
Arkana Ransomware Attack on WideOpenWest: What You Need to Know
A previously unknown threat actor has launched its first ransomware attack, marking a worrisome new chapter in the cyber threat landscape. This alarming incident involves Arkana, a previously unknown threat actor, and WideOpenWest, one of the largest cable and broadband service providers in the US. The alleged breach, first publicized by vx-underground, reveals that Arkana has accessed over 403,000 customer accounts and seized control of critical backend infrastructures, including AppianCloud and the Symphonica system. In this article, we dive into the details of this breach, its implications, and what it means for both WOW! and its customers.
What is WideOpenWest?
WideOpenWest, Inc. (WOW!) is one of the largest cable and broadband service providers in the United States, ranking as the eighth-largest operator in the industry. Founded in 1996 and headquartered in Denver, Colorado, WOW! delivers high-speed Internet, cable television, and digital phone services to its customers across several states, including Alabama, Florida, Georgia, Illinois, Indiana, Maryland, Michigan, Ohio, South Carolina, and Tennessee.
With a network that reaches approximately 1.9 million homes and businesses, WOW! serves around 538,100 subscribers.
Details About Arkana Security
Arkana Security is a newly emerged ransomware group that specializes in exploiting vulnerabilities in corporate systems, with a clear focus on extortion. According to their Onionsite, the operation is based on a three-phase model: Ransom, Sale, and Leak—each stage designed to coerce businesses into paying for the return of their compromised data. Based on the language used on the website and a recently shared video by vx-underground, there is evidence suggesting the group has Russian origins or affiliations.
In the first phase, the group claims to notify affected companies of a data breach, offering them a brief window to secure their systems before the data is exposed. If the company fails to act, Arkana escalates their activities by allegedly selling the stolen data on the dark web. The group gives companies one final chance to buy back the data, claiming that they will delete all copies and prevent further exposure if the deal is made. However, should the company refuse, Arkana moves to the final phase—publicly leaking the data, with the threat of reputational damage, financial loss, and legal consequences. This phase is further dramatized by Arkana’s creation of a so-called “Wall of Shame,” which they use to publicly shame companies that fail to address their security lapses.
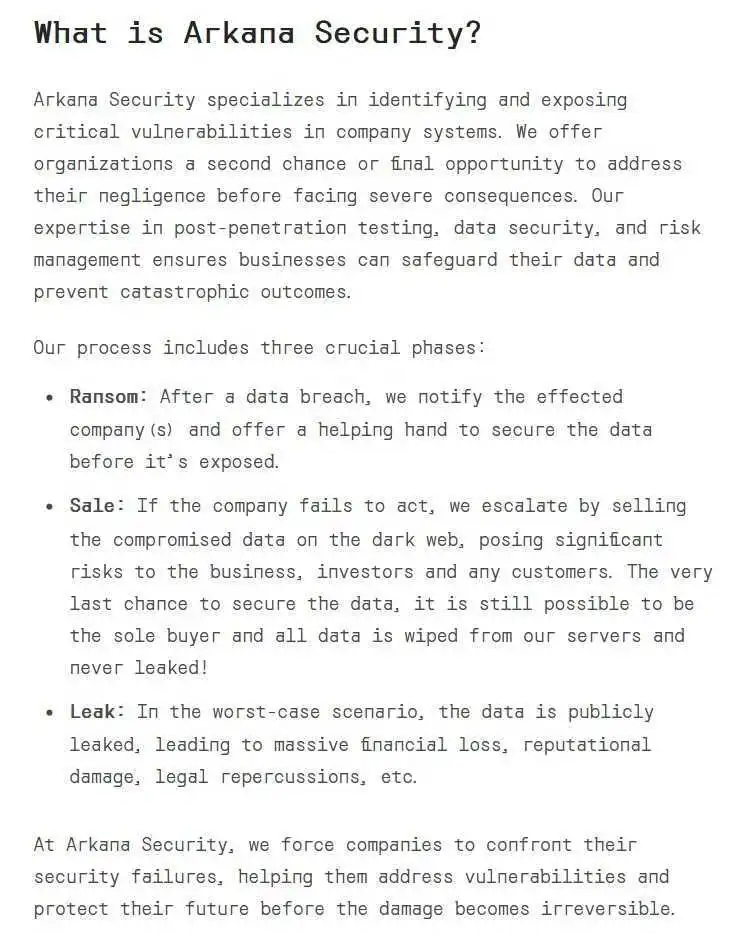
About Page from Arkana Security Onion Site
Arkana’s methods and tactics are unmistakably those of a ransomware group, operating under the guise of offering a “second chance” to companies before fully exploiting their vulnerabilities.
First Victim of Arkana Security, WideOpenWest (WOW!)
Previously unknown ransomware group, Arkana, has allegedly breached the systems of WideOpenWest (WOW!), one of the largest Internet Service Providers (ISP) in the United States. The threat actor has purportedly released extensive details about the alleged compromise, including sensitive customer data and internal company access.
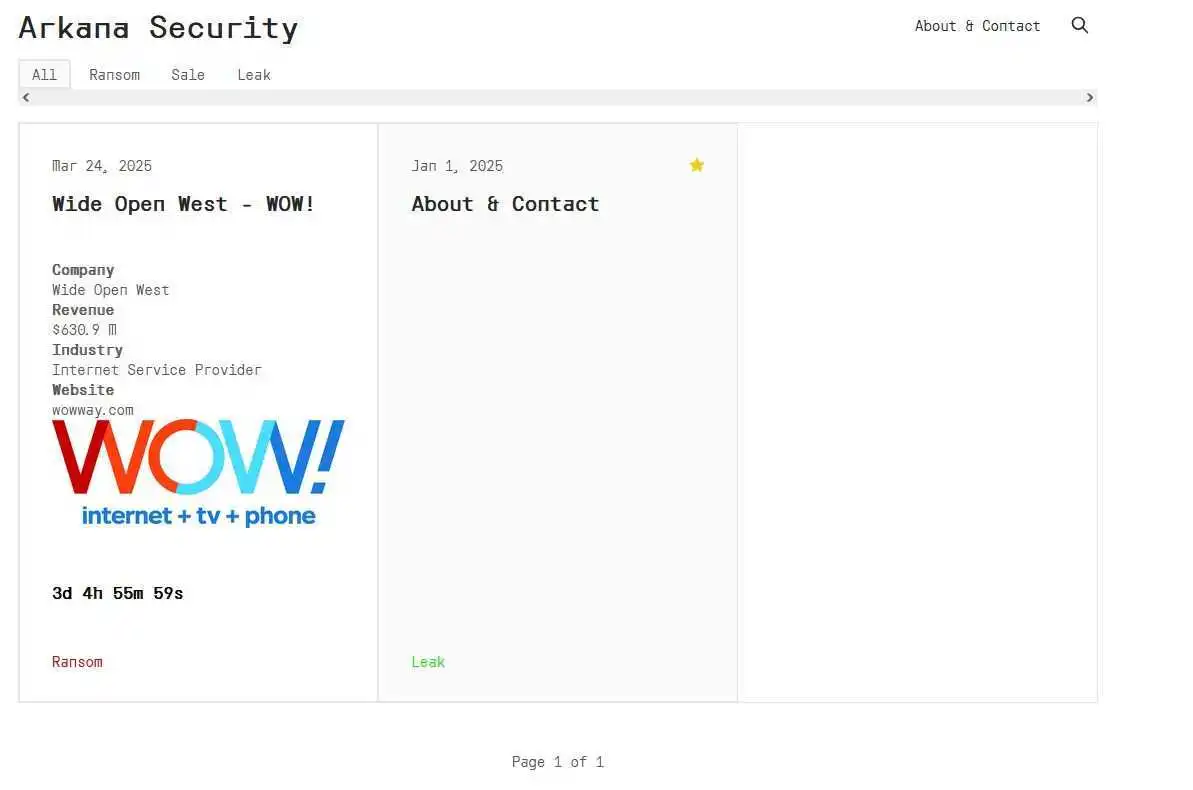
Arkana Security Onion Site Showing WOW as a Victim
Arkana, a previously unknown entity in the cyber threat landscape, has reportedly gained significant access to WOW!’s infrastructure, demonstrating advanced levels of infiltration. Leaked materials from the group suggest they have compromised over 403,000 customer accounts, including usernames, passwords, security questions, and service package details. They further claim full control over WOW!’s Symphonica system, which they claim that they can use to push malware onto customer devices.
The group has also allegedly infiltrated critical backend systems, such as AppianCloud, and gained access to its APIs, including those for authentication and transactions. With this control, Arkana can manipulate backend code, alter business logic, and modify data flows, including customer financial transactions, personal details, and billing records. Additionally, they can execute unauthorized transactions, access customer accounts, and modify billing information.
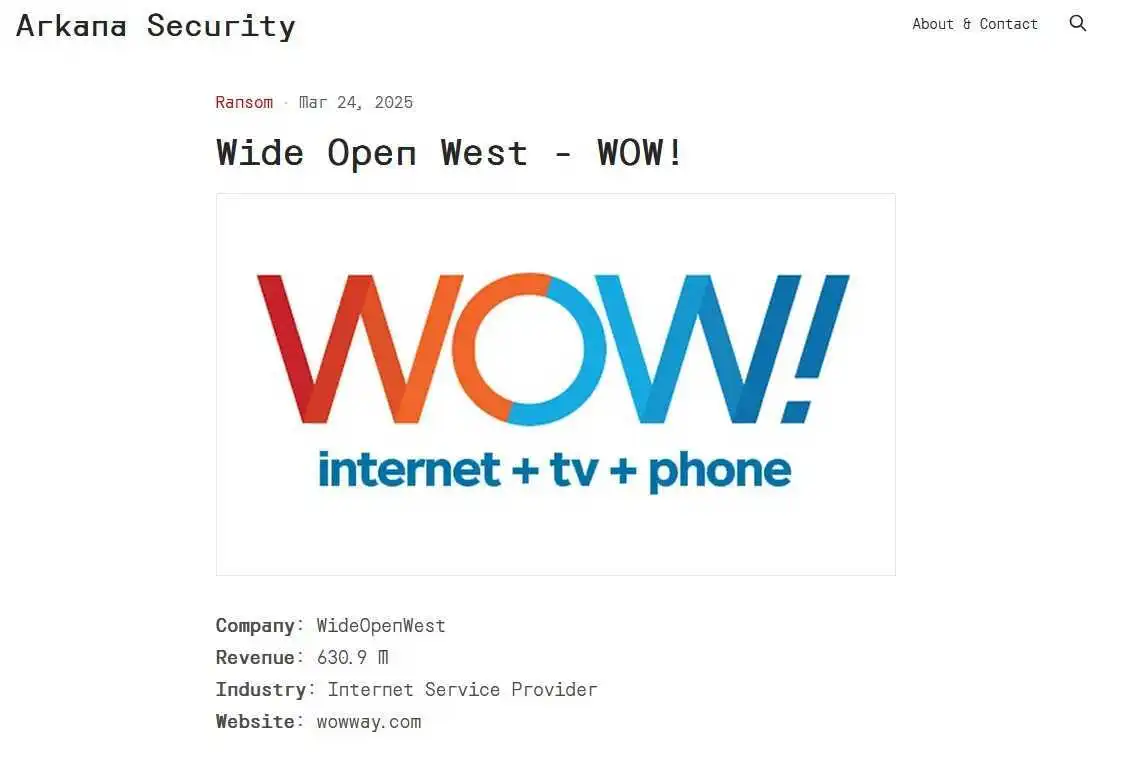
Arkana Security – WOW Victim Page
Arkana also claims in their post that their capabilities also extend to exfiltrating sensitive data, such as Social Security Numbers (SSNs), credit card information, and other Personally Identifiable Information (PII), all without detection. This comprehensive breach indicates a severe threat to both the infrastructure and the privacy of WOW!’s customers.
The following data is breached according to Arkana Security’s post:
User Identification
- userId (Primary Key, int, identity) – Unique identifier for the user
- customerAccountId (int) – Associated customer account ID
- username (nvarchar(100)) – User’s login name
Authentication & Security
- password (nvarchar(255)) – User’s password
- securityQuestionId (int) – ID of security question for account recovery
- securityAnswer (nvarchar(255)) – Answer to security question
- isPasswordExpired (tinyint) – Indicates if the password has expired
- PasswordExpirationDate (datetime) – Date when the password expires
- badLoginAttempts (int) – Number of failed login attempts
- isLockedOut (tinyint) – Indicates if the account is locked
- lockedOutDate (datetime) – Date when the account was locked
Personal Information
- firstName (nvarchar(50)) – User’s first name
- lastName (nvarchar(50)) – User’s last name
Email & Communication Preferences
- communicationEmail (nvarchar(255)) – Email used for communication
- communicationEmailDate (datetime) – Date communication email was set
- isOptIn (tinyint) – Indicates if the user has opted in for communications
- optInDate (datetime) – Date when the user opted in
- emailDomainId (int) – Identifier for the email domain
- isCommunicationEmailVerified (tinyint) – Indicates if communication email is verified
- LoginEmailUpdateDate (datetime) – Date when login email was last updated
- CommunicationEmailUpdateDate (datetime) – Date when communication email was last updated
Account Status & Activity
- isActive (tinyint) – Indicates if the account is active
- isSevenMonthInactive (tinyint) – Indicates if the account has been inactive for seven months
- createdDate (datetime) – Account creation date
- lastLoginDate (datetime) – Last successful login date
- deactivatedDate (datetime) – Date when the account was deactivated
- deactivationNote (nvarchar(2147483647)) – Notes regarding deactivation
Access & Permissions
- isPrimaryUser (tinyint) – Indicates if the user is the primary user
- hasDialUpAccess (tinyint) – Indicates if the user has dial-up access
- RoleId (int) – Role identifier for user permissions
Encryption & Security Services
- isComxEncrypted (tinyint) – Indicates COMX encryption
- isSynacorEncrypted (tinyint) – Indicates Synacor encryption
- synacorStatusId (int) – Status ID for Synacor
- isHostopiaUser (tinyint) – Indicates if the user is a Hostopia user
Firebase Integration
- firebaseUsername (nvarchar(355)) – Firebase username
- firebaseUID (nvarchar(150)) – Firebase User ID
- firebaseMigration (tinyint) – Indicates if the account has been migrated to Firebase
- isFirebaseUsernameVerified (tinyint) – Indicates if the Firebase username is verified
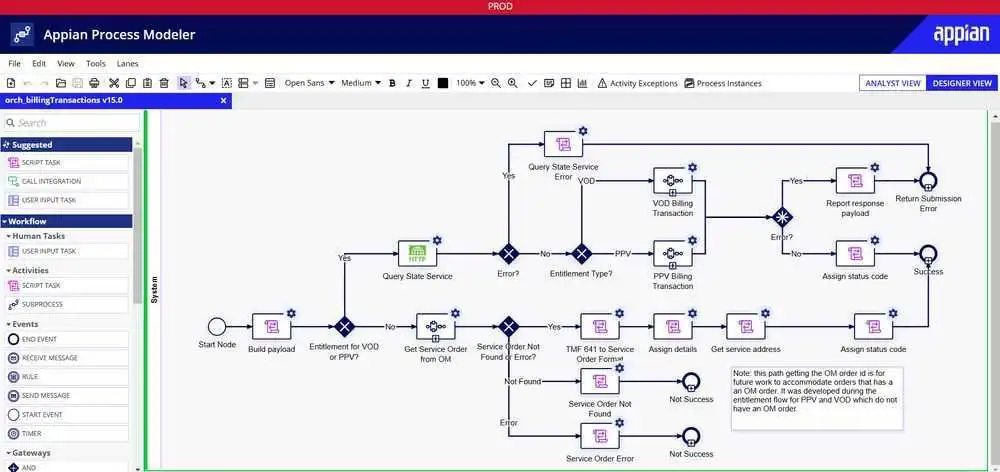
Appian Dashboard Published by Arkana Security
In addition to the technical allegations, Arkana is also engaged in doxxing activities involving WOW!’s CEO and other senior executives. The threat actor published sensitive personal information, including addresses, contact details, and the social security number of the company’s CEO, while simultaneously ridiculing them. Furthermore, the names of several directors, key individuals responsible for investor relations and media relations, as well as the Chairman of the Board, were also disclosed in the post. While the personal information of these individuals was not explicitly included, given the nature of the alleged breach, it is possible that their private details may also be at risk.
For WOW!, this alleged breach can translate into significant reputational damage and potential legal and regulatory repercussions. The exposure of sensitive customer data not only undermines trust but also forces the company to invest heavily in remediation and enhanced cybersecurity measures to prevent future incidents.
For customers, this incident means an elevated risk of identity theft, financial fraud, and malware infections. With access to personal details such as Social Security numbers, credit card information, and more, affected individuals may need to monitor their financial accounts closely and consider additional protective measures like credit monitoring or identity theft protection.
Overall, both parties face a challenging road ahead as they navigate the consequences of this sophisticated cyber attack.


































