
The Most Common Phishing Method Used by Cyber Scammers on WhatsApp
WhatsApp is the most downloaded and used messaging application by users in the world. For this reason, cyberattacks on WhatsApp can reach many people much faster than others. There is no single attacker type of fraudulent activity on WhatsApp.
There are many phishing methods, such as the message “WhatsApp is shutting down” from an acquaintance or someone not in your contacts suddenly asking you for money. However, SOCRadar Analysts recently observed a significant increase in attacks with the same type of content when examining phishing attacks on WhatsApp.
How is the Attack Started?
The method followed by the attackers is interesting enough to trap most people. They attract the victims’ attention with the supposed gift campaigns that some organizations give for a specific occasion such as the anniversary of their founding.
WhatsApp users leverage one of the most common features of WhatApp to claim the so-called rewards: sharing the same link on WhatsApp with 20 people or in 5 different groups. Just one click on the links that reach tens of thousands of people in a short time is enough to start the attack.
Which Steps Do Attackers Follow?
The victim, who clicks on the link, needs to fill out a four-question survey on the page that appears to participate in the so-called campaign:
- Do you know the company?
- Age
- What do you think of the company?
- Sex
After answering the questions, a pop-up opens as follows:
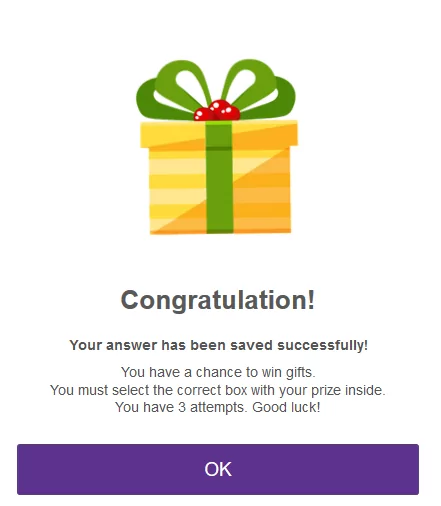
After confirming the pop-up message, 12 gift box images are showing to the victim. When one of these boxes is complete, victims can try their luck three times to find the correct box. The victim can continue with the campaign as the threat actors arrange to find a gift in one of every three attempts the victim will make.

At the end of the trials, a pop-up appears again, stating that you have won the award. For the victim to receive the gift, it is requested to share the link with 5 group accounts or 20 people. Thus, the spread of the campaign is ensured. Your circle of friends trusts you and clicks on these messages.
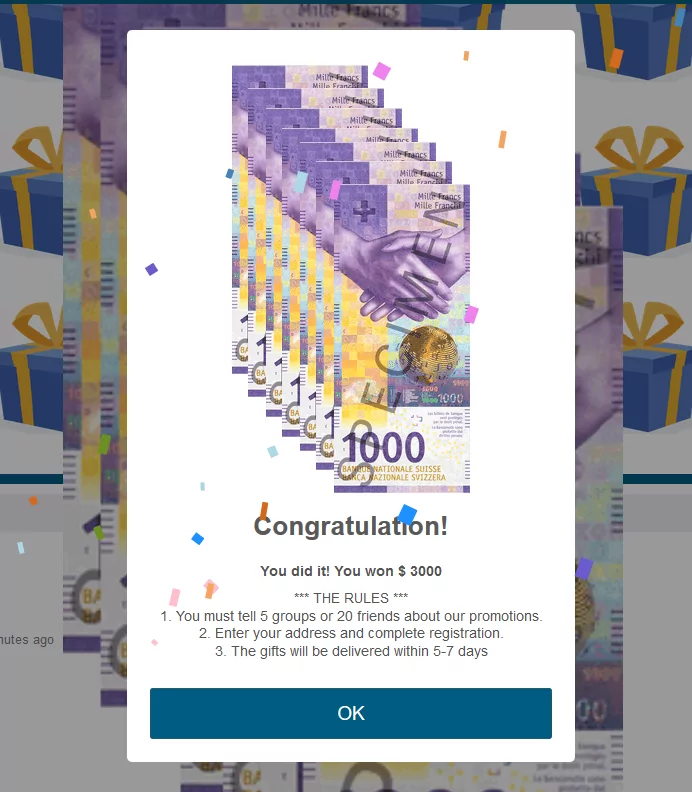
If the victim does not distribute the link with other individuals or groups, the campaign can continue. Again, a warning appears in front of the victim that the registration was successful. In particular, it is emphasized that the application to be downloaded is essential, and users are asked to continue the process.
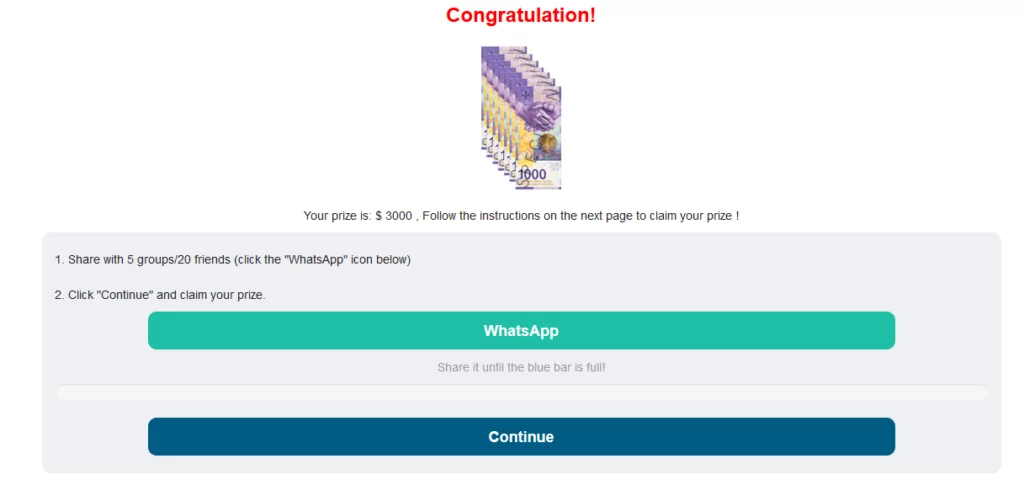
Then the victim is directed to various URL links, and finally, a Google page appears. However, this may not be true for all links. The stages vary from victim to victim. Because with the information such as IP address and computer name obtained from the user, the attacker can check whether someone has visited the same site before.
What’s the Motivation Behind this Attack?
When SOCRadar Analysts analyzed the hacked traffic and possible networks of relationships between the hackers, they found that the victims were sending DNS queries with malicious distributed domains. As an example, a domain and VirusTotal result are given below.
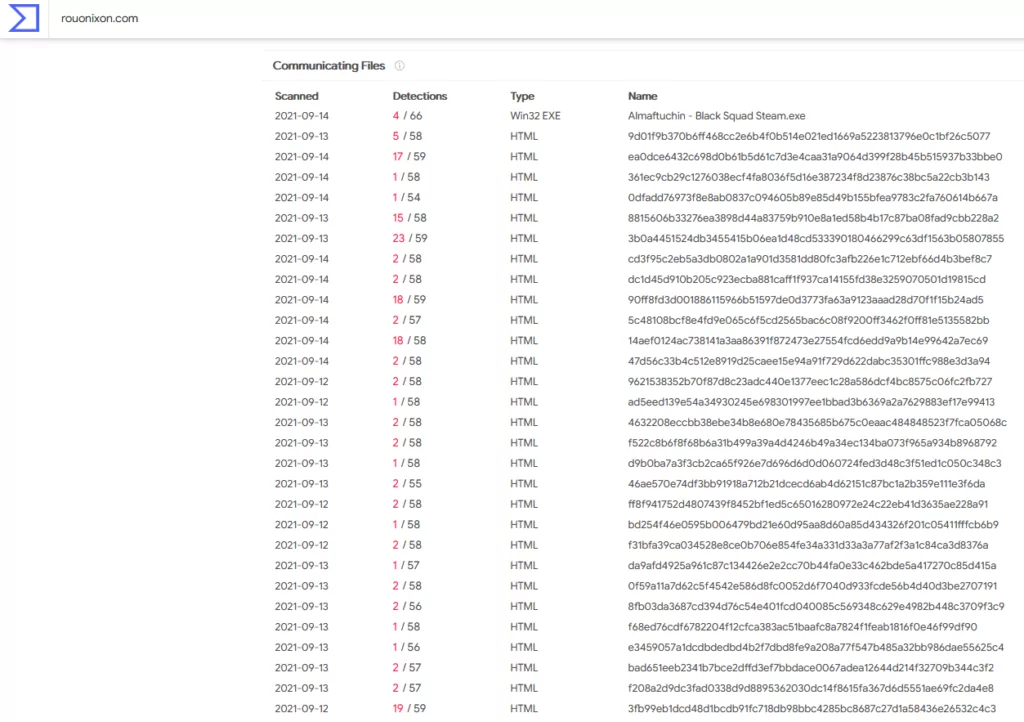
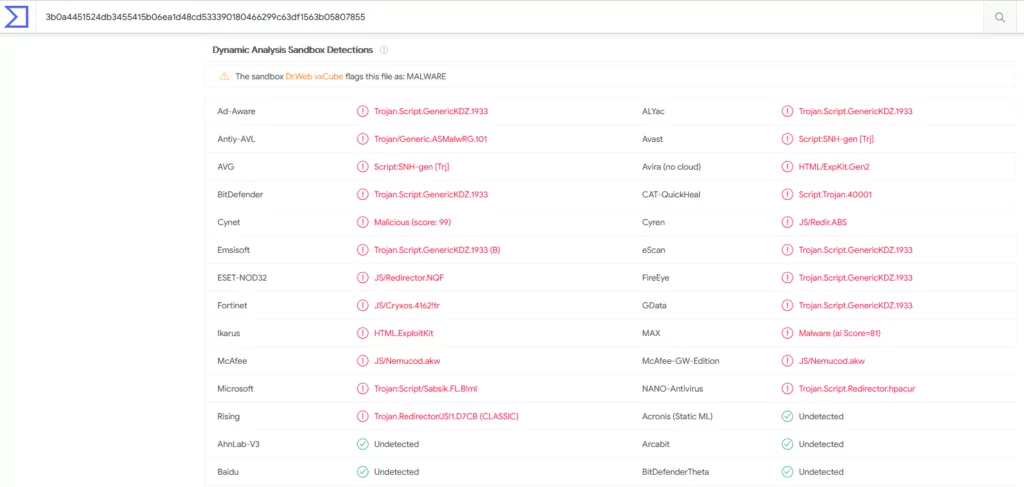
SOCRadar analysts conclude that the motivation for attacks using this method is to steal data or control the victim’s device with a Trojan to be implanted on the victim’s machine.
Information stolen from victims’ devices can be used for many different purposes:
- Retrieve and use saved passwords, login information, cookies by accessing browsers
- Listening to the environment of the victim by turning on the microphone
- Deleting, copying files on the device
- Charge/ransom the victim to unlock the encrypted data by installing ransomware on the victim’s device
- Stealing credentials on the logged-in website or mobile applications
- sending SMS
- making calls
- downloading files
- If you have credit card information, using it in illegal actions
- Sharing the data in question on dark web forums for free to lose track after the information is used
Organizations Targeted in the Attack
Many well-known brand names, especially in the e-commerce industry, are used in the scam campaign including Decathlon, Idea, Toyota, Continente, Honda, Lazada, Michelin, Adidas, Ford, Nestle, Cevital, Migros, Suzuki, Jumia, Keells, Shopee, Starbucks, Facebook, Jollibee, Burgerking, Huawei, and Walmart.
When SOCRadar analysts tracked the pishing attacks, they found that the campaign started two years ago. Still, when the campaign first started, the content varies in time.
Attacks Were At Their Peak in August
Until December 2020, there are just 22 domain/subdomain attacks recorded in various sources. The campaign started to be presented as a New Year’s gift lottery due to the approach in December. Then it turned into spinning wheels and opening gift boxes over time. When the domains used according to the months are analyzed, the peak in August is very apparent.
According to publicly available data, attacks exceeded two thousand in August and reached the ceiling amount.
The campaign, which seems to have used 4071 domains/subdomains in total, is still ongoing. The 20 sample domains used in the campaign are as follows:
vividcement[.]top
vividbasic[.]top
drawnturkey[.]top
eligiblebiology[.]top
fluentessay[.]top
diligenttwo[.]top
greenlightsa[.]top
smoke[.]ball
vitalupgrade[.]top
t5chgt[.]shop
eeanutees[.]top
fqemfz[.]shop
2j0oqe[.]shop
conferenceesd[.]xyz
palacewalnut[.]top
0sz3t2[.]shop
gratificationtoken[.]top
spectaclevenue[.]top
efficientdoctor[.]top
Optimismtrap[.]top
Attackers can create new domain directories with time-adjusted parameters or target multiple organizations’ customers using the same domain. The only thing that changes in the page contents of the re-created domains is the year of the establishment and its logo.
How Do You Know If Your Organization Is Affected By This Attack?
When a link is obtained about the domains detected to be used in the attack, one can see if an organization’s potential customers are under threat by typing the name of the organization.
According to the analyzes made by SOCRadar analysts, organizations from many different sectors, from e-commerce sites to finance, from the food industry to the automotive industry, can become the target of attacks.
An example URL used in the attacks is as follows:
hxxps[:][/][/]delightvery[.]top[/]tzwgyGdd[/]Companyname-wa[/]
How to Avoid Such Attacks?
All users should be informed in advance of such phishing attacks. It should be explained that any organization will not make a unique anniversary campaign on WhatsApp. Users should be warned that they should not respect the links sent to them by their relatives on WhatsApp, emphasizing the campaign. Users should also be told that when they encounter such a suspicious situation, they must first visit the organization’s official website.
A takedown process should be started for each detected domain to be closed to access.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free



































