
What is Spoofing Attack and How to Prevent It?
In the context of cybersecurity, spoofing is the act of impersonating another entity to earn our trust, obtain access to our systems, steal data, steal money, or transmit malware.
How Does Spoofing Work?
Spoofing often consists of two components: the spoof itself, such as a phony email or website, and the social engineering portion, which encourages victims to act. For instance, spoofers may send an email that looks to be from a senior colleague or boss, requesting that you transfer funds online and offering a compelling justification for the request. Spoofers often know how to coax a victim into doing the necessary action, in this case, approving a fake wire transfer, without arousing suspicion.
A successful spoofing attack may have severe repercussions, including the theft of personal or commercial information, the collection of credentials for use in future attacks, the propagation of malware, illegal network access, and the circumvention of access restrictions. These attacks may occasionally result in ransomware attacks or expensive data breaches for corporations.
There are several sorts of spoofing attacks, with the most straightforward using emails, websites, and phone calls. IP addresses, the Address Resolution Protocol (ARP), and Domain Name System (DNS) servers are used in the most sophisticated technological assaults. We examine the most prevalent instances of spoofing below.
Types of Spoofing
Email spoofing
Email spoofing is one of the most common types of cyberattacks. It happens when the sender forges email headers so that client software shows the false sender address, which most users accept at face value. Unless email receivers read the title thoroughly, they presume the bogus sender sent the message. If consumers recognize the brand, they are more inclined to trust it.
Fake emails often seek a money transfer or access to a system. In addition, they may include attachments that, when opened, install malware, such as Trojans or viruses. In many instances, malware is meant to infect the whole network in addition to your machine.
Email spoofing mainly depends on social engineering — the capacity to persuade human users that what they see is authentic, inciting them to take action by opening an attachment, transferring money, etc.
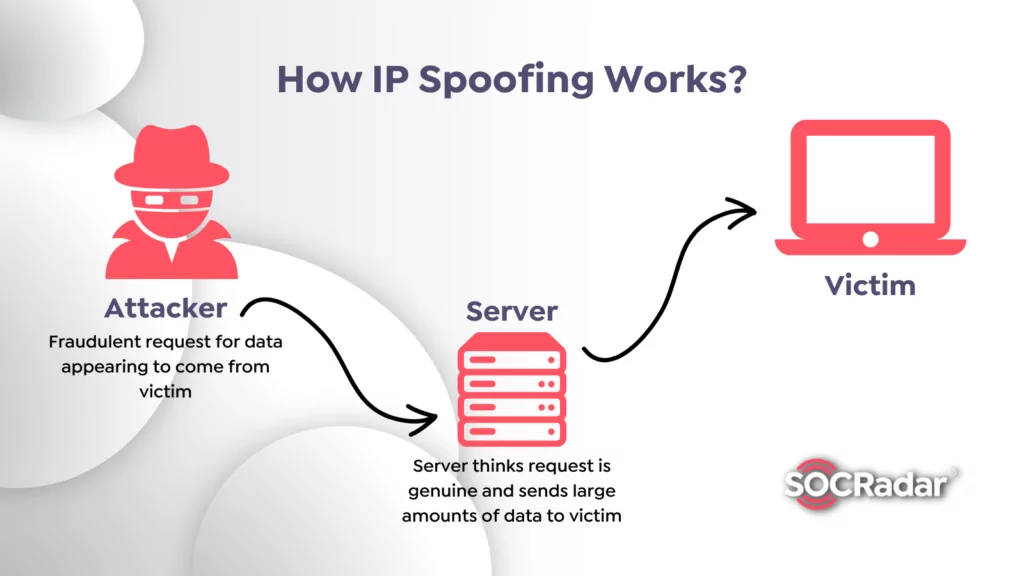
IP Spoofing
In contrast to email spoofing, IP spoofing is mainly directed toward a network.
IP spoofing includes an attacker attempting to obtain unauthorized access to a system by sending messages with a phony or spoofed IP address to make it seem as if the message originated from a trustworthy source, such as a computer on the same internal network.
Cybercriminals do this by stealing the IP address of a trustworthy host and modifying the packet headers transmitted from their system to make it look like they originated from the trusted machine. IP spoofing assaults are often part of DDoS (Distributed Denial of Service) attacks, which may take a whole network down. Therefore, it is crucial to detect them as soon as possible.
Website Spoofing
Website spoofing is impersonating a genuine website with a fraudulent one. The faked website will have a recognizable login page, stolen logos and comparable branding, and a URL that first looks to be correct.
Hackers create these websites to steal your login information and maybe infect your machine with malware. Frequently, website spoofing occurs in tandem with email spoofing; for instance, fraudsters may send you an email including a link to the bogus website.
Caller ID or Phone Spoofing
Caller ID spoofing, also known as phone spoofing, occurs when con artists misrepresent the information supplied to your caller ID to conceal their identity. They do this because they are aware that you are more likely to answer your phone if it seems to be a local number rather than an unfamiliar one.
VoIP (Voice over Internet Protocol) is used for caller ID spoofing, allowing fraudsters to establish a phone number and caller ID of their choosing. As soon as the target answers the phone, the fraudsters attempt to get vital information for fraudulent reasons.
Text Message Spoofing
Text message spoofing, also known as SMS spoofing, occurs when the text message’s sender provides false information. Sometimes, legitimate firms replace a lengthy number with a short, easy-to-remember alphanumeric identifier to make it simpler for consumers. Scammers, on the other hand, conceal their true identity behind an alphanumeric sender ID, often posing as a reputable business or institution. These counterfeit messages often include links to SMS phishing (also known as “smishing“) websites or malware downloads.
ARP Spoofing
ARP is a mechanism that allows network messages to reach a particular network device. ARP spoofing, also known as ARP poisoning, happens when an adversary transmits forged ARP packets over a local area network. This situation connects the MAC address of the attacker to the IP address of a genuine network device or service. This connection allows the attacker to intercept, alter, or even block any data destined for the IP address.
DNS Spoofing
DNS spoofing, also known as DNS cache poisoning, is an attack in which updated DNS records are used to redirect internet traffic to a sham website that closely mimics the actual destination. Spoofers do this by changing the IP addresses recorded on the DNS server with the IP addresses desired by the hackers.
GPS Spoofing
GPS spoofing happens when a GPS receiver is misled into transmitting false signals that seem to be authentic. This indicates that the fraudsters are faking their location while being in another. This may be used to hack a car’s GPS and send you to the incorrect area or, on a much larger scale, to interfere with the GPS signals of ships or airplanes. Numerous mobile applications depend on location data from smartphones, making them susceptible to this kind of spoofing attack.
Facial Spoofing
Facial recognition technology is utilized in law enforcement, airport security, healthcare, education, marketing, and advertising, as well as to unlock mobile devices and computers. Facial recognition spoofing is possible using unlawfully acquired biometric data from an individual’s online profile or compromised system.
How to Prevent?
- Activate your spam filter. This will prevent the vast majority of faked emails from reaching your inbox.
- Do not click on links or download files in unsolicited emails from unknown senders. If there is a possibility that the email is accurate, contact the sender through an alternative route and validate the email’s contents.
- Sign in from a different window or tab. Do not click the offered link if you get a suspicious email or text message demanding that you log in to your account and perform some action, such as verifying your details. Instead, create a new tab or window and browse the site. Alternatively, you may log in with the app on your smartphone or tablet.
- Utilize the telephone. If you’ve received a strange email purportedly from a friend, don’t be hesitant to phone or text the sender to verify that they sent the email. This is particularly true if the sender makes an unusual request, such as, “Please purchase 100 iTunes gift cards and provide me the card numbers by email. Thanks, Your Employer.”
- Windows displays file extension names. By default, Windows does not display file extensions, but you can alter this by choosing the “View” tab in File Explorer and selecting the checkbox to display file extensions. While this will not prevent fraudsters from spoofing file extensions, you will at least be able to identify faked extensions and avoid opening infected files.
- Invest in reliable antivirus software. Don’t panic if you click on a malicious link or file; a competent antivirus application will warn you of the danger, block the download, and prevent malware from infiltrating your system or network. Malwarebytes, for instance, offers free trials of its antivirus/anti-malware software before subscription.




































