
Operation Digital Eye: Exploiting Visual Studio Code Tunnels for Advanced Intrusions
Operation Digital Eye is a cutting-edge cyber campaign executed by Chinese Advanced Persistent Threat (APT) groups. This sophisticated operation exploits the tunneling functionality in Visual Studio Code to breach IT infrastructure, with a primary focus on European organizations.

An illustration of Operation Digital Eye, generated with DALL-E
Below is an analysis of this campaign, including key Indicators of Compromise (IoCs), mitigation strategies, and detection rules.
Campaign Overview
Operation Digital Eye manipulates legitimate features of Visual Studio Code, such as tunneling, to maintain persistence while avoiding detection. The attack demonstrates the evolving methods employed by adversaries to exploit trusted tools.
The campaign is linked to Chinese APT groups, known for their focus on cyber espionage and sophisticated attack techniques.
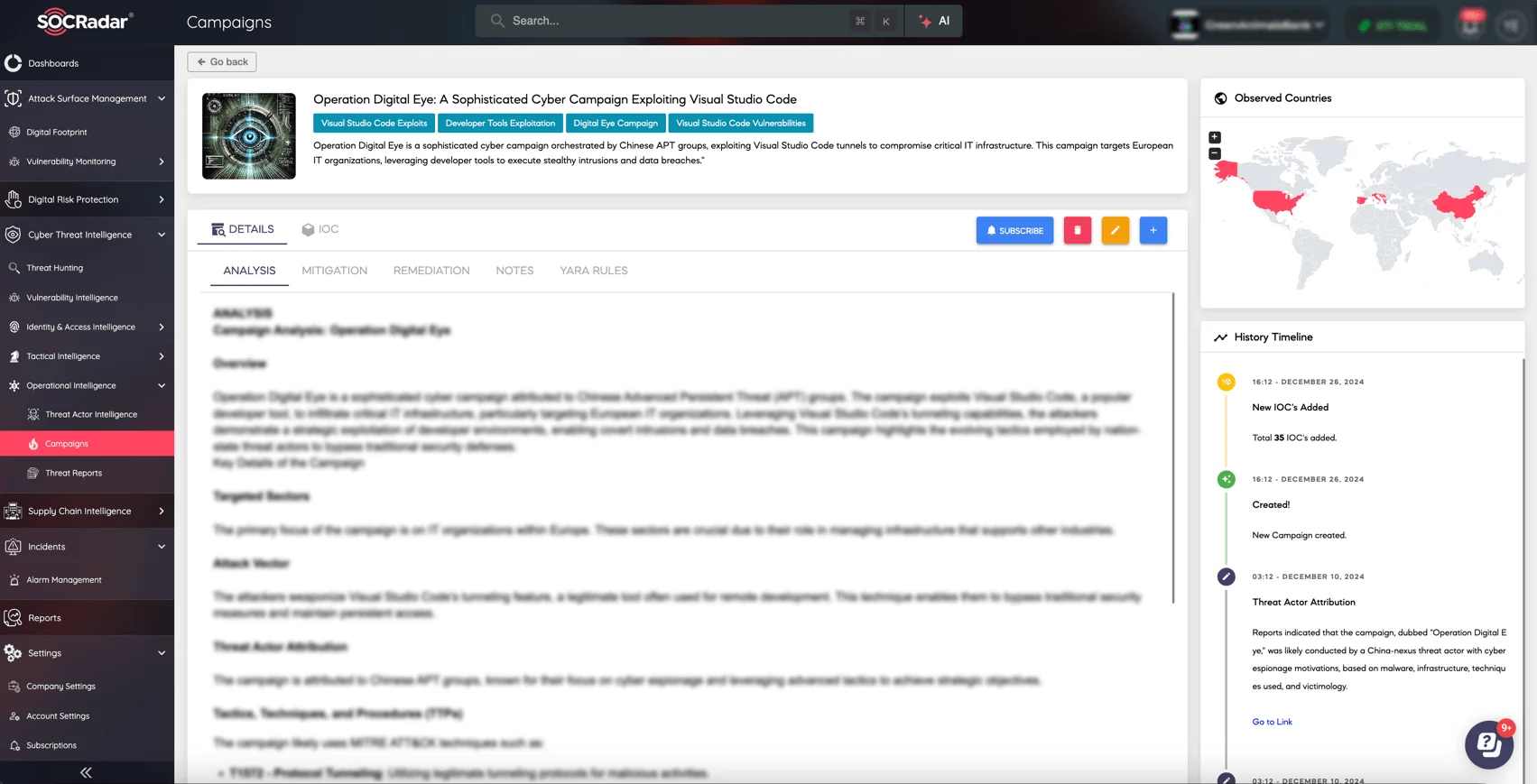
Details of Operation Digital Eye on SOCRadar XTI platform’s Campaigns page
Here are some additional key details about the campaign:
- Targeted Sectors: European IT organizations, which serve as foundational infrastructure for other industries.
- Impacted Regions: Countries in Southern and Eastern Europe, including Italy, Spain, Portugal, and Greece, as well as China and the United States.
- Severity Level: High, due to its capability to disrupt critical IT operations.
SOCRadar’s Role in Combatting Advanced Threats Like Operation Digital Eye
SOCRadar assists organizations in defending against advanced threats like Digital Eye with its comprehensive Extended Threat Intelligence (XTI) platform. Through powerful modules such as Advanced Dark Web Monitoring and features like Malware Analysis, SOCRadar provides real-time threat detection and alerts, allowing organizations to respond promptly to compromised credentials or new campaigns.
By leveraging Cyber Threat Intelligence, SOCRadar offers actionable insights into the Tactics, Techniques, and Procedures (TTPs) used by Digital Eye, helping organizations stay ahead of attackers. The platform’s Vulnerability Intelligence also highlights exploitable weaknesses, while Incident Response Support accelerates mitigation efforts after detection.
Recommendations Against Operation Digital Eye
To effectively defend against this threat, organizations should adopt the following practices:
- Conduct Frequent Security Assessments: Regularly evaluate developer tools, such as Visual Studio Code, to identify and address potential vulnerabilities that could be exploited by attackers.
- Monitor Unusual Activities: Keep an eye on suspicious or abnormal behaviors within development environments to detect malicious activity early on.
- Educate Developers: Ensure that developers are aware of the security risks associated with their tools and foster a culture of secure coding practices.
SOCRadar LABS provides a dedicated Campaigns page for Digital Eye, offering detailed analysis, Indicators of Compromise (IoCs), and the latest intelligence to ensure businesses are well-prepared for this ongoing threat. By using SOCRadar’s Extended Threat Intelligence and proactive defense tools, organizations can strengthen their cybersecurity posture and safeguard critical assets.
Explore the latest Campaigns and access our free SOC tools at SOCRadar LABS
Indicators of Compromise (IoCs)
| Type | Value | Description |
| SHA1 Hashes | 0be9dd709d7d68887a92c793881dd4a010796e95 | CreateDump tool (do.exe) |
| 213f06ed5ac9e688816b4bbe73bf507994949964 | GetUserInfo tool | |
| IP Addresses | 146.70.161.78 | Initial access server |
| 20.103.221.187 | Visual Studio Code dev tunnel | |
| Domains | [REDACTED].euw.devtunnels.ms | Visual Studio Code dev tunnel |
Mitigation Strategies
| MITRE ID | Mitigation | Description |
| M1031 | Network Intrusion Prevention | Use network signatures to detect and block malicious traffic. |
| M1037 | Filter Network Traffic | Block access to untrusted domains and resources. |
| M1040 | Behavior Prevention on Endpoint | Enable Attack Surface Reduction (ASR) rules to mitigate JavaScript-based threats. |
| M1021 | Restrict Web-Based Content | Deploy script-blocking extensions and ad blockers to minimize script execution risks. |
Detection and Remediation
| Data Source | Component | Detection Method |
| Network Traffic | Content Analysis | Inspect traffic for irregular syntax or unexpected patterns. |
| Command | Execution Monitoring | Monitor processes and command-line arguments for unusual behavior. |
| Module | Load Tracking | Identify the loading of suspicious modules associated with scripting languages. |
YARA Rules for Threat Detection
rule win_mimikatz_auto {
meta:
author = "Felix Bilstein"
description = "Detects win.mimikatz."
strings:
$sequence_0 = { f7f1 85d2 7406 2bca }
$sequence_1 = { 83f8ff 750e ff15???????? c7002a000000 }
condition:
any of ($sequence_*) and filesize < 1642496
}




































