
Appleton Harley-Davidson Leak, GTA V Source Code, and ORBCOMM Database on Dark Web
SOCRadar’s Dark Web Team has reported a wave of significant cyber threats in the past week, including an alleged leak of Appleton Harley-Davidson’s customer database, exposing nearly 20,000 records. Additionally, the source code for Grand Theft Auto V is purportedly up for sale. Other discoveries include a data breach involving the United Nations Capital Development Fund, the sale of a new Android RAT tool called Cellik RAT with advanced crypto-targeting capabilities, and the alleged compromise of ORBCOMM’s database, totaling over 70 terabytes.
Receive a Free Dark Web Report for Your Organization:
Alleged Customer Database of Appleton Harley-Davidson is Leaked
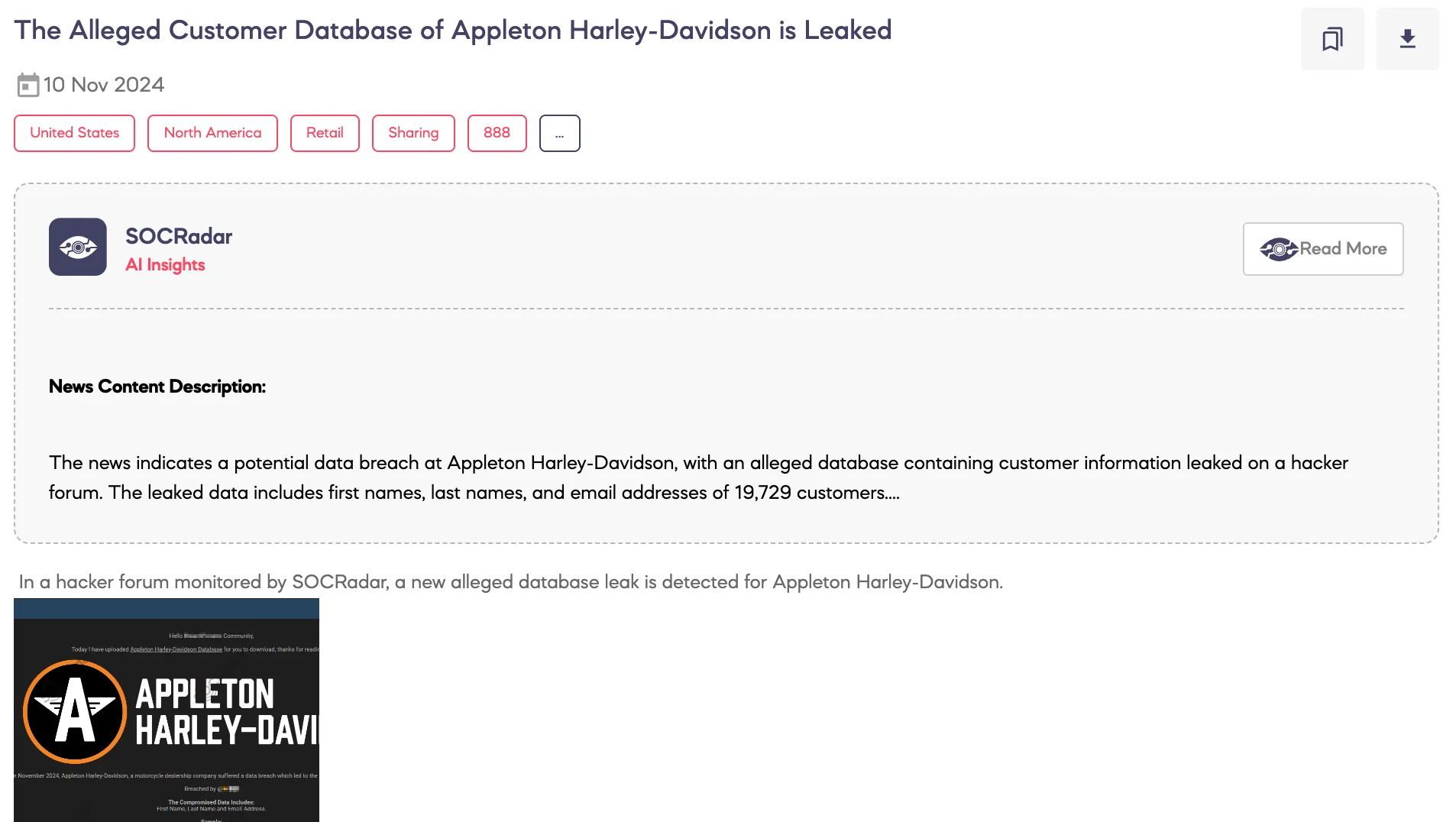
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to have leaked the customer database of Appleton Harley-Davidson, a motorcycle dealership. According to the post, a data breach in November 2024 exposed 19,729 customers’ data, including first names, last names, and email addresses. The threat actor has shared a sample of the compromised data, allowing potential buyers to verify its authenticity. This incident underscores the ongoing risks of personal data exposure on dark web markets.
Alleged Source Codes of Grand Theft Auto V are on Sale
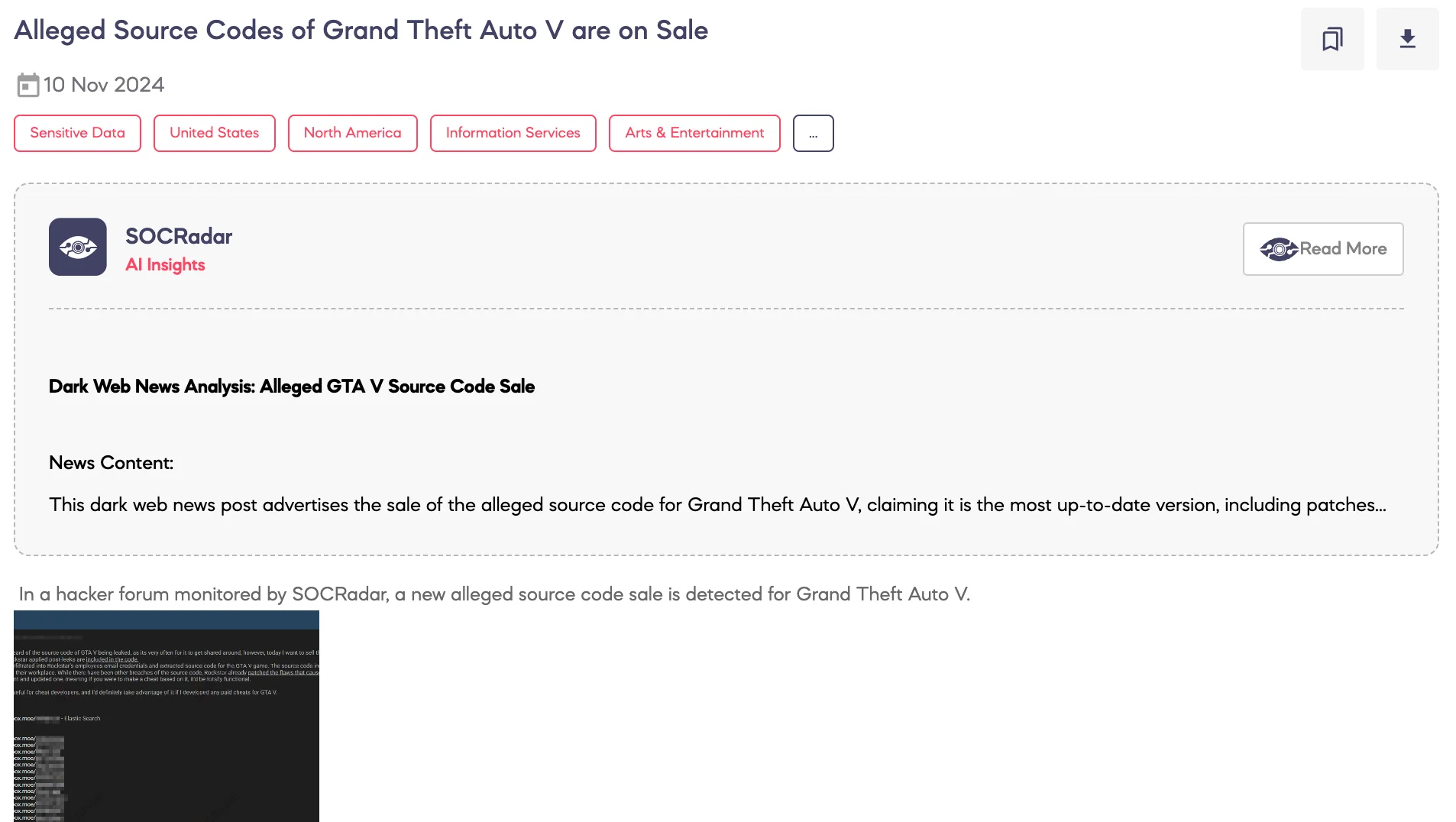
SOCRadar Dark Web Team has identified a post on a dark web hacker forum where a threat actor is offering the alleged source code for Grand Theft Auto V (GTA V) for sale. The actor claims this is the most recent and fully updated version, containing patches applied by Rockstar Games, including the anti-cheat system and internal tools used by the company.
According to the post, previous versions of leaked source codes have been patched, rendering older cheats ineffective. However, this new leak is highlighted as being highly valuable for cheat developers, as it would enable the creation of functional and undetected cheats for GTA V. This incident demonstrates the ongoing vulnerabilities in the gaming industry, where source code leaks can be exploited for profit on dark web markets, impacting game integrity and security.
Alleged Database of United Nations Capital Development Fund is Leaked
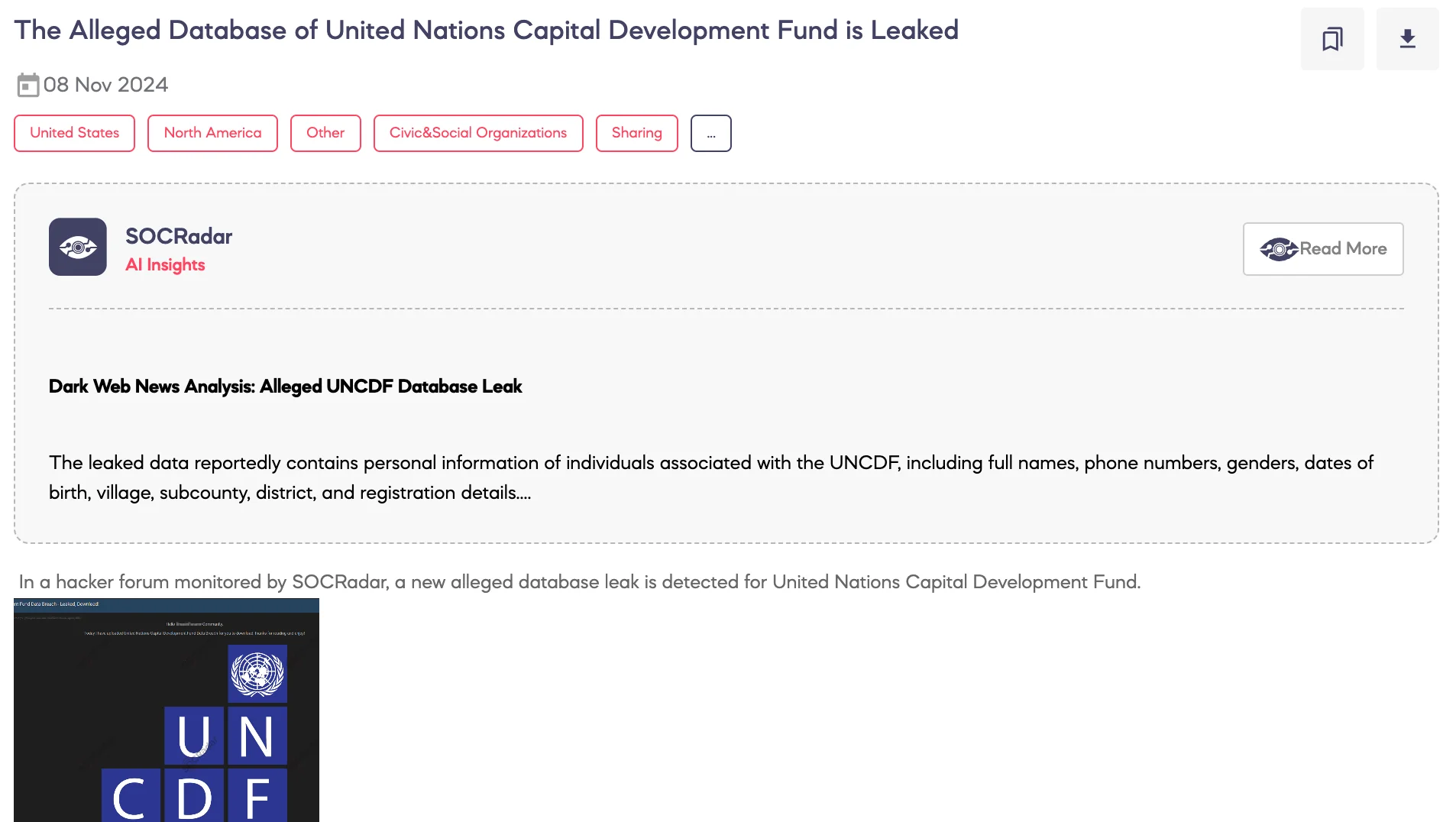
SOCRadar Dark Web Team detected a post on a dark web hacker forum where a threat actor claims to have leaked a database allegedly belonging to the United Nations Capital Development Fund (UNCDF). The actor states that in November 2024, UNCDF experienced a data breach, resulting in the exposure of approximately 328,000 records. The leaked data allegedly includes sensitive information such as full names, phone numbers, gender, dates of birth, business names, employee and branch details, and various location-specific details for service providers in Uganda.
A New RAT Tool is on Sale
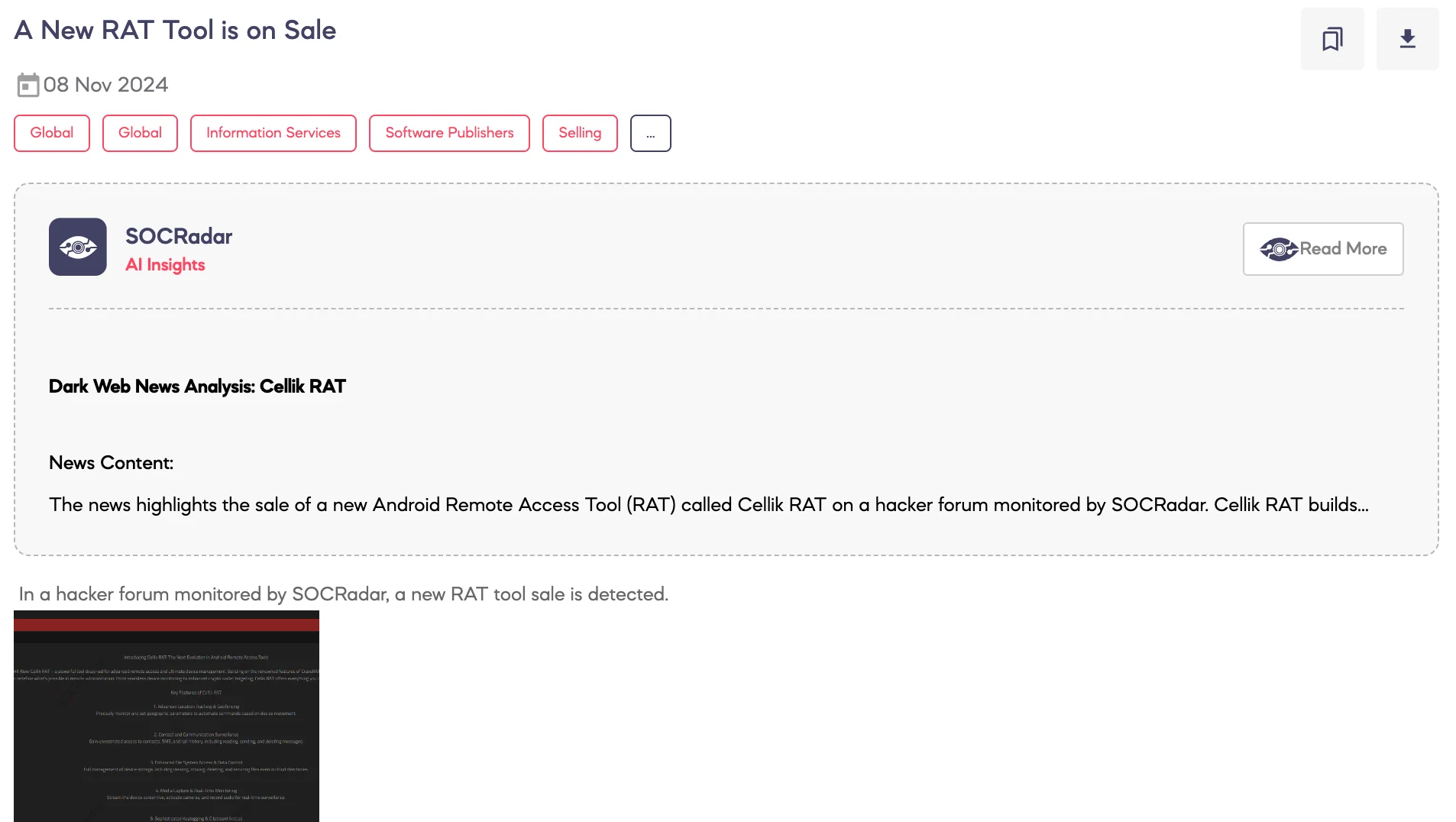
SOCRadar Dark Web Team has detected a post on a hacker forum where a threat actor is advertising a new Android Remote Access Tool (RAT) called Cellik RAT.” According to the threat actor, Cellik RAT represents a major evolution in remote access tools, offering capabilities such as advanced location tracking, real-time media capture, communication surveillance, and the ability to bypass Google Play Protect with persistent anti-detection measures. They claim the tool is optimized for stealthy control over Android devices, particularly highlighting features designed to target and extract data from popular crypto wallets, including transaction interception and private key exfiltration.
The threat actor states that Cellik RAT provides comprehensive device control, allowing file management, device configuration adjustments, and even AI-driven behavioral analysis for automated task execution. They offer the tool at $100 for a one-month license or $900 for lifetime access, positioning it as an all-in-one solution for those seeking high-level remote administration capabilities on dark web markets.
Alleged Database of ORBCOMM is on Sale
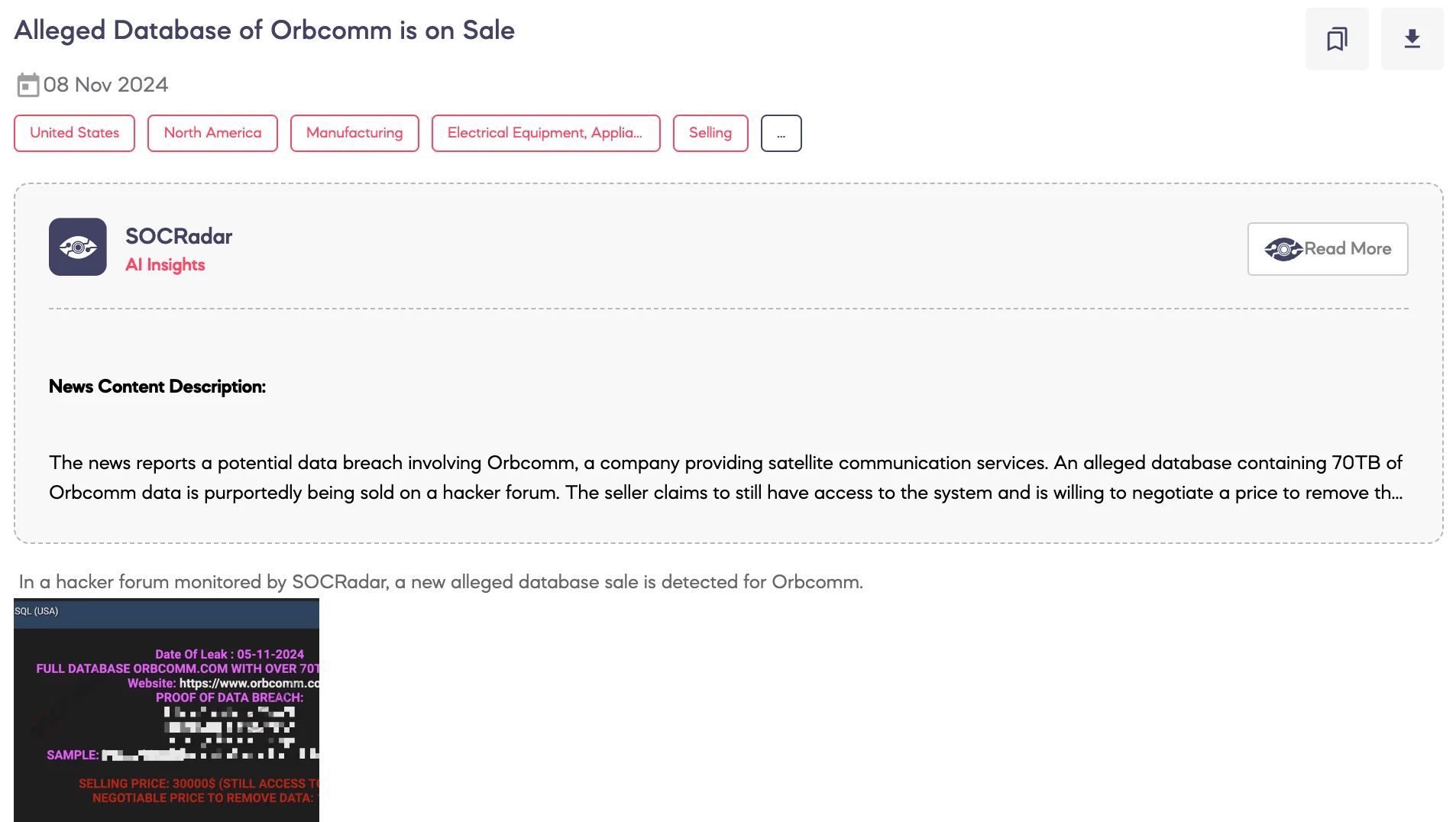
On November 8, 2024, SOCRadar Dark Web Team identified a post on a dark web hacker forum. A threat actor claims to have the complete database of ORBCOMM, a U.S.-based company in the industrial Internet of Things (IoT) and Machine-to-Machine (M2M) communications sector. The alleged leak, reportedly over 70 terabytes in SQL format, includes structured data. The threat actor also claims to have ongoing access to ORBCOMM’s system as of November 5, 2024. They are offering the data for $30,000, with a negotiable $100,000 price to delete it entirely.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































