
Change of Tactic in DDoS: Attackers Now Use VPS for Improved Botnet Attacks
Cloudflare, a prominent internet security company, recently published a report on hyper-volumetric DDoS attacks changing tactics in the first quarter of 2023. Botnets are now exploiting compromised Virtual Private Servers (VPS) rather than IoT devices.
This new generation of DDoS attacks shifts away from creating botnets from many weak IoT devices. Instead, it focuses on compromising vulnerable and misconfigured VPS servers using known exploits or leaked API credentials. Botnets are built easier and faster this way, and attacks are significantly stronger than before, with botnets being up to 5,000 times stronger.
Cloudflare explains that cloud computing providers offer VPS to enable businesses to create performant applications. This also allows attackers to create highly efficient botnets.
Cloudflare is collaborating with cloud computing providers and partners to combat these emerging VPS-based threats. They claim to have taken down large portions of these novel botnets.
DDoS Statistics of 2023 Q1: Major Increase in Ransom-Based DDoS
The report also shows that the DDoS activity remained consistent in the first quarter of 2023. However, ransom-based DDoS attacks have increased by 60% yearly, accounting for 16% of all DDoS attacks.
The most targeted countries included the United States, Canada, and Turkey; however, the top country was Israel, possibly due to the Killnet-supported Anonymous Sudan specifically targeting the country.
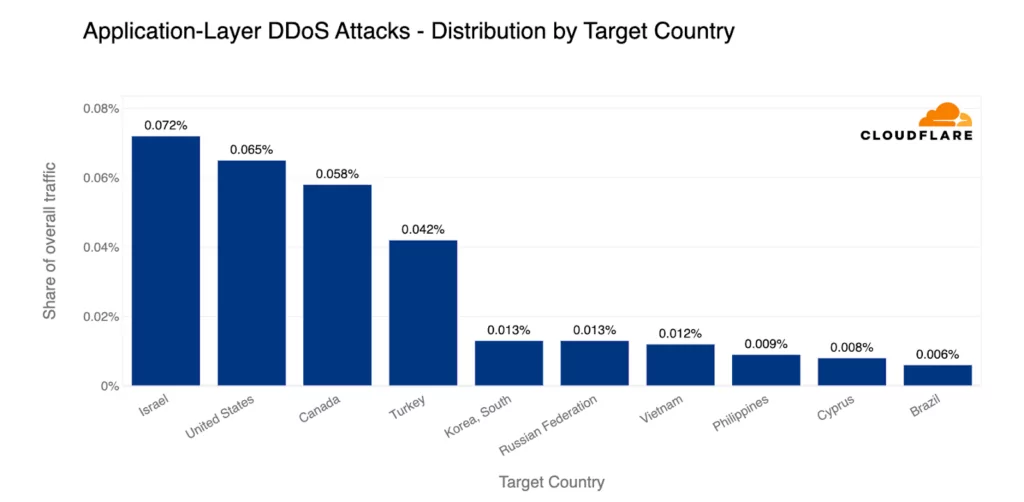
Gaming and gambling were the most targeted industries in Asia, Europe, and the Middle East, as were banking and financial services in South and Central America. Other targeted industries to mention are internet services, marketing, and software.
In the first quarter of 2023, Finland was the leading source of HTTP DDoS attacks in terms of attack traffic as a percentage of total traffic per country. The British Virgin Islands came in second place, closely followed by Libya and Barbados.
Finland, the British Virgin Islands, Libya, and Barbados were the leading sources of HTTP DDoS attacks in Q1 2023.
DNS-Based DDoS Attacks Take the Lead as Most Popular Attack Vector
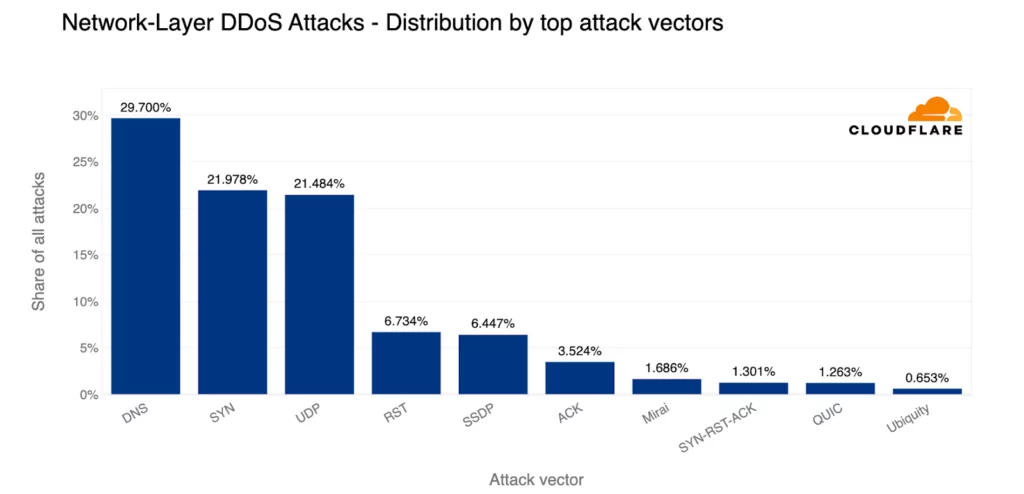
There has been a major change in the top DDoS attack vectors this quarter. DNS-based attacks have now become the most popular, with a 30% share, pushing SYN floods to second place with a 22% share.
In fact, almost one-third of all L3/4 DDoS attacks were DNS-based, including DNS floods and DNS amplification/reflection attacks. UDP-based attacks came in third place with a 21% share, not far behind SYN floods.
Previous World Record Exceeded
The largest attack that Cloudflare has encountered this quarter peaked at more than 71 million requests per second. This exceeds Google’s previous world record of 46 million requests per second by 55%.
Another noteworthy event involved a DDoS attack with a throughput of 1.3 terabits per second that was directed at a telecommunications provider in South America.
The majority of the attacks (86.6%) lasted for under 10 minutes, and 91% of them did not exceed 500 Mbps in terms of size and duration.
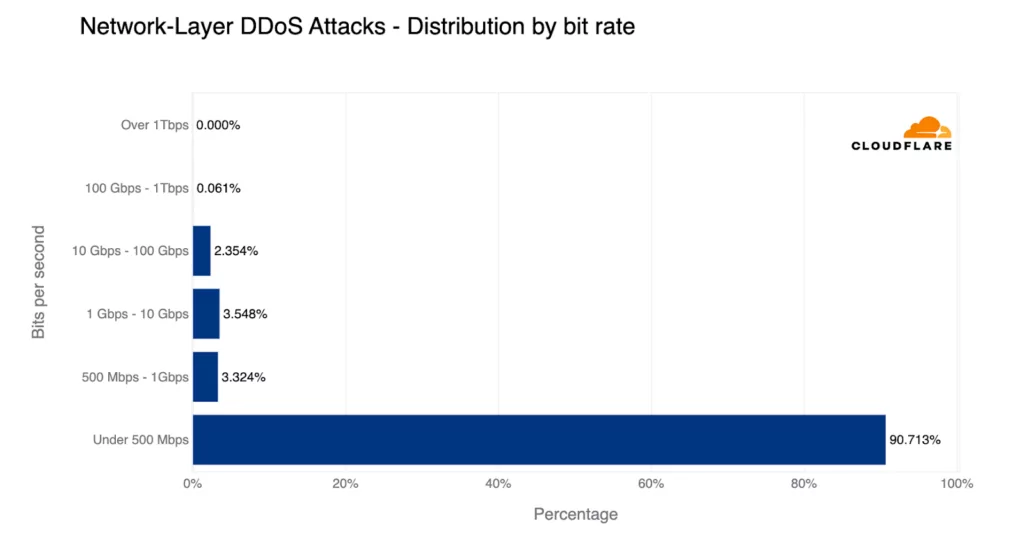
As of the most recent quarter, there were around 6% more attacks that exceeded 100 Gbps, indicating that the frequency of larger attacks is continually increasing.
Emerging Threats: Significant Increase in SPSS, DNS Amplification, and GRE-Based DDoS Attacks
Recent data shows a significant increase in emerging threats. SPSS-based DDoS attacks rose by 1,565% QoQ (Quarter on Quarter), partly due to vulnerabilities such as CVE-2021-22713 and CVE-2021-38153, which can be exploited for reflection DDoS attacks. DNS amplification DDoS attacks also surged by 958% QoQ, while GRE-based DDoS attacks increased by 835% QoQ.
These trends highlight the need for organizations to implement effective security measures to protect against these evolving threats.
DoS Resilience Service: Check Your Domain or Subnet’s Resilience Against DoS Attacks
The free DoS Resilience service offered by SOCRadar Labs provides valuable information for website owners and network administrators to assess their system’s resilience against DoS (Denial of Service) attacks.
With this service, you can easily check your domain’s or subnet’s resilience against common DoS attacks like slowloris, amplification, and reflection attacks. This helps you take preventive measures to ensure your system remains secure and functional.



































