Apache Superset Default Configuration Vulnerability Could Lead to RCE
[Update] January 9, 2024: “CISA Added Apache Superset Vulnerability (CVE-2023-27524) to the Known Exploited Vulnerabilities (KEV) Catalog”
Developers of Apache Superset, an open-source data visualization software, have released patches to fix a vulnerability in the default configuration settings. The vulnerability, identified as CVE-2023-27524, has a high severity CVSS score of 8.9.
An unauthenticated attacker who successfully exploits the insecure default configuration vulnerability could perform remote code execution, gather credentials, and compromise data.
Which Apache Superset Instances Are Affected?
CVE-2023-27524 affects all versions of Apache Superset up to and including 2.0.1. The issue arises from the use of a default SECRET_KEY, which allows attackers to authenticate and access unauthorized resources on installations that are exposed to the internet. However, Superset instances that have changed the default SECRET_KEY value to a more secure random string are not affected by CVE-2023-27524.
Exploitation of CVE-2023-27524
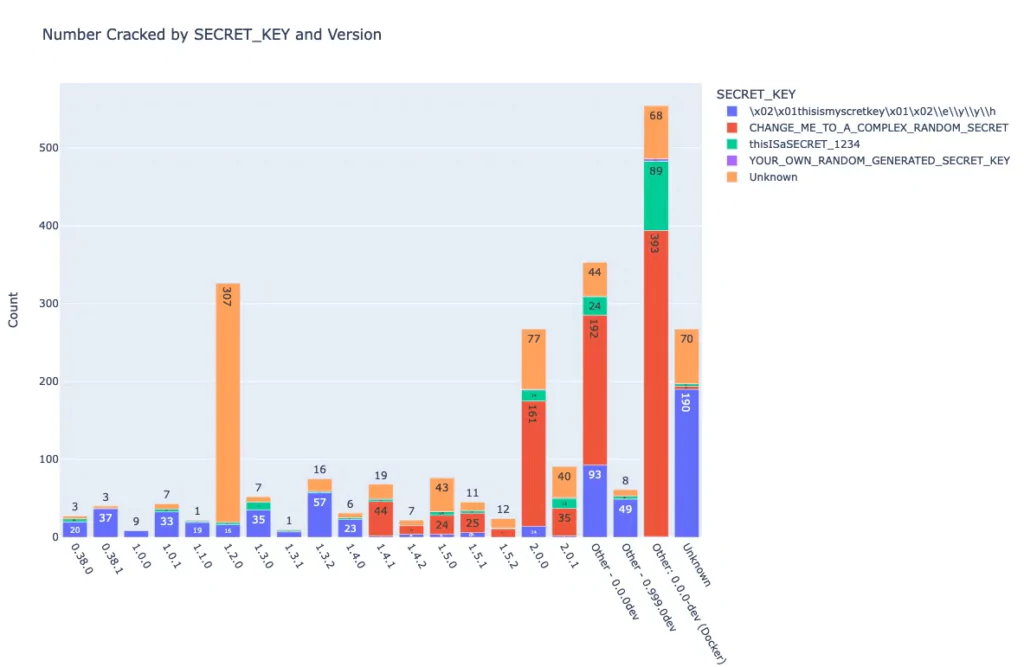
Researchers from Horizon3.ai found that during installation, the SECRET_KEY is set to “x02x01thisismyscretkeyx01x02eyyh,” and 918 of 1,288 publicly accessible servers were running the default configuration in October 2021. An attacker who knows the secret key could then sign in as an administrator to these servers by forging a session cookie due to CVE-2023-27524 and ultimately take control of the systems.
On January 11, 2022, Apache Superset project maintainers tried to resolve the issue by changing the SECRET_KEY value in Python code to “CHANGE_ME_TO_A_COMPLEX_RANDOM_SECRET,” and they also gave users instructions on how to override it.
Researchers later discovered two more SECRET_KEY configurations with default values of “USE_YOUR_OWN_SECURE_RANDOM_KEY” and “thisISaSECRET_1234.“
Over 2,000 Apache Superset Instances Use a Default Key
In February 2023, a wider search was conducted with all four keys, and it revealed 3,176 instances where 2,124 were using one of the default keys. This impacted various organizations, including large corporations, small businesses, government agencies, and universities.
The Apache security team was notified again, and a new update (version 2.1) was released on April 5, 2023, which addressed the security flaw by preventing the server from starting up if configured with the default SECRET_KEY.
According to Naveen Sunkavally, the chief architect at Horizon3.ai, the fix for the security issue in Superset is not completely reliable since it is still possible to install Superset with a default SECRET_KEY if it is installed through a docker-compose file or a helm template. This is because the docker-compose file has a new default SECRET_KEY of TEST_NON_DEV_SECRET, which some users may unknowingly use to run Superset.
Additionally, some configurations may set admin/admin as the default credential for the admin user.
Horizon3.ai has provided a Python script that can be used to check if Superset instances are vulnerable to CVE-2023-27524.
Sunkavally suggests that applications should be designed to guide users toward secure choices rather than relying on users to read the documentation.
The best way to address this issue is to remove the option for users to choose to be insecure and require them to take deliberate actions to be purposefully insecure.
Stay Secure with SOCRadar
SOCRadar offers two functional modules for managing vulnerabilities and threats. The Vulnerability Intelligence module enables you to search for and access detailed information about vulnerabilities, which can aid in managing vulnerability issues and prioritizing patches.
Meanwhile, the Attack Surface Management (ASM) module is designed to identify your digital assets and alert you to emerging issues, ensuring you stay on top of potential threats.