An Overview of Microsoft March 2024 Patch Tuesday: Severe RCE and Privilege Escalation Vulnerabilities
Microsoft has released Patch Tuesday for March 2024, which addresses 61 security vulnerabilities. Two of the vulnerabilities are classified as critical in maximum severity in Microsoft advisories; this month’s update does not involve any zero-day vulnerabilities.
During the February 2024 Patch Tuesday, some vulnerabilities that had been addressed later emerged as zero-days, highlighting the potential for sudden changes in the threat landscape. As of the March 2024 Patch Tuesday, although there are no zero-day vulnerabilities, the situation may evolve in the future.
The March 2024 Patch Tuesday is focused on a range of vulnerabilities; here are the number of vulnerabilities in each category:
- 18 Remote Code Execution (RCE) Vulnerabilities
- 24 Elevation of Privilege (EoP) Vulnerabilities
- 6 Denial of Service (DoS) Vulnerabilities
- 2 Spoofing Vulnerabilities
- 6 Information Disclosure Vulnerabilities
- 1 Cross-site Scripting (XSS) Vulnerabilities
- 3 Security Feature Bypass Vulnerabilities
There is also a ‘Compressed Folder Tampering Vulnerability’ that affects Windows but does not fit into the vulnerability categories we have used in our overviews of Patch Tuesday updates.
Let’s now proceed to summarize the vulnerabilities that have been addressed.
Important RCE and DoS Vulnerabilities in Windows Hyper-V: CVE-2024-21407 and CVE-2024-21408
Microsoft advisories list two vulnerabilities with maximum of critical severity, both of which affect Windows Hyper-V.
One of them is an RCE vulnerability identified as CVE-2024-21407, with a high severity score of 8.1. According to Microsoft, an authenticated attacker on a guest VM could exploit the vulnerability by sending specially crafted file operation requests to the VM’s hardware resources, enabling RCE on the host server.
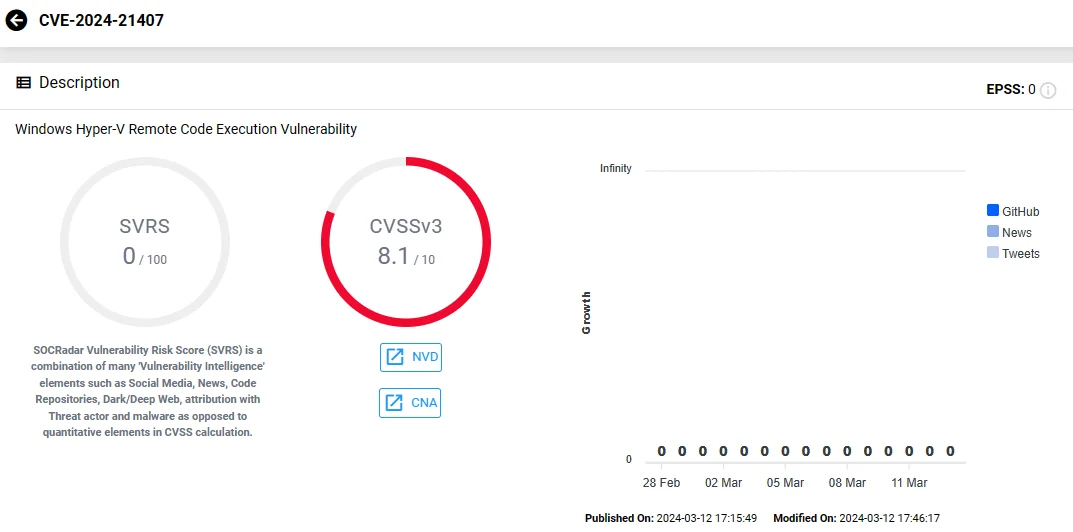
CVE-2024-21407 (SOCRadar Vulnerability Intelligence Module)
To successfully exploit CVE-2024-21407, an attacker must first gather environment-specific information and take additional steps to prepare the target environment.
The other vulnerability, CVE-2024-21408, has a lower CVSS score of 5.5. At the time of the Microsoft advisory’s release, there is little information available about this vulnerability, other than the fact that it has a significant impact on availability by causing a Denial-of-Service (DoS) in Windows Hyper-V.
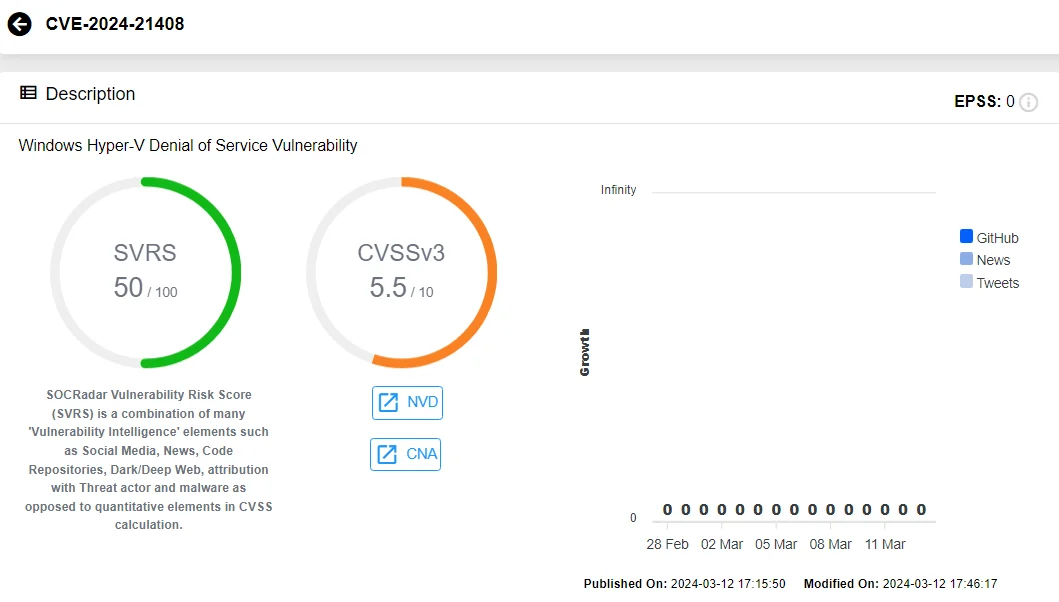
CVE-2024-21408 (SOCRadar Vulnerability Intelligence Module)
By providing detailed information about vulnerabilities and tracking related activities such as exploitation and hacker trends, the SOCRadar Vulnerability Intelligence module enables organizations to prioritize and address the most critical security risks effectively.
With access to actionable intelligence, organizations can enhance their security posture, mitigate potential threats, and stay resilient against evolving cyber threats.
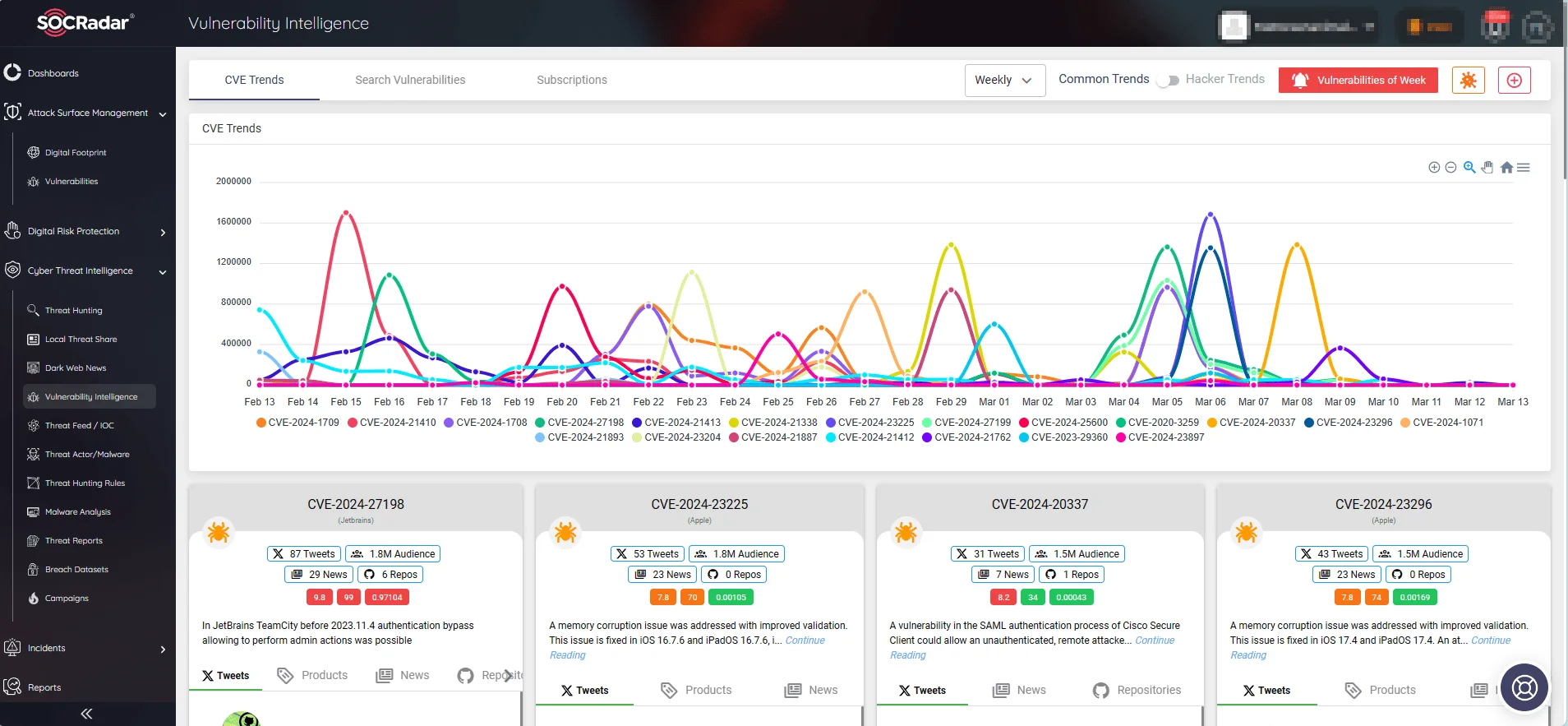
Vulnerability Intelligence module within SOCRadar XTI offers organizations continuous monitoring and insights into emerging security vulnerabilities.
Critical Vulnerabilities Fixed in Open Management Infrastructure, Azure Kubernetes Service: CVE-2024-21334 and CVE-2024-21400
In the March 2024 Patch Tuesday update, there are vulnerabilities that Microsoft classified as ‘Important’ in terms of maximum severity but are critical according to their CVSS score.
CVE-2024-21334 (CVSS: 9.8), an RCE in Open Management Infrastructure, is the highest-scored vulnerability in the update.
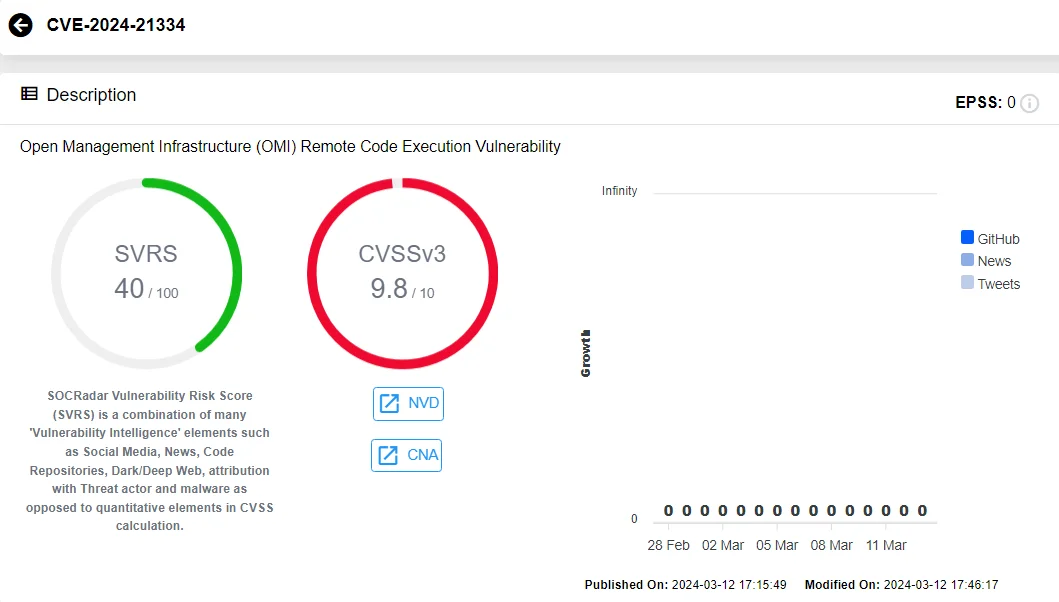
CVE-2024-21334 (SOCRadar Vulnerability Intelligence Module)
A remote unauthenticated attacker could connect to the OMI instance via the internet and send specially crafted requests, triggering a use-after-free vulnerability, as stated in the advisory. Microsoft recommends that customers running affected versions of SCOM (System Center Operations Manager) update to OMI version 1.8.1-0 to safeguard against this vulnerability.
If unable to update, customers can protect against this vulnerability by disabling the incoming ports for OMI on Linux machines that do not require network listening.
CVE-2024-21400 (CVSS 9.0), an Elevation of Privilege vulnerability in Azure Kubernetes, has the second-highest CVSS score in the March 2024 Patch Tuesday.
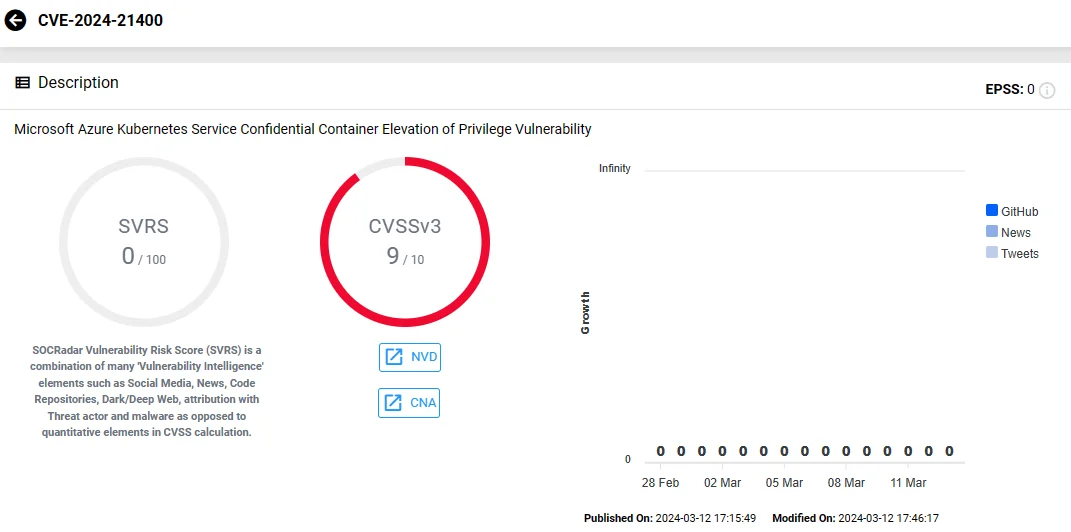
CVE-2024-21400 (SOCRadar Vulnerability Intelligence Module)
As reported by Microsoft, successful exploitation of CVE-2024-21400 requires an attacker to prepare the target environment to improve exploit reliability; it may result in credential theft, and enable access to an untrusted AKS (Azure Kubernetes Service) node and AKS Confidential Container to take over confidential guests and containers beyond the network stack to which it is bound.
To be protected from this vulnerability, Microsoft states customers should ensure they are running the latest version of az confcom and Kata Image.
Which March 2024 Patch Tuesday Vulnerabilities Are Likely to be Exploited?
Some high and medium severity vulnerabilities addressed in the March 2024 Patch Tuesday update are considered ‘more likely’ to be exploited, and there are no workarounds available. These vulnerabilities are:
- CVE-2024-21433 (CVSS: 7.0) – Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2024-21437 (CVSS: 7.8) – Windows Graphics Component Elevation of Privilege Vulnerability
- CVE-2024-26160 (CVSS: 5.5) – Windows Cloud Files Mini Filter Driver Information Disclosure Vulnerability
- CVE-2024-26170 (CVSS: 7.8) – Windows Composite Image File System (CimFS) Elevation of Privilege Vulnerability
- CVE-2024-26182 (CVSS: 7.8) – Windows Kernel Elevation of Privilege Vulnerability
- CVE-2024-26185 (CVSS: 6.5) – Windows Compressed Folder Tampering Vulnerability
It is highly recommended that you review the vulnerabilities that may impact your business’s digital environment and promptly apply the patches to mitigate potential security threats. For further details on the vulnerabilities addressed in the March 2024 Patch Tuesday update, refer to the latest Microsoft Release Note.
Attack Surface Management (ASM) is a critical component of SOCRadar XTI, allowing organizations to proactively assess and respond to security vulnerabilities within their perimeter. By quickly identifying potential points of attack, ASM enables organizations to strengthen their defenses and mitigate risks before they escalate.
Organizations can stay ahead of cyber threats by using comprehensive vulnerability assessment and real-time monitoring tools of SOCRadar to ensure a strong security posture.
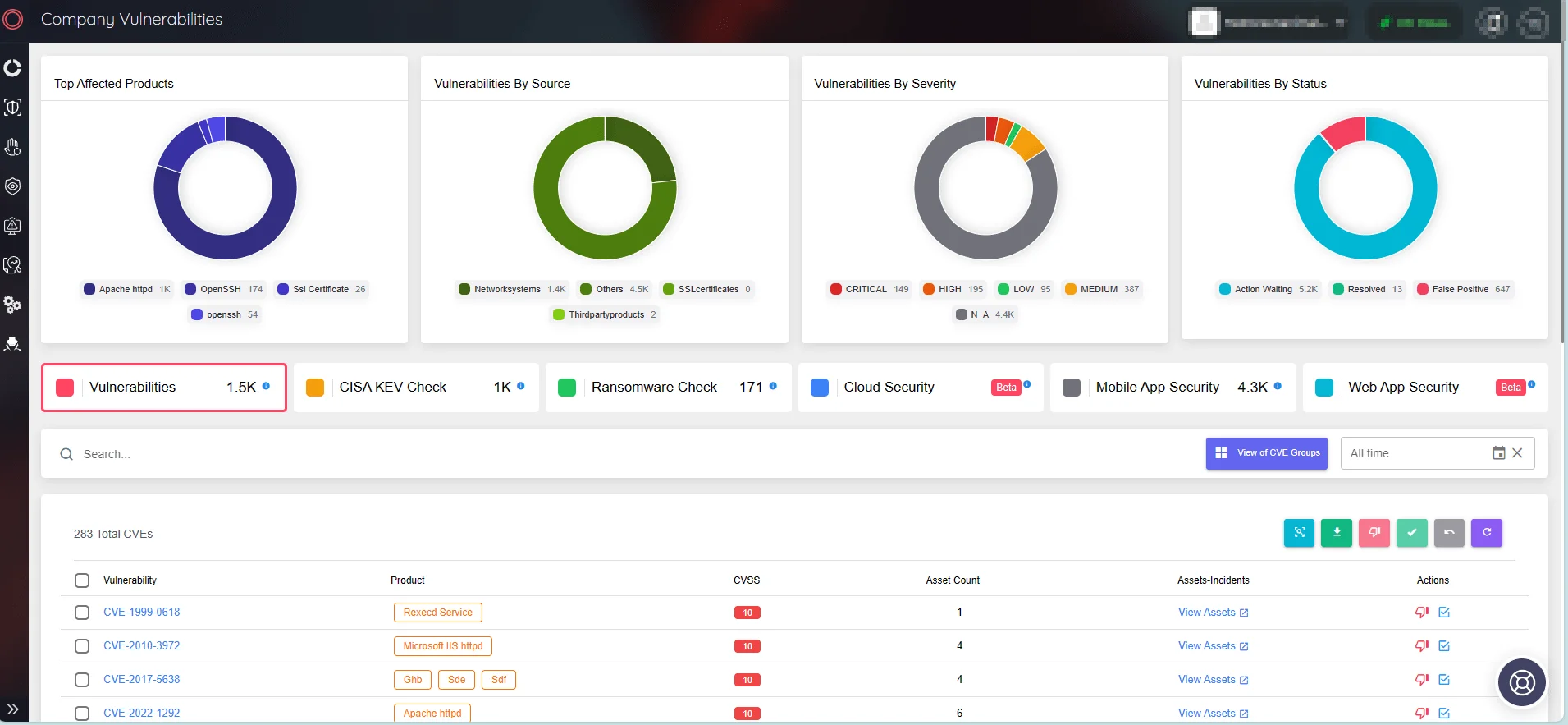
SOCRadar’s Attack Surface Management, Company Vulnerabilities page.
Experience the power of the SOCRadar XTI platform with our Free Edition (Freemium):




































