
New Playground for Fraudsters: How Do I Get WhatsApp Scam IoCs?
SOCRadar analysts, while investigating phishing attacks via WhatsApp, recently found a significant increase in an attack with the same type of content. One of the most notable features of the attack was that it quickly reached a large audience.
How is the Attack Started?
The attackers attract the victims’ attention with the campaigns they create in the form of free spins of the gift wheel or opening a gift box for the anniversary of the organization’s foundation. To receive the so-called prize, users must share the same link with 20 people or in 5 different groups via WhatsApp. For this reason, it becomes inevitable to reach tens of thousands of people in a short time. The only condition to participate in the draw is to click on the link sent to the victim.
How Does the WhatsApp Scam Process Work?
The victim participating in the campaign needs to fill out a 4-question survey by clicking on the link.
Survey questions:
- Do you know the target company?
- How old are you?
- What do you think of the target company?
- What is your gender?
After answering simple survey questions, a pop-up like the one below opens. Then the victim is directed to various URLs, and finally, the Google page opens. It is not the same for every link. The information received from the user, such as the IP, computer name, etc., and the victim’s previous visit to the site are also taken into account.
What’s the Motivation Behind the Attack?
When SOCRadar analysts analyzed the traffic and its relationships, they found that the victim sent DNS queries with malicious distributed domains. An example domain and VirusTotal result are given below.
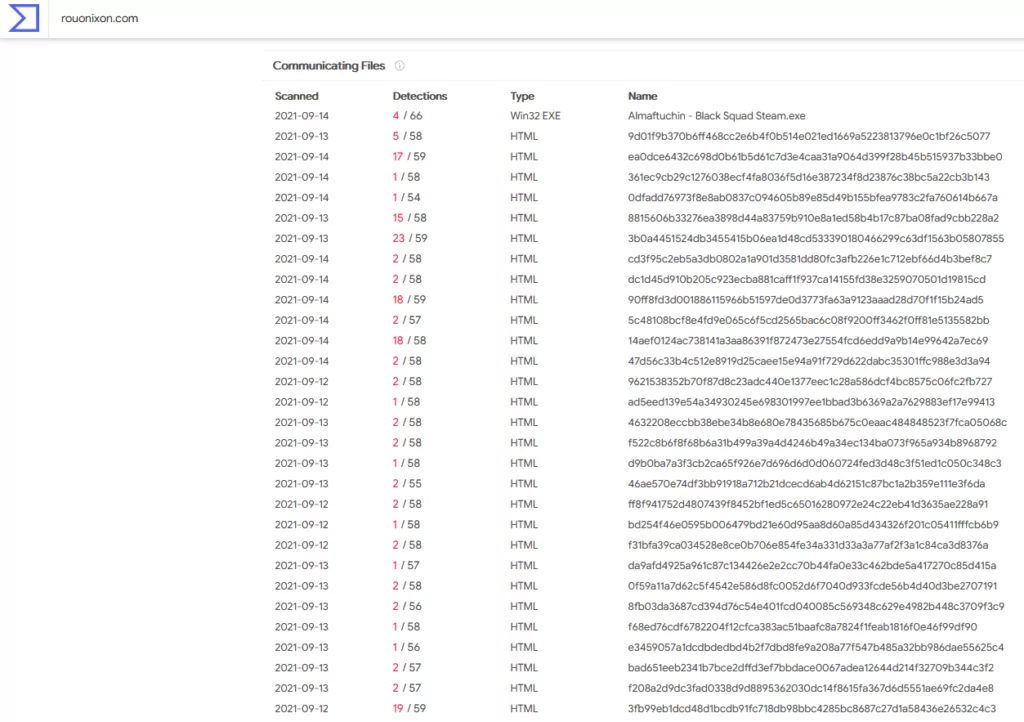
When a more detailed query is made for any of them, the trojan horse intended to infect the user is obtained.
The information stolen from the victims’ devices can be used for many different purposes as follows.
- Receiving and using saved passwords, session information, and cookies by accessing web browsers,
- Listening to the environment by turning on the microphone, if any,
- Deleting, copying files on the device,
- Demanding a ransom to unlock encrypted data by installing ransomware,
- Collecting the identity information on the logged-in website or mobile applications,
- Sending SMSs,
- Downloading files,
- Using credit card information in illegal actions,
- Sharing information on dark web forums for free to lose track after using it.
Is My Organization Affected by These Attacks?
Suppose a link is obtained about the domains detected to be used in the attack. In that case, you can see if your customers are under threat by typing your organization’s name, regardless of which organization it was prepared for.
According to the analysis made by SOCRadar researchers, it has been determined that vast audiences are targeted from e-commerce sites to banks, from the food sector to the automotive industry. An example URL used in the attacks is given below.
hxxps[:][/][/]delightvery[.]top[/]tzwgyGdd[/]Companyname-wa[/]
What Should Be Done to Protect From WhatsApp Scams?
All customers should be warned that there is no such campaign specific to the foundation year, that the links sent to them on WhatsApp and similar platforms should not be respected, and that they should not click on the link for their safety.
In addition, if they visit the organization’s website, they should be encouraged to make sure that they are going to the right site.
The takedown process must be started for each detected domain to be closed to access.
IoCs related to all cyberweapons used in cyber-attacks should be reached, and endpoint security devices should be fed with feeds to protect against potential attacks.
Whatsapp Scam: How Can I Access SOCRadar Threat Feed / IoC List?
You can access the relevant IoCs from the SOCRadar feeds in cyber attacks. There are over 2K constantly updated feed lists in the SOCRadar Feed Database:
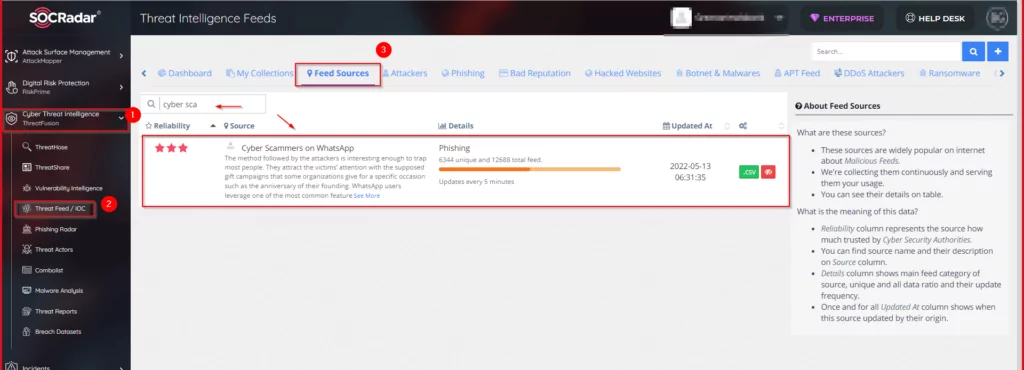
SOCRadar Platform>>ThreatFusion>>Threat Feed/IoC >> Feed Sources >>Cyber Scammers on WhatsApp
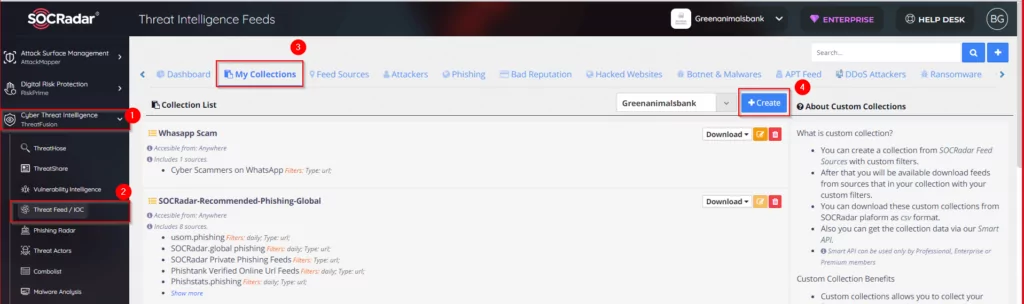
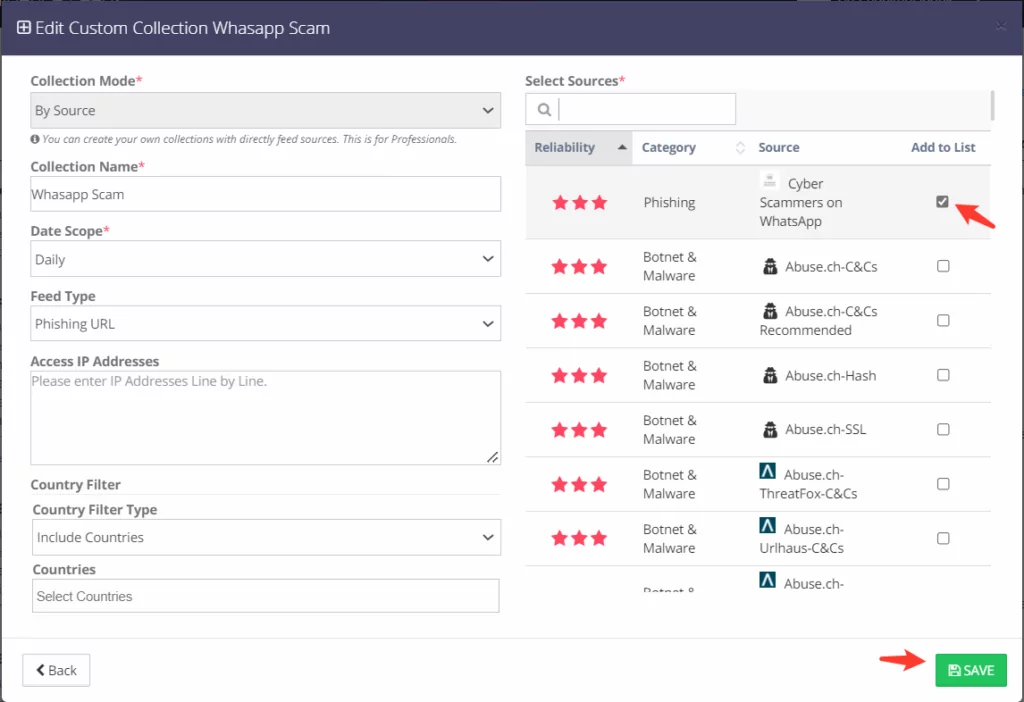
As shown below, you can customize IoCs for your security products in SOCRadar Threat Intelligence Feeds>>My Collections.
Click the “Create” button. Then select “By Source.”
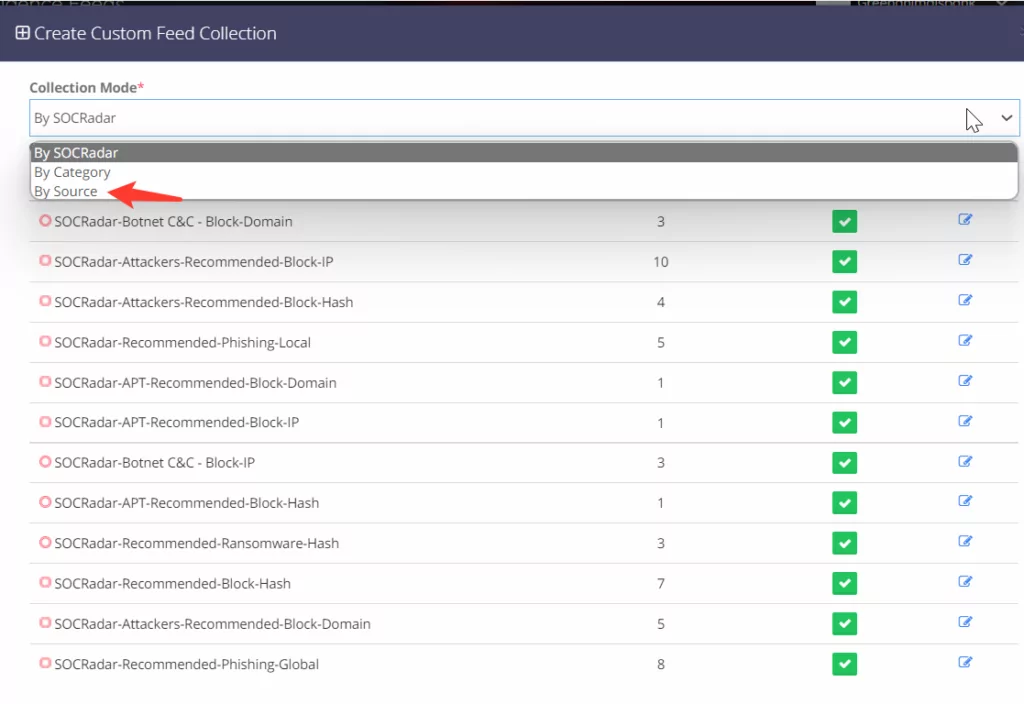
Customize it and then click the “Save” button.
You can download IoCs in CSV, TXT, Excel, or JSON format.
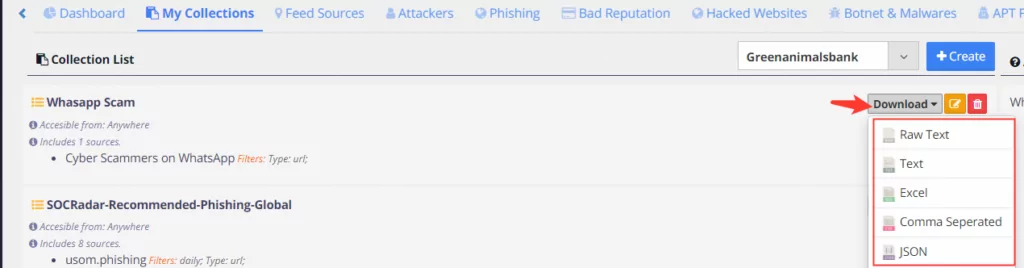
Related IoCs have been added to SOCRadar-Recommended-Block-Hash/Phishing-Global and SOCRadar-Recommended-Phishing-Loc list. If you have integrated with your security products, IoCs feed your device automatically.

If you have any questions, please don’t hesitate to reach us via [email protected].
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access.


































