From Zero to Adversary: APTs
By SOCRadar Research
From time to time, news hit the front pages regarding cyberattacks on significant infrastructures, such as nuclear facilities, or major companies, such as SolarWinds. These attacks are carried out by cyber threat actors called Advanced Persistent Threat (APT) groups consisting of animal names, elements, or numbers along with country names.
Looking at MITRE ATT&CK‘s cyber threat group list, there are more than 100 known APT groups, and their number will continue to increase daily.
So, what factors bring them to the agenda, subject them to various names, and make them unique?
An APT is a threat actor that is able to breach a computer network or system via exploitation and remain hidden for a long time while potentially stealing data or performing harmful actions. These actors are well-funded and may be connected to nation-states or other large entities. They utilize various tactics such as malware, social engineering, and more to gain access to their target systems.
What Traits Make a Threat Actor an APT?
APT groups often target government organizations that handle sensitive information, such as military information and advanced technology. These groups differ from other cybercriminals as they can evade security measures and stay undetected in a system for extended periods.
Also, there are specific characteristics that distinguish APTs from other threat actors:

They operate covertly, often staying undetected, and they are able to maintain access to a target system for a long time, often for months or years. For example, the APT29 (or the Dukes) operated its cyberespionage activities by compromising government targets from 2013 to 2019 without drawing attention during its “Operation Ghost” campaign.
APTs are often carried out by organized groups or teams rather than individual cybercriminals and typically have a clear motivation or objective, such as espionage, sabotage, or financial gain. They are often state-sponsored and have a specific target in mind. Their targets are government agencies such as the department of defense of the country, universities, research programs, large enterprises and institutions such as enterprises whose work in finance, manufacturing, and tech or essential and critical infrastructure of a country such as electric grids, nuclear facilities, military or telecommunication. According to HP’s report in 2021, nation-state-sponsored threat actors targeted Enterprises most:
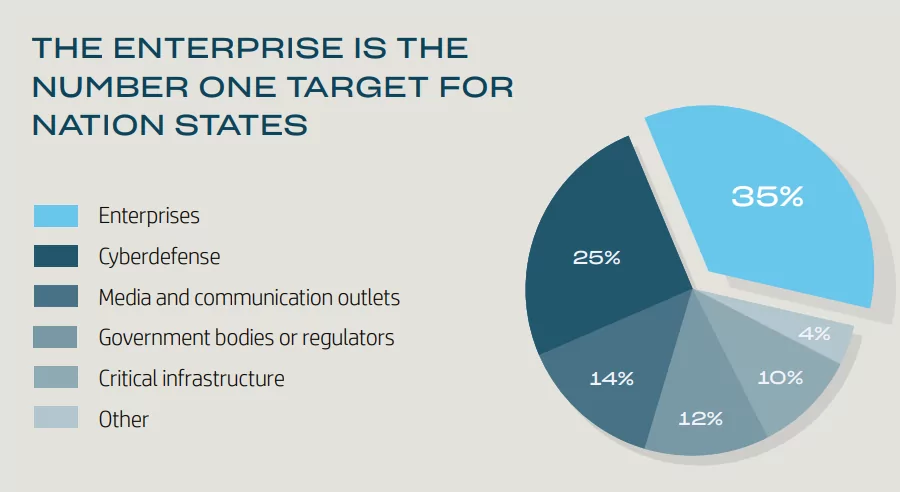
APTs typically act when a more advanced and prolonged attack is necessary to achieve the desired outcome. Simple attacks may not be sufficient against their high-profile targets; that’s why APTs are operating more sophisticatedly.
Their attack’s impact can be genuinely devastating; for example, the Stuxnet worm that targets Iran’s nuclear facility destroyed numerous centrifuges by causing the uranium enrichment facilities to burn themselves out, demonstrating the potential for cyberattacks to cause physical damage and disruption to critical infrastructure.
Can Ransomware Groups be named as APTs?
Ransomware groups are not generally considered to be APT groups because they tend to have different motivations and goals. APT groups are often state-sponsored and focused on espionage, while ransomware attacks are typically driven by financial gain.
APT groups are known for maintaining a long-term presence in a target’s infrastructure and going undetected for longer periods. In contrast, ransomware groups focus on quickly encrypting data and demanding payment in exchange for the decryption key.
Although they are different, according to the research of Cyber Security Works, 43 APTs use ransomware, such as APT35, Exotic Lily, and DEV-0401, and APT groups using ransomware are slightly (7.5%) increasing.
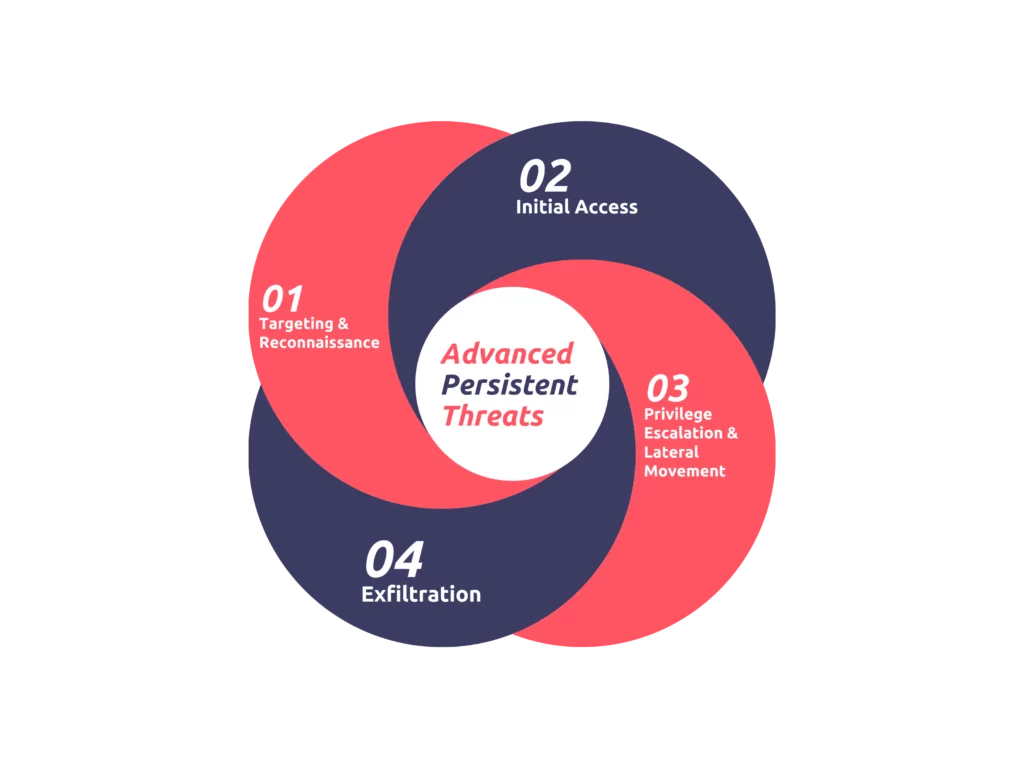
What are the APTs’ Common Attack Stages?
APT attacks follow certain stages; these stages are:
- Targeting and Reconnaissance
APT attacks begin with target selection and reconnaissance, as in Cyber Kill Chain. APT groups select their target for their sponsored nation’s interests. After the target is selected, they will start their attack cycle by discovering potential entry points.
- Initial Access
APT’s reconnaissance follows unauthorized access to its target’s network by using attack vectors. The most common way to achieve this stage is through social engineering techniques, especially spear phishing. Research analyzing around 90 APT reports shows that 80% of the APT attacks’ initial vector is spear phishing.
While they are thought to be exploiting zero-day vulnerabilities, research shows that APT groups often exploit certain CVEs.
Top CVEs exploited by APT Groups and their weakness enumerations (CWE):
|
CVE |
CWE |
|
Not-defined |
|
|
Not-defined |
|
After gaining access, the attacker executes the first payload on the compromised machine. This payload is used in three scenarios: Reconnaissance, defense evasion, and connecting to Command and Control (C2) server.
- Privilege escalation and lateral movement
This stage consists of harvesting access credentials to escalate the privileges. Escalated privileges give the attacker more freedom of movement inside the victim’s network to reach high-value assets.
- Exfiltration
After infiltrating a target’s network and accessing valuable data, the APT attacker will transfer the information to their system. The data is often packaged in an encrypted, compressed file and then transferred in small chunks to avoid detection.
How Are APTs Named?
Security companies often adopt a profiling approach similar to that of the FBI when investigating threat actors. Just as the FBI uses the modus operandi of a serial killer to build a profile of the perpetrator, even if their identity is unknown, cybersecurity researchers use information about a group’s typical targets, tactics, malware, and techniques to track APT activity and campaigns globally. These groups are often given names, which serve as a convenient way to organize and document their threat patterns, often with a connection to the region they are believed to originate from.
Also, the naming process is beneficial for the follow-up of threat actors in a more organized way in the cyber world.
There are certain standardizations that vendors make internally:
- Crowdstrike
CrowdStrike maintains strict standards for analytic integrity and trains its analysts to use proper language, eliminate bias, and employ analytic tools.
The attribution process is thorough and includes review by multiple teams before an actor is named and added to CrowdStrike’s list of known adversaries.
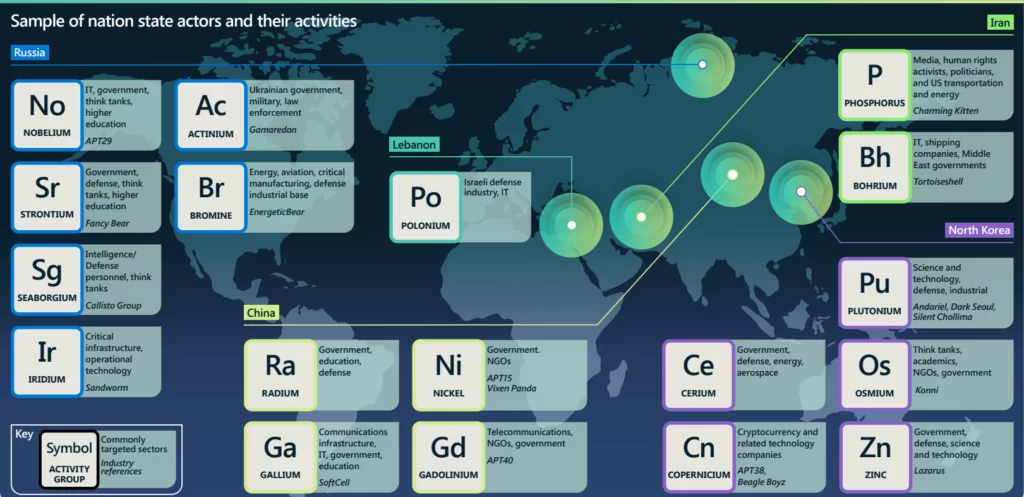
Also, Crowdstrike is known for naming the threat actors they observed with animals paired with the country or the main objective of the threat actor. For example, Russian threat actors are named “Bear,” such as Fancy Bear and Cozy Bear. Iranian threat actors are named with “Kitten” tags such as Charming Kitten and Remix Kitten. Cybercriminals motivated by monetary gain are named “Spider,” such as Scattered Spider and Catapult Spider. Hacktivists looking to create political disruption are named “Jackal,” such as Deadeye Jackal, etc.
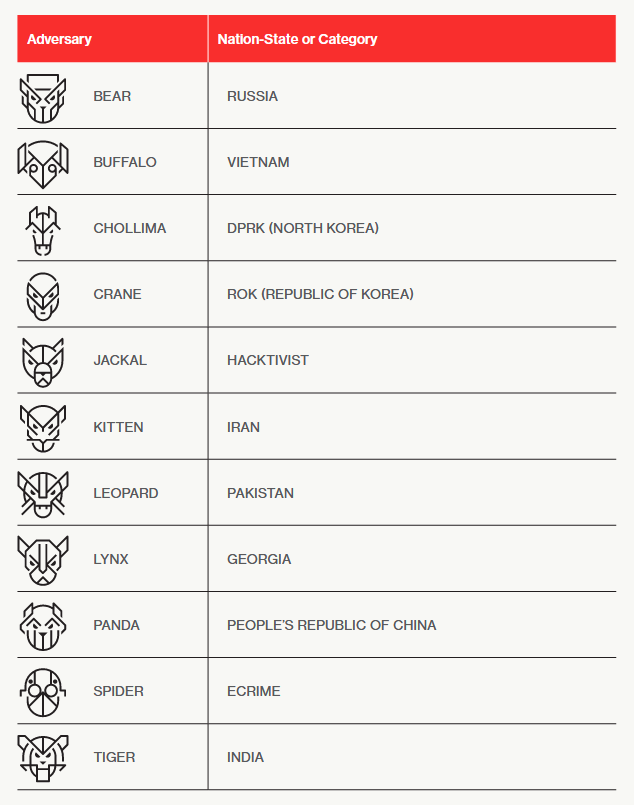
Some vendors, such as Checkpoint, Kaspersky, and ClearSky, use Crowdstrike’s naming scheme to name the threat actor they are observing. For example, Domestic Kitten, Fox Kitten, Vicious Panda, and Sharp Panda haven’t gotten their names from Crowdstrike.
Borrowing CrowdStrike’s nomenclature without using the same standards or processes as Crowdstrike could be an issue with correctly describing the threat actor and may cause confusion.
- FireEye / Mandiant
Mandiant is known for pioneering naming conventions in threat intelligence, with the release of its APT1 report in 2013. Mandiant names APT groups using an APT keyword with tag numbers, -APT##- but it does not specify which nation-state is involved. For example, APT34 is an Iranian APT group which is named Helix Kitten by Crowdstrike. Over time, Mandiant added other prefixes, such as UNC, TEMP, and FIN, to provide more information about the group. UNC is for unclassified activity clusters, TEMP for evolving clusters, and FIN for publicly named groups with financial or espionage motivations.
- Palo Alto Unit42
Unit42 has its threat actor naming based on constellations, but they follow certain rules, as they mentioned in their post about naming updates. If there were already a commonly used name available, they would use it; for example, they have used the common name “Sofacy” to refer to what others call APT28 or Fancy Bear. If there was no common name, they would create a new name for the group at the researchers’ discretion. Unit42 has its own threat actor naming based on constellations if they will name themselves. Unit42 names the Russian nation-state-sponsored threat actors as “Ursa,” Indian nation-state-sponsored ones as “Gemini,” and North Korean nation-state-sponsored threat actors as “Pisces,” and so on. For example, Unit42 named a Russian state-sponsored group Trident Ursa, which is named Primitive Bear by Crowdstrike.
- Microsoft
Microsoft names the threat actor it is examining by the actors’ intent, such as nation-state actors associated with element names, criminal activity with volcanoes, and private sector activity with trees. In addition, DEV represents a new activity that is still under investigation. For example, Microsoft named an Iranian threat actor, Phosphorus which is named APT42, by Mandiant.
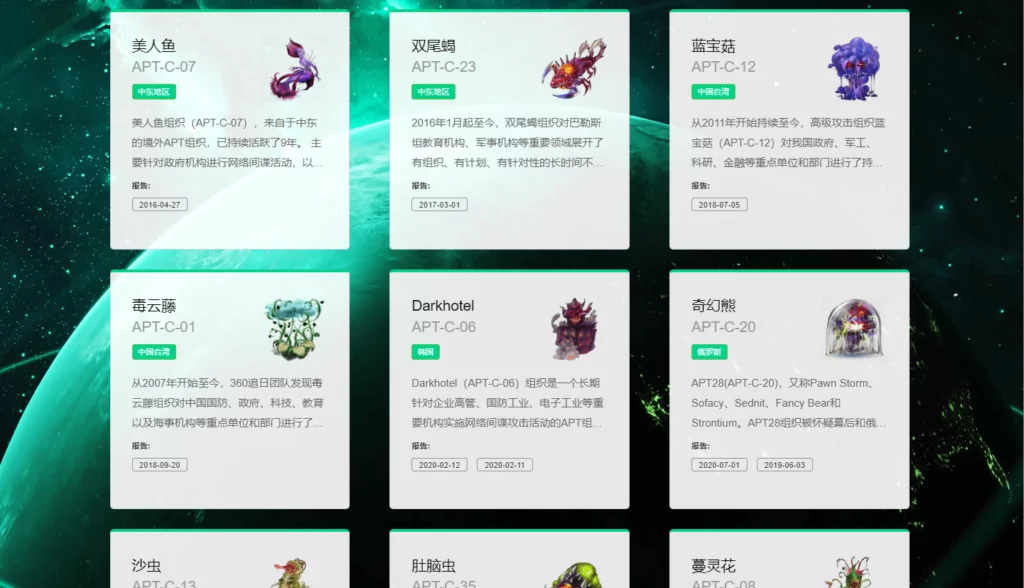
- Qihoo 360
360 is naming the threat actors they are examining using the “APT-C-” keyword with tag numbers –APT-C-##-. For example, a South Korean threat actor named APT-C-06 is examined by Kaspersky as DarkHotel.
However, there are various reasons for naming confusion in the threat intelligence field, including human error and technical factors. Human-caused reasons include using operation names or malware names as threat actor names, vendors failing to connect research, and journalists not correcting errors in articles. Technical reasons include vendors seeing different pieces of the whole picture, threat actors joining or splitting, groups sharing tools and infrastructure, and vendors disagreeing on names due to different TTPs.
What Are the Notable APT Activities?
APT groups come to the forefront with their activities in significant events such as the Olympics, wars, and compromising critical systems of their target countries.
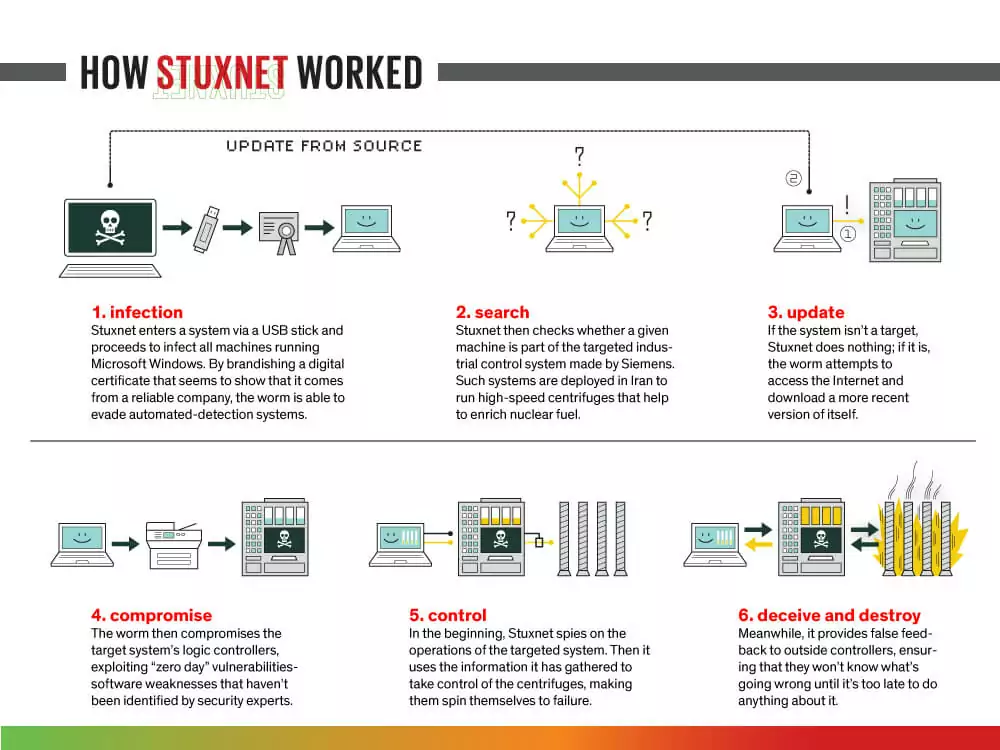
- Stuxnet
Stuxnet is a computer worm believed to have been developed by the Equation APT Group and targeted Iranian nuclear facilities. Stuxnet was designed to specifically target industrial control systems (ICS) and was the first known malware to do so. It is considered one of the most sophisticated cyberattacks in history, demonstrating the potential for cyber attacks to have significant real-world consequences.
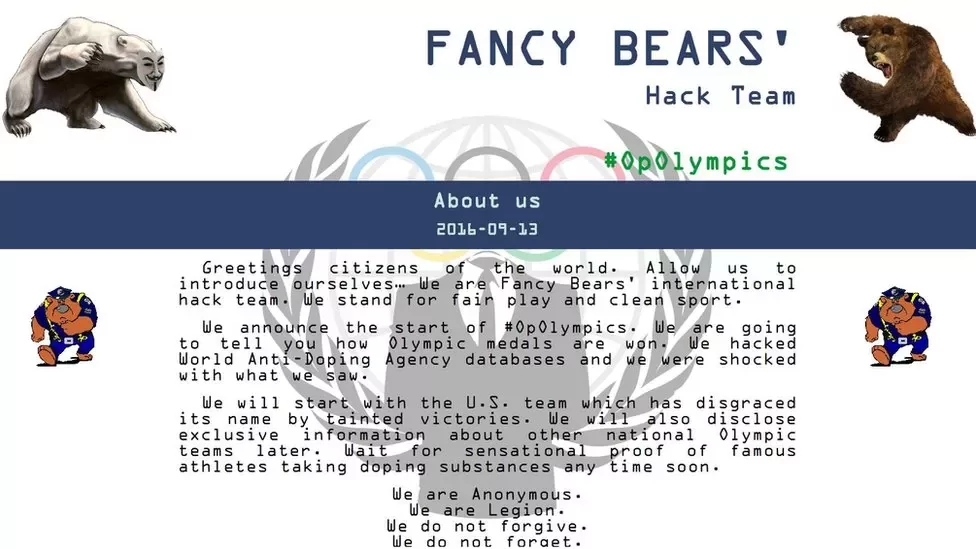
- 2016 Rio Summer Olympics
Fancy Bear (STRONTIUM, or APT28) played a significant role in the 2016 Rio Summer Olympics by stealing World Anti-Doping Agency’s (WADA) drug testing files from Olympics athletes. Following the WADA incident, the group hacked the International Association of Athletics Federations (IAAF) ‘s servers in April 2017.
- SolarWinds Supply Chain Compromise
According to the White House and the Government of Canada’s report in 2021, Cozy Bear (NOBELIUM and APT29) is behind the cyber espionage attack that exploited the SolarWinds Orion platform to access the US Government’s IT infrastructures.
- Ukraine’s Power grid attack
In 2015, the power grid of Ukraine was hacked, resulting in power outages for some consumers in Ukraine for hours. It is thought that the Sandworm Team (Voodoo Bear) is the perpetrator of this incident.
- Operation Ababil
The Izz ad-Din al-Qassam Cyber Fighters operated the Ababil campaign from September to October 2012. According to Radware, the group aims to target media organizations that they believe insult Islam. The group targeted American banks and financial institutions with DDoS attacks. The action was believed to have been taken as retaliation for a movie posted online that offended the prophet of Islam, Muhammad, which was made as an anti-Islam film.
- Dark Seoul
In April 2013, South Korea was hit by a coordinated attack using basic but effective malware that caused tens of thousands of computers in the media and financial services industries to become inoperable. The attackers also used the malware to steal sensitive information from the targeted organizations, such as Korean television broadcasters KBS, MBC, and YTN. The attack’s origin is not confirmed, but it is believed that North Korea or a group associated with it was behind it.
- BadBlood
In late 2020, APT42 (TA453), which is a threat actor allegedly affiliated with the Islamic Revolutionary Guard Corps (IRGC) Intelligence Organization (IRGC-IO) and operates on behalf of them, launched a spear phishing campaign for credential harvesting purposes that target senior medical professionals who specialize in genetic, neurology, and oncology research in the United States and Israel.
Conclusion
APT (Advanced Persistent Threat) groups are typically state-sponsored. They are known for their ability to maintain a long-term presence in a target’s network, often going undetected for extended periods and commonly operating for their geopolitical goals.
It is also worth noting that the APTs have evolved; the tactics, techniques, and procedures (TTPs) used by APT groups are constantly evolving, which makes them sophisticated threat actors, and the definition of APT itself may change as a result.
Regardless of their standing and naming, threat actors continue to pose risks in cyberspace.
SOCRadar monitors the current campaigns by making continuous observations. In addition, the campaigns panel, which is constantly updated, can be accessed through SOCRadar Labs to keep up to date.
In addition, it is difficult to accurately determine the number of APT groups that exist, as these groups often operate covertly and can be difficult to track.
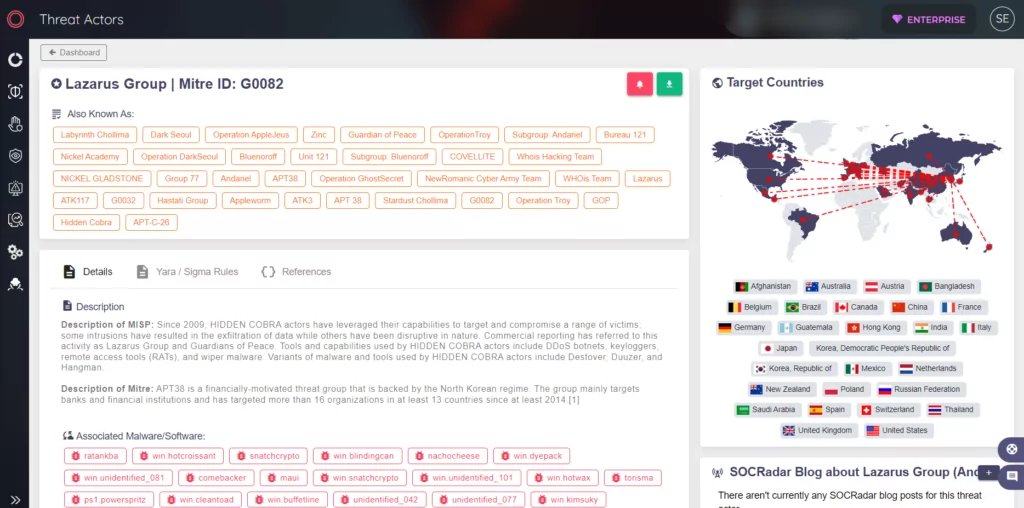
SOCRadar has a Threat Actor panel that continuously updates its knowledge base as soon as there is an encounter.
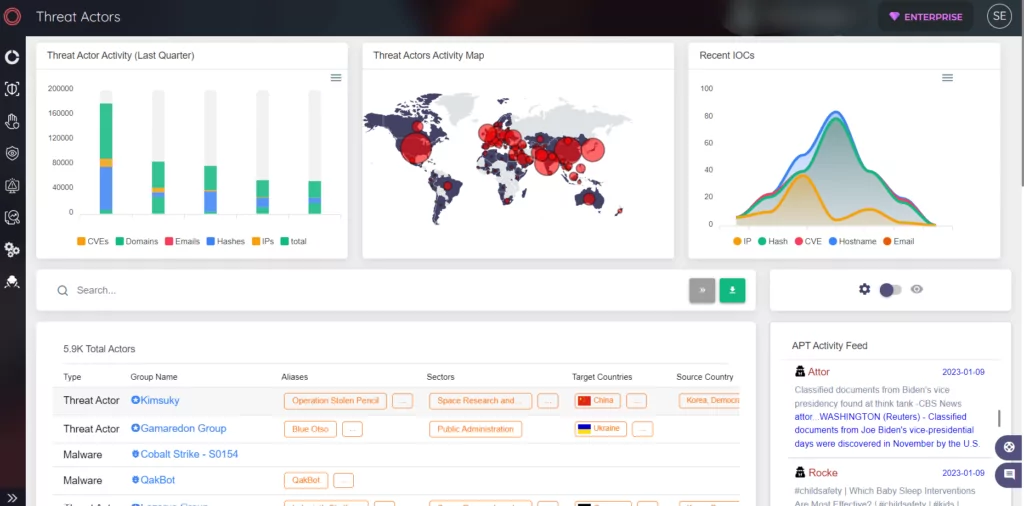
Also, you can examine threat actors such as Lazarus APT Group in detail with SOCRadar’s Threat Actor panel.