Dux Human Health Breach, U.S. Credit Card Sale, Boulanger Database Leak, and More
SOCRadar’s Dark Web Team has monitored concerning activity on hacker forums over the past week, revealing significant cyber threats. These include an alleged data breach affecting 200,000 Dux Human Health customers and the sale of 20,000 U.S. credit card records, with pricing options for bulk purchases.
Additionally, the team identified the sale of a 27.5 million-record database linked to French e-commerce platform Boulanger and a shared proof of concept exploit for CVE-2024-45387, targeting Apache Traffic Control. Hacktivist group Anonymous Guys also claimed responsibility for DDoS attacks on Ukrainian telecoms and government websites, emphasizing ongoing risks to critical infrastructure.
Receive a Free Dark Web Report for Your Organization:
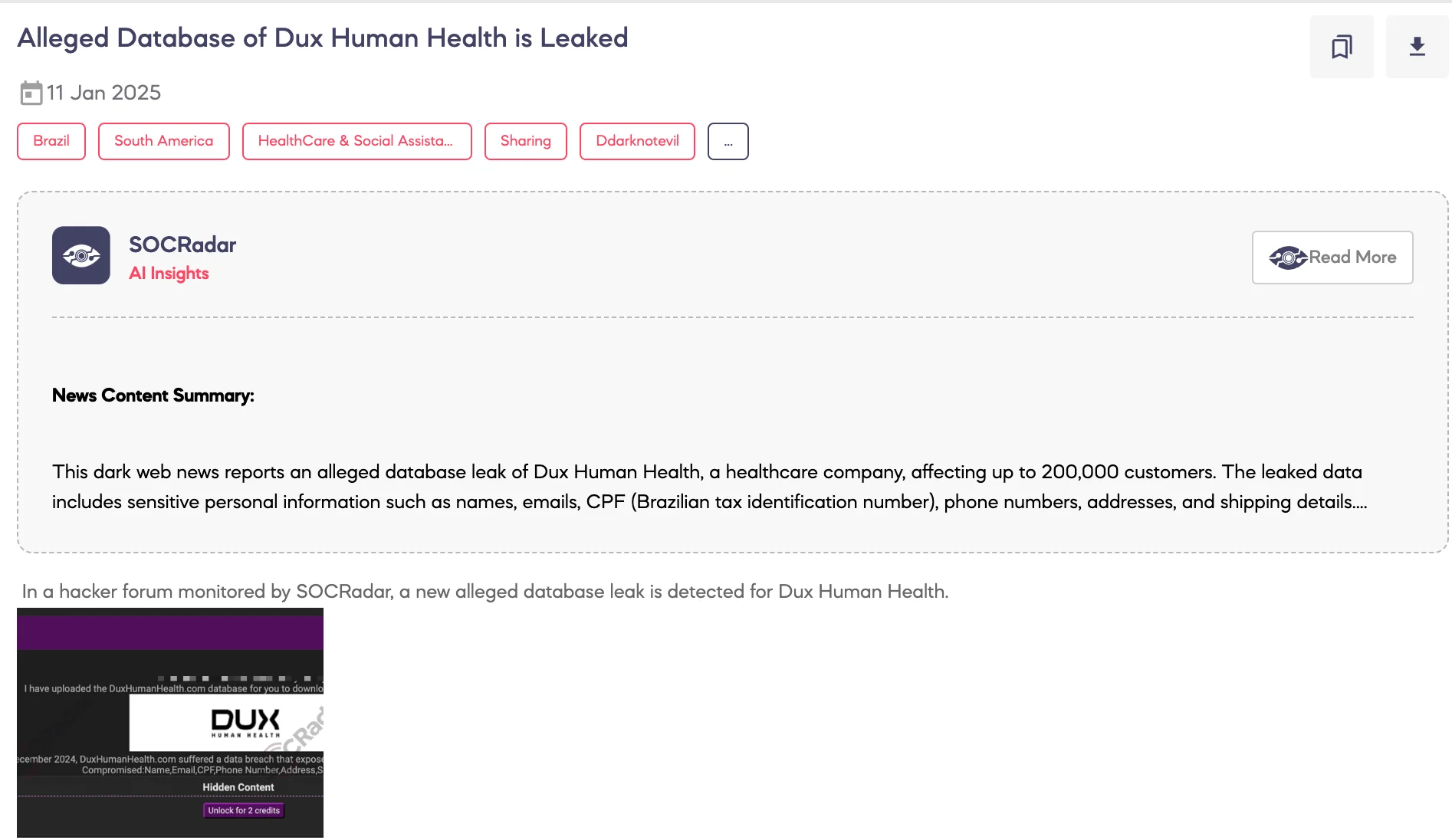
Alleged Database of Dux Human Health is Leaked
SOCRadar Dark Web Team identified a post on a hacker forum alleging a data breach involving Dux Human Health.
The threat actor claims that in December 2024, DuxHumanHealth.com experienced a data breach that compromised the personal information of up to 200,000 customers. The exposed data reportedly includes names, email addresses, CPF (Cadastro de Pessoas Físicas – Brazilian Individual Taxpayer Registry), phone numbers, addresses, and shipping information.
Note: A similar breach claim for Dux Health was shared on December 29, 2024, on a popular Russian-speaking hacker forum. This highlights the rapid spread of data on the Dark Web and emphasizes the critical importance of monitoring Dark Web activities.
Alleged 20K Credit Cards Belonging to the United States are on Sale
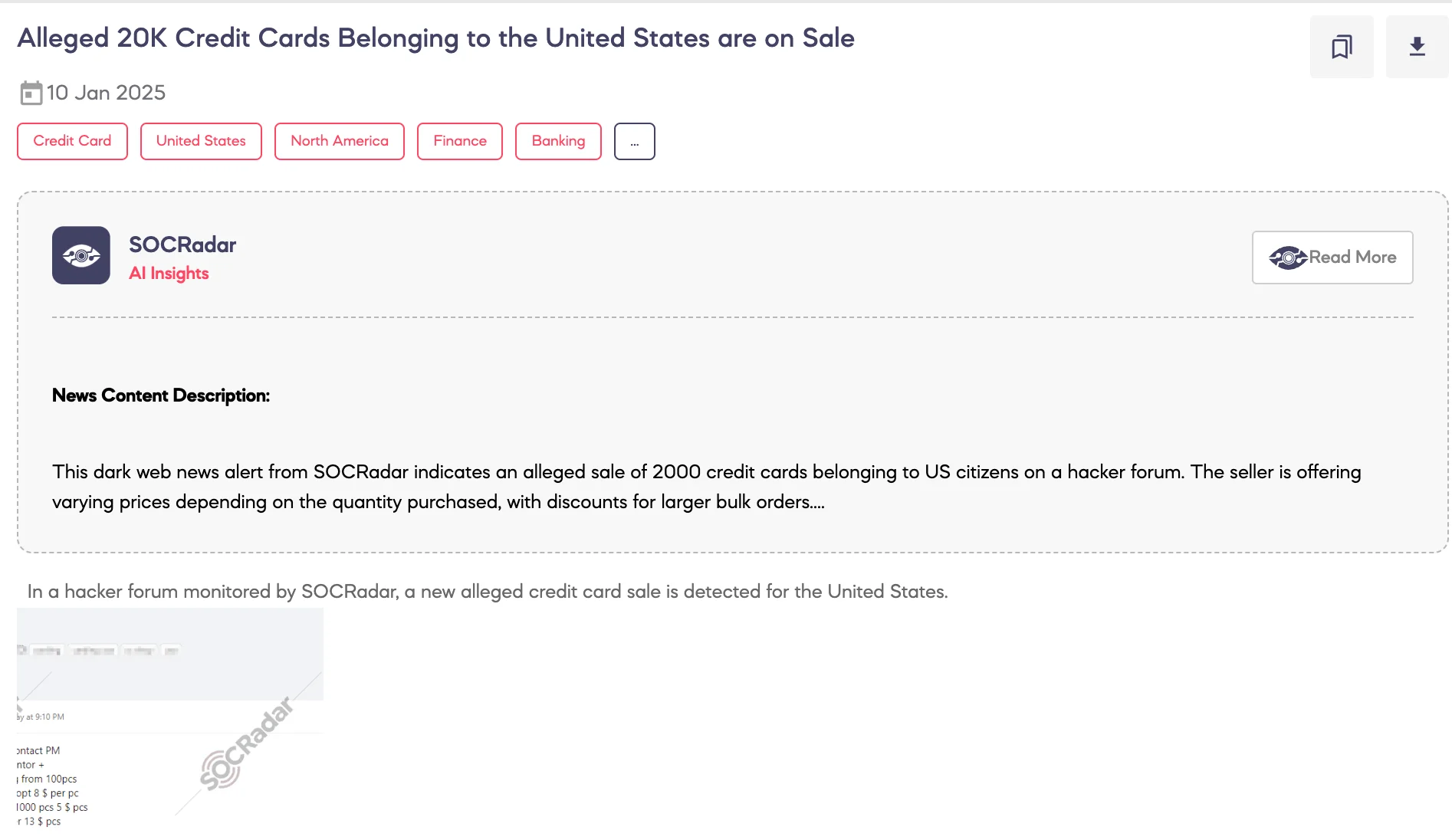
SOCRadar Dark Web Team detected a post on a hacker forum advertising the sale of an alleged database containing 20,000 credit card records associated with individuals in the United States.
According to the post, the threat actor offers the following terms for the sale:
- Minimum purchase of 100 records.
- Pricing is set at $8 per record for small quantities.
- Bulk purchases of 1,000 records or more are offered at $5 per record.
- Retail records are priced at $13 per record.
The threat actor also mentions the availability of a guarantor service to facilitate secure transactions and invites interested parties to establish contact via private messaging.
Alleged Database of Boulanger is on Sale
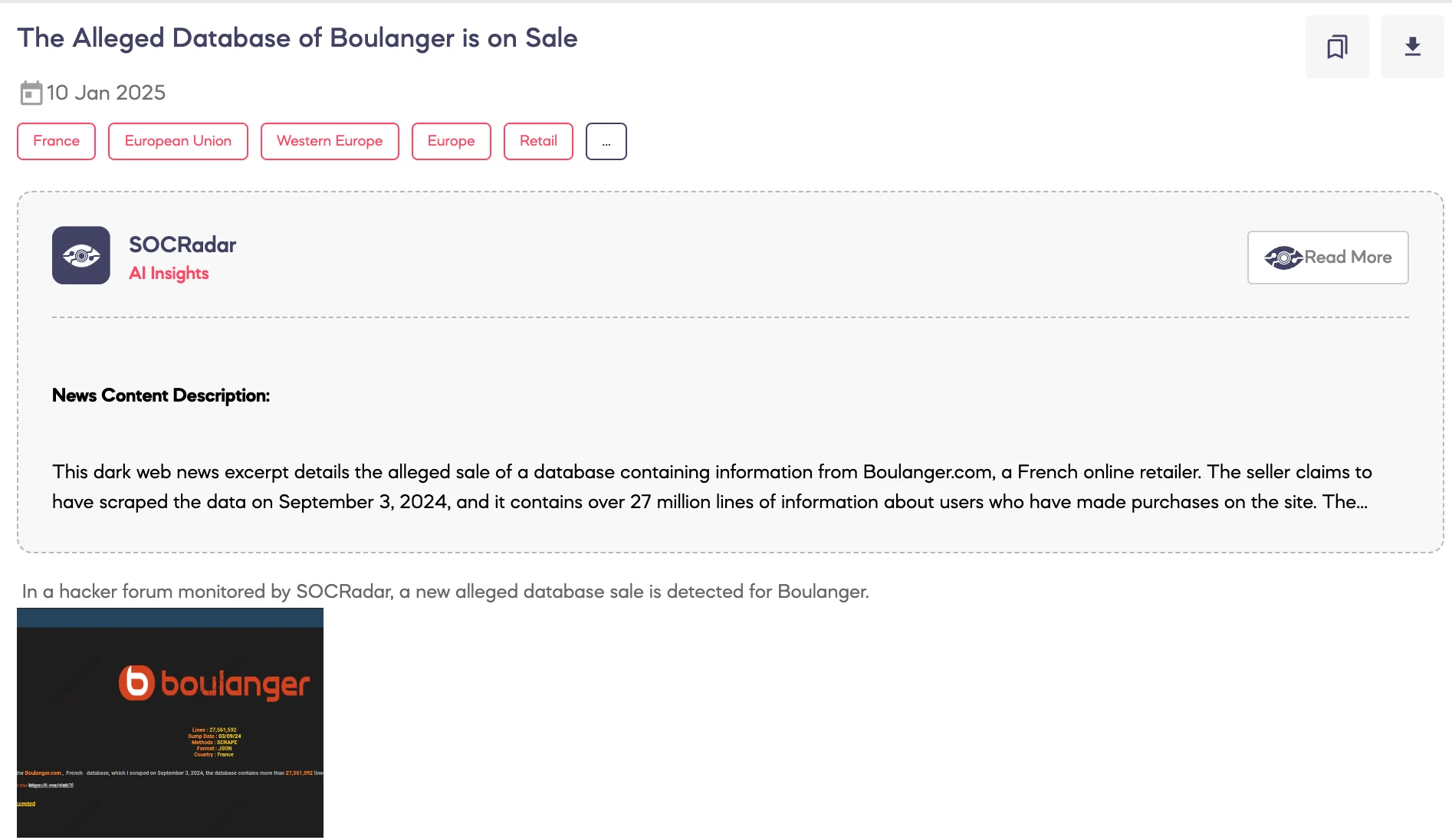
SOCRadar Dark Web Team identified a post on a hacker forum advertising the sale of an alleged database reportedly linked to Boulanger, a French e-commerce platform.
According to the threat actor, the database contains over 27.5 million records, including sensitive customer information. The leaked data reportedly includes fields such as names, addresses, phone numbers, and dates of birth, as well as metadata related to customer interactions and website activities. The database is described as being in JSON format and specific to users in France.
The threat actor claims the database was scraped on September 3, 2024, and has invited potential buyers to propose a price. Escrow services are stated as an option for completing the transaction.
Alleged CVE-2024-45387 Exploit POC is Shared
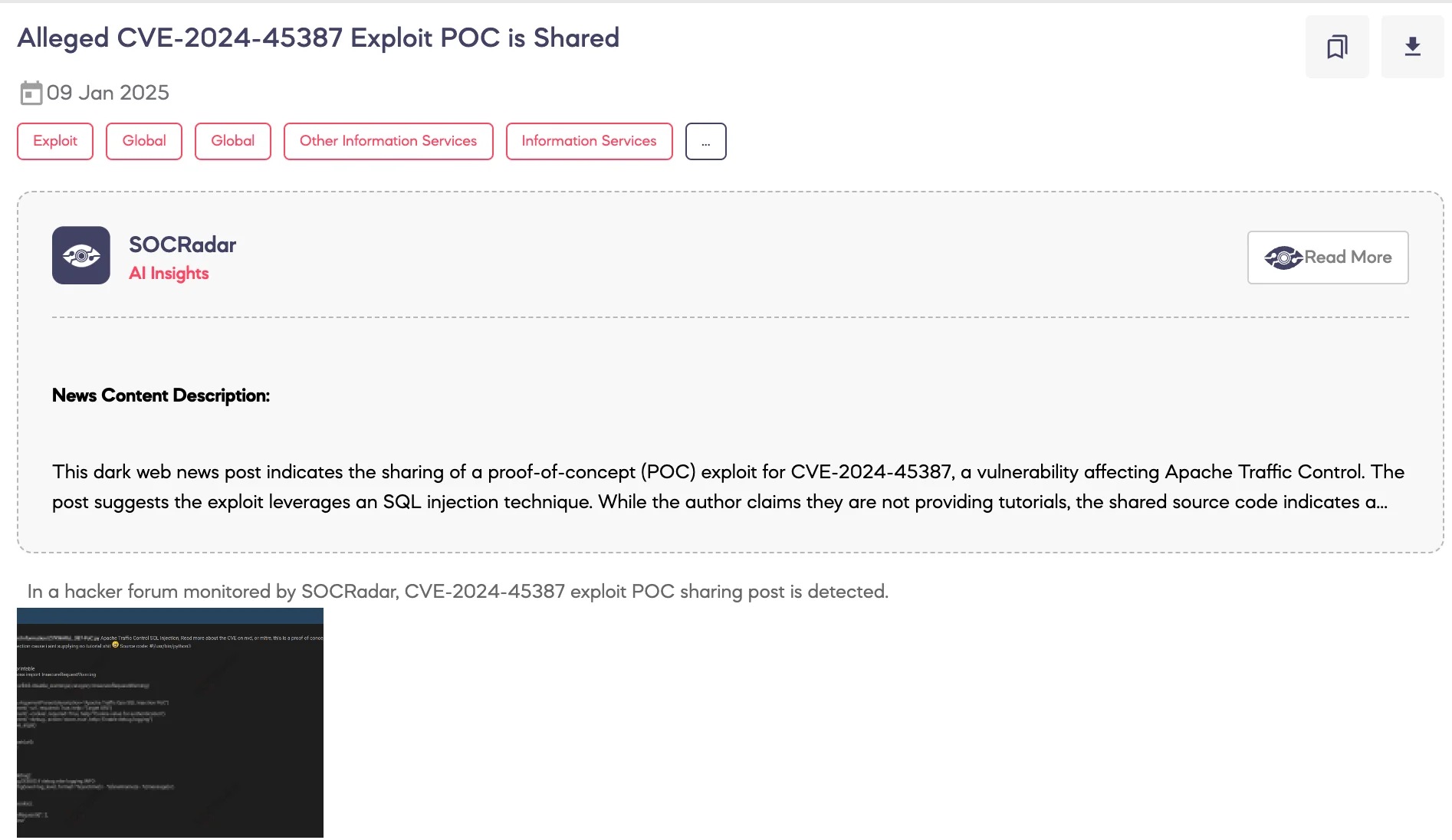
SOCRadar Dark Web Team identified a post on a hacker forum where a threat actor shared a proof of concept (POC) exploit for CVE-2024-45387.
According to the threat actor, the vulnerability pertains to an SQL injection exploit targeting Apache Traffic Control. The post provides a Python-based source code as the POC for exploiting the vulnerability, encouraging individuals familiar with SQL injection techniques to utilize it. The actor states that no tutorial or further guidance will be provided.
If the claims are accurate, this shared exploit could enable unauthorized access or manipulation of systems running vulnerable versions of Apache Traffic Control, posing significant security risks to affected organizations.
Anonymous Guys Conducted DDoS Attacks on Ukrainian Telecom Companies
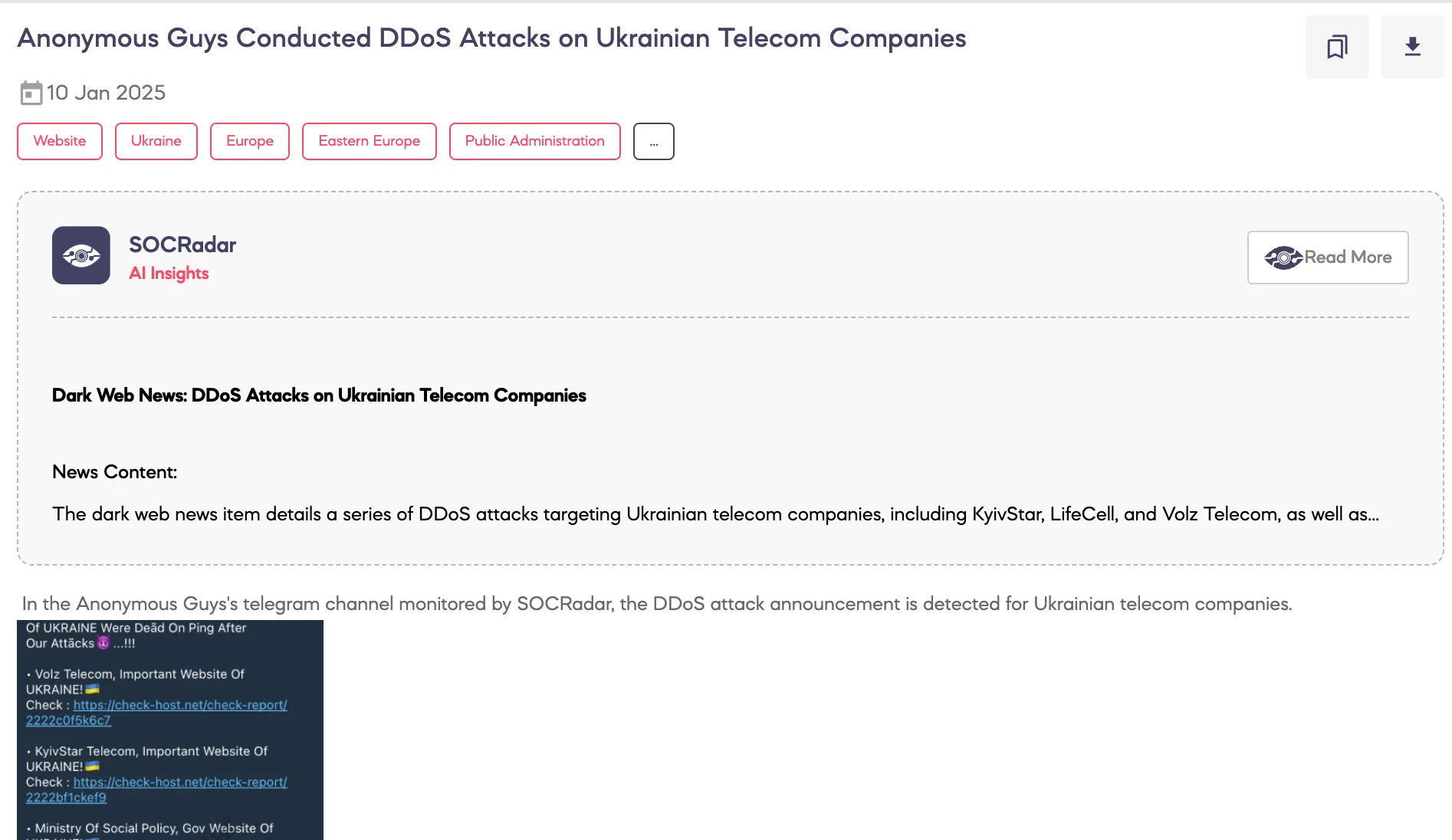
SOCRadar Dark Web Team detected a post on a hacktivist Telegram channel where a threat actor announced Distributed Denial-of-Service (DDoS) attacks targeting Ukrainian telecom companies and government websites.
According to the threat actor, the attacks resulted in several Ukrainian government and telecom websites becoming inaccessible. Specific targets mentioned include Volz Telecom, KyivStar Telecom, LifeCell Telecom, and Adanosa Telecom, as well as the website of the Ministry of Social Policy. The post included links to reports on the affected websites’ statuses.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.