APT Profile: Volt Typhoon
[Update] February 01, 2024: U.S. Government Actions Against Volt Typhoon
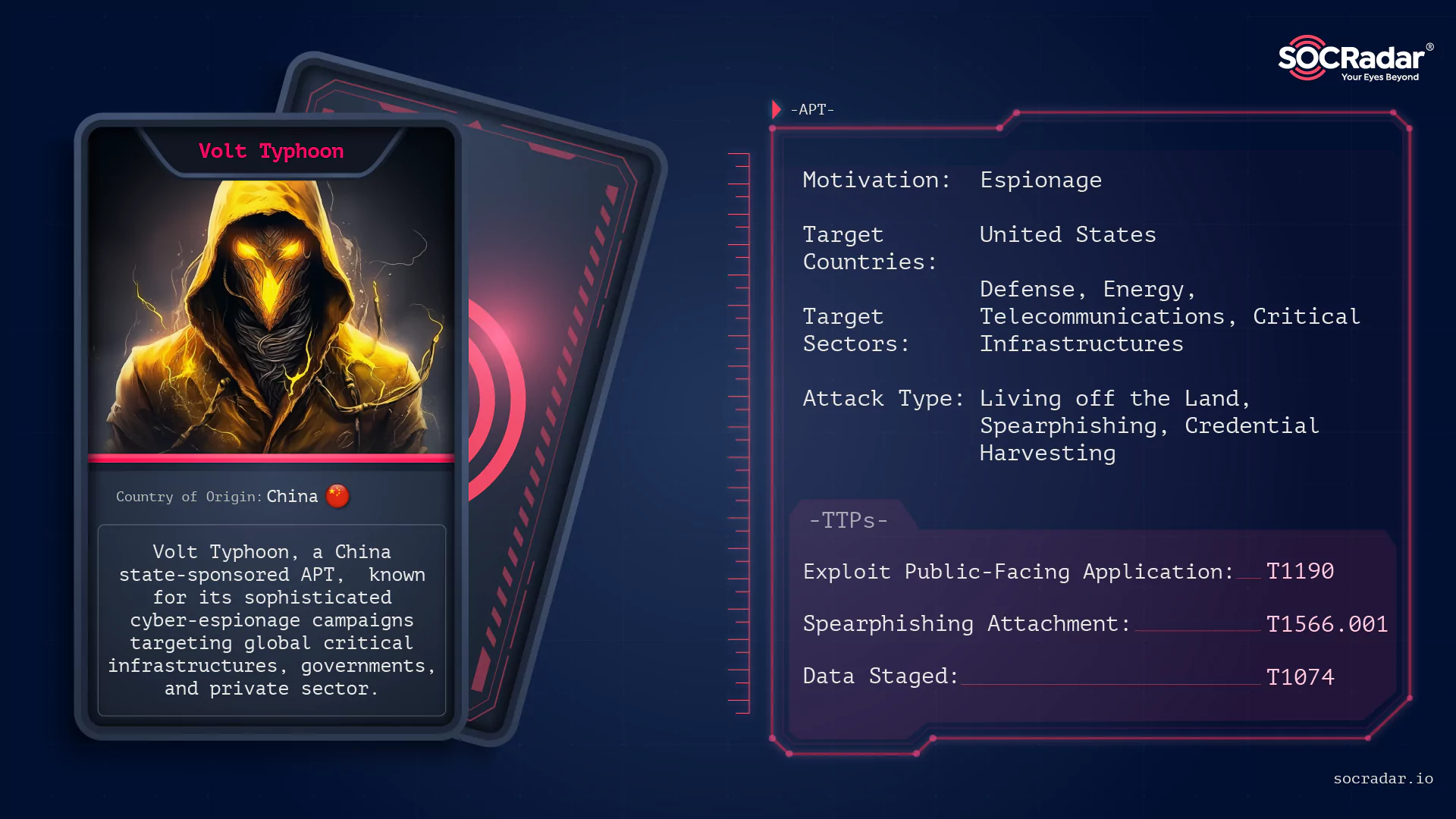
As cyber currents ebb and flow, a storm named Volt Typhoon surges from the digital depths. This isn’t your typical tempest from the sea but a state-sponsored maelstrom with a tendency for espionage. Volt Typhoon, believed to be backed by the Chinese government, stands out for its sophisticated tactics and high-profile targets. This group has been at the forefront of several cyber-espionage campaigns, targeting critical infrastructures, governmental bodies, and private sectors across various nations.
In this article, we will delve deep into the operations, objectives, and techniques of the Volt Typhoon, shedding light on their way of working and the potential threats they pose.
Who is the Volt Typhoon?
Volt Typhoon (or BRONZE SILHOUETTE) is a sophisticated state-sponsored Advanced Persistent Threat (APT) group widely believed to have its origins in China. Over the past few years, their cyber activities have been closely monitored and documented by various cybersecurity firms, intelligence agencies, and government bodies worldwide.
The group is believed to have been operating since 2021 but is mostly active in May 2023.

The group primarily focuses on intelligence gathering, with a keen interest in both governmental and private sectors. The group’s operations are characterized by precise planning, custom malware deployments, and stealthy infiltration techniques, making them one of the most formidable cyber adversaries nowadays.
Their alleged backing by a nation-state not only provides them with advanced resources but also potentially aligns their objectives with geopolitical interests, further amplifying the threat they pose.
How does the Volt Typhoon attack?
The success of the Volt Typhoon in infiltrating high-profile targets can be attributed to their diverse and evolving attack methodologies. Here’s a breakdown of some of their most notable techniques:
Living off the Land (LotL) Techniques: Volt Typhoon is adept at using legitimate tools and processes present on the target system to carry out their malicious activities. By leveraging these tools, they can effectively blend in with regular network activities, making their detection significantly more challenging.
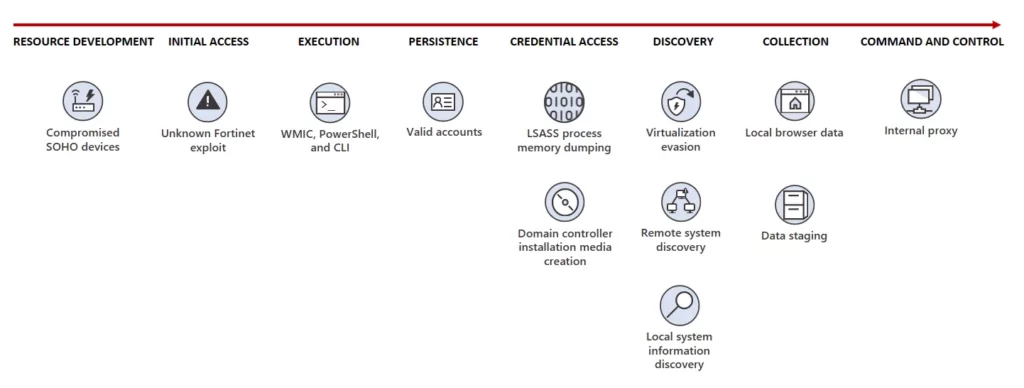
Spear Phishing: One of their primary infiltration methods involves crafting highly customized phishing emails tailored to lure specific individuals or departments within an organization. These emails often contain malicious attachments or links, leading to web pages that deploy exploit techniques.
Exploiting Known Vulnerabilities: The group is known to keep an eye on public vulnerability disclosures. They act swiftly to exploit these vulnerabilities before organizations can patch them, gaining unauthorized access to systems.
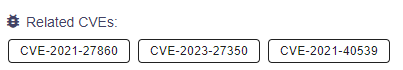
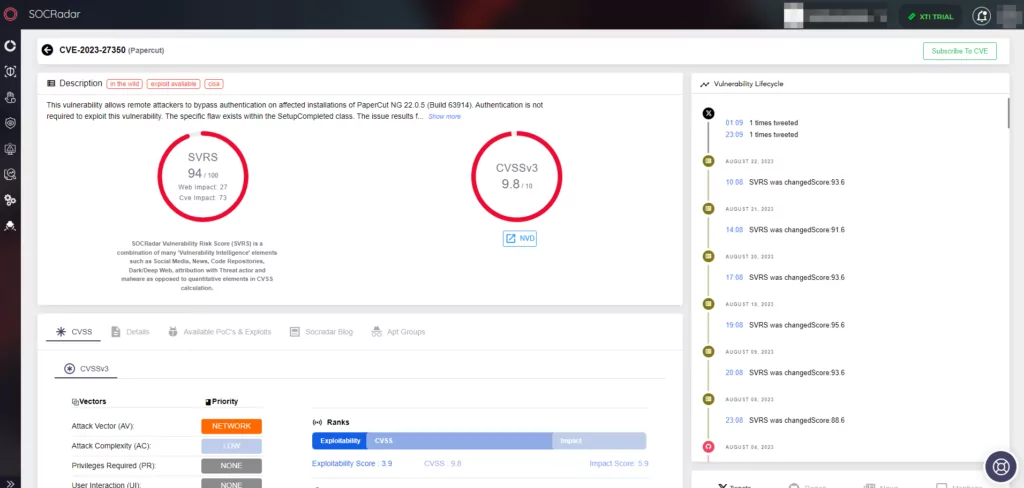
When looking at the vulnerabilities exploited by the group, it is possible to say that they mostly exploited the Zoho Management vulnerabilities (CVE-2021-27860 and CVE-2021-40539) observed in 2021, and the Papercut vulnerability (CVE-2023-27350) that came to the agenda in 2023.
Custom Malware Deployment: Volt Typhoon has developed a range of custom malware tools tailored for specific tasks, from maintaining persistence on a compromised system to data exfiltration. Their malware often exhibits advanced evasion techniques to bypass traditional security solutions.
Credential Harvesting: Once inside a network, the group often seeks to gather credentials, which can be used to move laterally across the network, accessing more systems and escalating privileges.
What are the Targets of the Volt Typhoon?
Volt Typhoon’s targeting pattern reveals a strategic approach, focusing on entities that can provide them with valuable intelligence or offer geopolitical advantages. Their targets span across various sectors and regions:
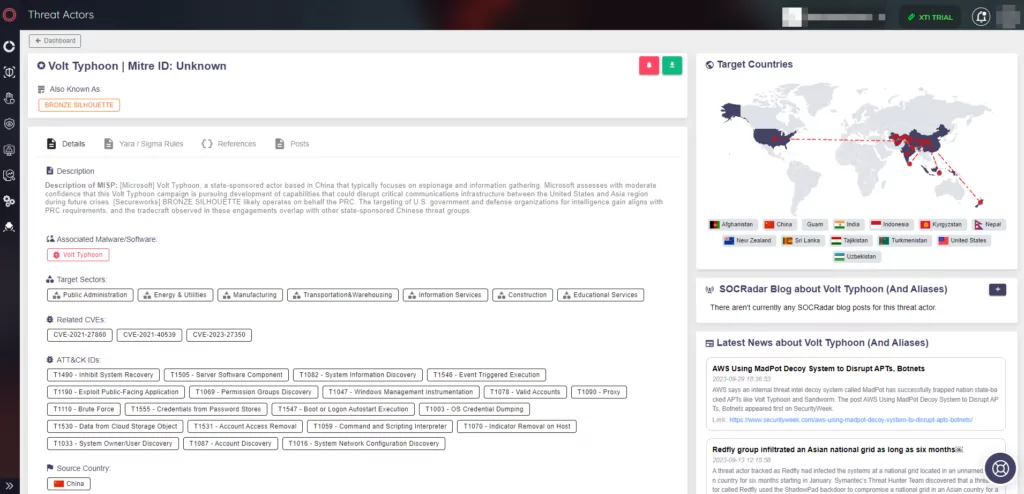
Targeted Sectors:
Defense: Military installations, defense contractors, and research institutions have been prime targets, likely to gather intelligence on defense capabilities, strategies, and emerging technologies.
Energy: The group has shown interest in energy sectors, including power grids and oil & gas installations. Compromising such entities can provide both intelligence and potential disruption capabilities.
Telecommunications: Telecom sectors offer a wealth of data, from communication intercepts to infrastructure details, making them a valuable target.
Critical Infrastructure: Beyond energy, other critical infrastructures like transportation, water supply, and healthcare have also been in their crosshairs.
Targeted Countries:
While the U.S. remains a primary target for Volt Typhoon, their activities have not been limited to one region. Evidence suggests operations in various parts of Europe, Asia, and other regions. Their targeting pattern often aligns with geopolitical events or tensions, suggesting a strategic approach to their campaigns.
The broad spectrum of their targets underscores Volt Typhoon’s capabilities and the potential threat they pose to global security and stability.
Notable operations of Volt Typhoon:
Volt Typhoon’s cyber campaigns have left a significant mark on the global cybersecurity landscape. Here are some of their most notable operations:
U.S. Critical Infrastructure Compromise: One of the most alarming campaigns involved the group targeting U.S. critical infrastructure. Leveraging LotL techniques, they infiltrated several key installations, raising concerns about potential disruptions and the safety of critical services.
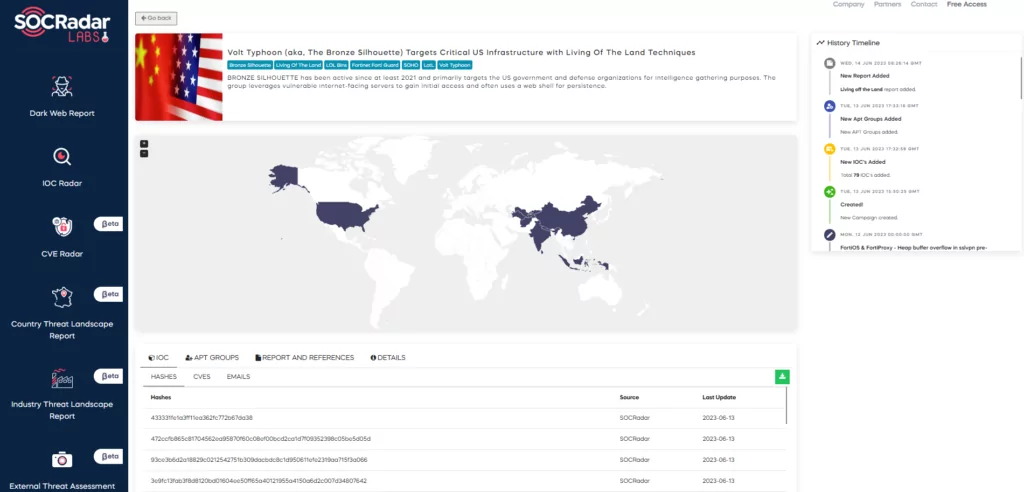
Espionage Campaigns: Volt Typhoon has been linked to a series of cyber-espionage campaigns targeting defense organizations, governmental entities, and private sectors. These campaigns often involve the theft of sensitive data, intellectual property, and strategic information.
Asia’s National Grid Attack: In a bold move, the group compromised a national grid in an Asian country, maintaining their presence for several months. This operation highlighted their capability to infiltrate and potentially disrupt essential services in a nation.
Credential Theft and Lateral Movement: In multiple instances, the group has demonstrated its prowess in stealing credentials from compromised systems and using them to move laterally across networks. As a result, they can access more systems, escalate privileges, and deepen their foothold.
Use of Custom Malware Tools: Several of their operations have unveiled the use of custom malware tools tailored for specific tasks. These tools often exhibit advanced evasion and persistence techniques, therefore making them challenging to detect and remove.
These operations provide a glimpse into the group’s capabilities, objectives, and the potential threats they pose. Their strategic targeting and advanced techniques underscore the need for robust cybersecurity measures to counter such threats.
U.S. Government Actions Against Volt Typhoon
Recent developments from the U.S. Department of Justice and the Cybersecurity and Infrastructure Security Agency (CISA) reveal significant actions against the Chinese state-sponsored group known as Volt Typhoon. The U.S. government disrupted a botnet used by Volt Typhoon to conceal their hacking activities, which targeted critical infrastructure in the U.S. and other countries. This operation involved removing malware from infected routers while maintaining their legitimate functions.
Additionally, CISA Director Jen Easterly’s statement before the House Select Committee on Strategic Competition highlights the gravity of Volt Typhoon threat. The group has deeply infiltrated U.S. critical infrastructure, preparing for potential destructive cyber-attacks. Easterly emphasizes the necessity of collective action and resilience against such threats, including the importance of reporting cyber incidents, utilizing CISA’s services, and the need for technology companies to prioritize security in product development. This collective effort is vital for national security and to counter sophisticated cyber adversaries like Volt Typhoon.
Read the full DOJ statement and CISA Director Jen Easterly’s statement for more information.
Conclusion
The emergence and activities of state-sponsored threat actors like Volt Typhoon underscore the intricate and evolving nature of the cyber threat landscape. With nation-states leveraging advanced cyber capabilities for espionage, influence, and potential sabotage, the challenges for defenders have never been more pronounced. Volt Typhoon, with its alleged state backing and sophisticated modus operandi, represents a clear and present danger to global security, stability, and economic interests. As their campaigns continue to unfold, it becomes imperative for nations, organizations, and individuals to understand the threat they pose and take proactive measures to safeguard their digital assets and interests.
Security Recommendations against Volt Typhoon:
In light of the significant threat posed by Volt Typhoon, organizations and individuals must adopt a proactive and layered approach to cybersecurity. Here are some recommended measures to counter the threats from this formidable group:
Regular Updates and Patching: Ensure that all software, operating systems, and hardware are regularly updated. Promptly apply security patches to mitigate known vulnerabilities that could be exploited.
Employee Training: Conduct regular cybersecurity awareness training for employees. Emphasize the dangers of spear-phishing and teach them how to recognize and report suspicious emails or activities.
Implement Multi-factor Authentication (MFA): Use MFA wherever possible, especially for accessing critical systems and sensitive data. This adds an additional layer of security, even if credentials are compromised.
Network Segmentation: Segment your network to ensure that if one section is compromised, the threat actor cannot easily move laterally to other parts of the network.
Advanced Threat Detection: Employ advanced threat detection solutions that can identify and counter sophisticated threats in real-time. Consider solutions that use artificial intelligence and machine learning for enhanced detection capabilities.
Regular Backups: Regularly back up critical data and ensure that backups are stored in a secure location, isolated from the main network. This ensures data availability even in the event of a ransomware attack or data breach.
Incident Response Plan: Have a well-defined incident response plan in place. Ensure that all employees are familiar with the plan and know the steps to take in the event of a security breach.
Limit Privileged Access: Adopt the principle of least privilege. Ensure that only necessary personnel have access to critical systems and data, and regularly review and update access permissions.
By adopting these measures and maintaining a proactive security posture, organizations can significantly reduce the risk of falling victim to Volt Typhoon’s cyber campaigns and safeguard their assets against potential threats.
IoCs Related to Volt Typhoon
| IP | 104.161.54[.]203 |
| IP | 109.166.39[.]139 |
| IP | 23.227.198[.]247 |
| CVE | CVE-2021-27860 |
| CVE | CVE-2021-40539 |
| CVE | CVE-2023-27350 |
| HASH | ef09b8ff86c276e9b475a6ae6b54f08ed77e09e169f7fc0872eb1d427ee27d31 |
| HASH | d6ebde42457fe4b2a927ce53fc36f465f0000da931cfab9b79a36083e914ceca |
| HASH | d6ab36cb58c6c8c3527e788fc9239d8dcc97468b6999cf9ccd8a815c8b4a80af |
| HASH | e453e6efc5a002709057d8648dbe9998a49b9a12291dee390bb61c98a58b6e95 |
| HASH | 7939f67375e6b14dfa45ec70356e91823d12f28bbd84278992b99e0d2c12ace5 |
For more IOCs, you can visit the Threat Actor/Malware page under the CTI module of SOCRadar XTI Platform.
MITRE ATT&CK TTPs of Volt Typhoon
| Technique | ID |
| Resource Development | |
| Compromise Infrastructure: Server | T1584.004 |
| Compromise Infrastructure: Botnet | T1584.005 |
| Obtain Capabilities: Tool | T1588.002 |
| Initial Access | |
| Exploit Public-Facing Application | T1190 |
| Execution | |
| Command and Scripting Interpreter: PowerShell | T1059.001 |
| Command and Scripting Interpreter: Windows Command Shell | T1059.003 |
| Windows Management Instrumentation | T1047 |
| Persistence | |
| Server Software Component: Web Shell | T1505.003 |
| Defense Evasion | |
| Indicator Removal: File Deletion | T1070.004 |
| Indicator Removal: Clear Network Connection History and Configurations | T1070.007 |
| Masquerading: Match Legitimate Name or Location | T1036.005 |
| Masquerading: Masquerade File Type | T1036.008 |
| Valid Accounts: Domain Accounts | T1078.002 |
| Virtualization/Sandbox Evasion: System Checks | T1497.001 |
| Credential Access | |
| Credentials from Password Stores | T1555 |
| OS Credential Dumping: LSASS Memory | T1003.001 |
| OS Credential Dumping: NTDS | T1003.003 |
| Discovery | |
| Account Discovery: Domain Account | T1087.002 |
| Log Enumeration | T1654 |
| Permission Groups Discovery: Local Groups | T1069.001 |
| Permission Groups Discovery: Domain Groups | T1069.002 |
| Process Discovery | T1057 |
| Query Registry | T1012 |
| Remote System Discovery | T1018 |
| Software Discovery | T1518 |
| System Information Discovery | T1082 |
| System Network Configuration Discovery | T1049 |
| System Network Connections Discovery | |
| System Owner/User Discovery | T1033 |
| Collection | |
| Archive Collected Data: Archive via Utility | T1560.001 |
| Data from Local System | T1005 |
| Data Staged | T1074 |
| Local Data Staging | T1074.001 |



































