
Alleged Sales: AMD Breach, U.S. Tax Portal Access, and Fortinet Exploit
Recent findings by the SOCRadar Dark Web Team highlight several significant cyber threats targeting various organizations. Among the most notable incidents are the alleged unauthorized sale of portal access for a U.S. tax company, enabling access to sensitive financial and tax documents. Additionally, IntelBroker claims to have breached AMD’s internal communications, while a new database leak from the University of Toronto has surfaced. Furthermore, the National Research Council of Italy’s project data has allegedly been compromised, and a Remote Code Execution (RCE) exploit for Fortinet devices is being sold.
Receive a Free Dark Web Report for Your Organization:
Alleged Unauthorized Portal Access Sale is Detected for an American Tax Company
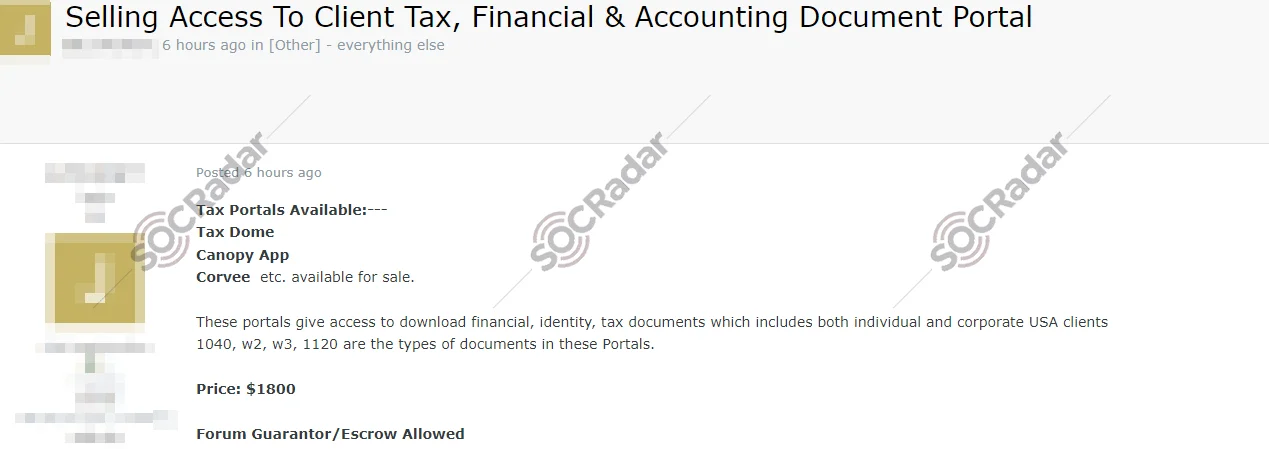
The SOCRadar Dark Web Team detected a post on a hacker forum advertising the unauthorized sale of portal access allegedly belonging to a tax company based in the United States. The threat actor claims that the portals available for purchase, including Tax Dome, Canopy App, and Corvee (popular tax management platforms) allow access to download sensitive financial, identity, and tax documents for individual and corporate clients in the USA. The documents mentioned include critical forms such as 1040, W-2, W-3, and 1120. The access is being offered for $1,800, with the option of using a forum guarantor or escrow service to facilitate the transaction.
IntelBroker Threat Actor Claims to Sell AMD’s Internal Communications
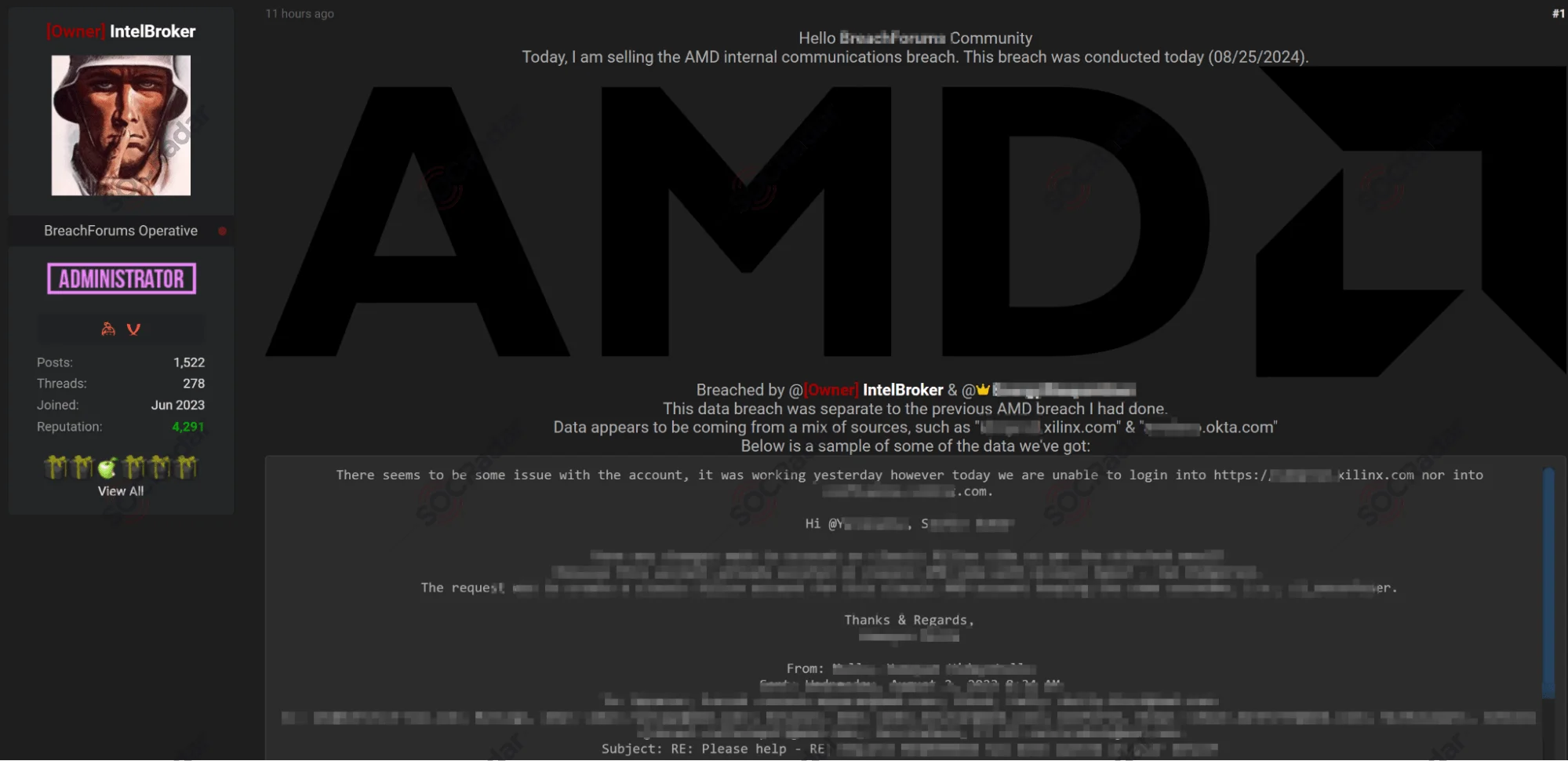
The SOCRadar Dark Web Team detected a post on a hacker forum channel where a new data breach claim has emerged. The threat actor, IntelBroker, alleges that they have breached AMD’s (Advanced Micro Devices, a multinational semiconductor company specializing in computer processors and related technologies) internal communications as of August 25, 2024. This breach is purported to be distinct from a previous incident involving AMD on June 17, 2024.
Alleged Log of Governmental Accounts is on Sale
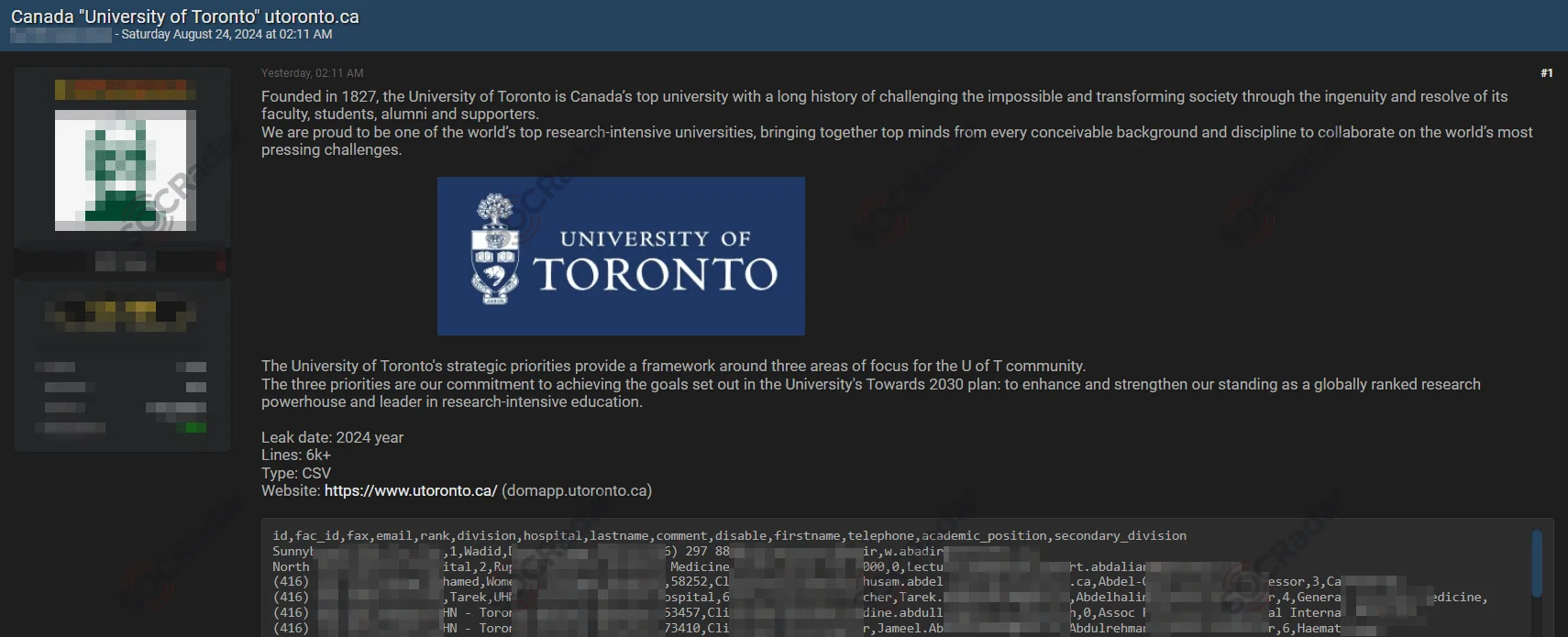
The SOCRadar Dark Web Team detected a post on a hacker forum claiming an alleged database leak from the University of Toronto. The alleged leak, dated 2024, supposedly contains over 6,000 records in CSV format, including sensitive details such as faculty IDs, emails, academic positions, and more. The threat actor emphasized the university’s prestigious status and extensive research history, potentially indicating the value of the compromised data.
Alleged Customer Database of National Research Council of Italy is Leaked
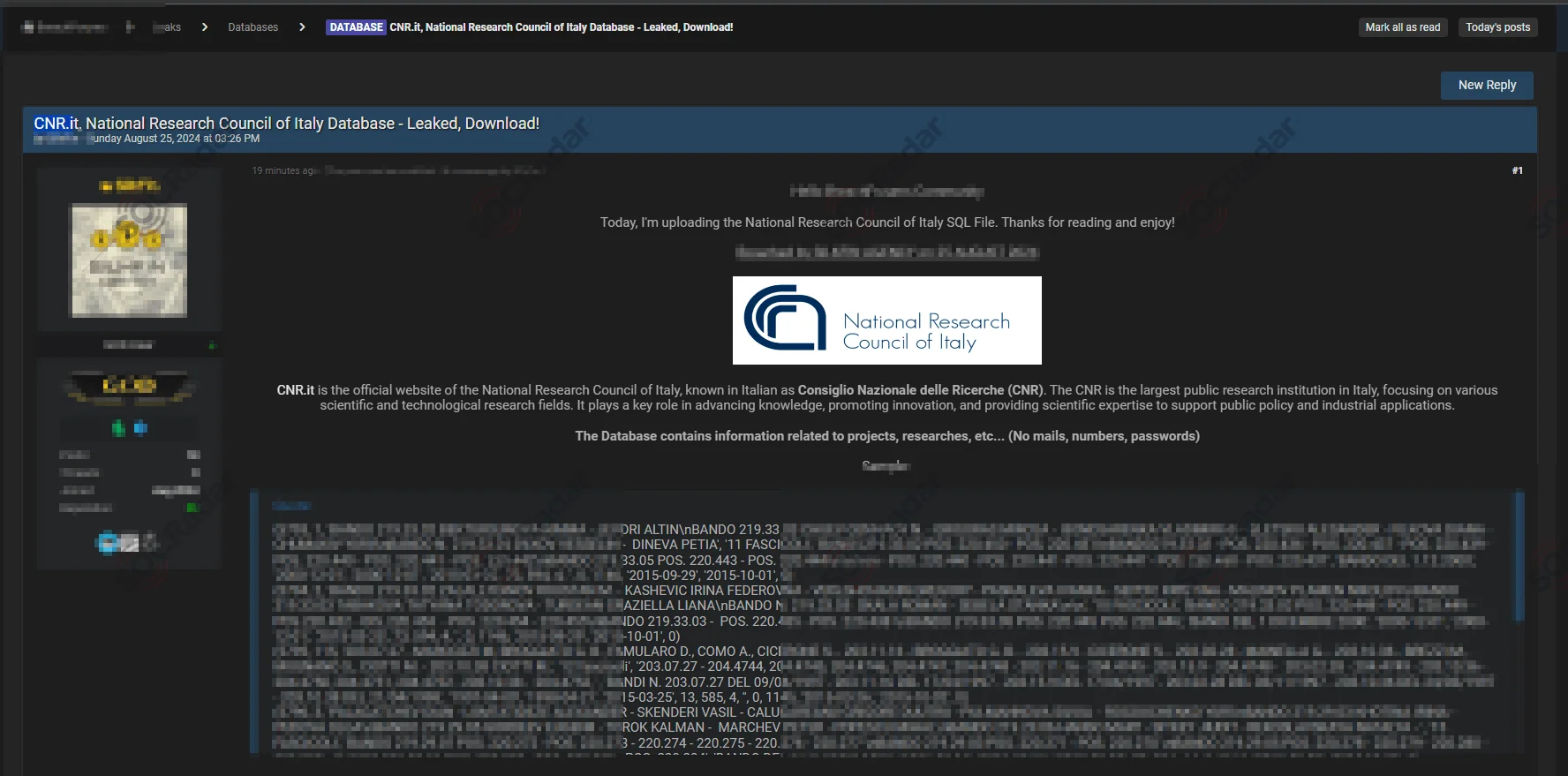
The SOCRadar Dark Web Team detected a post on a hacker forum claiming an alleged database leak from the National Research Council of Italy (CNR). The threat actor states that the database contains project and research information but excludes emails, phone numbers, and passwords.
Alleged RCE Exploit of Fortinet is on Sale
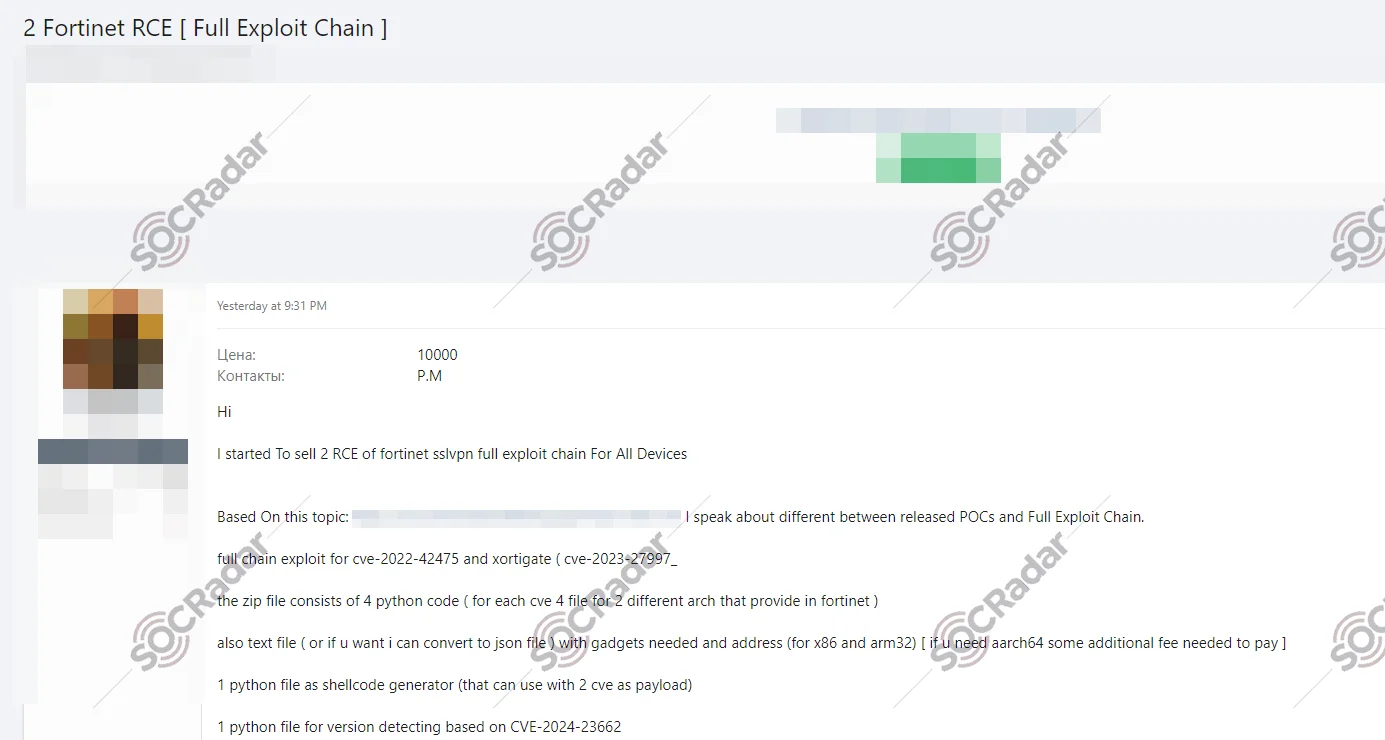
The SOCRadar Dark Web Team has identified a post on a hacker forum advertising the sale of an alleged Remote Code Execution (RCE) exploit for Fortinet devices. The threat actor claims to offer a full exploit chain for CVE-2022-42475 and CVE-2023-27997, including Python scripts and necessary gadgets for different architectures (x86 and ARM32). The package reportedly includes a shellcode generator, a version detection script, and a tutorial for implementation. The seller is open to customizing the files for additional architectures upon request.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































