
What is EMOTET Malware and How to Protect Yourself
According to Arne Schoenbohm, who leads the German Federal Office of Information Security (BSI), EMOTET is the king of malware. EMOTET actively attacks many devices in every industry, including small-large businesses, individuals, non-profit organizations, governments, and schools. Regarding that, each attack, on average, costs around 1M$. If malware had a council, this infamous malware would be the Caesar. Thus, the kaiser insists on not relinquishing its crown; although it is an enemy we have known for about ten years, it is still in the wild and actively used even in 2023.
What is EMOTET?

EMOTET was first detected and described as a banking trojan in 2014. However, it constantly evolved and became much more destructive after each upgrade. This upgradeable, modular designbecame the main reason why it is dangerous. Progressing over the years, Emotet transformed into an intricate malware platform featuring a modular architecture, empowering it to execute an extensive array of malicious actions. Emotet has experienced a series of updates and alterations across its history. By 2017, enhancements were introduced, including the ability to install supplementary malware like TrickBot and Qakbot. In 2018, Emotet incorporated a spam module to initiate massive spam campaigns, sending millions of unsolicited messages daily. The year 2019 saw the integration of a fresh module for pilfering email content and contact lists.
Emotet commonly propagates via phishing emails that carry harmful attachments or links. The malware is downloaded and installed on their system when users interact with these attachments or links. Emotet possesses polymorphic capabilities, enabling it to modify its code and avoid being detected by antivirus programs. After installation, Emotet establishes persistence on the compromised system, ensuring it remains active even following a reboot. Additionally, it shows communication with command-and-control (C2) servers to receive commands and fetch supplementary payloads like other types of malware or ransomware.
Since it uses C&C servers, EMOTET can be upgraded without any visual signs after settling a device, just like any operating system update in our daily lives. However, through its upgrades, EMOTET does not just patch itself. It also loads other malware to the device confidentially.
With many tricks up its sleeve, EMOTET became a MaaS (Malware-as-a-Service) portal for cyberattackers eventually. To exemplify this situation, EMOTET can be described as an experienced thief who breaks into your house, copies your keys, steals your valuable information secretly, and then sells all this information to other less skilled but dangerous thieves.
How Does it Spread?
Mail Spam and Phishing

Spamming mail is the most common way to spread this insidious trojan EMOTET. Its spam emails include macro-enabled document files or links.
These spam emails may contain malicious attachments or URLs that allows the attackers to sneak into the victim’s system through these. Although it is a quite common and known malware spread method, it can still take over many users because these e-mails seem reliable to the recipient.
Another danger that does not always appear as spam e-mail is targeted phishing attacks. This way, especially used by APTs and major ransomware operators, is the starting point for a quarter of all cyber attacks.
Common Passwords
With a connected network, EMOTET spreads and infects the systems by using the common password lists. It tries to guess its way onto other linked systems in a brute-force assault*.
*Brute-force assault: A brute-force assault in cryptography entails an attacker submitting many passwords or passphrases to guess them accurately.
EMOTET’s Short-Term Decline
In late January 2021, Europol reported that the “EMOTET” virus and botnet had been disabled because of international cooperation between eight law enforcement agencies. It resulted in law enforcement and judicial authorities gaining control of the infrastructure and bringing it down from the inside in the last week of January 2021.
A security researcher operating under the handle “milkream” determined that EMOTET was deploying a new module onto compromised devices on January 27, 2021, the same day as Europol’s press announcement. Victims’ infected computers were forwarded to this law enforcement-controlled infrastructure. That was a revolutionary and unique way to disrupt the actions of cybercrime facilitators efficiently. However, this disruption did not last long.
EMOTET Resurged
In 2022, Emotet experienced a resurgence and persistently deployed advanced forms of malware, including ransomware, in the aftermath of the initial compromise. Researchers observed a significant surge in Emotet-related activities throughout the year, indicating that it was frequently utilized as the preferred method for distributing ransomware payloads. However, with Microsoft’s update that disables VBA macros for downloaded files, Emotet’s primary attack vector weakened. In the quarter of 2022, Emotet activities started to decline compared to the rest of the year.
In 2023, three distinct malspam campaigns were executed according to Eset’s research, each experimenting with different intrusion methods and social engineering tactics. However, the decreasing scale of the attacks and frequent shifts in strategy may indicate dissatisfaction with the results.
The initial campaign occurred around March 8th, 2023, involving the Emotet botnet distributing Word documents that masqueraded as invoices. These documents contained malicious VBA macros, despite Microsoft’s default disabling of VBA macros, which prevented victims from executing the embedded harmful code.
The attackers acknowledged these limitations in the second campaign, spanning from March 13th to March 18th. In addition to using the reply chain approach, they transitioned from VBA macros to OneNote files (ONE) embedded with VBScripts. Upon opening the file, victims encountered what appeared to be a secured OneNote page, prompting them to click a “View” button to access the content. Concealed behind this visual element was a hidden VBScript set to download the Emotet DLL.
Even though a OneNote warning alerted users about potential malicious content, individuals often click on such prompts out of habit, inadvertently allowing attackers to compromise their devices. The final observed campaign, launched on March 20th, leveraged the upcoming income tax deadline in the US. Emails sent by the botnet posed as communications from the US tax office IRS and contained an attached archive file named “W-9 form.zip.” Inside the ZIP file was a Word document embedded with a malicious VBA macro, which the recipient likely had to enable. Alongside this US-targeted campaign, another co-occurring campaign utilized VBScripts and the OneNote method.
What Should You Do If You Have Been Infected?

You must clean your system when you realize or suspect that the EMOTET has infected your device. Before that, you should inform people on your e-mail list to protect them from EMOTET. Then, you should check the network system since it may spread through.
As a next step, you should change your passwords and login details for all your accounts to prevent spreading. The key point is here; you should not use the same device since it is already infected. In other words, you should use a different device that is not connected to the same infected network.
After these steps, you can move on to cleaning the infected part. The important thing here is that you can get the virus again when you connect, so you must be sure all parts and each device connected to the same network are immaculate. You can either use an antivirus program or a specialist in this area for this step.
How Can SOCRadar Help Protect Yourself from EMOTET and Other Malware?
SOCRadar’s Extended Cyber Threat Intelligence module helps cybersecurity teams investigate threats with its easy-to-use design and in-depth data. IP addresses can be blacklisted due to malware spread or being part of a botnet. It also may provide feeds for Emotet, where you can track current IoCs and TTPs and integrate them into your security systems. In this wayyou can proactively improve your security posture by using SOCRadar’s Extended Threat Intelligence approach.
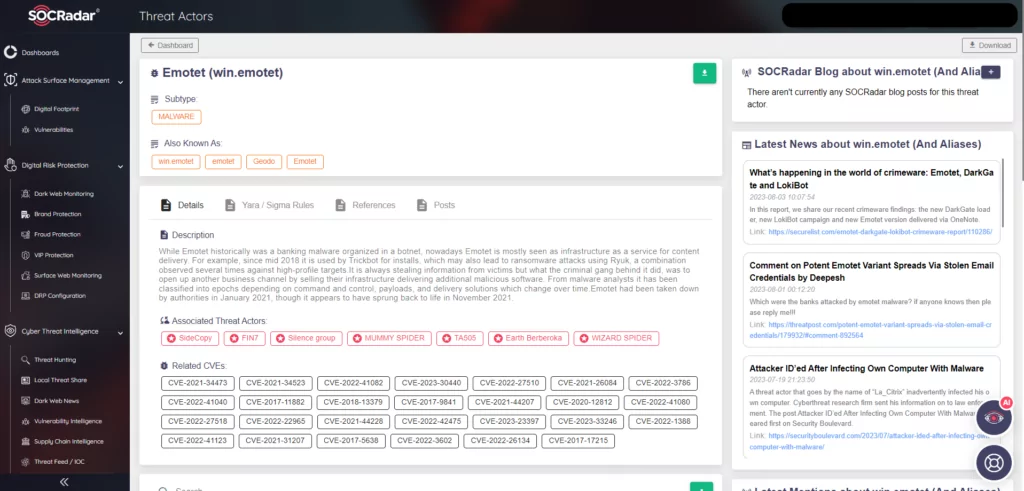
You can also check Emotet’s primary attack vector, the e-mail attachments, and the e-mail itself via SOCRadar Malware Analysis.
Additional References
https://ensarseker1.medium.com/emotet-one-of-the-most-dangerous-trojans-ever-created-a8c7fb4393
https://www.welivesecurity.com/2023/07/06/whats-up-with-emotet/


































