
Guarding the Gates: An Exploration of the Top 10 Supply Chain Attacks
Once upon a time, an anxious emperor, having heard a prophecy of his daughter’s demise by a snakebite, ordered the construction of an isolated fortress. This was the Maiden’s Tower, rising from the heart of the Bosphorus. The daughter was relocated to this distant haven, shielded from the world and, by extension, the foreseen serpent. Yet, destiny played its part. A seemingly innocent basket of fruits delivered to the tower concealed the deadly snake, which, against all odds and defenses, fulfilled the prophecy.
In our digital age, this tale reverberates. The tower is our network, the princess, our precious assets. The firewall stands tall, yet the serpent – a threat actor – is crafty, infiltrating through an unsuspecting ‘fruit basket’ – the trusted supply chain. Thus, the story whispers a cautionary tale – beware of what lies hidden in your supplies.

In today’s digital era, the complex interconnections of an organization’s supply chain may become its Achilles’ heel. As firms grow more reliant on their collaborations with partners and suppliers, they inadvertently subject themselves to the mounting danger of supply chain attacks. For organizations to protect themselves against these cyber threats, it is essential to recognize the most impactful incidents and draw valuable lessons from them.
This article investigates the ten most significant supply chain attacks that have considerably impacted the cybersecurity landscape, such as the APT29’s SolarWinds compromise, the recent GoAntywhere MFT, and 3CX supply chain compromises.
By analyzing the techniques utilized by cyber adversaries, the essential outcomes for targeted organizations, and the lessons extracted from these occurrences, this article delivers valuable insights to organizations on enhancing their security measures and protecting their assets from future threats targeting the supply chain.
1- SolarWinds Supply Chain Compromise
Overview of the attack:
In late 2020, a massive cyber-espionage campaign, known as the SolarWinds Attack, compromised the software of SolarWinds’ Orion platform. The attacker, APT29 (Cozy Bear), inserted a backdoor called SUNBURST, and another malware called SUPERNOVA was separately placed on the server, enabling them to infiltrate numerous government agencies and organizations worldwide. SUNSPOT was identified as the highly sophisticated and novel code designed to inject the SUNBURST malicious code into the Orion Platform during the build process. TEARDROP and RAINDROP were reportedly malware loaders that could be deployed as secondary tools using the SUNBURST backdoor.
Impact on organizations:
Among the affected were the US Treasury and the Department of Commerce. The attack highlighted the vulnerabilities in supply chain security and the need for a robust defense. As a part of their response to the SUNBURST vulnerability, SolarWinds revoked the code-signing certificate used to sign the affected software versions and obtained new digital code-signing certificates. They have rebuilt the affected versions, re-signed their code, and re-released all of the products previously signed with the certificate to be revoked.
Key lessons learned:
Adopting a comprehensive suite of security measures, such as Endpoint Detection and Response (EDR) and Extended Detection and Response (XDR) systems, is crucial. These systems provide real-time monitoring and automated responses to potential threats, reinforcing the ability to detect and prevent incoming attacks. Moreover, utilizing network anomaly detection technologies is vital to identify unusual behavior that could lead to a security breach. Additionally, using network anomaly detection technologies is crucial, as it allows for identifying unusual behavior that may indicate a breach. Furthermore, implementing a zero-trust architecture, which operates under the “Never trust, always verify” motto, can significantly reduce the attack surface and restrict lateral movement within networks.
In addition to all these preventative measures, it is strongly recommended that third-party platforms be installed behind firewalls, with their internet access restricted and ports and connections limited to operational necessities only. This further minimizes the potential entry points for attackers, mitigating the supply chain risk.
The SolarWinds breach demonstrates the criticality of promptly comprehending and responding to potential security anomalies, as it was detected but not fully comprehended for six months before its official discovery. Effectively identifying and addressing threats requires proactive action and not only detection. This event also emphasizes the importance of collaborating with external security firms to provide comprehensive threat analysis and resolution.
2- 3CX Attack
Overview of the attack:
The SmoothOperator supply chain attack hit the 3CX VOIP desktop client, compromised by a North Korean hacker group UNC4736 also allegedly affiliated with the APT group Lazarus. This incident marked the first-ever double supply chain attack involving compromised software chains of both 3CX and X_TRADER, a discontinued trading platform. This complex attack, involving malware strains TAXHAUL, Coldcat, and a backdoor named VEILEDSIGNAL, affected Windows and macOS systems.
Impact on organizations:
Prominent clients, such as American Express, AirFrance, BMW, and Coca-Cola, were impacted. Over 242,519 IP addresses were potentially compromised, threatening the privacy and security of these organizations through the theft of user credentials and sensitive data.
Key lessons learned:
It is possible that “double supply chain attacks” will emerge in the future, highlighting the potential risks they pose and emphasizing the need for robust cybersecurity measures across a software’s lifecycle.
When this incident was asked about on the 3CX forums, the Support Team replied that it was a false positive; once again, it emphasized the importance of taking into account the anomalies in this case, as in the SolarWinds case.
3- GoAnywhere MFT
Overview of the attack:
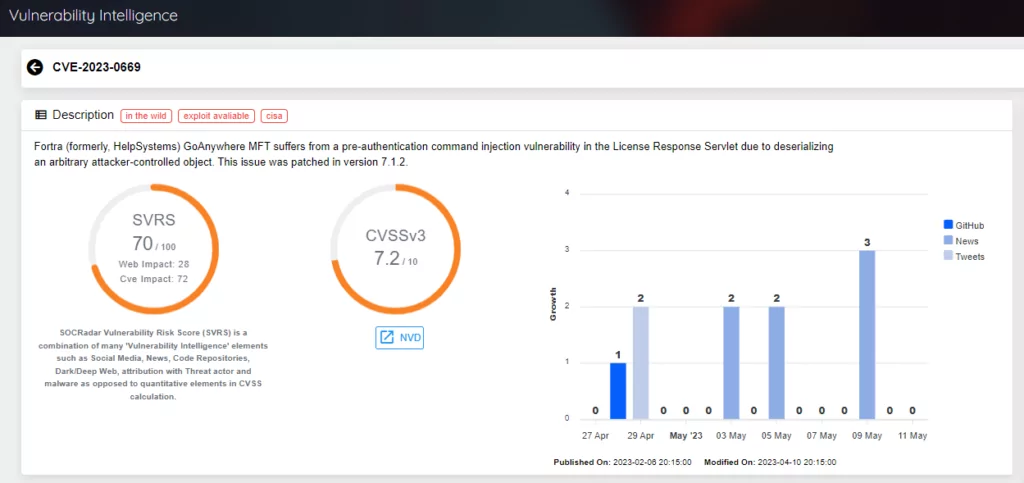
Clop and LockBit ransomware groups exploited a high-severity vulnerability (CVE-2023-0669) in GoAnywhere MFT product, Fortra’s secure managed file transfer solution, leading to a 91% increase in ransomware attacks in March 2023.
Impact on organizations:
The compromised GoAnywhere MFT software contributed to a 91% increase in ransomware attacks, affecting various industries such as healthcare, finance, and manufacturing. Among these industries, the healthcare sector was heavily targeted; for example, Brightline, a mental health provider, suffered a data breach impacting over 780K patients.
Key lessons learned:
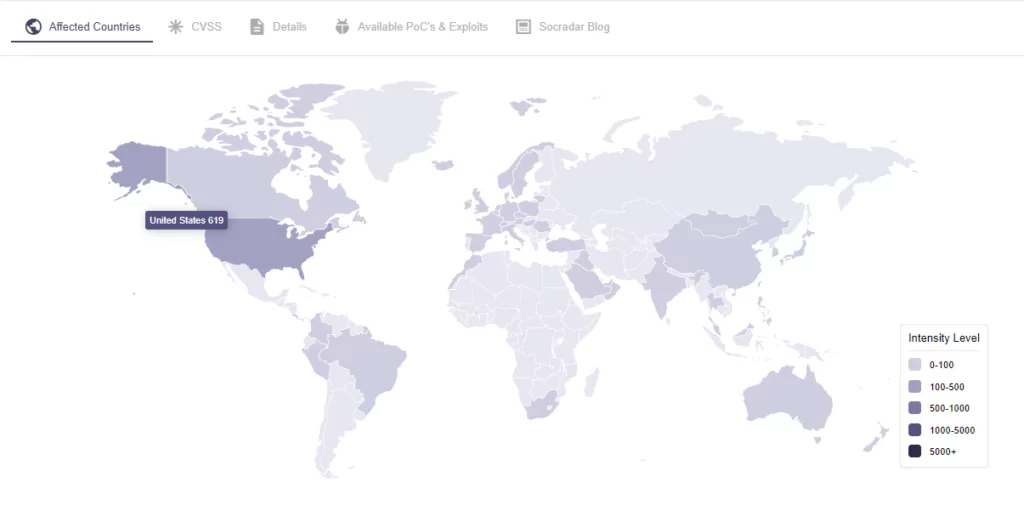
Organizations should prioritize patch management, conduct regular security audits, and maintain up-to-date backups to minimize the risks associated with supply chain attacks. According to SOCRadar’s observations, there are more than 1,000 systems worldwide whose administrative ports that may be vulnerable to this vulnerability are still open to the public internet. At this point, using a vulnerability intelligence service will enable organizations to recognize which vulnerability poses/may pose a risk and take precautions.
Through SOCRadar’s Vulnerability Intelligence panel, organizations can access the pages of CVEs and observe the CVE’s SVRS (SOCRadar Vulnerability Risk Score), a combination of many ‘Vulnerability Intelligence’ elements such as social media, news, code repositories, dark/deep web, attribution with threat actor and malware as opposed to quantitative elements in CVSS calculation, and CVSSv3 score, as well as whether the vulnerability is current and mentioned.
4- Okta Breach
Overview of the attack:
Ransomware group Lapsus$ claimed to have breached Okta, an identity management platform, by accessing an administrative account on March 21, 2022. The initial intrusion was detected to have occurred between January 16th-21st, 2022, through a third-party customer support engineer’s account.
Impact on organizations:
This breach represents a significant threat to Okta’s customers and the broader supply chain, and according to Bitsight’s report, there are potentially up to 2.5% of Okta’s customers are affected. Given Okta’s role in enterprise identity management, this incident has raised concerns about the potential cybersecurity implications for their customers and exposure throughout their third parties landscape.
Key lessons learned:
The incident highlights the critical importance of securing third-party supply chains and the potential risk even when internal systems are not directly breached. It is crucial for organizations to actively investigate their potential exposure in such incidents, monitor for unusual activities, and identify potential vulnerabilities within their own supply chain.
5- GitHub Supply Chain Attack
Overview of the attack:
In April 2022, a software supply chain attack was carried out against GitHub. The attackers used stolen user tokens from Heroku and TravisCI to gain access to private repositories. This was made possible due to an unknown vulnerability in OAuth tokens which GitHub had adopted recently.
Impact on organizations:
The attack affected several organizations, including GitHub and npm. It could have potentially put at risk over 2,200 companies that use Heroku and 1,700 that use TravisCI in their tech setups. The private repositories of these organizations were accessed, thereby exposing their sensitive information.
Key lessons learned:
This attack highlights the importance of having strong security measures in place to manage software supply chains, especially those involving third-party integrations. Organizations, therefore, need to regularly review their OAuth applications, restrict third-party access, and regularly review organization audit logs, user account security logs, and authorized OAuth applications.
6-Compromise of Comm100 Live Chat Application
Overview of the Attack:
In September 2022, the Comm100 Live Chat application fell victim to a supply chain attack. The attack employed a trojanized installer to distribute a JavaScript backdoor. The malware was spread using a Comm100 installer available on the company’s website, signed with a valid certificate.
Impact on Organizations:
The full impact of the attack was unclear. Comm100, a company with more than 15,000 customers in 51 countries at the time of the attack, provides chat and customer engagement applications to businesses, making the potential reach of the attack extensive. North American and European companies operating in various industries, including technology and healthcare, reportedly found the malicious file.
Key Lessons Learned:
The attack highlights the essential role of robust supply chain security measures, given the trojanized installer’s use. It underscores the importance of promptly identifying and rectifying security threats, as one provider only marked the installer as malicious. Lastly, it is noteworthy that this attack, like the Solarwinds compromise, was potentially carried out by an APT group (APT-Q-27, aka Dragon Breath).
7- Exploitation of Kaseya’s VSA
Overview of Attack:
In July 2021, a US technology company, Kaseya Limited, fell victim to a ransomware attack orchestrated by the Russian-speaking criminal group REvil. The attackers exploited vulnerabilities in Kaseya’s Virtual System Administrator (VSA) remote management software, specifically within its latest update. This allowed the hackers to replace the software with ransomware, affecting numerous managed service providers that used Kaseya’s products.
Impacted Organizations:
The attack had a significant ripple effect, impacting around 50 managed services providers directly and approximately 1,500 organizations indirectly. These organizations were customers of the affected service providers, demonstrating the extensive reach of the attack. The victims were from various industries, including many small and medium-sized businesses that rely on managed service providers for their IT needs.
Key Lessons Learned:
It highlights the potential for a single vulnerability to have far-reaching effects due to the interconnected nature of digital services. The incident serves as a reminder that companies must regularly update and patch their software to address potential security flaws. Furthermore, it emphasizes the need for businesses to understand their supply chain thoroughly, including the security protocols of their suppliers, as vulnerabilities can quickly propagate downstream.
8- Exploitation of ASUS’s Live Update Utility
Overview of the attack:
In 2018, a sophisticated supply chain attack targeted ASUS, a prominent computer hardware manufacturer. The attackers exploited the ASUS Live Update Utility, a tool pre-installed on most ASUS computers for automatic BIOS, UEFI, drivers, and application updates. The attackers injected a backdoor into the utility, using stolen digital certificates used by ASUS to sign legitimate binaries. This allowed them to distribute trojanized versions of the utility from official ASUS update servers, affecting as many as 500,000 to possibly over a million systems worldwide.
Impacted organizations:
The primary victim of this attack was ASUS and its vast user base. The attackers were able to compromise the ASUS Live Update Utility, which is pre-installed on most new ASUS computers. This means that potentially every user of the affected software could have become a victim. However, the attackers were particularly interested in several hundreds of specific users, of which they had prior knowledge. Also, similar methods and techniques were found in software from three other vendors in Asia, suggesting they might have been compromised as well.
Key lessons learned:
The ASUS supply chain attack underscores the increasing sophistication and danger of supply chain attacks. These attacks exploit the trust between vendors and customers, making them particularly effective and difficult to detect. It highlights the need for robust security measures at every stage of the supply chain, especially the software update process. Furthermore, it emphasizes the importance of monitoring all applications for suspicious activity, even those from trusted sources. Also, the attack stands as a reminder that even large, reputable organizations can fall victim to such attacks, underlining the need for continuous awareness and proactive solutions.
9- CCleaner Supply Chain Attack
Overview of the attack:
In 2017, a popular system optimization tool, the CCleaner software, was compromised by a sophisticated cyber-espionage group, Axiom or APT17, likely based in China. The attackers infiltrated the software supply chain, embedding a malicious payload within the CCleaner software that was then downloaded by unsuspicious users. The attack was highly targeted and had multiple stages, with the initial stage affecting 2.27 million users and a more focused second stage impacting only a select group of tech companies.
Impacted organizations:
The attack specifically targeted large technology and telecommunications companies, with a particular interest in a subset of PC users working for these firms. Companies in Japan, Taiwan, the UK, Germany, and the US were targeted. Specific companies that were victims of the second stage of the attack included tech giants like Akamai, D-Link, Google, HTC, Linksys, Microsoft, Samsung, Sony, VMware, and Cisco.
Key lessons learned:
It highlights the need for robust security measures at all software development and distribution stages. The attack also demonstrates the potential for state-level or industrial espionage in the cyber realm. Organizations should consider not only their own security practices but also those of their software suppliers. Regularly updating software to the latest versions and using quality antivirus products are recommended practices. For corporate users, restoring from backups is advised to ensure the complete removal of any potential malware.
10- NotPetya
Overview of the attack:
The NotPetya cyberattack, primarily targeting Ukraine in 2017, was a devastating supply chain attack that used a malware wiper disguised as ransomware. The attackers infiltrated the accounting software firm MeDoc and injected malicious code into their software, which was widely used by Ukrainian businesses. Unlike typical ransomware, NotPetya was designed to irreversibly encrypt data on infected systems, making recovery impossible.
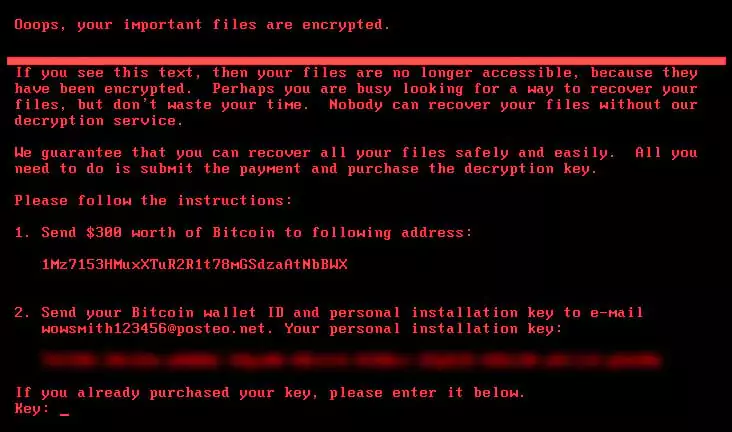
Impacted organizations:
The NotPetya attack had a global impact, affecting numerous organizations beyond its primary target in Ukraine. Multinational corporations such as Maersk, an international shipping giant, were severely impacted, with operations grinding to a halt due to the attack.
Key lessons learned:
The NotPetya attack underscored the vulnerability of supply chains to cyberattacks and the potential for widespread damage. It highlighted the need for organizations to integrate security at every stage of the development process, as well as the importance of validating the origin of code before including it in production releases. The attack also demonstrated the catastrophic consequences of failing to secure internal networks.
There Are Always Possibilities
Except for the supply chain attacks listed above, some situations might seem like they had the potential for supply chain attacks but didn’t actually lead to one. Some of them are listed below:
- MSI Ransomware Attack and Code Signing Keys Leak: In 2023, a ransomware attack on the PC manufacturer MSI led to the theft and public leak of private code signing keys, including those for Intel Boot Guard. This breach could potentially have enabled attackers to deploy malicious firmware updates, affecting an entire ecosystem of devices.
- Log4Shell Vulnerability on Apache Log4j: The discovery of a zero-day vulnerability in the Apache Log4j library, widely used in Java applications, led to the potential for remote code execution on victim systems. Despite its widespread impact, the exploit did not result in a direct supply chain attack, although it highlighted the potential for such attacks in similar situations.
- NVIDIA Ransomware Attack and Data Leak: The tech company NVIDIA suffered a cyberattack in 2022, which resulted in operational disruption and the threat of a large-scale data leak. The attackers demanded changes to NVIDIA’s product firmware and threatened to release confidential files. While this did not result in a supply chain attack, it exposed potential vulnerabilities in the supply chain.
Conclusion
Supply chain attacks have become an increasingly prominent threat to organizations worldwide. The top 10 attacks that have been discussed, the SolarWinds, 3CX, GoAnywhere MFT, Okta, GitHub, Comm100, Kaseya’s VSA, ASUS, CCleaner, and NotPetya demonstrate the diverse tactics employed by threat actors and the devastating impact these attacks can have on businesses and consumers.
Key lessons learned from these incidents emphasize the importance of implementing strict access controls, securing third-party relationships, and investing in advanced threat detection and response capabilities. Notably, the integration of vulnerability intelligence becomes a necessity in this landscape. This means identifying, assessing, and mitigating potential weaknesses in our systems or applications. Further, promoting collaboration between security and development teams is vital, as is the inclusion of vulnerability intelligence in the continuous integration and deployment (CI/CD) process. Organizations should prioritize patch management within their CI/CD process, backed by effective vulnerability intelligence, and always monitor their systems for anything unusual. Employees should also be educated about the dangers tied to attacks that come through the supply chain, including those potentially exploiting known vulnerabilities.
In addition, implementing a “shift-left” approach, where security checks are integrated early in the development process, ensures fewer vulnerabilities and faster mitigation times, reinforcing the overall infrastructure.
Organizations can adopt a proactive approach to cybersecurity with Cyber Threat Intelligence (CTI). This forward-thinking strategy helps businesses identify and counteract emerging cyber threats like supply chain attacks. Leveraging the power of CTI, companies can anticipate potential cyber-attacks, prioritize security patching, and cultivate a culture centered around cybersecurity. In today’s rapidly changing digital environment, investing in CTI is crucial to protect crucial assets, safeguard valuable data, and uphold the organization’s reputation. With the rise in cyber threats, the importance of CTI in our interconnected digital world cannot be overstated.
How Can SOCRadar Extended Threat Intelligence (XTI) Help Organizations Defend Against Supply Chain Compromises?
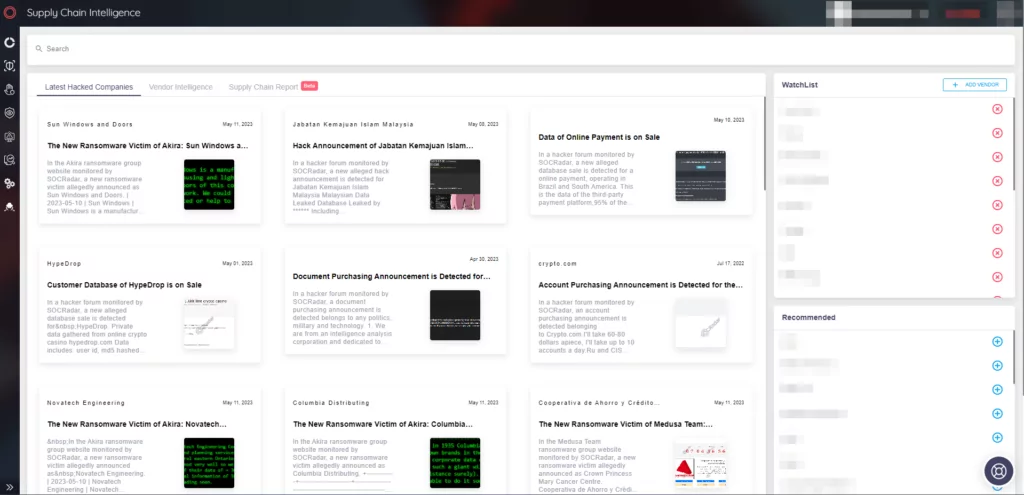
Organizations can obtain various insights from the Supply Chain Intelligence panel inside the CTI of SOCRadar’s platform. These pieces of information are explained below respectively:
When logged into the module, the first tab (Latest Hacked Companies) shows the news of companies that have suffered cyber attacks:
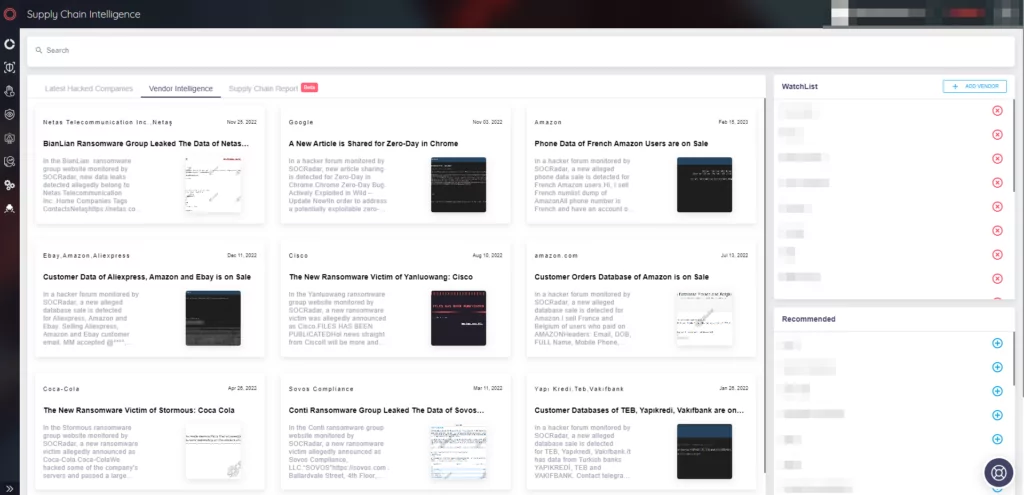
In the Vendor Intelligence tab, apart from the hacked companies, there is up-to-date news about the vendors that have suffered supply chain attacks.
In the Supply Chain Report tab, which is currently in the beta phase, it is possible to review reports with detailed information about companies and their status on the web in terms of security.
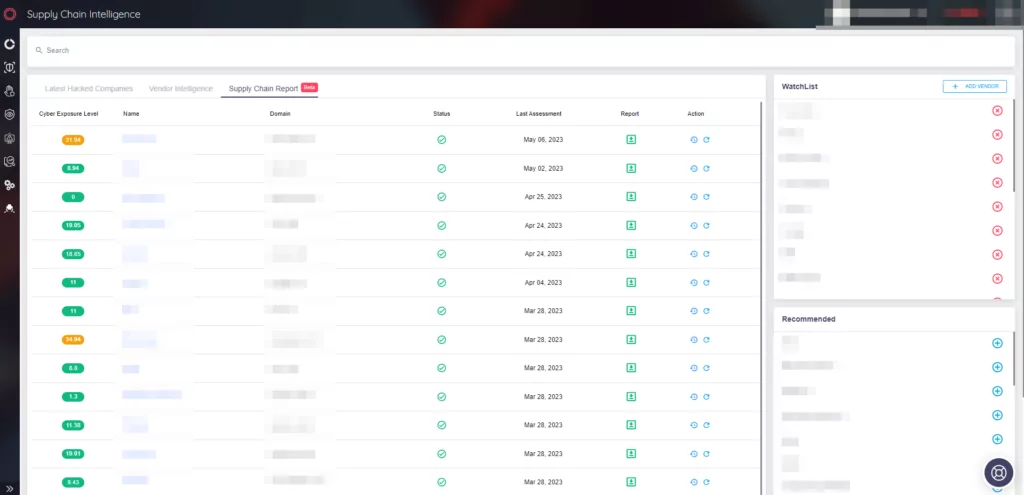
Here is an example report generated by Supply Chain Report:
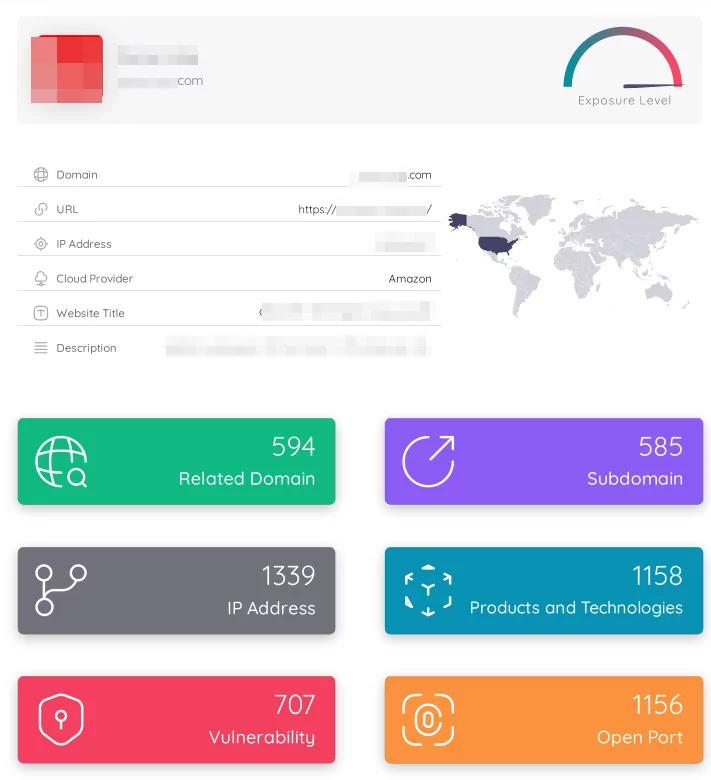
In addition to the Supply Chain Intelligence module, the Vulnerability Intelligence module will also help organizations with information about various threats:
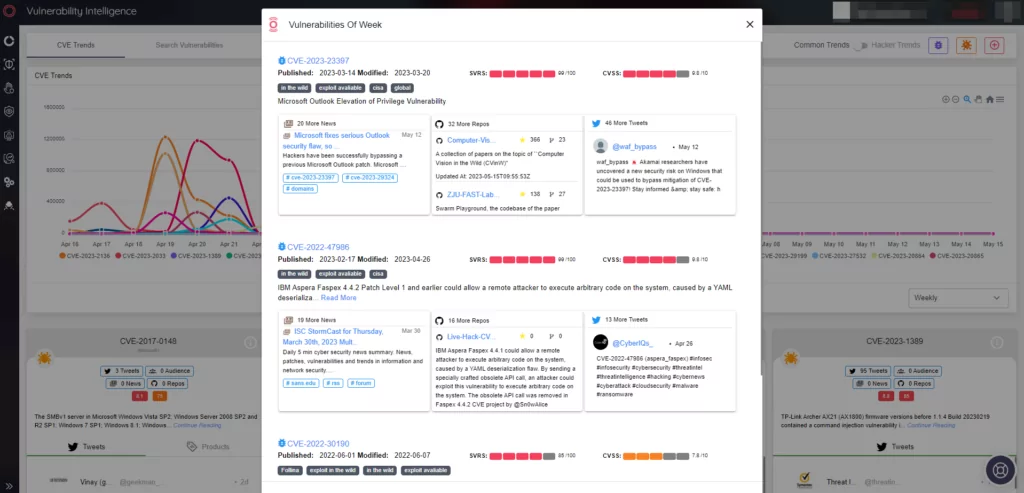
Screenshot of the Vulnerability Intelligence panel, when the panel is opened for the first time, the Vulnerabilities that have been on the agenda that week appear as a pop-up in front of the user.




































