
How to Detect & Prevent Ransomware Attacks (2024 CISO Edition)
Why is Ransomware One of the First Items on the CISOs Agenda?
Rise with Pandemic
With the pandemic, as we rush towards an increasingly digitized world, ransomware has become our institutions’ most prevalent cyber threat.
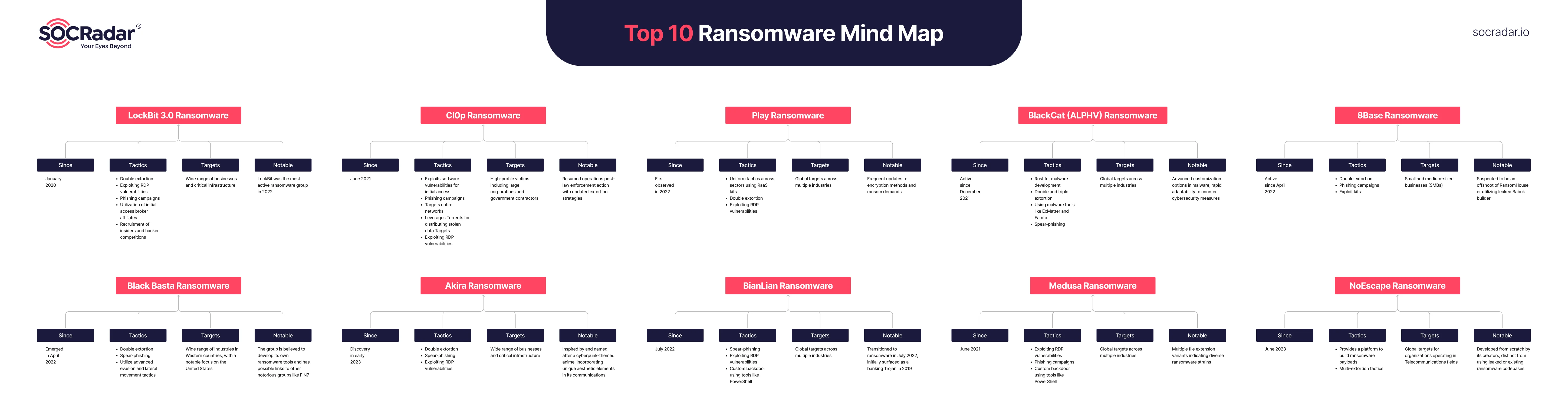
Top 10 Ransomware Mind Map
In May 2021, a notorious ransomware attack disrupted the fuel supply chain Colonial Pipeline operations in 17 states in the USA. The outage lasted five days, and they had no choice but to pay approximately US$4.4 million ransom. JBS, the world’s largest meat processor, was targeted within the same period and had to pay US$11 million.
IBM Cost of a Data Breach Report 2022 states that the average cost of a ransomware attack is $4.54 million, excluding the cost of ransom itself. It is a combined cost that includes many aspects – downtime costs, reputation damage, new security practices, etc.- that play into k. On the other hand, Check Point researchers reported that the total cost of a ransomware attack includes costs nearly seven times higher than the ransom demanded by threat actors.
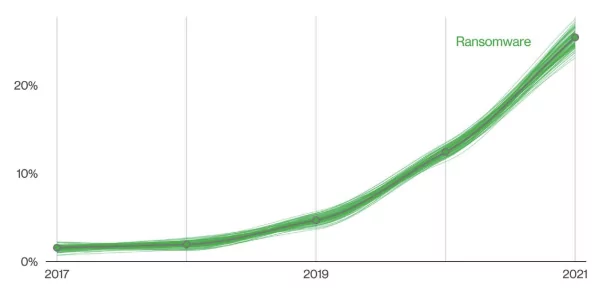
Ransomware will cost its victims around US$265 billion annually by 2031, with a new attack every 2 seconds (Figure 1). Ransomware is the fastest growing type of cybercrime, as stated by Cybersecurity Ventures.

According to Verizon 2022 Data Breach Investigation Report (DBIR), ransomware attacks increased by 13%, a jump greater than the past 5 years combined (Figure 2).
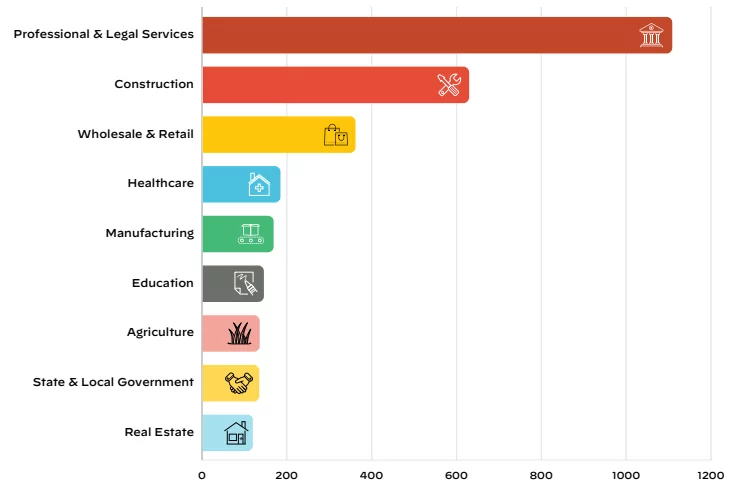
Recently, it has affected a broad spectrum of industries like transportation, telecommunication, financial institutions, healthcare, education, public law enforcement, legal, manufacturing, food industry, etc. (Figure 3). Furthermore, it can impact every company, from large enterprises to SMEs, without distinguishing company size. In short, it does not discriminate against any target.
It is A Business
Ransomware is at the top of the list of CISOs‘ agendas because it has become an important part of the criminal business model.
Ten years ago, it was the goal of only a few digital criminals, but nowadays, as it has become an industry, the volume of attacks has increased dramatically.
It has now evolved into a professional business run by criminal organizations that have built their cybercrime ecosystem.
These criminals not only create ransomware but also provide support services where victims can contact to learn how to pay the ransom.
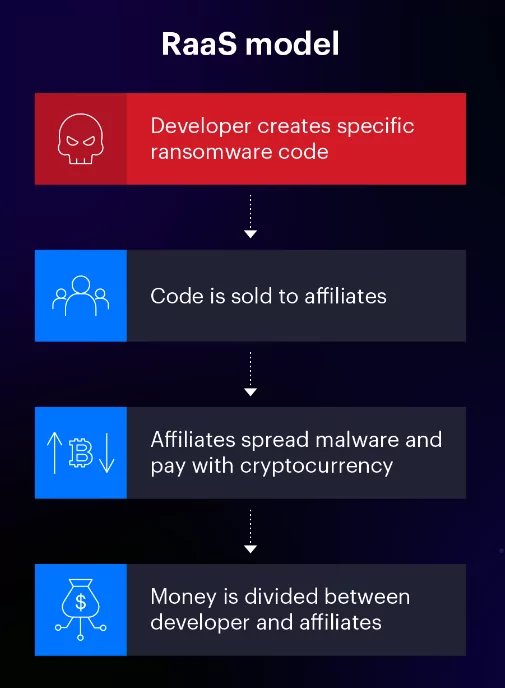
On the other hand, with the ransomware–as–a–service (RaaS) model, malware creators make malicious software available to customers called affiliates. Affiliates with little technical knowledge can spread the malicious software, and finally, paid ransom is divided between ransomware operators and affiliates. This model creates an environment where even someone without technical knowledge can make these attacks (Figure 4).
Multiple Extortions Hurt
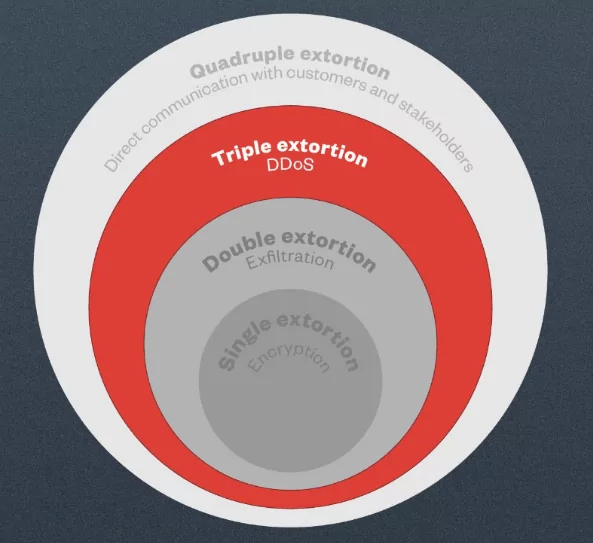
Another disturbing reason for considering ransomware a top threat is; that ransomware threat actors utilize multiple extortion schemes after seizing files and resources of organizations (Figure 5).
Nowadays, ransomware operators commonly utilize as many as four methods, also known as quadruple extortion, for pressuring victims into paying:
- In the first stage, they encrypt all the files, and victims have to pay to regain access to the unencrypted, original data,
- Then, they steal some or all of the data and threaten to disclose or sell it if there is no payment for the ransom,
- If these two methods don’t work, they threaten with the Denial-of-Service (DoS) attacks to stop the public services of the victim,
- And lastly, they contact clients, partners, employees of victims, and the media to harass and tell them about the breach.
Moreover, when the ransomware is triggered, the organization encounters an availability loss as it can no longer access its data. And systems can go offline for days or weeks, which has a devastating impact on a business.
With the above extortion techniques and consequences, it is not difficult to estimate that ransomware can cause substantial financial loss and reputational damage to the organization. And they also make organizations more willing to pay.
How Does Ransomware Spread?
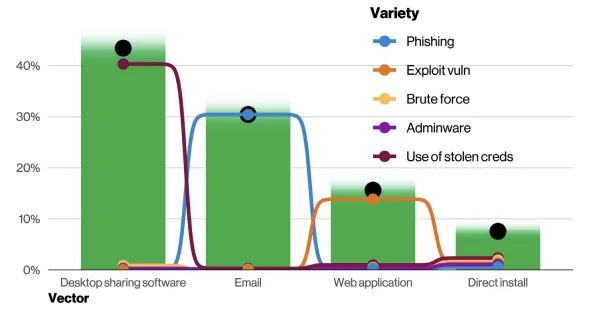
Ransomware infects systems via following the three most common attack vectors; misconfigured desktop sharing software or built-in remote desktop services (RDP), phishing emails, and vulnerable web application. Different tools are used by threat actors for each vector, as depicted in Figure 6.
1. Stolen RDP credentials
RDP services have been an infamous attack vector for years, especially for use where phishing emails may not be as profitable. However, the pandemic and the popularity of work-from-home shifts have made RDP attacks even more prevalent.
Threat actors use desktop sharing software like RDP in 40% of ransomware incidents. And within this attack vector, they most predominantly utilize stolen credentials.
Stolen RDP credentials can be found on black markets on the dark web for a few bucks. It is the first and easy option for initial network access and does not require user interaction or a huge effort by threat actors.
After threat actors gain access to those credentials, they can bypass endpoint protection measures and disrupt systems.
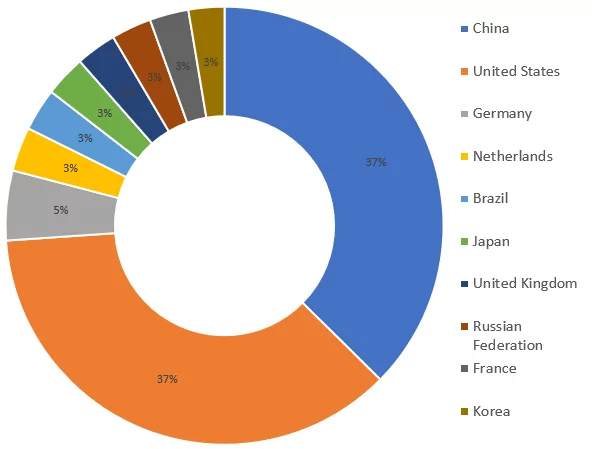
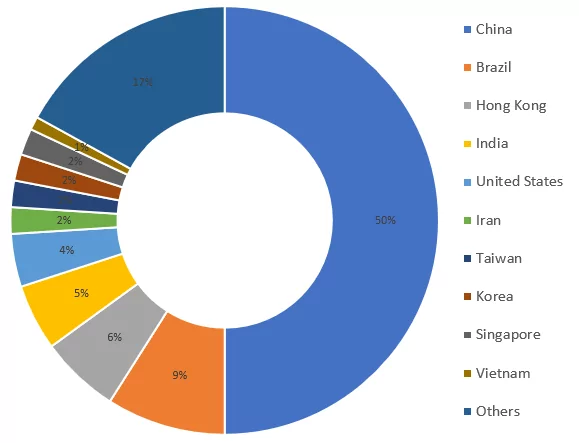
Per country, the percentage of RDP ports and stolen credentials are shown in Figure 7 and Figure 8.
The list includes the United States, United Kingdom, Germany, Netherlands, Brazil, India, Japan, Korea, Singapore, Taiwan, and Vietnam, apart from China and the Russian Federation.
It shows us that both developed and emerging economies are affected by this threat.
2. Phishing Emails
Phishing is another most common ransomware attack vector at 35%, whether used via links, attachments, or both.
As part of social engineering schemes, phishing allows the threat actor to perform their actions without being detected.
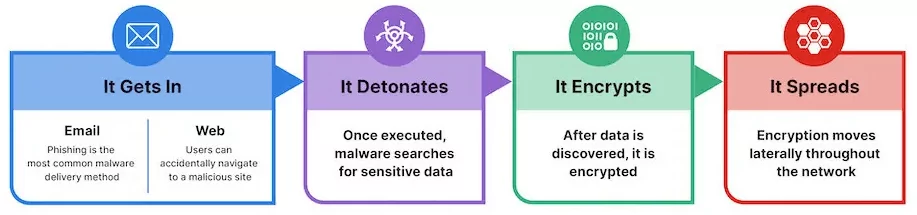
Once the recipient opens the attachment or clicks the URLs, the ransomware is downloaded, leading to the system becoming infected and providing access to threat actors. After the initial foothold, ransomware can spread to the whole network, encrypt and exfiltrate data for ransom.
Figure 9 shows us how ransomware spreads through phishing emails.
3. Exploitable Vulnerabilities
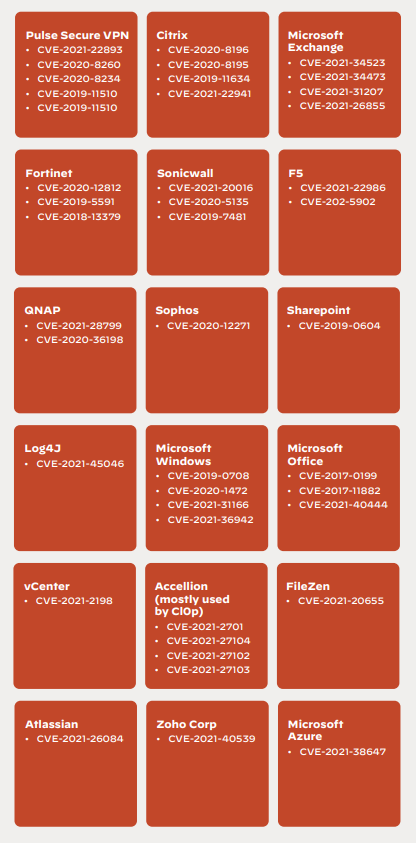
The third attack vector of this devastating threat is vulnerabilities in internet-facing applications. 20% of ransomware incidents occur because of exploitable vulnerabilities. If they aren’t effectively and timely patched, ransomware finds its way into the systems.
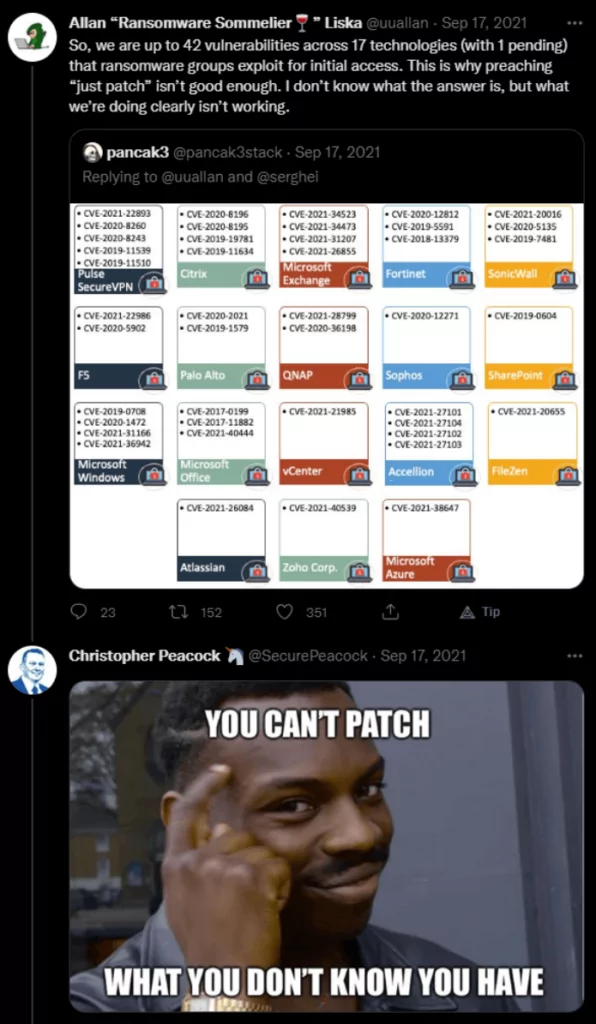
Ransomware attacks leverage various vulnerabilities as an initial vector of compromise. In 2021, Unit 42 observed at least 42 vulnerabilities across different technologies used by ransomware operators (Figure 10).
How to Detect and Prevent Ransomware with SOCRadar?
The question we have to answer is how do we prevent this threat or how can we detect it when we are under attack?
As an answer to these questions, SOCRadar has many remarkable features to cope with ransomware attacks, as shown below.
Credentials & Data Leak Detection
SOCRadar Digital Risk Protection suite scans deep, dark, and surface web for any stolen credentials and sensitive data leaks.
When it reveals company assets or related keywords in dark web forums, chat channels, black markets on the dark web, and even in public code repositories, it immediately notifies you or your teams.
For instance, it can discover stolen credentials belonging to your company assets/employees and notify you in real-time. The SOCRadar Dark Web Team helps you obtain this data when necessary. You can detect the related employee account and take preventive actions before threat actors use it for malicious intent.
Figure 11 shows a sample alarm with the Blackmarket Botnet Detection title, in which a VPN credential is discovered in DarkWeb.
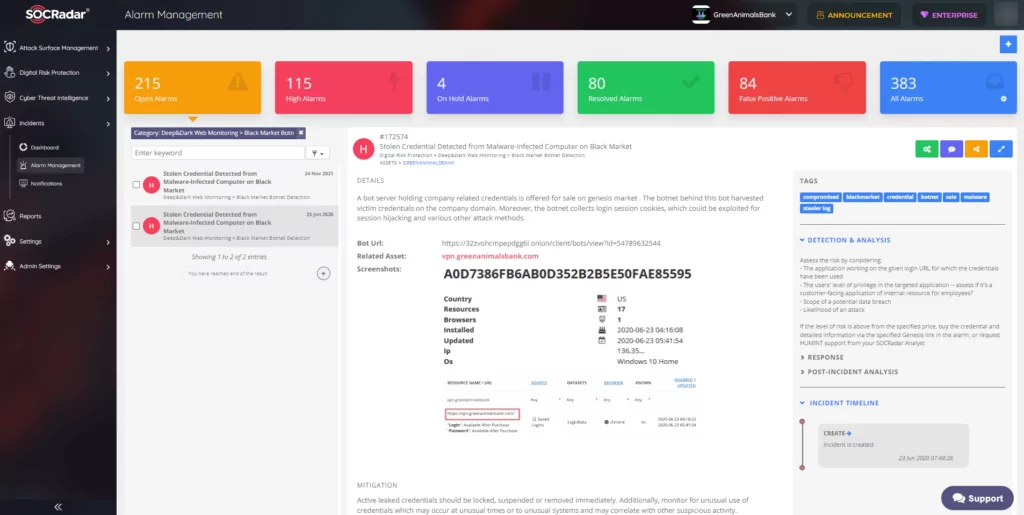
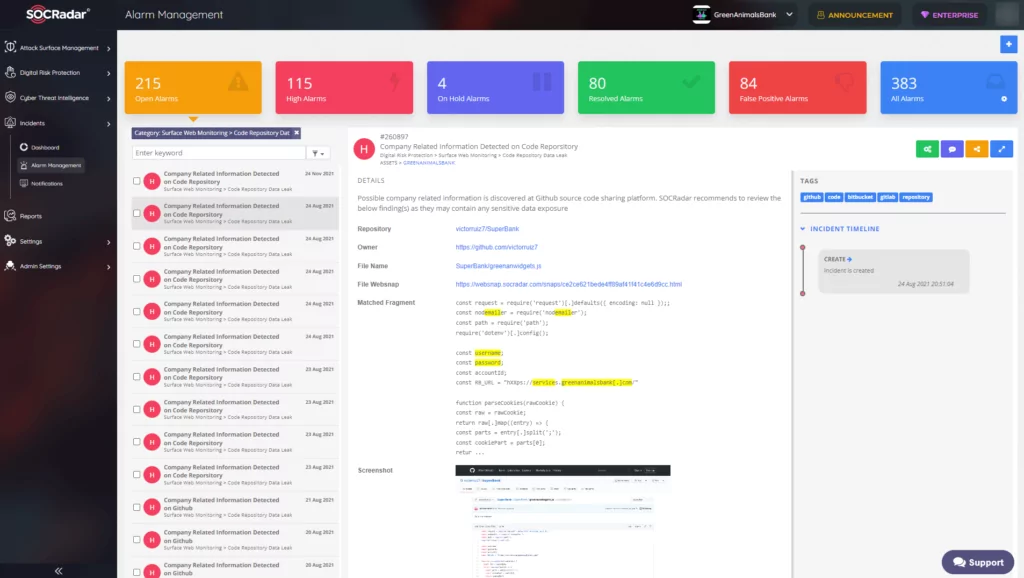
Figure 12 shows a sample alarm with Code Repository Data Leak Detection title, in which a sensitive credential is discovered.
Asset Discovery
SOCRadar Attack Surface Management suite discovers and monitors your Internet-facing assets.
With SOCRadar, you can;
- Aware of your digital assets accessible from the Internet not only by your friendly visitors but also the threat actors,
- Monitor your enterprise’s critical open ports via scheduled active scans,
- Monitor your enterprise’s critical vulnerabilities and emerge zero days via scheduled active vulnerability scans,
With this capability in your toolset, you can prevent ransomware attacks via timely, accurate, and fit-for-purpose critical port and vulnerability detection alerts.
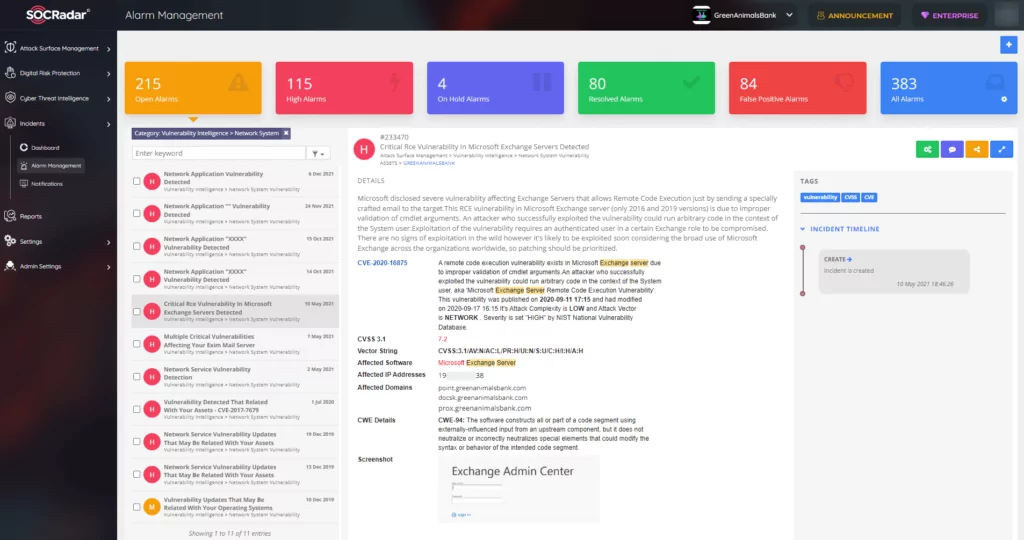
For instance, once a critical RCE vulnerability emerges, SOCRadar maps your assets with the affected software of the vulnerability and notifies you immediately.
Figure 13 shows a sample alarm with a Critical Open Port Detection title, in which RDP ports are discovered.
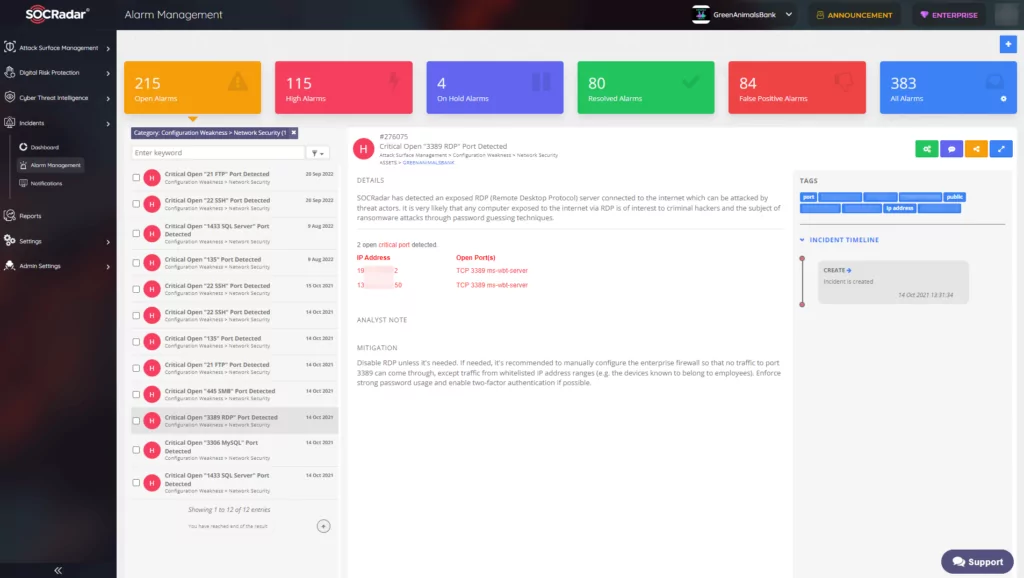
Figure 14 shows a sample alarm with a Critical Vulnerability Detection title, in which an RCE Vulnerability is discovered.
If your digital asset management is not up to date you can’t patch any system with vulnerabilities that you don’t aware of stated as below in a screenshot. (Figure 15).
Threat Intelligence
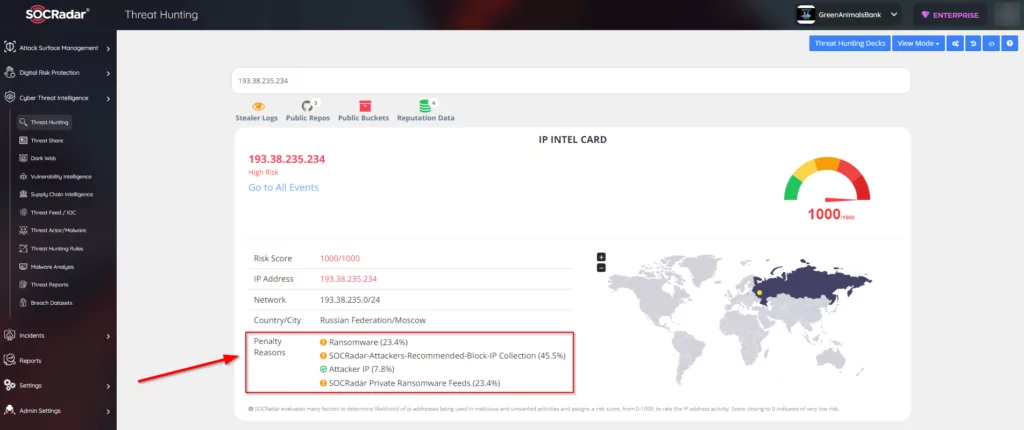
SOCRadar Cyber Threat Intelligence suite has different capabilities and features to help you to detect and prevent ransomware attacks. The Threat Hunting page allows you to search Indicators of Compromise (IoCs) and get attribution data from 2.5 billion records (Figure 16). Besides manual searching during incident response, you can also integrate the Threat Hunting data with your Security orchestration, automation, and response (SOAR) solution with a Restful API easily.
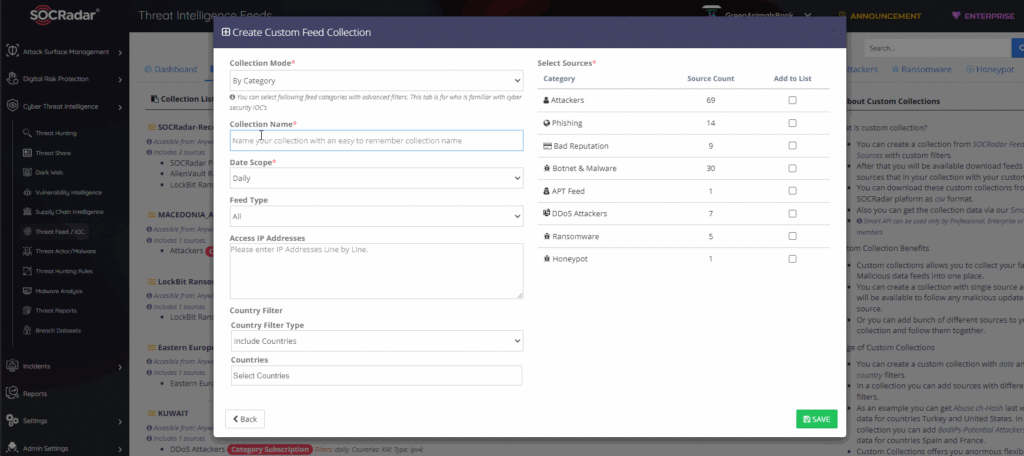
The Threat Feed page lets you create tailored custom IoC collections, especially for ransomware (Figure 17). Therefore you can integrate those newly created custom feeds to your Security Information and Event Management (SIEM), Firewall (FW), Endpoint Detection and Response (EDR), or any security technologies that support monitoring, detecting, and preventing the traffic from these malicious sources.
SOCRadar has an extensive phishing detection capability and adds these newly detected phishing URLs to its private IoC collections.
As a customer, you can easily integrate those collections into your security products like SIEM, FW, and EDR solutions and prevent ransomware attacks from newly detected malicious URLs.
As SOCRadar, we consistently improve and enhance our platform to fit your needs to protect your enterprise against digital criminals and their new tactics, techniques, and procedures. Feel free to explore our platform and take advantage of it for free just in minutes! Do not hesitate to provide your feedback and opinions or get in touch with us.



































