April 2025 Patch Tuesday: Microsoft Addresses 126 Vulnerabilities Including Actively Exploited CLFS Zero-Day
Microsoft’s April 2025 Patch Tuesday brings an extensive set of updates aimed at shoring up system defenses across its product ecosystem. With 126 vulnerabilities addressed, 11 classified as critical and one already exploited in the wild, this month’s update demands prompt attention from security teams.
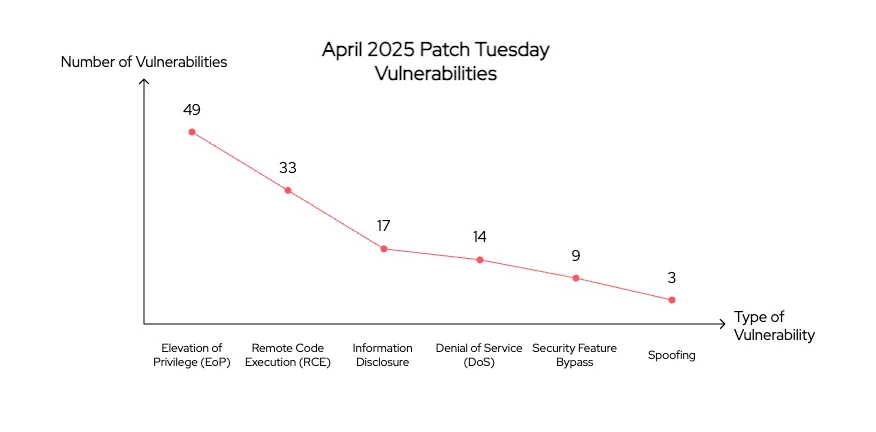
Here’s an overview of the April 2025 Patch Tuesday vulnerabilities:
- 49 Elevation of Privilege (EoP) Vulnerabilities
- 33 Remote Code Execution (RCE) Vulnerabilities
- 17 Information Disclosure Vulnerability
- 14 Denial of Service (DoS) Vulnerability
- 9 Security Feature Bypass Vulnerabilities
- 3 Spoofing Vulnerabilities
The high count of Elevation of Privilege and Remote Code Execution flaws highlights the risk of attackers gaining unauthorized access or executing malicious code. More concerning is the confirmation that a zero-day is being actively exploited, placing unpatched systems directly in the crosshairs.
With such a broad attack surface at stake, security teams should prioritize patching based on exploitability and criticality. Swift action today could mean avoiding major compromises tomorrow. Let’s draw attention to the vulnerabilities that are in the news this month.
A Closer Look at the Actively Exploited Zero-Day: CVE-2025-29824
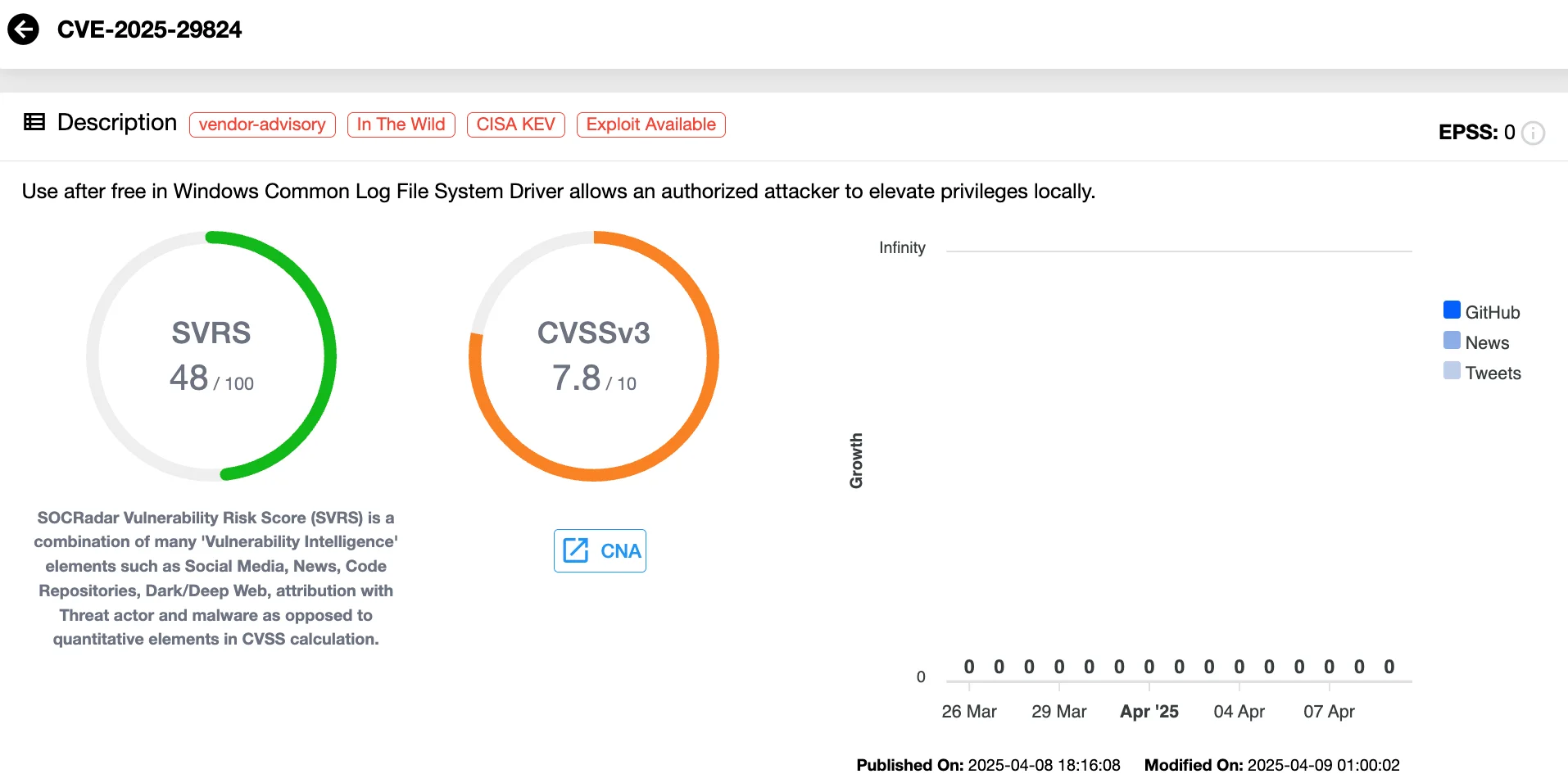
Among the April 2025 Patch Tuesday disclosures, one vulnerability stands out due to its active exploitation in the wild: CVE-2025-29824 (CVSS 7.8), a flaw in the Windows Common Log File System (CLFS) driver. This elevation of privilege vulnerability allows local attackers to gain SYSTEM-level privileges, making it an ideal entry point for ransomware campaigns.
Microsoft confirmed in a report that the Storm-2460 threat actor group, also linked to the PipeMagic backdoor and RansomEXX ransomware, has been exploiting this flaw in targeted attacks. Industries hit include IT and real estate firms in the U.S., financial institutions in Venezuela, a Spanish software vendor, and retail operations in Saudi Arabia.
The exploit was used to inject malicious payloads via the winlogon.exe process, followed by credential theft using Sysinternals’ procdump.exe tool to access the LSASS memory. Once in control, the attackers encrypted files, appending random extensions and dropping ransom notes titled !READ_ME_REXX2!.txt.
Security patches for CVE-2025-29824 were made available on April 8, 2025, for Windows Server and Windows 11. However, updates for Windows 10 systems remain pending, with Microsoft assuring a forthcoming release.
Importantly, Microsoft noted that Windows 11 version 24H2 is not affected by the observed exploitation, even though the vulnerability exists in that version. The Cybersecurity and Infrastructure Security Agency (CISA) has added the flaw to its Known Exploited Vulnerabilities Catalog, setting a remediation deadline of April 29, 2025, for affected federal systems.
Given the direct link to ransomware deployment, Microsoft urges all organizations to prioritize patching elevation of privilege flaws like CVE-2025-29824 as part of a proactive defense against sophisticated attacks.
To stay ahead of threats like CVE-2025-29824, your security team can benefit from using SOCRadar’s Cyber Threat Intelligence module. With real-time insights and continuous monitoring, the platform’s Vulnerability Intelligence capabilities help your organization identify, track, and prioritize high-risk vulnerabilities, enabling you to patch faster and reduce exposure before attackers can exploit it.
Which Critical Vulnerabilities Were Addressed in April 2025 Patch Tuesday?
The April 2025 Patch Tuesday release resolves several critical vulnerabilities which could allow Remote Code Execution (RCE). These vulnerabilities affect core Windows services and productivity applications, representing high-value targets for attackers aiming to gain initial access or execute malicious code within enterprise environments.
Here’s the full list of April 2025 vulnerabilities that Microsoft has classified as critical based on their maximum severity ratings:
- CVE-2025-27482 (CVSS 8.1) – Windows Remote Desktop Services Remote Code Execution Vulnerability
- CVE-2025-27480 (CVSS 8.1) – Windows Remote Desktop Services Remote Code Execution Vulnerability
- CVE-2025-26663 (CVSS 8.1) – Windows LDAP Remote Code Execution Vulnerability
- CVE-2025-26670 (CVSS 8.1) – LDAP Client Remote Code Execution Vulnerability
- CVE-2025-27745 (CVSS 7.8) – Microsoft Office Remote Code Execution Vulnerability
- CVE-2025-29791 (CVSS 7.8) – Microsoft Excel Remote Code Execution Vulnerability
- CVE-2025-27748 (CVSS 7.8) – Microsoft Office Remote Code Execution Vulnerability
- CVE-2025-27749 (CVSS 7.8) – Microsoft Office Remote Code Execution Vulnerability
- CVE-2025-27752 (CVSS 7.8) – Microsoft Excel Remote Code Execution Vulnerability
- CVE-2025-26686 (CVSS 7.5) – Windows TCP/IP Remote Code Execution Vulnerability
- CVE-2025-27491 (CVSS 7.1) – Windows Hyper-V Remote Code Execution Vulnerability
Two of the most severe issues affect Windows Remote Desktop Services, tracked as CVE-2025-27482 and CVE-2025-27480 (both CVSS 8.1). Successful exploitation of these flaws could allow attackers to execute arbitrary code without user interaction, potentially enabling lateral movement within a network.
Similarly, CVE-2025-26663 and CVE-2025-26670 (both CVSS 8.1) expose vulnerabilities in the Windows Lightweight Directory Access Protocol (LDAP) and its client. LDAP is often used for authentication and directory lookups, making these RCE vulnerabilities especially risky for domains with misconfigured or exposed services.
Vulnerabilities with Serious Exploit Potential
While not currently under active exploitation, several vulnerabilities patched this month are considered high-risk due to their potential for abuse and the absence of available mitigations or workarounds. These flaws span multiple core Windows components and enterprise applications, increasing the likelihood they could be leveraged in future attacks, especially by threat actors scanning for newly disclosed weaknesses.
This group includes two Windows LDAP vulnerabilities (CVE-2025-26663 and CVE-2025-26670) already marked as critical by Microsoft, as well as serious flaws affecting Remote Desktop Gateway, Office, SharePoint, and the Windows Kernel.
Here’s the full list of high-risk vulnerabilities with notable severity and potential for exploitation:
- CVE-2025-26663 (CVSS 8.1) – Windows LDAP Remote Code Execution Vulnerability
- CVE-2025-26670 (CVSS 8.1) – LDAP Client Remote Code Execution Vulnerability
- CVE-2025-27480 (CVSS 8.1) – Remote Desktop Gateway Service Remote Code Execution Vulnerability
- CVE-2025-27482 (CVSS 8.1) – Remote Desktop Gateway Service Remote Code Execution Vulnerability
- CVE-2025-29794 (CVSS 8.8) – Microsoft SharePoint Server Remote Code Execution Vulnerability
- CVE-2025-27727 (CVSS 7.8) – Windows Installer Elevation of Privilege Vulnerability
- CVE-2025-29812 (CVSS 7.8) – Windows Kernel Memory Information Disclosure Vulnerability
- CVE-2025-29809 (CVSS 7.1) – Windows Kerberos Elevation of Privilege Vulnerability
- CVE-2025-29792 (CVSS 7.3) – Microsoft Office Remote Code Execution Vulnerability
- CVE-2025-29793 (CVSS 7.2) – Microsoft SharePoint Server Remote Code Execution Vulnerability
- CVE-2025-27472 (CVSS 5.4) – Windows Mark of the Web (MOTW) Security Feature Bypass Vulnerability
Security teams should proactively address these gaps as part of their patch management cycle, especially in environments where these components are exposed or play a role in access control, remote connectivity, or document processing.
Harden Your Security Posture Before It’s Too Late
Organizations are encouraged to take immediate steps to reduce risk: assess your attack surface, apply all relevant patches, and strengthen your defenses against potential exploitation.
SOCRadar’s Attack Surface Management (ASM) module provides the visibility and intelligence you need to track threats like those addressed in the April 2025 Patch Tuesday update. With quick insights, automated alerts, and continuous monitoring of your digital footprint, your security team can quickly detect, prioritize, and remediate vulnerabilities before attackers can exploit them.
For the full list of vulnerabilities patched this month and technical details, view Microsoft’s official April 2025 Patch Tuesday release note.