BidenCash Dark Web Market Leaks Nearly One Million Credit Cards
Nearly one million leaked credit cards have been exposed by the dark web market BidenCash in a newly launched campaign. Shared through clearnet file-hosting services, the stolen card data includes numbers, expiration dates, and CVV codes. The dump was promoted on a Russian-speaking hacker forum to emphasize the freshness and exclusivity of the compromised records.
What is BidenCash?
BidenCash is a well-known dark web marketplace that emerged in 2022, quickly gaining traction for its aggressive promotion tactics and its focus on the sale of stolen financial data. It has built a reputation around releasing massive datasets as marketing tools, often leaking credit card records, personal information, and access credentials to attract buyers and boost visibility.
The platform is equipped with automated buying tools, a loyalty system, and a so-called buyer protection program that claims to ensure the freshness of its listings. It operates on both clearnet and Tor.
What Happened in the Latest Data Dump?
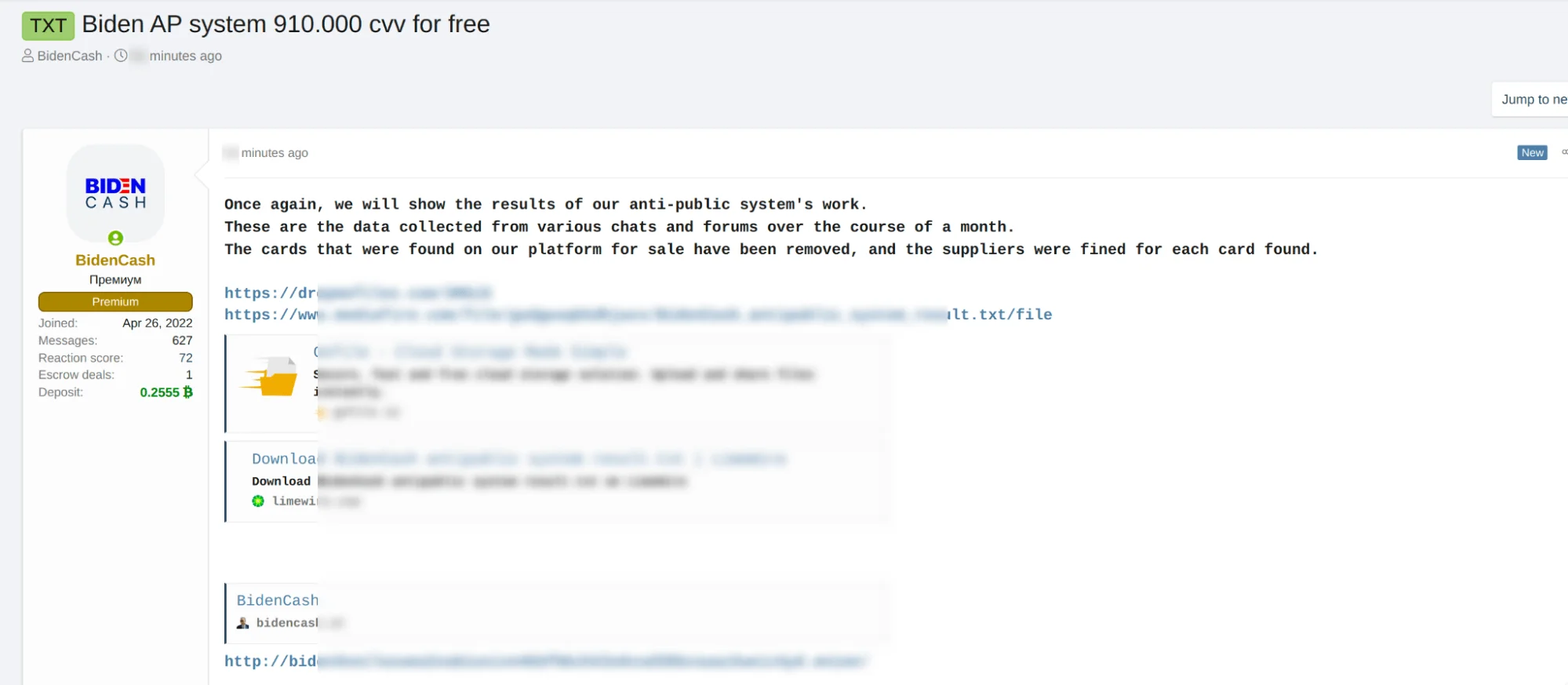
On April 15, 2025, BidenCash published a new dataset containing over 910,000 credit card records, shared openly through several clearnet file-hosting services. The leaked information includes card numbers, expiration dates, and CVV codes, making the data highly actionable for cybercriminals.
The announcement was made on XSS, a well-known Russian-language hacker forum where BidenCash frequently promotes its high-profile campaigns. The release was framed as part of the platform’s Anti-Public System—a process designed to verify that all leaked data is exclusive and not already circulating on public channels. According to the operators, the card data had been harvested from chats and forums over the past month, and any duplicates already listed on the market were removed. Vendors responsible for redundant records were reportedly penalized.
Beyond showcasing its filtering mechanism, the campaign likely serves multiple strategic purposes for BidenCash:
- The BidenCash team aims to drive traffic to the marketplace, especially following service disruptions such as DDoS attacks or domain takedowns.
- The operators seek to reinforce buyer trust by demonstrating a commitment to delivering only “fresh” and exclusive stolen data.
- The campaign is also intended to strengthen BidenCash’s reputation within the cybercriminal ecosystem as a consistent and high-volume source of valuable credit card information.
Through campaigns like this, BidenCash positions itself not just as a vendor but as a brand—one that thrives on visibility, credibility, and aggressive growth within the dark web ecosystem.
What is the Anti-Public System?
BidenCash’s Anti-Public System is a mechanism the platform claims to use for verifying the exclusivity of data sold on its marketplace. According to the marketplace, the system scans known leaks and public sources to filter out recycled or widely shared information. Any data flagged as already public is allegedly removed from listings, and vendors responsible for these duplicates are fined.
By operating part of the system on Telegram, BidenCash reinforces the visibility and perceived credibility of the Anti-Public System—positioning it as an ongoing, externally accessible process rather than an internal or unverifiable claim.
Exposed Cards Had Been Detected by SOCRadar Before Public Release
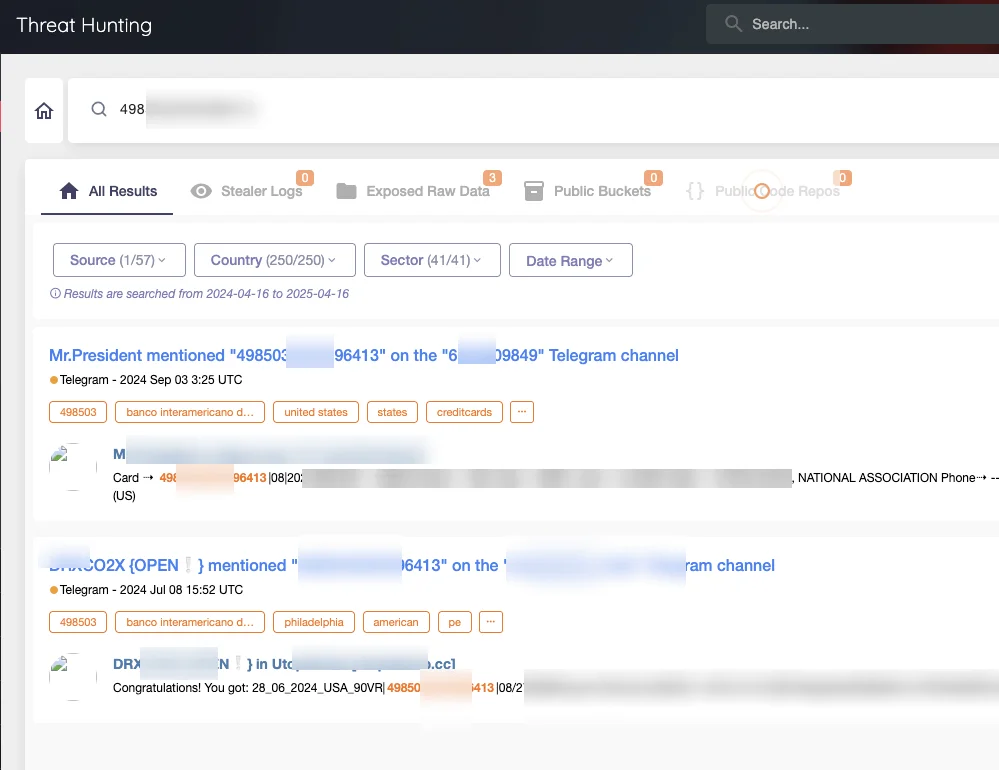
SOCRadar Dark Web Team verified the leaked files and found that many of the exposed card records had already been detected and flagged through SOCRadar’s Threat Hunting module.
This confirmation not only validates the effectiveness of proactive dark web monitoring, but also shows that organizations leveraging SOCRadar were already in a position to mitigate the threat before the public dump occurred.
By continuously scanning dark web sources, SOCRadar enables early warning and actionable insight—helping enterprises identify exposed data, respond rapidly, and reduce potential financial damage.
Conclusion: A Growing Need for Proactive Credit Card Security
The BidenCash leak once again highlights how dark web markets continue to industrialize the sale and distribution of stolen financial data. By leaking nearly one million credit cards, the platform reinforces a dangerous trend—where cybercriminals not only trade, but publicly advertise sensitive information to gain reputation and market share.
For organizations, this means that credit card monitoring, real-time visibility, and dark web intelligence are no longer optional—they are essential components of a modern security strategy.
Recommended Cybersecurity Measures:
- Continuously monitor the dark web for leaked customer or payment data.
- Implement fraud detection systems capable of identifying abnormal transactions tied to exposed cards.
- Maintain an up-to-date inventory of internet-facing digital assets to reduce external attack surface.
- Enforce compliance and risk management for Personally Identifiable Information (PII) exposure.
How SOCRadar Can Help
SOCRadar provides comprehensive protection across the entire exposure lifecycle—from early detection to actionable remediation.
- Its dark web scanning technology actively monitors marketplaces, Telegram channels, and hacker forums to identify stolen credit card data before it spreads.
- The platform’s credit card monitoring feature enables rapid detection of compromised records, helping organizations reduce financial losses.
- Through PII protection and 360-degree visibility, SOCRadar supports regulatory compliance while mapping digital assets vulnerable to exploitation.
- Most importantly, SOCRadar combines automated intelligence with the insights of dedicated analysts to ensure threats are not just seen—but understood and acted upon.
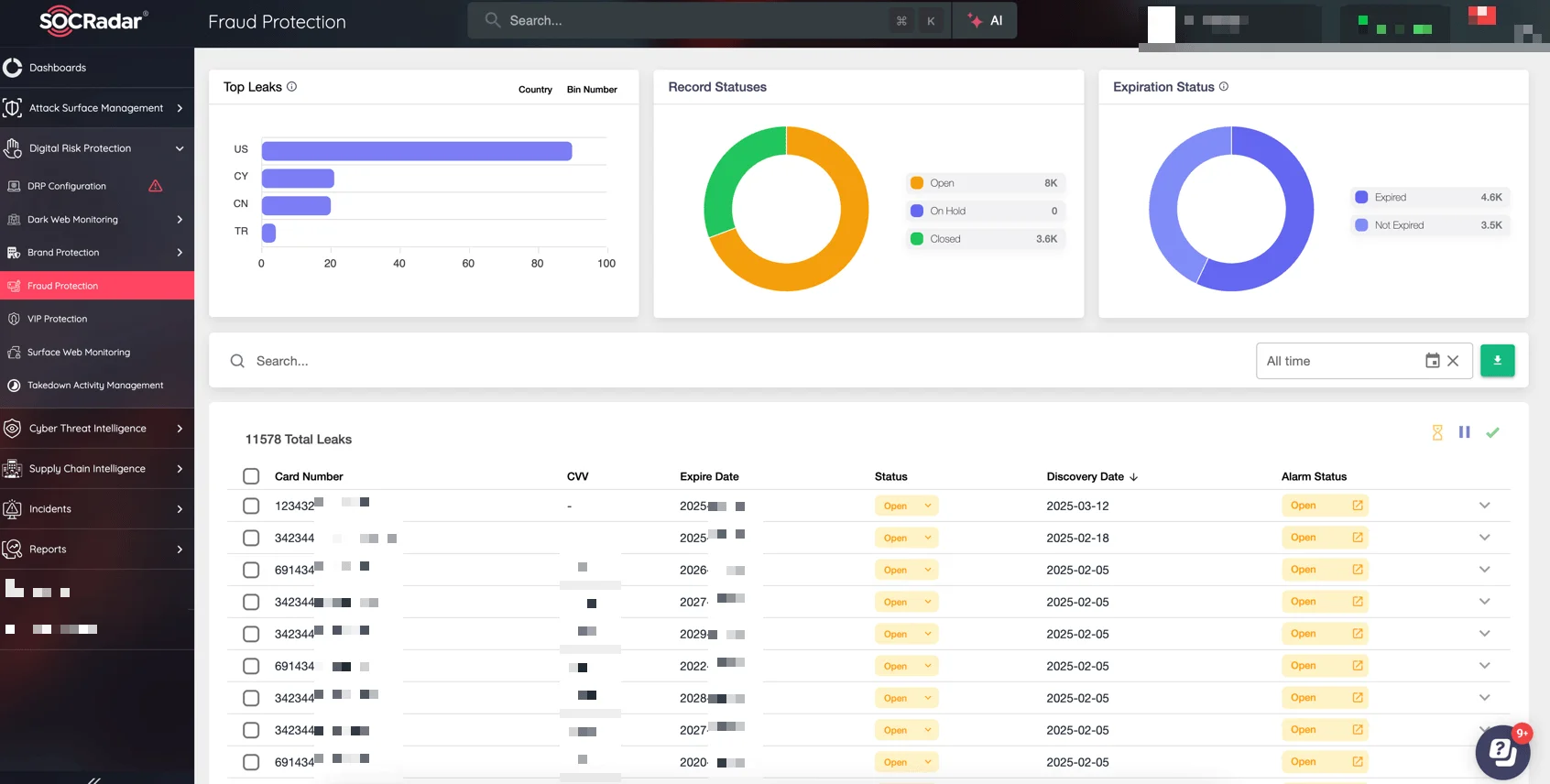
SOCRadar Fraud Protection
In incidents like the BidenCash leak, early detection means early defense—and SOCRadar helps organizations stay one step ahead of cybercriminal operations.