
Top Linux Bash Commands that SOC Analysts Should Know
Within the domain of Cyber Threat Intelligence (CTI), where various tools and processes are deployed for vigilant defense, Bash commands are one such solution. In the pursuit of swift and precise actions, cybersecurity defenders turn to these commands to execute a spectrum of activities, spanning data analysis, system monitoring, and investigative tasks.
The use of Bash commands in CTI enables defenders to easily navigate the complex narrative of digital threats, assisting them in dissecting the specifics.

Illustration of a person using bash commands, Bing Image Creator
This article discusses the importance of Bash commands in the context of Cyber Threat Intelligence, shedding light on their usage, relevance, and the key commands that improve the efficiency of threat intelligence operations.
What Are Bash Commands?
Bash, an acronym for “Bourne Again Shell,” is a command processor built into Unix and Linux operating systems. It is an improved version of the Bourne shell (sh) supplied with Linux and GNU operating systems, with enhanced features. It operates in the Command-Line Interface (CLI) where users input commands to trigger specific actions.
Bash commands are the heart of Linux-based systems, providing users with a powerful environment for navigating file systems, executing commands, and performing a variety of operations, allowing tasks to be completed easily.
Of even greater significance regarding the topic of our article, Bash commands are essential tools for defenders in the world of cybersecurity.
What Are Some of the Bash Commands Useful in CTI?
In CTI, Bash commands are fundamental items, providing analysts, system administrators, developers, researchers, and unfortunately hackers too, with an easy means of improving operational efficiency.
Their contribution to CTI practices includes, but is not limited to, facilitating quick and precise malware analysis, enabling efficient log analysis, ensuring file integrity with hash computation, and investigating network traffic and anomalies, contributing to comprehensive endpoint forensics.
By considering the various applications of Bash commands mentioned, you can grasp their utility and the challenges they can effectively address within the CTI domain.
The following are some of the top Bash commands that prove useful in specific practices and are useful in CTI:
Text Search and Manipulation
- grep: Used to search for patterns within files. It is inva
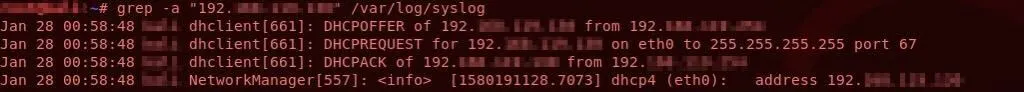
Example usage and output for ‘grep’
- ngrep: A grep command specifically designed for network packet analysis. It allows you to filter and display network packets based on specific criteria like protocol, source, destination, or pattern matching within packet payloads.
- sed: Stands for “stream editor.” It’s a powerful command-line utility for text manipulation and transformation. It’s often used for search and replace operations, text substitutions, and stream editing tasks.
- awk: A versatile text processing tool for pattern scanning and processing. It is capable of handling complex data manipulation tasks, including field extraction, pattern matching, and data formatting.
- tr: Stands for “translate.” It’s used for translating or deleting characters in text streams. It is commonly used for tasks like converting uppercase characters to lowercase, removing special characters, or performing character substitutions.
- strings: Extracts printable strings from binary files, helping to identify human-readable content within them. It can be used to analyze text in malicious software; for example, to search for a ransom note within a binary.
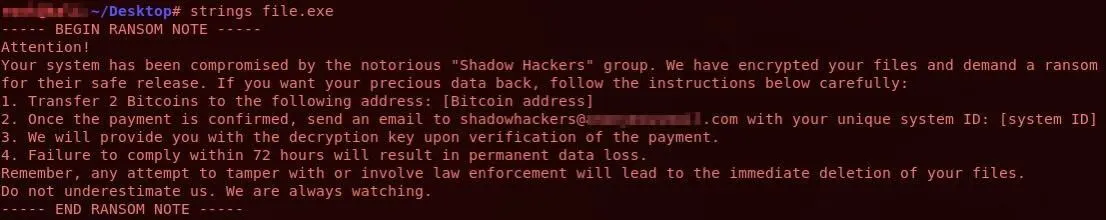
Example usage and output for ‘strings’
The output shows that the ‘strings’ command extracts human-readable strings from a binary file. It displays the printable strings contained in the file, which may include text messages, error messages, prompts, and other readable content.
By analyzing the strings extracted from a binary file, you can learn about its contents and identify any suspicious behavior. For example, you could look for specific keywords or phrases, like ‘ransom’ or other signs of malicious activity.
- hexdump: Displays file contents in hexadecimal, providing a detailed view of the binary data.
Process Analysis
- ps: Provides information about currently running processes. It can also be used to identify all processes owned by a specific user.
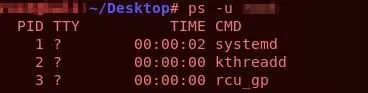
Example usage and output for ‘ps’
- pgrep: Searches for processes based on their name or other attributes.
- lsof: Lists open files and the processes that opened them, providing insights into system activity and resource usage.
Network Analysis
- netstat: Displays network connections, routing tables, interface statistics, masquerade connections, and multicast memberships.
- tcpdump: A packet analyzer that allows the user to display TCP/IP and other packets being transmitted or received over a network to which the computer is attached. If you want to capture and analyze network packets related to a specific IP address, you can use the command as follows:
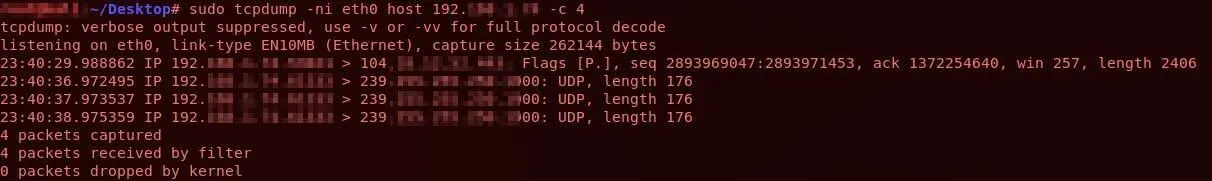
Example usage and output for ‘tcpdump’

Bash commands can facilitate text search and manipulation, process analysis, and network analysis.
File and Data Processing
- cut: Enables the extraction of specific fields or columns from text files with delimiter-separated values. It is useful for processing structured data such as CSV files or log files with fixed fields.
- sort: Arranges lines of text files alphabetically or numerically, making it easier to read and analyze data. It is commonly used in combination with other commands to organize data before further processing.
- uniq: Filters adjacent duplicate lines from a sorted text file or input stream. It’s useful for identifying unique entries or removing duplicate records from datasets.
- diff: Compares the contents of two text files line by line and highlights the differences between them. It is commonly used to track changes between different versions of files or directories.
- comm: Compares two sorted files line by line and displays lines unique to each file as well as lines common to both files. It is often used in conjunction with sort and uniq for data analysis tasks.
- csvcut: Specifically designed for working with CSV (comma-separated values) files. It allows you to select and extract specific columns from CSV files based on their position or header names.
- jq: A lightweight and flexible command-line JSON processor. It is used for parsing and manipulating JSON data, allowing you to extract, filter, and transform JSON documents efficiently.
- md5sum/sha256sum: Computes and verifies MD5 and SHA256 checksums of files, allowing users to verify file integrity.
Example usage and output for ‘md5sum’
- file: Determines the file type of a file or files.
- stat: Displays detailed information about a file or file system, including access permissions, file type, and timestamps.

Bash commands can enable efficient processing by manipulation of file and data structures in various formats.
File Viewing and Navigation
- head/tail: These commands are used to display the first (head) or last (tail) few lines of a file or input stream. They are useful for quickly previewing the contents of large files or extracting specific portions of data.
- less: A pager program used to view the contents of text files one page at a time. It allows for scrolling, searching, and navigation within files, making it faster and easier to access the file content (for large files). The ‘more’ command in Bash is also used for the same purpose, but ‘less’ provides more advanced features like backward scrolling and searching within the file.
- ccze: A log colorizer tool used to highlight and colorize log files for easier readability. It is especially useful when dealing with large log files containing various types of information and messages.
- ls: Lists directory contents, providing information about the files and directories within the specified directory.
Commands such as head/tail, less, ccze, and ls are useful for file viewing and navigation.
Usage of Bash Commands in CTI
To gain a comprehensive understanding of the contribution of Bash commands to CTI practices, let’s explore which commands offer what kind of benefits in various scenarios:
Log Analysis
Understanding how a network was breached and deciphering the attacker’s actions are crucial aspects of addressing a security incident. Log data serves as a valuable resource for gaining insights into these areas. Analyzing system and device logs within the organization assists defenders in comprehending the sequence of events leading to the incident.
Log data encompasses details on system and network activity, user actions, security events, and other pertinent information. While many modern tools offer centralized log analysis capabilities, manual analysis using traditional Linux tools is sometimes necessary.
By utilizing Bash commands like grep, awk, and sed, defenders can scrutinize various log types to detect suspicious activities, track the source of security incidents, and uncover potential weak points.
Let’s explore the types of threats identifiable using Bash commands across different logs:
- Web Server Logs: Defenders can review web server logs to identify unusual patterns of access, such as a high number of HTTP 404 errors or multiple failed login attempts. This could indicate potential attempts to exploit vulnerabilities or brute force credentials.
- Firewall Logs: Analyzing firewall logs helps in understanding incoming and outgoing network traffic. A defender might look for unexpected outbound connections or repeated attempts to access restricted resources, which could signify unauthorized access attempts or malware communication.
- Authentication Logs: Authentication logs contain information about user logins and authentication attempts. An analyst can detect suspicious activities by monitoring for multiple failed login attempts from the same user account or unusual login times outside regular business hours.
- DNS Logs: DNS logs provide insights into domain name resolutions. A defender may investigate DNS logs for unusual domain name resolutions, such as domains associated with known malware or command and control servers.
- Email Server Logs: Email server logs record email transactions and delivery attempts. Analyzing email server logs can help detect phishing attempts, suspicious attachments, or unusual email forwarding rules that may indicate a compromised account.
- Syslog Events: Syslog events capture system messages and events from various devices and applications. An analyst might monitor syslog events for alerts related to system crashes, resource utilization, or unauthorized access attempts.
- Database Logs: Database logs track database activities, including queries, logins, and data modifications. Analyzing database logs can reveal unauthorized database access attempts, SQL injection attacks, or unusual database activities indicative of data exfiltration attempts.
- Endpoint Logs: Endpoint logs provide visibility into activities occurring on individual endpoints. An analyst may review endpoint logs for signs of malware infections, unusual file modifications, or attempts to escalate privileges.
- VPN Logs: VPN logs record user connections and activities over virtual private networks. Monitoring VPN logs can help detect unauthorized access attempts, abnormal connection patterns, or potential insider threats.
- Cloud Service Logs: Cloud service logs contain information about activities and events within cloud environments. Analyzing cloud service logs can uncover unauthorized access attempts, configuration changes, or data transfers outside predefined policies.
Analysis of File Hashes:
The generation and comparison of file hashes are fundamental in CTI for verifying file integrity and identifying potentially malicious files. Bash commands like md5sum and sha256sum enable analysts to compute and compare hashes, aiding in the rapid identification of suspicious files.
These applications underscore the versatility of Bash commands in CTI, offering analysts a robust toolkit to gather, process, and analyze threat intelligence data efficiently.
Network Analysis:
Bash commands play a pivotal role in network analysis, allowing defenders to investigate network traffic, identify anomalies, and pinpoint potential security breaches. Commands like tcpdump and netstat provide insights into network activities, aiding in the identification of suspicious connections or patterns.
Malware Analysis
Malware analysis requires a variety of comprehensive tools and techniques beyond bash commands. Still, certain aspects of malware analysis – such as examining file properties, extracting strings, or analyzing network traffic – can be performed using bash commands. Here are some ways bash commands can contribute to malware analysis:
- File Analysis: Bash commands like file, strings, and hexdump can provide insights into the structure and content of suspicious files. They can reveal file types, extract strings from binaries, and display hexadecimal representations.
- Static Analysis: Bash commands can help perform static analysis by examining file properties, permissions, and attributes. Commands like ls, stat, md5sum, and sha256sum can be used to gather information about files and directories.
- Log Analysis: Malware often leaves traces in system logs. Bash commands like grep, awk, and sed can help search and analyze log files for suspicious activities and Indicators of Compromise (IOCs).
- Network Analysis: Bash commands like netstat, tcpdump, and wireshark (command-line version) can be used to capture and analyze network traffic generated by malware. They can help identify communication channels, protocols used, and potential command and control (C2) servers.
- Process Analysis: Commands like ps, pgrep, and lsof can be used to examine running processes and identify any suspicious or malicious activities.
Enriching your manual analysis with additional context is where SOCRadar shines. When you identify a suspicious file hash or log entry, SOCRadar can:
- Compare it against millions of known malware signatures and threat intelligence databases.
- Provide details about the malware family, attack vectors, and associated threat actors.
- Allow you to search for the details of potential IOCs (Indicators of Compromise) found in analyses.
With SOCRadar’s Malware Analysis module, you can analyze a variety of files, from binary to office files, including EML files, and receive immediate reports.
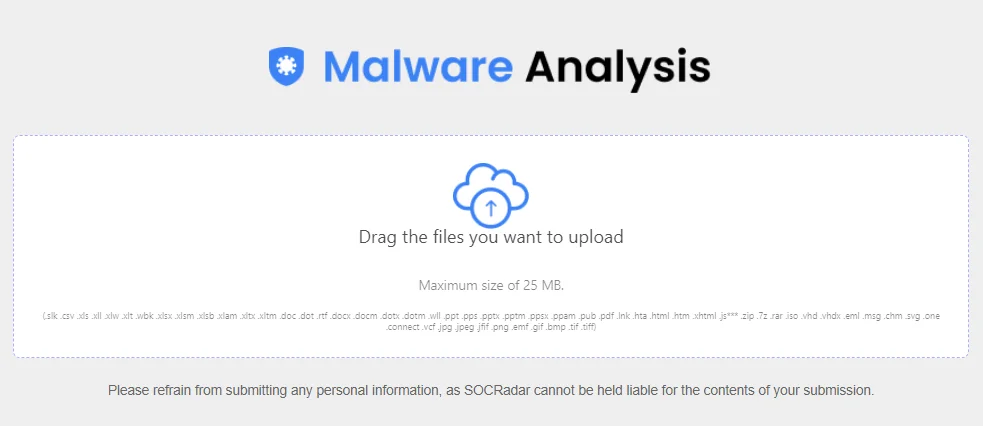
SOCRadar’s Malware Analysis aims to provide users with a thorough understanding of malware samples, allowing for quick detection and analysis.
Additionally, you can keep track of the Tactics, Techniques, and Procedures (TTPs) employed by particular threat actors and obtain insights into past attack campaigns with SOCRadar XTI.
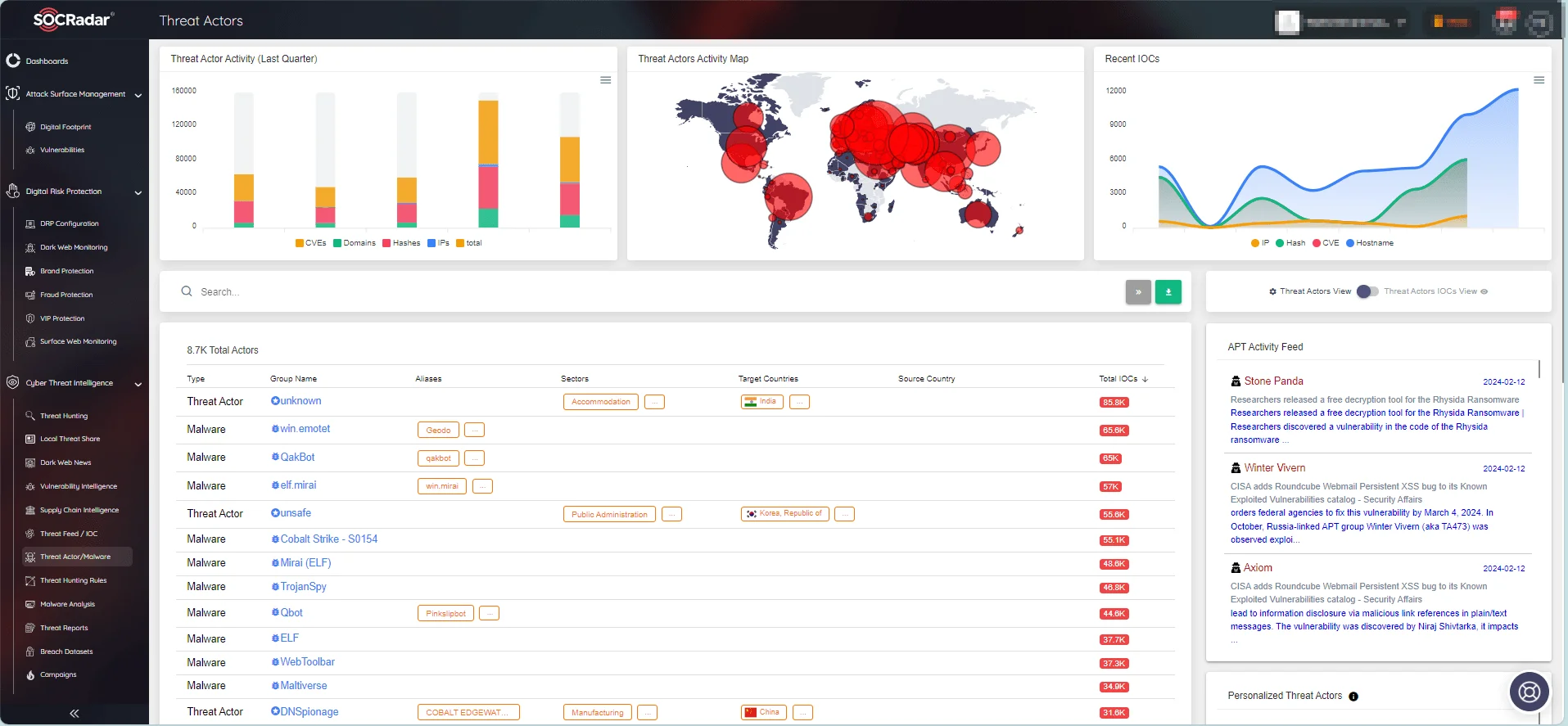
SOCRadar Threat Actors/Malware page.
With the Threat Feed/IOC module, you can search for potential IOCs discovered during manual analysis and find related information to gain better context. You can test the IOC Search feature within the module through SOCRadar Labs’ IOC Radar, which is a complementary service.
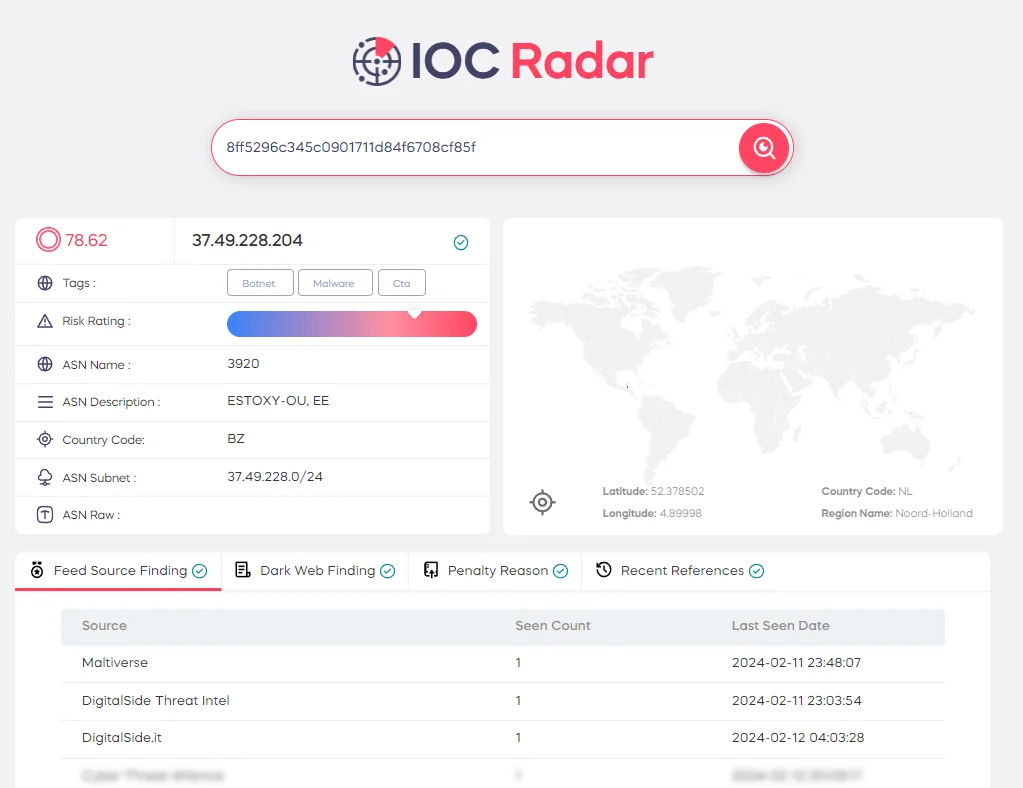
SOCRadar Labs’ IOC Radar
Conclusion
Through adept use of Bash commands, defenders can navigate the intricate web of cyber threats with ease, dissecting the specifics of malicious activities and fortifying defenses against evolving adversaries. These commands empower defenders to identify suspicious activities, trace security incident origins, and gain valuable insights into potential vulnerabilities.
From log analysis to file integrity verification and network traffic investigation, Bash commands offer a versatile toolkit to address multifaceted challenges within the CTI domain.
While manual use of Bash commands remains instrumental in CTI practices, SOCRadar complements these efforts with an automated approach to threat intelligence. SOCRadar provides a comprehensive platform that keeps cybersecurity professionals updated with real-time alerts, enriched threat intelligence, and actionable insights.
By integrating advanced analytics and machine learning algorithms, SOCRadar enhances the efficiency and effectiveness of threat detection and response operations, enabling organizations to stay ahead of emerging threats and proactively mitigate risks.


































