
Palo Alto Firewall Vulnerability (CVE-2025-0108) Under Attack – Are You at Risk?
[Update] February 19, 2025: “Escalating Exploitation of CVE-2025-0108”
Palo Alto Networks has addressed a newly discovered authentication bypass vulnerability, CVE-2025-0108 (CVSS 7.8), that affects the management web interface of its next-generation firewalls. This flaw could allow unauthorized users to execute specific PHP scripts within PAN-OS, posing a threat to system integrity and confidentiality.
Initially, Palo Alto Networks reported no evidence of exploitation, but security researchers have since detected active attempts to exploit this weakness in the wild. With attackers already probing vulnerable systems, organizations must act swiftly to apply patches and reinforce security measures to prevent potential breaches.
How CVE-2025-0108 Works
The vulnerability was identified by researchers while analyzing patches for two previously exploited PAN-OS vulnerabilities – CVE-2024-0012 and CVE-2024-9474.
After noticing architectural inconsistencies in how the PAN-OS management interface processes authentication, the researchers suspected that additional flaws might still be present. Their deeper analysis revealed CVE-2025-0108, an authentication bypass vulnerability that could be exploited due to discrepancies in how Nginx and Apache handle URL requests.
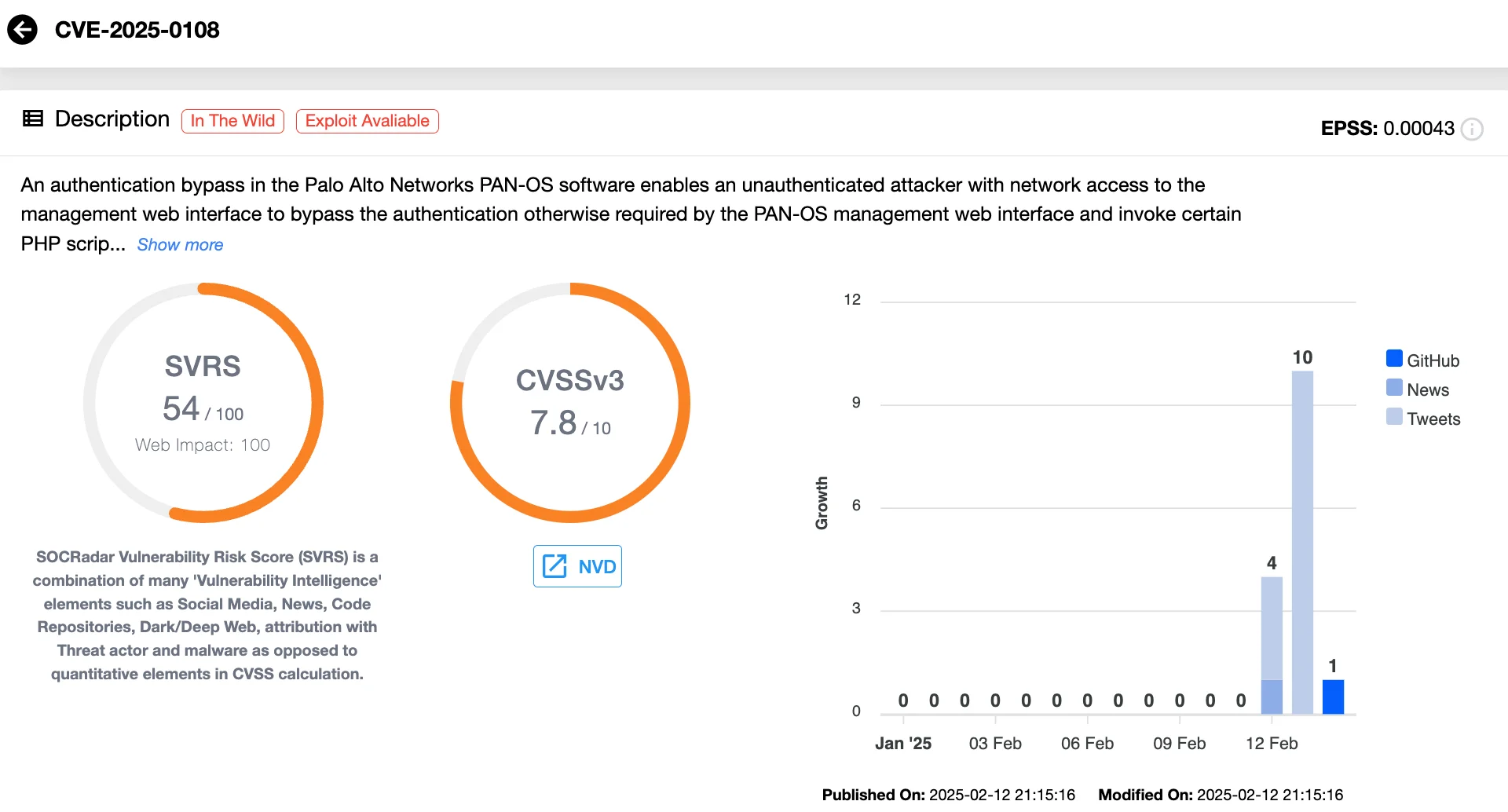
Vulnerability card of CVE-2025-0108 (SOCRadar Vulnerability Intelligence)
This vulnerability enables unauthenticated attackers to execute specific PHP scripts on the firewall’s management interface by exploiting a misalignment between Nginx and Apache’s request handling mechanisms. Although this does not grant full Remote Code Execution (RCE), it does pose risks to data integrity and confidentiality within PAN-OS.
Technical Details of the Exploit
Research revealed that the flaw stems from a path confusion issue between Nginx and Apache’s handling of URL decoding and path normalization. The PAN-OS management interface leverages Nginx as a reverse proxy, which forwards requests to Apache. Authentication is determined based on the X-pan-AuthCheck header, which is set by Nginx. However, due to inconsistencies in how Nginx and Apache interpret and normalize paths, attackers can manipulate URL encoding to bypass authentication checks.
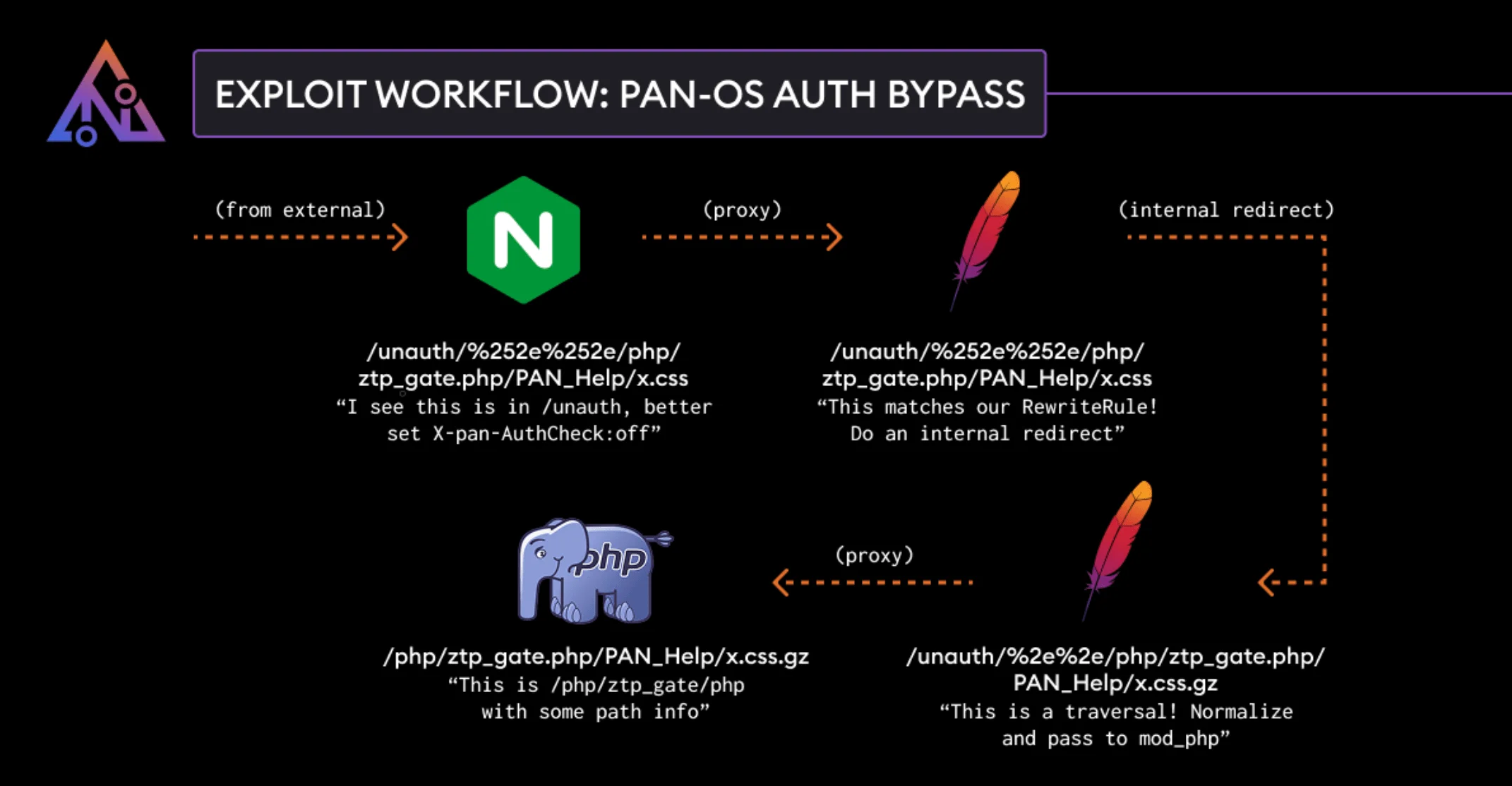
Exploit workflow for CVE-2025-0108 (AssetNote)
- Step 1: Nginx Misinterpretation – A crafted request containing a double-encoded URL (e.g., /unauth/%252e%252e/php/ztp_gate.php/PAN_help/x.css) tricks Nginx into marking it as unauthenticated.
- Step 2: Apache Decoding – Apache processes the same request, decoding it again and applying an internal redirect that normalizes the path.
- Step 3: Authentication Bypass – Since Nginx had already set the authentication flag off, the request proceeds without authentication, allowing access to restricted PHP scripts.
Affected Products and Versions
Several versions of PAN-OS have been identified as vulnerable to CVE-2025-0108, putting affected firewalls at risk of unauthorized access. Organizations using these versions should assess their exposure and take immediate remediation steps. The impacted versions include:
- PAN-OS 11.2 – Versions earlier than 11.2.4-h4
- PAN-OS 11.1 – Versions earlier than 11.1.6-h1
- PAN-OS 10.2 – Versions earlier than 10.2.13-h3
- PAN-OS 10.1 – Versions earlier than 10.1.14-h9
Prisma Access and Cloud NGFW are not impacted by this issue.
When a vulnerability like CVE-2025-0108 is being actively exploited, it’s vital to have visibility into your entire digital footprint. SOCRadar’s Attack Surface Management (ASM) module provides continuous monitoring, ensuring that potential risks are identified across your organization’s systems and even third-party providers.
Monitor your digital assets’ security to prevent exploitation (SOCRadar Attack Surface Management)
By offering timely insights into vulnerabilities, SOCRadar ASM enables security teams to reduce attack surfaces, track vulnerabilities, and take action before threats materialize.
Tracking Exploitation Attempts of CVE-2025-0108 in the Wild
Following the public disclosure of CVE-2025-0108, GreyNoise began tracking active exploitation attempts against vulnerable Palo Alto Networks firewalls. The increasing activity suggests that cybercriminals are actively scanning for and attempting to compromise unpatched firewalls, reinforcing the urgency of timely patch deployment.
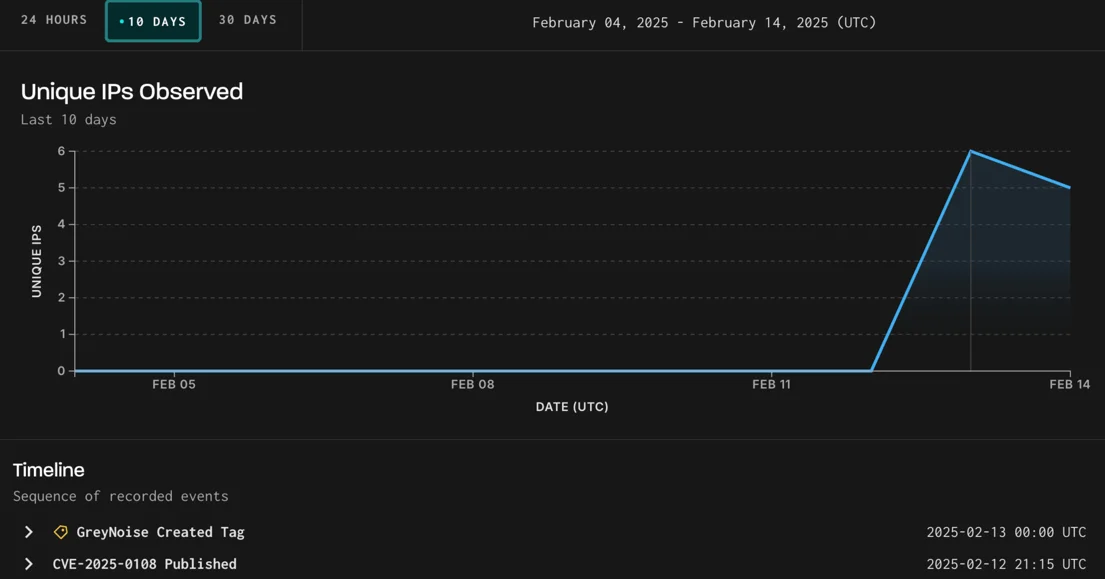
Exploitation activity targeting CVE-2025-0108 in the last 10 days (GreyNoise)
You can find the observed and documented unique IPs attempting to exploit this vulnerability here.
Escalating Exploitation of CVE-2025-0108
The exploitation of CVE-2025-0108, a critical PAN-OS authentication bypass vulnerability, has escalated rapidly. GreyNoise now tracks 25 malicious IPs actively targeting the flaw, a sharp increase from just 2 on February 13. The majority of attack traffic is originating from the United States, Germany, and the Netherlands, signaling a global surge in exploitation attempts.
In response to the growing threat, Palo Alto Networks has officially confirmed active exploitation, classifying the vulnerability as ‘Highest Urgency’ for defenders. Additionally, the Cybersecurity and Infrastructure Security Agency (CISA) has added CVE-2025-0108 to its Known Exploited Vulnerabilities (KEV) catalog, setting a compliance deadline of March 11, 2025 for affected federal organizations.
Organizations using PAN-OS must prioritize patching and mitigation to prevent potential intrusions.
Steps to Secure Your Firewall Against CVE-2025-0108
Palo Alto Networks has rolled out security patches aimed at closing the authentication bypass vulnerability in impacted PAN-OS versions. Organizations using affected firewalls should upgrade to the following patched versions as soon as possible:
- PAN-OS 11.2.4-h4 and later
- PAN-OS 11.1.6-h1 and later
- PAN-OS 10.2.13-h3 and later
- PAN-OS 10.1.14-h9 and later
With active exploitation attempts already detected, organizations using PAN-OS should take immediate action to secure their systems. The most effective step is to apply the latest patches provided by Palo Alto Networks. Additionally, companies should implement strict access controls, ensuring that firewall management interfaces are not publicly exposed, and monitor network logs for signs of potential exploitation.
Reviewing past security advisories can also help identify any misconfigurations that could leave systems vulnerable.
For further details and patch guidance, refer to Palo Alto Networks’ official advisory for CVE-2025-0108.
Streamline Patch Management with SOCRadar’s Vulnerability Intelligence
With vulnerabilities like CVE-2025-0108 in Palo Alto Networks firewalls emerging every day, organizations need an efficient way to respond to such risks. With SOCRadar’s Vulnerability Intelligence, featured under the Cyber Threat Intelligence module, you can easily track new vulnerabilities, analyze risk levels, and get actionable insights to prioritize remediation.
New CVEs and hacker trends (SOCRadar Vulnerability Intelligence)
By integrating SOCRadar’s capabilities, security teams can ensure that patches are deployed quickly and reduce their exposure to cybercriminal activity.




































