
GrassCall: The Malware Draining Crypto Wallets Through Fake Job Interviews
The Web3 and crypto scene, while full of promise and innovation, is increasingly attracting sophisticated security threats. One of the more concerning recent cases is the GrassCall malware campaign, a highly targeted social engineering effort that deceives job seekers with fake job offers and interviews to steal their digital assets.
What Is GrassCall?
GrassCall is a malware campaign built on social engineering, particularly targeting professionals in the blockchain and Web3 sectors. Rather than exploiting technical vulnerabilities, it relies on human trust and curiosity.
In this campaign, cybercriminals create fake companies with polished websites and enticing job postings. These fraudulent listings often appear on legitimate platforms such as LinkedIn, CryptoJobList, and WellFound, promoting remote roles with competitive salaries. After a candidate applies, they’re invited to an interview and asked to download a proprietary video conferencing tool – GrassCall – which appears to be standard software but is actually malicious.
Once installed, the application quietly deploys info-stealing malware such as Rhadamanthys for Windows or Atomic Stealer (AMOS) for macOS. These tools are designed to extract:
- Crypto wallet data
- Browser session cookies
- Saved passwords and credentials
- Browser history and login tokens
This stolen information is then transmitted to attacker-controlled servers, enabling the theft of cryptocurrency and access to sensitive accounts.
How the Attack Functions
Usually, the GrassCall attack sequence consists of these well-coordinated actions:
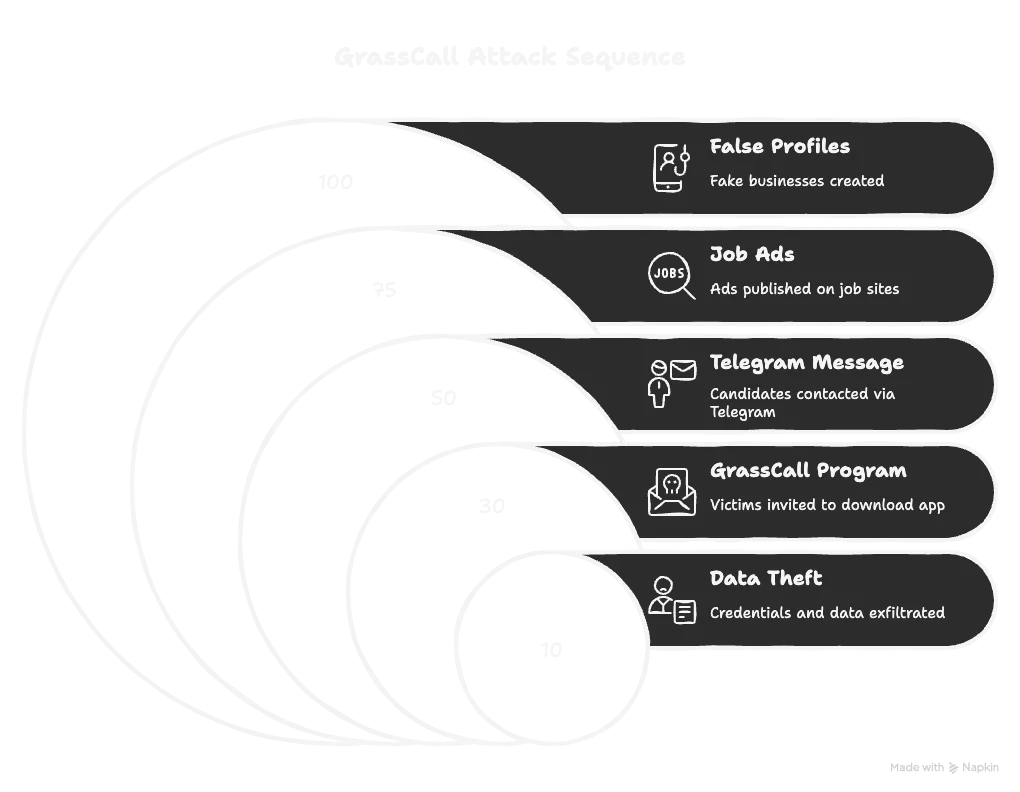
GrassCall attack sequence
- A fake job listing is created under a fabricated company.
- The victim is approached through trusted job boards or professional networks.
- During the interview process, they are asked to download the GrassCall app.
- The malicious app installs an info-stealer in the background.
- Collected data is exfiltrated, leading to the takeover of wallets and accounts.
The campaign is designed for stealth, with minimal user awareness of the breach until it’s too late.
Who Is Being Targeted?
GrassCall primarily targets:
- Job seekers in the Web3 and crypto industry
- Freelancers and remote workers
- Cryptocurrency wallet holders
- Individuals unfamiliar with advanced cybersecurity practices
Attackers exploit these groups’ career ambitions and urgency to bypass typical defenses using trust and social manipulation.
How to Protect Yourself
Preventing attacks like GrassCall requires a combination of awareness and technical safeguards. Consider these practical steps:
Awareness and Validation
- Verify companies and job offers across multiple sources. Look up the domain, team members, and social presence.
- Avoid installing unknown apps for interviews. Reputable employers use tools like Zoom, Microsoft Teams, or Google Meet.
- Be wary of early requests to move communication to Telegram or WhatsApp.
Technical Best Practices
- Enable Multi-Factor Authentication (MFA) on all critical accounts.
- Use endpoint protection or firewalls to prevent unauthorized apps from connecting to the internet.
- Disable remote access tools unless explicitly required.
- Scan suspicious files or links using platforms like VirusTotal or AlienVault OTX.
Conclusion
By means of fictitious interviews, the GrassCall campaign reminds us of how quickly cyber threat actors are changing their social engineering strategies. By combining realistic job opportunities with hidden malware, they bypass traditional technical defenses and exploit human behavior.
At SOCRadar, we emphasize the importance of proactive cybersecurity to stay ahead of such threats. Individuals should research job opportunities carefully, remain skeptical of unusual download requests, and stay updated via threat intelligence feeds.
Organizations, especially those in the crypto space, should monitor for impersonation attempts and train staff, including recruiters, on the growing trend of fake job postings. SOCRadar’s Brand Protection module helps detect fake domains, impersonated social profiles, and suspicious activity across the web, providing early warnings before damage occurs.
SOCRadar Labs, Campaigns page
For ongoing insights into campaigns like GrassCall, the SOCRadar Labs Campaigns page offers updates on trending threat actor tactics, giving both security teams and individuals a clearer view of the evolving threat landscape.



































