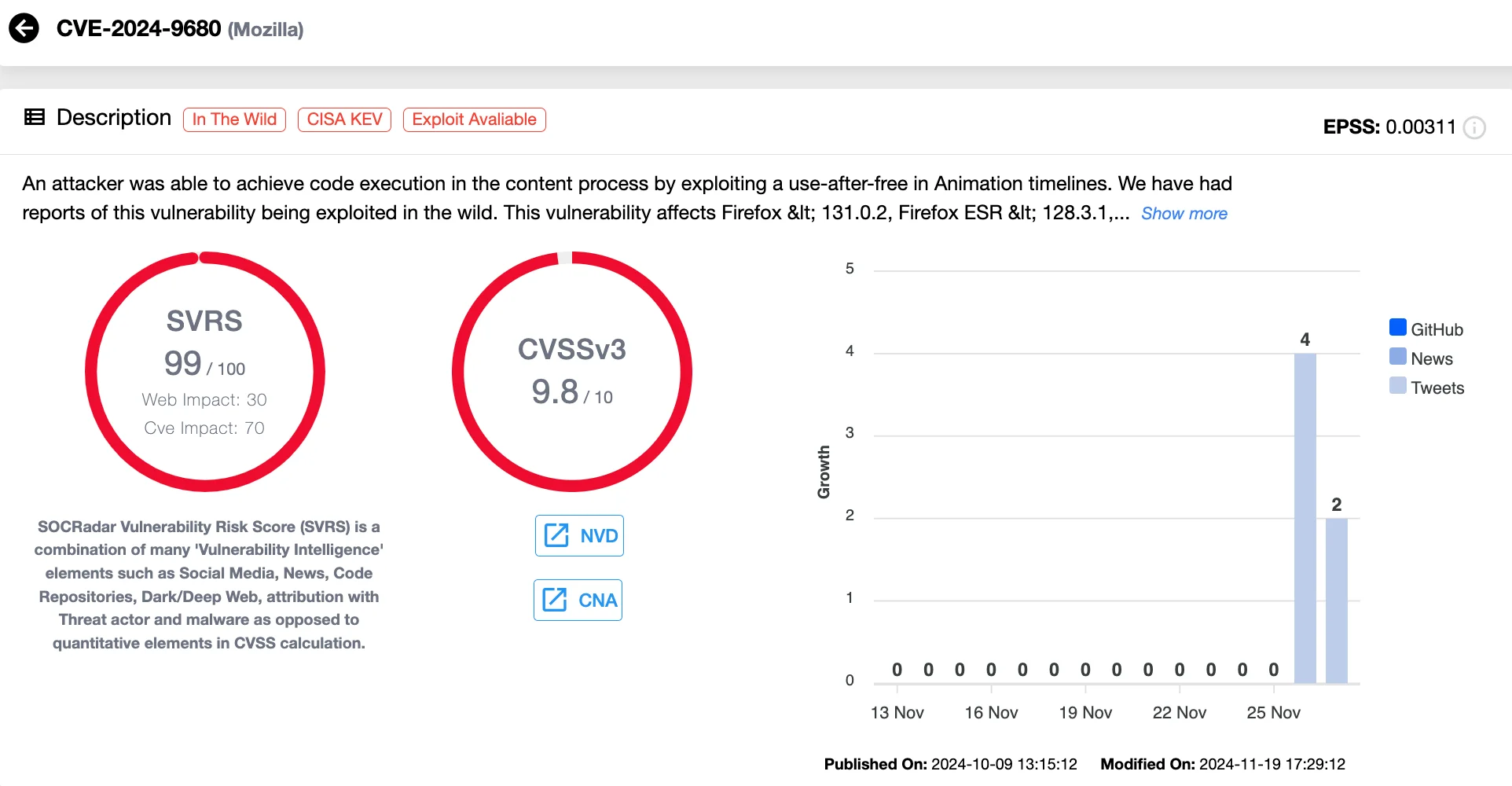
Details of CVE-2024-9680 (SOCRadar Vulnerability Intelligence)
The second vulnerability, CVE-2024-49039 (CVSS 8.8), is an Elevation of Privilege flaw in the Windows Task Scheduler service. By exploiting this vulnerability, attackers bypassed Firefox’s sandbox protections and gained elevated privileges on the victim’s system.
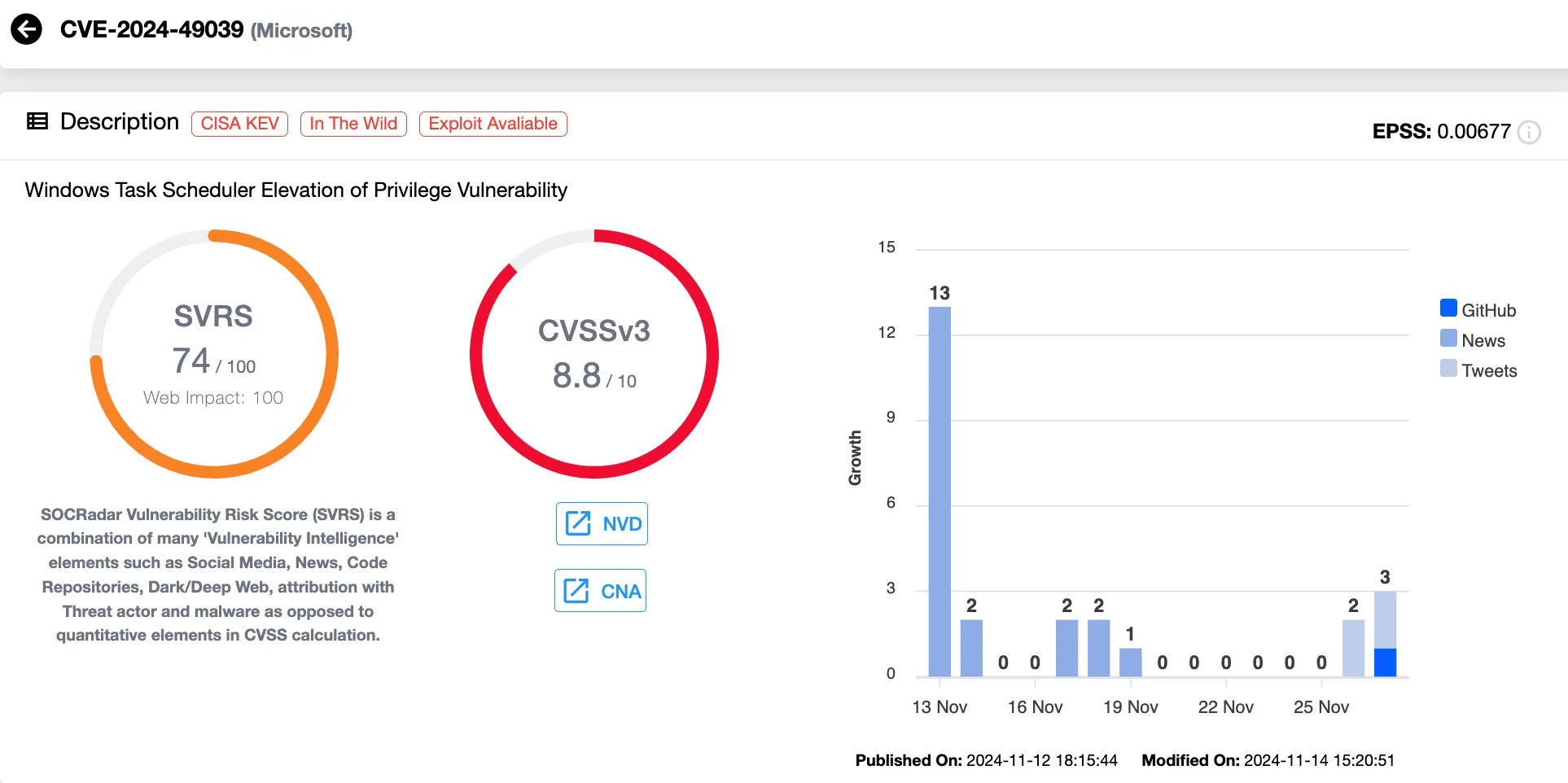
Details of CVE-2024-49039 (SOCRadar Vulnerability Intelligence)
ESET points out that victims simply had to visit a malicious website to trigger the exploit, leading to the installation of the RomCom backdoor and granting attackers full control over compromised systems. Moreover, between October 10 and November 4, 2024, researchers identified most victims of this campaign in Europe and North America, with some regions reporting up to 250 affected targets.
Tracking emerging vulnerabilities and exploit trends is vital to protect your systems. With SOCRadar’s Vulnerability Intelligence module, you gain real-time insights into newly disclosed CVEs and associated threats. This module enables you to:
- Identify critical vulnerabilities that could impact your organization.
- Monitor exploit developments and prioritize patching efforts.
- Stay informed about evolving attack tactics through actionable intelligence.
SOCRadar’s Vulnerability Intelligence
By leveraging Vulnerability Intelligence, you can proactively protect your organization against sophisticated campaigns like RomCom’s.
How RomCom Executes its Attack Chain
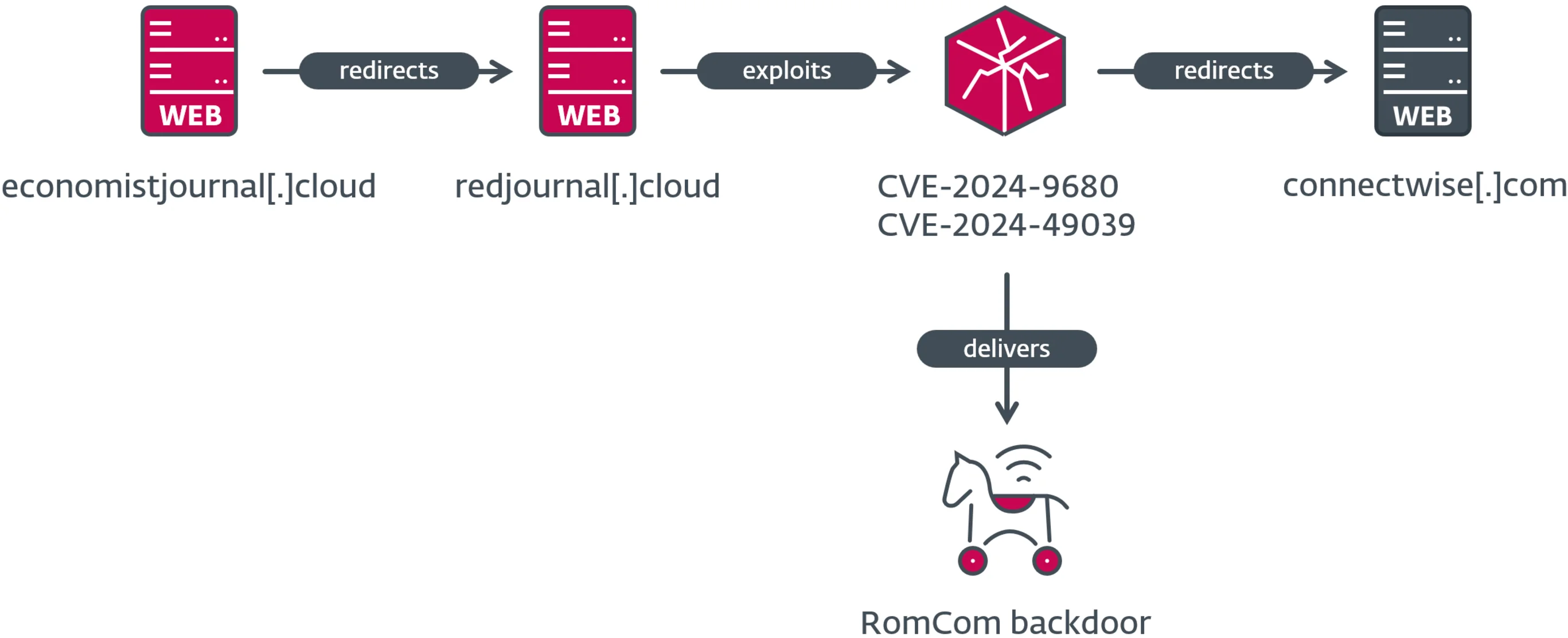
The campaign relied on phishing domains that impersonated legitimate platforms, tricking victims into unknowingly activating the exploit. A detailed description of the attackers’ exploit chain and its various stages is provided below.
1. Fake Domains and Exploit Hosting
RomCom utilized counterfeit domains resembling authentic websites to evade suspicion. Examples include redircorrectiv[.]com, mimicking the newsroom Correctiv, and devolredir[.]com, impersonating remote access provider Devolutions.
These sites hosted the exploit payloads and leveraged a predictable naming pattern, as noticed by researchers, appending terms like ‘redir’ or ‘red’ to legitimate domain names, occasionally altering the TLDs.
SOCRadar’s Brand Protection module is designed to shield your organization from impersonation threats by detecting counterfeit domains like those used in RomCom’s campaign. Additionally, with its Integrated Takedown service, you can quickly act against harmful domains, streamlining threat identification and removal to protect your brand and stakeholders.
2. Zero-Click Exploit Activation
When victims visited these malicious websites using vulnerable browsers, the attack chain executed without any other user interaction. A two-part shellcode facilitated the exploitation:
- Part 1: Retrieved additional malicious components from memory and prepared the system for exploitation.
- Part 2: Deployed Reflective DLL Injection (RDI) to bypass Firefox’s sandbox, enabling privilege escalation and deeper system compromise.
The attack chain (Source: ESET)
3. Stealthy Redirection
After the payload was executed, victims were redirected via JavaScript (using window.location.href) to legitimate websites. This redirection masked malicious activity, delayed detection, and helped maintain the operation’s cover.
4. Deployment of the Backdoor Malware
The RomCom backdoor was staged on Command and Control (C2) servers such as journalctd[.]live, correctiv[.]sbs, and cwise[.]store. Once installed, it granted attackers full control over the compromised system, enabling command execution, data theft, and further malware deployment.
Who is RomCom?
RomCom is a sophisticated cyber threat group with suspected ties to Russia, known for blending espionage with financially motivated attacks. The group, also referred to as Tropical Scorpius, Storm-0978, or UNC2596, has targeted a variety of sectors, including military, government, and political organizations in Ukraine and NATO-affiliated countries.
RomCom’s operations reflect their dual focus on intelligence gathering and cybercrime. By deploying advanced malware like the RomCom backdoor, the group can exfiltrate sensitive data, execute commands, and deliver additional malicious payloads. These activities demonstrate a calculated strategy aimed at both short-term financial gain and long-term espionage objectives.
The RomCom backdoor is a central element of their toolkit, showcasing their ability to adapt to different attack scenarios. Its modular architecture allows it to execute commands, establish persistence, and expand its capabilities through additional modules. These features make RomCom a persistent and versatile threat.
Details about RomCom (SOCRadar Threat Actor Intelligence)
Monitoring the activities of adversaries like RomCom is vital to staying ahead of emerging threats. SOCRadar’s Threat Actor Intelligence, under the Cyber Threat Intelligence module, provides detailed insights into attackers’ Tactics, Techniques, and Procedures (TTPs). Combined with the Attack Surface Management (ASM) feature, you can track vulnerabilities and ensure your digital assets remain protected against evolving attack vectors.
Indicators of Compromise (IOCs)
To defend against RomCom’s campaign, identifying key Indicators of Compromise (IOCs) is essential. These include malicious domains, Command and Control (C2) servers, and file names related to the attacks.
Files:
| Filename | SHA1 Hash |
| utils.js | A4AAD0E2AC1EE0C8DD25968FA4631805689757B6 |
| main-tor.js | CA6F8966A3B2640F49B19434BA8C21832E77A031 |
| main-128.js | 21918CFD17B378EB4152910F1246D2446F9B5B11 |
| main-129.js | 703A25F053E356EB6ECE4D16A048344C55DC89FD |
| PocLowIL.dll | ABB54C4751F97A9FC1C9598FED1EC9FB9E6B1DB6 |
| PocLowIL.dll | A9D445B77F6F4E90C29E385264D4B1B95947ADD5 |
Network Indicators:
| IP Address | Domain |
| 194.87.189[.]171 | journalctd[.]live |
| 178.236.246[.]241 | correctiv[.]sbs |
| 62.60.238[.]81 | cwise[.]store |
| 147.45.78[.]102 | redircorrectiv[.]com |
| 46.226.163[.]67 | devolredir[.]com |
| 62.60.237[.]116 | redirconnectwise[.]cloud |
| 62.60.237[.]38 | redjournal[.]cloud |
| 194.87.189[.]19 | 1drv.us[.]com |
| 45.138.74[.]238 | economistjournal[.]cloud |
| 176.124.206[.]88 | N/A |
For a more detailed list of IOCs, accompanied by detailed TTPs and additional insights into the RomCom campaign, visit this GitHub page.