
Android Spyware SpinOk Affects Over 420M Installations on Google Play
Researchers have discovered a new Android trojan, and they track it as “SpinOk.” The trojan is distributed as an advertisement Software Development Kit (SDK) on Google Play Store and has affected numerous mobile apps. Collectively, the infected apps have garnered over 420 million downloads.
The SpinOk trojan is a dangerous spyware that can steal your information and compromise the security of your device. Mobile app users should be wary of this threat and take steps to protect themselves.
Which Popular Apps Are Affected by The SpinOk SDK?
Researchers from the antivirus software and solutions developing company Dr. Web, who discovered SpinOk, state that it can steal private data from user devices and send it to a remote server. The SpinOk spyware deceptively appears as a set of engaging activities, like mini-games with daily rewards, to keep users hooked on the apps for extended periods.
Although Google has addressed the issue, users who previously downloaded these apps remain vulnerable. Below are some of the widely-used mobile applications that have been infected by the SpinOk trojan, along with their installation counts:
- Noizz – video editor with music – 100,000,000+
- Zapya – File Transfer, Share – 100,000,000+
- VFly – video editor & video maker – 50,000,000+
- MVBit – MV video status maker – 50,000,000+
- Biugo – video maker & video editor – 50,000,000+
- Crazy Drop – 10,000,000+
- Cashzine – Earn money reward – 10,000,000+
- Fizzo Novel – Reading Offline – 10,000,000+
- CashEM – Get Rewards – 5,000,000+
- Tick – watch to earn – 5,000,000+
You can find a list of all apps affected by the SpinOk spyware on GitHub.
SpinOk SDK Gathers Data and Performs Malicious Actions
When the trojan SDK is initialized, it connects to a C2 server and sends a request with extensive technical information about the infected device.
The information transmitted by the trojan SDK includes data from the Android device’s sensors to verify that it is not running in a restricted environment known as a sandbox, which researchers commonly use to analyze suspicious Android applications.
The SDK ignores device proxy settings to ensure its security, allowing it to hide network connections during analysis. It then downloads a list of URLs from a remote server for displaying expected mini-games.
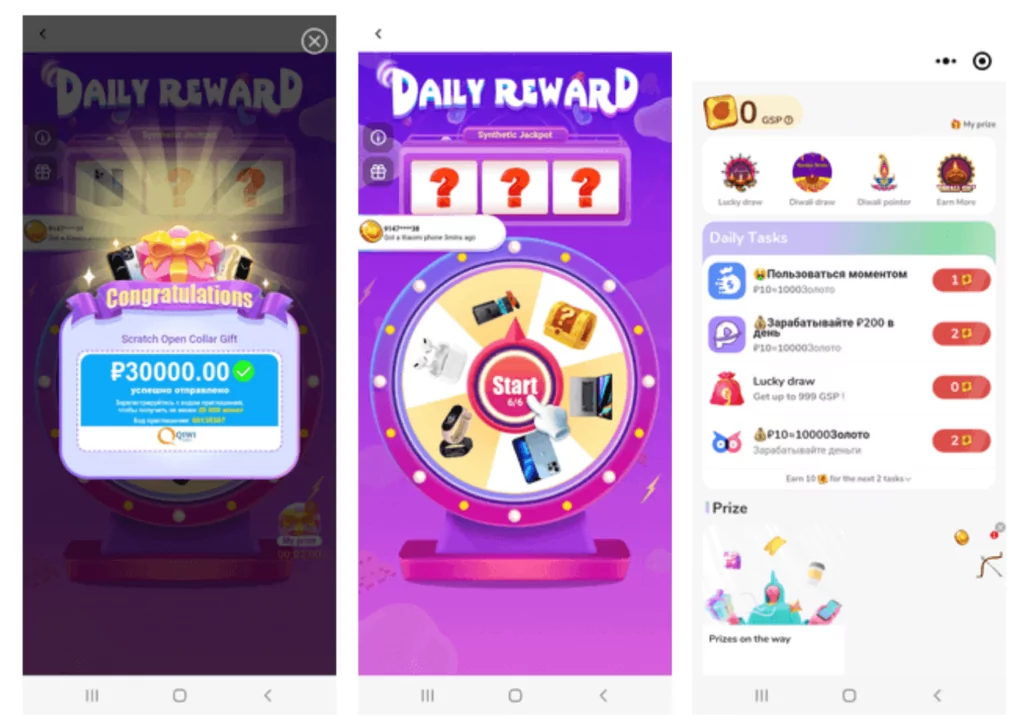
Although the mini-games are visible to the app’s users through the WebView interface, Dr. Web reports that the SDK can perform additional malicious actions in the background. These actions include listing files in directories, searching for specific files, uploading files from the device, and replacing the contents of the device’s clipboard.
The file exfiltration feature is particularly concerning. It can expose private images, videos, and documents. Additionally, the SDK’s clipboard manipulation allows its operators to steal passwords and credit card data and hijack cryptocurrency payments. They can redirect payments to their own crypto wallet addresses.
Enhance the Security of Your Mobile App With SOCRadar
Similar infections on applications are commonly caused by third-party breaches and supply chain attacks; it is unclear if any of the developers included SpinOk spyware on purpose.
If you use an app affected by the SpinOk malware, update to the most recent versions available on Google Play to avoid data theft. It is recommended to uninstall any apps that do not have a fix and to use an antivirus tool to ensure there are no spyware remnants.
With SOCRadar’s Mobile App Security (MAS) module, you can protect your organization’s mobile apps and avoid reputational damage caused by fake apps.
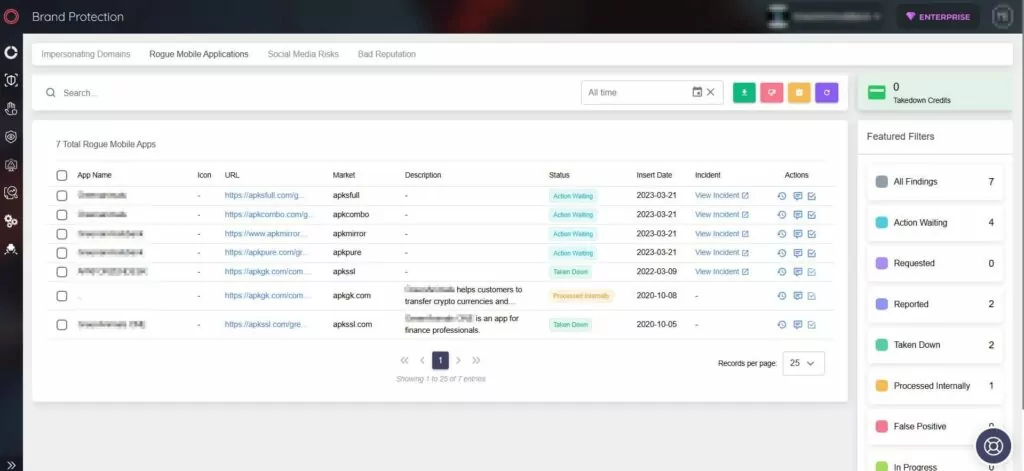
SOCRadar MAS offers a range of features to enhance your mobile app security:
- Malicious App Detection: Quickly identify malicious apps similar to your own in app stores using the APK code.
- Behavior Monitoring: Get instant notifications of any unusual app behavior in real-time, enabling you to take timely action.
- Server Tracking: Track the servers your app communicates with, helping you identify potential threats.
- App Ecosystem Insights: Gain awareness of potential threats in other apps that your app interacts with.
- Continuous Security Checks: Stay ahead of threat actors by performing regular security checks and staying updated on the latest risks.




































