
Android RAT Tool, Asus Taiwan Access, and Palo Alto Exploit Detected on Dark Web
A wave of cyber threats has been uncovered in recent investigations by SOCRadar’s Dark Web Team, including a service offering bank accounts in German banks tailored for dropshipping across the EU. Additionally, a new Android RAT tool (Remote Access Trojan) bypassing Play Store protections is being sold.
Other findings include a leaked patient database from an Argentina hospital, 15 million leaked phone records from Claro Peru, and an unauthorized access sale targeting Asus Taiwan’s firewall systems. Lastly, a zero-day RCE exploit for Palo Alto Networks is on the market, posing a critical risk to cybersecurity defenses.
Receive a Free Dark Web Report for Your Organization:
Alleged Bank Account Providing Service is Detected
SOCRadar Dark Web Team detected that a threat actor is offering bank account provisioning services on a hacker forum, specifically targeting users within the European Union (EU).
The threat actor claims to be providing bank accounts, currently limited to German banks, and is offering tailored conditions for dropshipping operations across any EU country. They express a preference for long-term business relationships, aiming to customize bank selections, account conditions, and other specifics according to each client’s needs.
New Android RAT Tool Sale is Detected
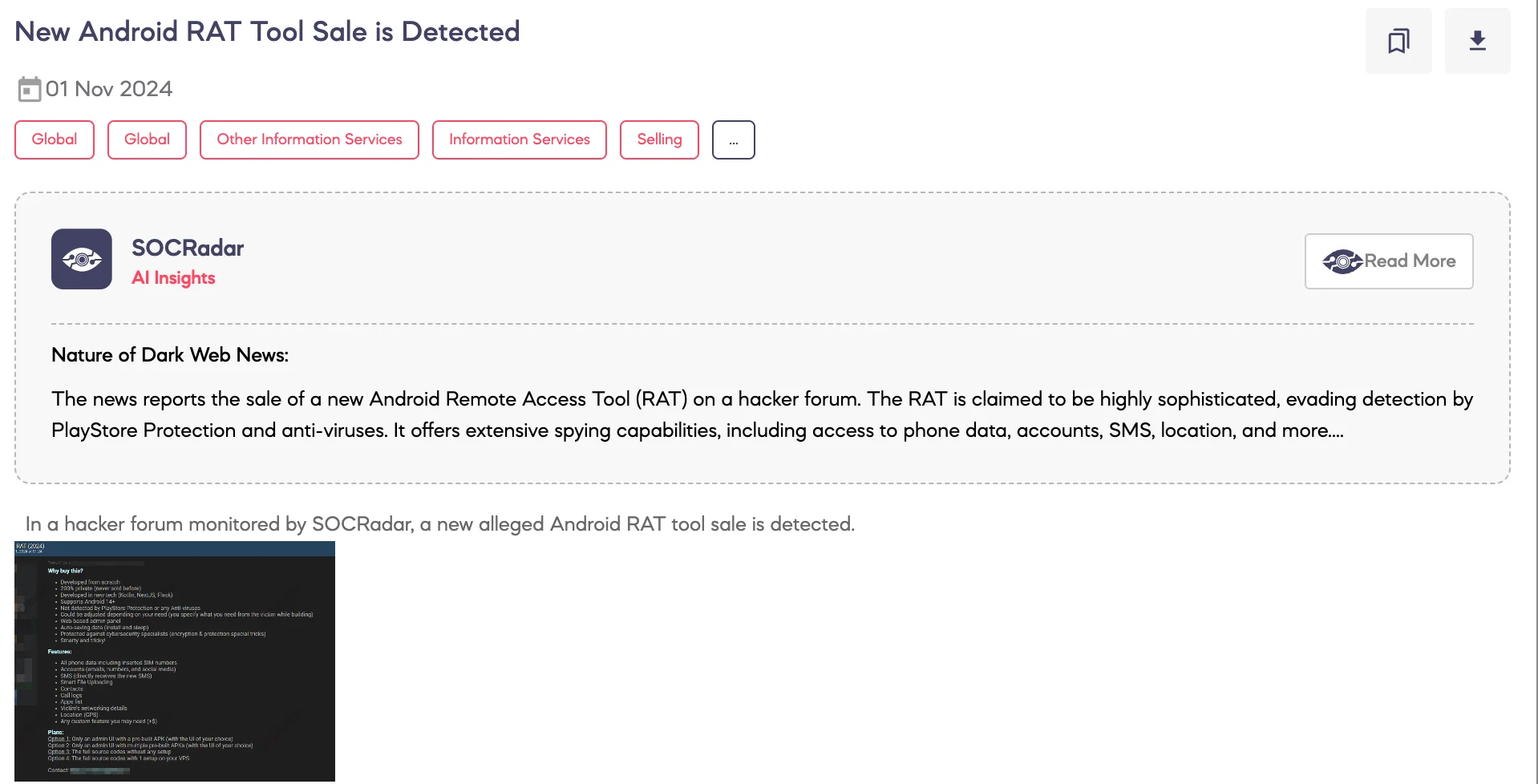
SOCRadar Dark Web Team detected that a threat actor is allegedly selling a new Android Remote Access Trojan (RAT) tool on a hacker forum.
The threat actor claims the RAT tool was developed from scratch using technologies like Kotlin, NextJS, and Flask, and is marketed as “200% private,” having never been sold before. This tool is designed to work on devices running Android 14 and above, bypassing Play Store protections and antivirus software. It includes a web-based admin panel with auto-saving data capabilities and offers encryption techniques purportedly to evade detection by cybersecurity specialists.
According to the threat actor, the tool’s features include access to all phone data, SIM card numbers, accounts (emails, phone numbers, and social media), SMS interception, contacts, call logs, installed apps, network details, GPS location, and additional custom features on request for an extra fee. The seller provides multiple purchase options: a pre-built APK with a custom UI, multiple APKs, the full source code without setup, or the full source code with setup on a VPS.
Alleged Customer Database of Hospital Italiano is Leaked
SOCRadar Dark Web Team detected that a threat actor claims to have leaked a customer database from Hospital Italiano in Argentina on a hacker forum.
The threat actor claims that the data leak involves sensitive information of approximately 1,130,643 medical patients, including personal data and photos of Hospital Italiano. The sample data provided by the actor includes fields such as personal identifiers, names, gender, birth dates, documentation details, addresses, and contact numbers. Additional data fields include location information with specific address details, and contact information including mobile and fax numbers.
Alleged Database of Claro Peru is Leaked
SOCRadar Dark Web Team detected that a threat actor is allegedly leaking a database containing information from Claro Peru on a hacker forum.
The threat actor claims to have obtained a database of 15 million leaked phone records from Claro Peru, dated 2023. The actor has shared a download link to access the leaked data, which is publicly available on the forum.
Alleged New 0-Day RCE Exploit for Palo Alto Networks is on Sale
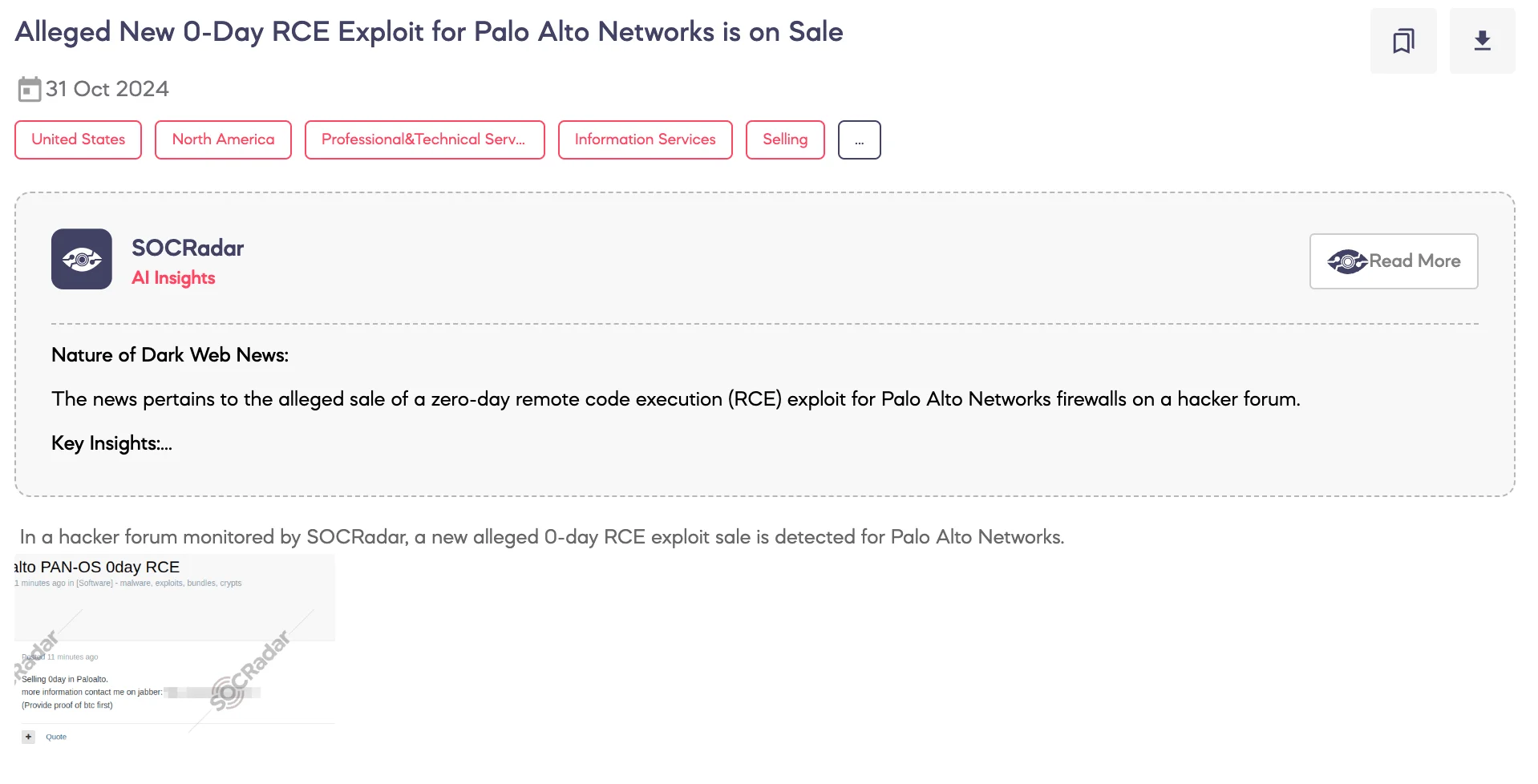
SOCRadar detected a post on a hacker forum where a threat actor claims to be selling a new zero-day Remote Code Execution (RCE) exploit targeting Palo Alto Networks, a leading cybersecurity company.
The threat actor states they have an undisclosed zero-day exploit that impacts Palo Alto Networks’ systems and are offering it for sale. Interested buyers are directed to contact the seller via Jabber, with the requirement to provide proof of Bitcoin funds before any additional information is disclosed.
Alleged Unauthorized Initial Access Sale is Detected for Asus Taiwan
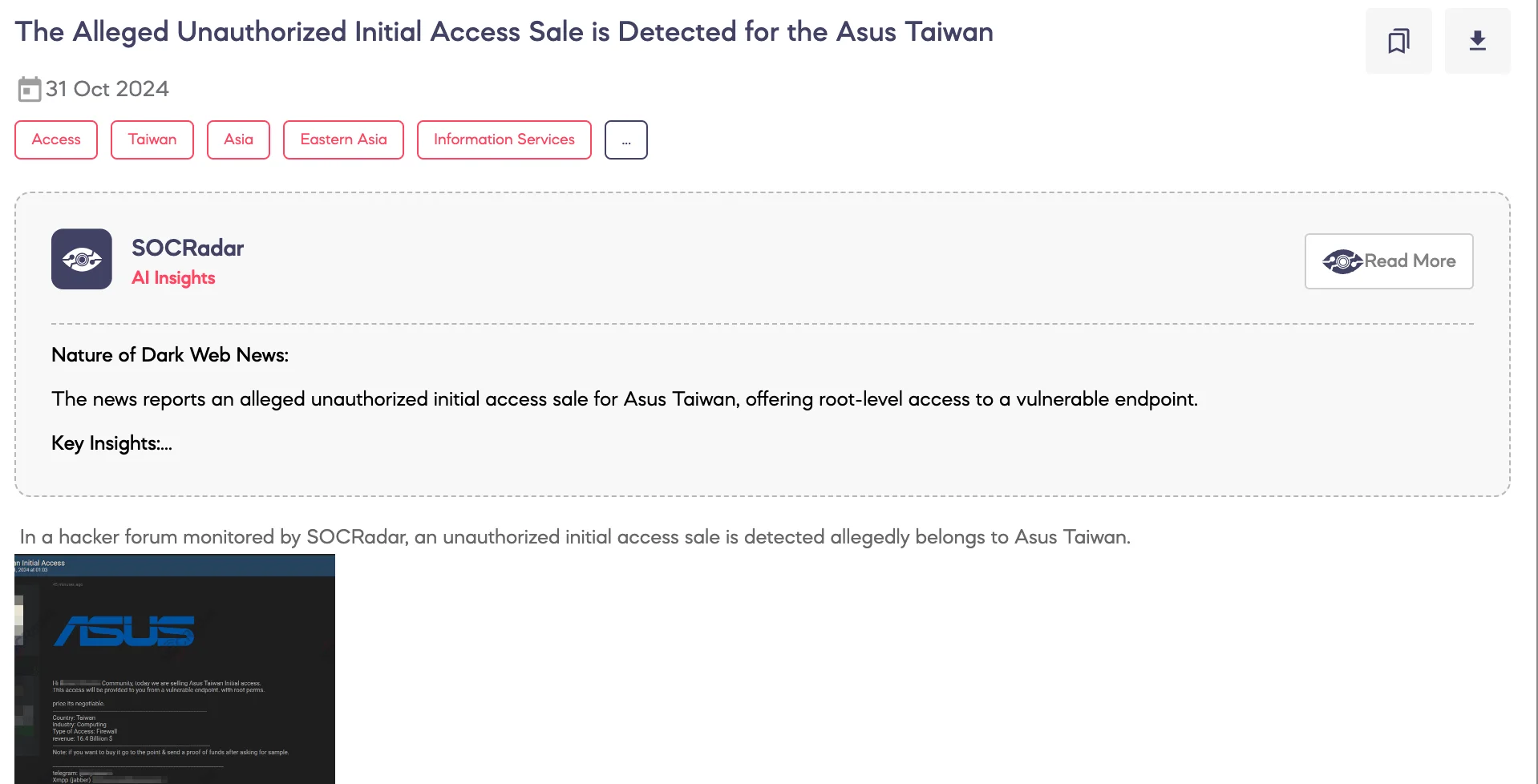
SOCRadar Dark Web Team detected a post on a hacker forum in which a threat actor claims to offer unauthorized initial access to Asus Taiwan.
The threat actor claims to provide access to Asus Taiwan’s network via a vulnerable endpoint with root permissions, specifically targeting the organization’s firewall systems. They have indicated that the price is negotiable, based on offers from potential buyers. Asus Taiwan, a major company in the computing industry with an estimated revenue of $16.4 billion, could face significant risks if this unauthorized access is legitimate.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.


































