
IntelBroker Strikes HPE Again, Cardinal Health Breach, and U.S. ISP Root Access Sale
SOCRadar’s Dark Web Team has identified alarming cyber threats this week, including a second alleged data leak from Hewlett Packard Enterprise (HPE) by IntelBroker, exposing source code and private keys. Meanwhile, unauthorized root access to a U.S. ISP’s firewall server is being sold on hacker forums. Additionally, a threat actor is purchasing high-level intelligence related to U.S. government operations, and Cardinal Health’s Controlled Substance Monitoring database has reportedly been compromised via a supply chain attack.
Receive a Free Dark Web Report for Your Organization:
Alleged Unauthorized Root Access Sale is Detected for an American ISP
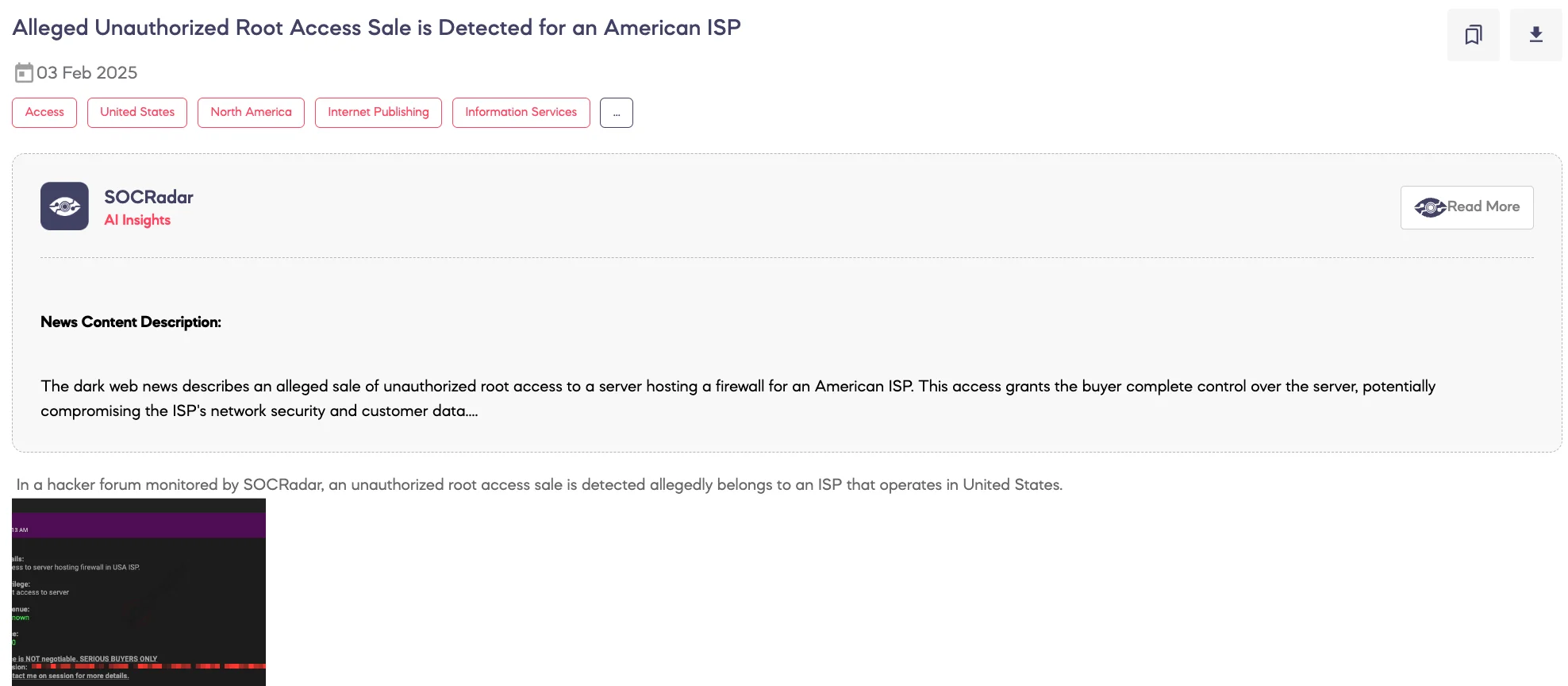
SOCRadar Dark Web Team detected a post on a hacker forum offering unauthorized root access allegedly belonging to a server hosting the firewall of an Internet Service Provider (ISP) operating in the United States. The threat actor claims to have full root privileges on the server and is selling access for $400, with no room for negotiation. Contact details are provided through the Session messaging platform.
High-Level Intelligence Purchasing Announcement is Detected
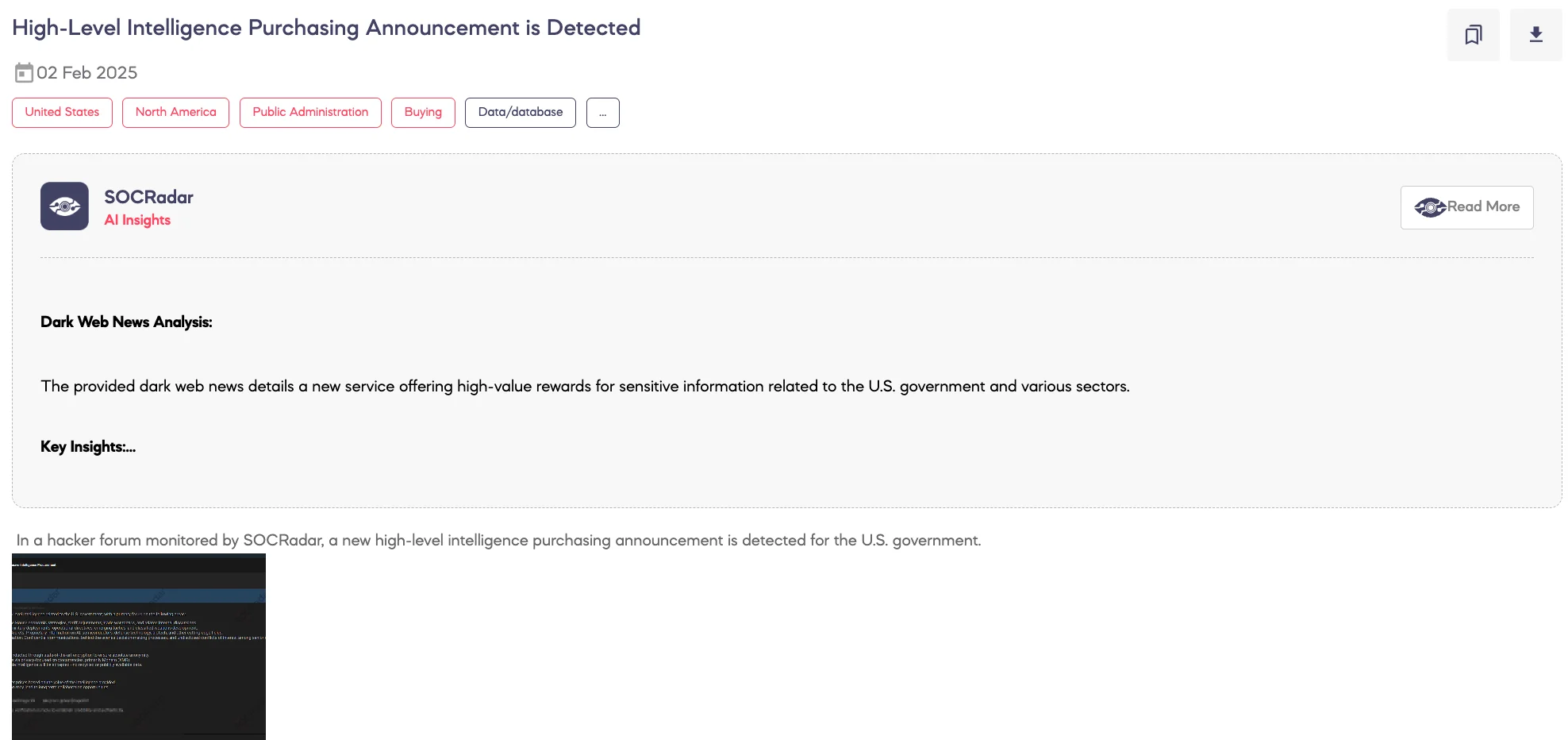
SOCRadar Dark Web Team detected a post on a hacker forum announcing the purchase of high-level intelligence related to the U.S. government. The request specifically targets economic policy, military strategy, high-tech corporate secrets, and political insider information. The post emphasizes the use of advanced encryption for secure transactions, with payments conducted through privacy-focused cryptocurrencies, primarily Monero (XMR). The threat actor specifies that only exclusive and verifiable intelligence will be accepted, offering high rewards based on the value of the information provided and potential long-term collaboration opportunities.
Alleged Source Code and Sensitive Data of Hewlett Packard Enterprise Are Leaked
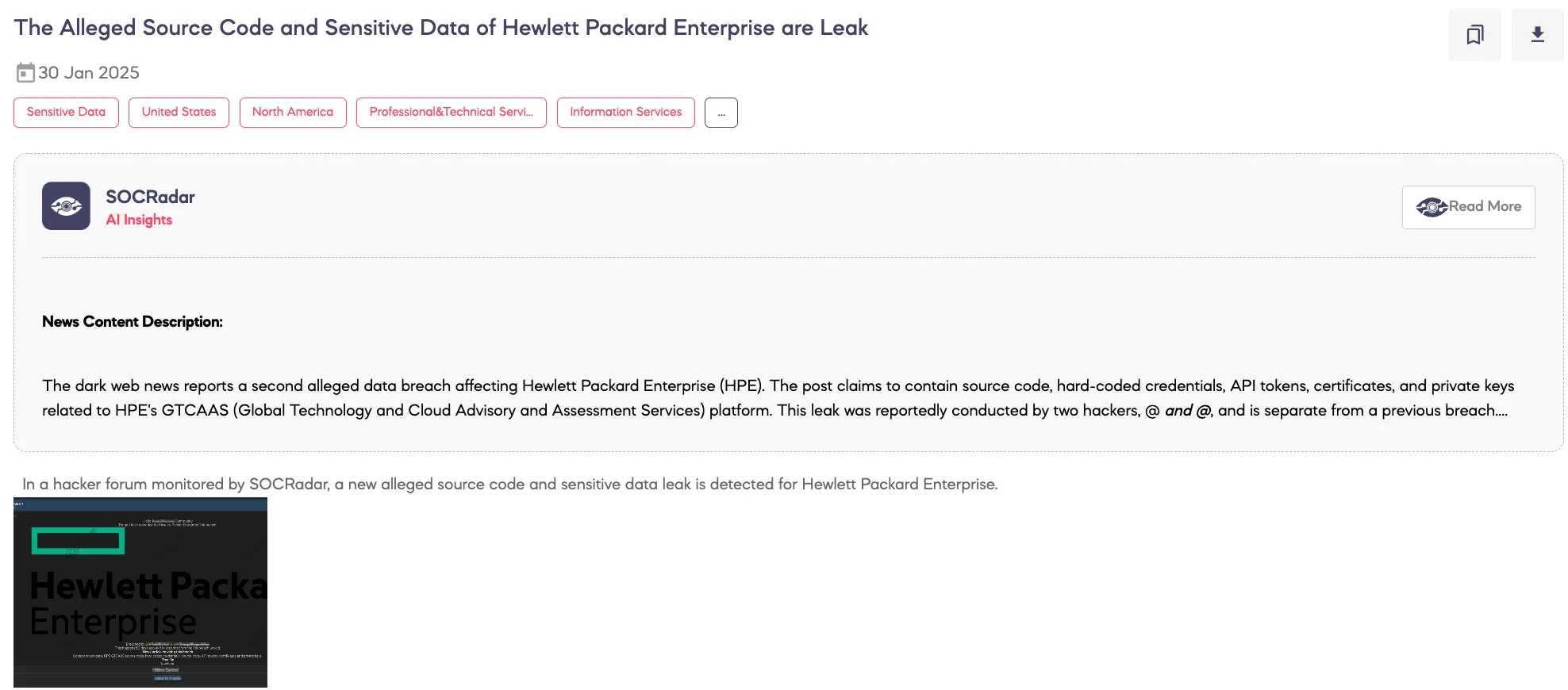
SOCRadar Dark Web Team detected a new post on a hacker forum where the threat actor IntelBroker claims to have leaked source code and sensitive data allegedly belonging to Hewlett Packard Enterprise (HPE). This marks the second alleged breach targeting HPE by the same actor. The exposed data includes HPE GTCAAS source code, hardcoded credentials, API tokens, certificates, and private keys. IntelBroker also shared a file tree structure and a download link.
Alleged Database of Cardinal Health is Leaked
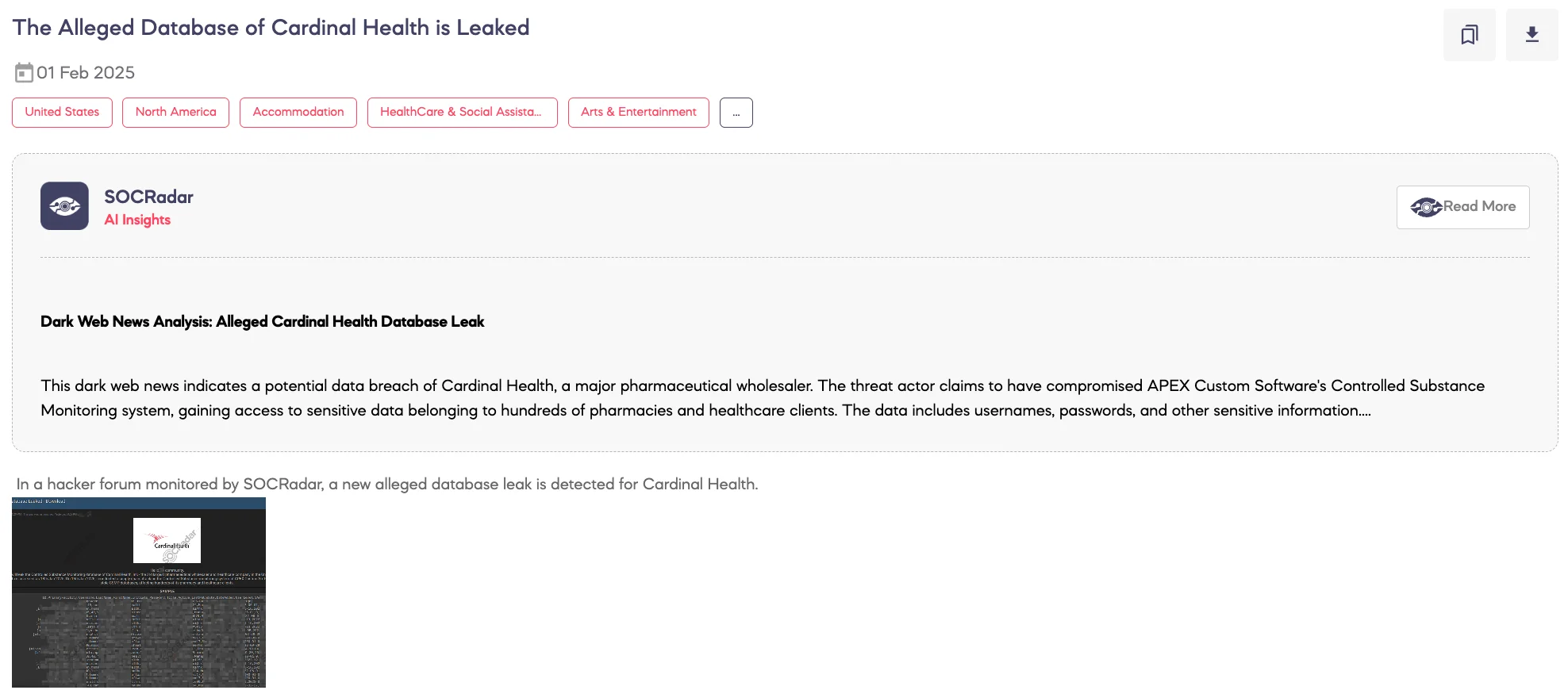
SOCRadar Dark Web Team detected a post on a hacker forum claiming to have leaked the Controlled Substance Monitoring database of Cardinal Health. The threat actor states that the breach stems from a supply chain attack conducted on January 16, 2025, targeting APEX Custom Software, Inc., which allegedly compromised the Controlled Substance Monitoring Program (CSMP) databases of numerous pharmacies and healthcare clients. The leaked data, allegedly as recent as January 18, 2025, includes user credentials and access details.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































