
APT Profile: Who is Phosphorus?
Phosphorus is an attack group linked to the Iranian government, also known as Charming Kitten, Ajax Security, NewsBeef, which has been very active since 2017. Its targeting strategy aligns with Iran’s Islamic Revolutionary Guard Corps.
Despite its lack of sophistication, a state-sponsored group as a nation-state, despite its lack of culture-sponsored advanced persistent threat on December 15, 2017. APT35 was observed to be expanding its malware capabilities and intrusion activities, according to research conducted by FireEye in 2018.
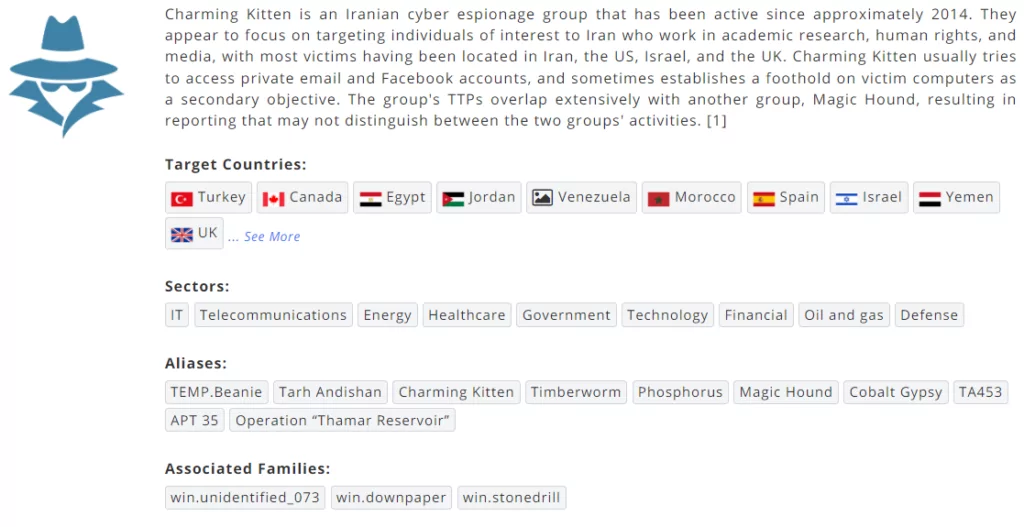
APT35 Attacks Plenty of Countries in Various Sectors
The Phosphorus organization has been operating for several years and has drawn the attention of law enforcement officials and security and technology firms. This group was observed to target vulnerable FortiGate VPN appliances and exploit ProxyShell in MS Exchange and Log4Shell in Log4j to gain initial access into the victims’ networks.
In December 2021, a sub-cluster of Phosphorus called DEV-02 was identified as being related to the ransomware attack against Cox Media Group.
In December 2020, researchers revealed that the Phosphorus group targeted a limited, exact set of people in the medical research industry throughout a credential-theft campaign, which took place. The attackers utilized the well-known spear-phishing approach; however, the lure is a little different given that all of the targets are in the medical area.
Earlier in 2019, Microsoft took down a large swath of the Phosphorus infrastructure 2019, taking control of 99 different domains used in the group’s phishing campaigns.
Later that year, the company revealed details of a campaign in which Phosphorus targeted people it is connected to the 2020 presidential campaigns, journalists, and government officials. The group has also targeted defense sector companies and government entities.
Strategies of Phosphorus APT Group to Infiltrate the Victims
The gang is very well known to be using phishing to imitate company websites and creating phony accounts and DNS domains to steal customers’ passwords. APT35 thrives by concurrently targeting high-risk and high-profile people, mainly through creating realistic documents for phishing attacks.
One strategy this group executes is to send out emails to attendees of specified conferences where researchers meet. According to research by Google’s Threat Research Group (TAG), to easily lure targeted victims, the group utilized the Munich Security and Think-20 (T20) Italy conferences as baits in non-malicious first-contact email messages. The attackers followed up with phishing links in email conversations when they did.
The use of Telegram for operator notifications is one of APT35’s unique tactics. When phishing pages are loaded, the attackers use JavaScript to notify them. They use the Telegram API send Message function to deliver the message, which allows anyone to send a message to a public Telegram channel using a Telegram bot.
The attackers employ this feature to send device-based data to the track, allowing them to access real-time details like the IP address, user agent, and location of visitors to their phishing sites. Google has since reported the bot, and Telegram has taken it down, demonstrating the advantage this group is acquiring by bombarding consumers with AI technologies.
To Protect Your Cybersecurity Infrastructure Against APT35
The recommended techniques and notes on defending against persistent advanced threats are below.
- APT hackers will utilize malware, trojans, and viruses to exploit your system, and up-to-date antivirus software can identify and block them.
- Intrusion prevention systems (IPS) are a critical IT security solution that continuously monitors your network for unusual behavior or malicious code and notifies you if any is detected.
- A sandbox is a safe, virtual environment that allows you to launch and run untrustworthy applications or documents delivered to your users without endangering your operating system’s integrity.
- APT hackers can quickly get initial access to your company’s network through remote access hazards such as an unprotected Wi-Fi hotspot.
- Activate anti-spam and anti-malware protection for your email clients.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free


































