
All You Need To Know About the MegaRAC BMC Vulnerabilities
1. What are MegaRAC BMC Vulnerabilities?
Three vulnerabilities have been discovered in American Megatrends Inc.’s MegaRAC Baseboard Management Controller (BMC) software: CVE-2022-40259, CVE-2022-40242, and CVE-2022-2827. The vulnerabilities were discovered by Eclypsium and are referred to as BMC&C.
2. How Critical are the MegaRAC BMC Vulnerabilities?
CVE-2022-40259 and CVE-2022-40242 vulnerabilities have CVSS scores of 9.8, while the CVE-2022-2827 vulnerability has a CVSS score of 7.5 on the National Vulnerability Database (NVD).
MegaRAC BMC is a well-known firmware that is used to connect hardware in cloud environments. Using a vulnerable BMC can also make other devices in an environment vulnerable, and the vulnerability can spread to other vendors and servers.
These vulnerabilities pose a serious risk because they could lead to supply chain attacks. Many server manufacturers, including NVidia, AMD, Asus, Huawei, Lenovo, Quanta, and Dell EMC, use MegaRAC BMC.
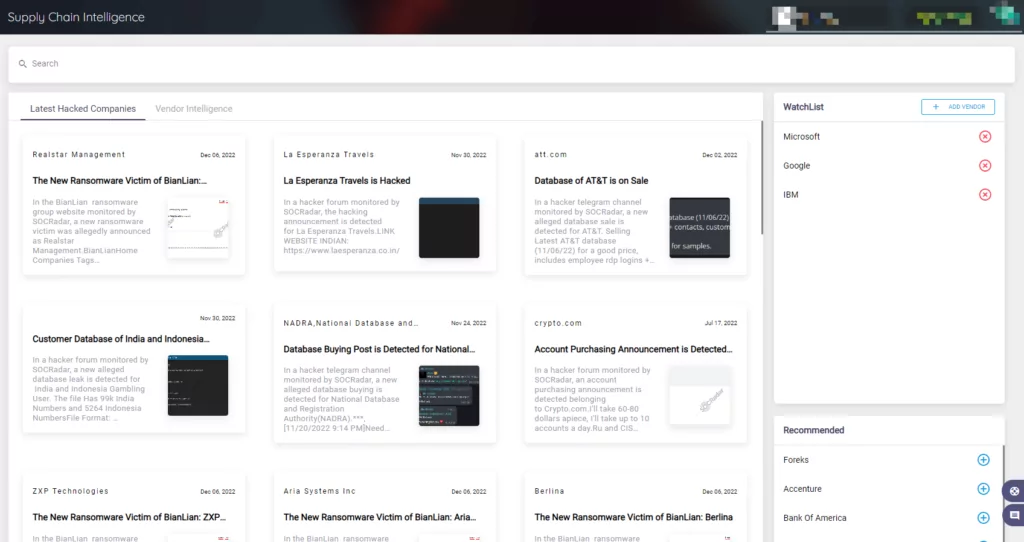
You can keep up with the most recent hacks on companies using the Supply Chain Intelligence tab on the SOCRadar Platform. Businesses can also add particular businesses, like their vendors, to the WatchList.
3. Which Versions are Vulnerable?
|
Products |
Versions |
|
AMI MegaRAC SPx12 |
0 – 6.00 |
|
AMI MegaRAC SPx13 |
0 – 4.00 |
4. How Do the Vulnerabilities Work?
CVE-2022-40259 enables arbitrary code execution with a specially crafted exploit through the Redfish API. This exploit necessitates minimum-level access on the device and directs the attacker to a sysadmin shell (UID = 0).
CVE-2022-40242 is caused by the default credentials for the sysadmin user shell being available with SSH, as found in etc/shadow, with backhints to 2014.
CVE-2022-2827 permits user enumeration via API. In a password reset request, a parameter can be changed to learn if a user exists. The attacker is only required to know the username itself to test this.
5. Are BMC&C Vulnerabilities Actively Exploited in the Wild?
There are no reports or evidence of the vulnerabilities being actively exploited, but exploiting these flaws can result in server physical damage, remote malware deployment, ransomware infection, and remote control of compromised servers.
These flaws could be used by an attacker who has gained access to a data center or administrative network. Any BMC-level vulnerability would likely affect a sizable number of devices and could potentially have an impact on the entire data center as well as the services it offers.
Since standard EDR & AV products focus on the operating system rather than the underlying firmware, detecting exploitation of BMC vulnerabilities is difficult due to their location and nature.
6. Is There Any Mitigation or Patch Available?
Make sure that all remote server management interfaces (like Redfish and IPMI) and BMC subsystems in their environments are located on their dedicated management networks, not on any public networks.
Make sure critical firmware and remote server management subsystems (like MegaRAC, iDRAC, iLO, etc.) are covered in vulnerability assessments.
Enterprises must also make sure that every piece of critical firmware in servers is regularly checked for signs of compromise or unauthorized changes. You must check the supply chain of new equipment and determine that all new servers have the most recent firmware installed and all critical vulnerabilities patched.
Additionally, ensure only administrators with ACLs or firewalls can access the internal BMC interface.



































