
Dark Web Stories: DDoS as a Service
DoS (Denial-of-service attacks) are frequently encountered in the cyber world and result in violation of the availability of online services. When this attack is made with the help of many computers (botnets), it is called DDoS and can turn into a cyber weapon that can interrupt the services of companies. Every web application user has probably heard or read about DDoS (Distributed Denial of Service) attacks. In this article, we will introduce DDoS as a service, a widely used hiring model adopted by several threat actors on the dark web.
What Happens During a DDoS Attack?
DDoS attacks are unwelcome attempts to render an online service inoperable by sending massive traffic from multiple sources.
As a result, the targeted systems cannot respond to abnormal volume network traffic, leading to slowing down and even crashing.
Attackers use a multi-device botnet that they can remotely control to generate large amounts of network traffic.
What is DDoS as a Service?
DDoS as a service, on the other hand, is when hackers with a botnet network attack a target determined by a malicious person using this network for a certain fee. The botnet network can also be considered a rental. The fee varies depending on the size, duration of the attack, the breadth of the botnet network used, and even whether the target systems use an anti-DDoS product. Expectedly, attacks against systems protected by an anti-DDoS product will be more expensive.
The Story Behind the Dark Web DDoS Attack Service
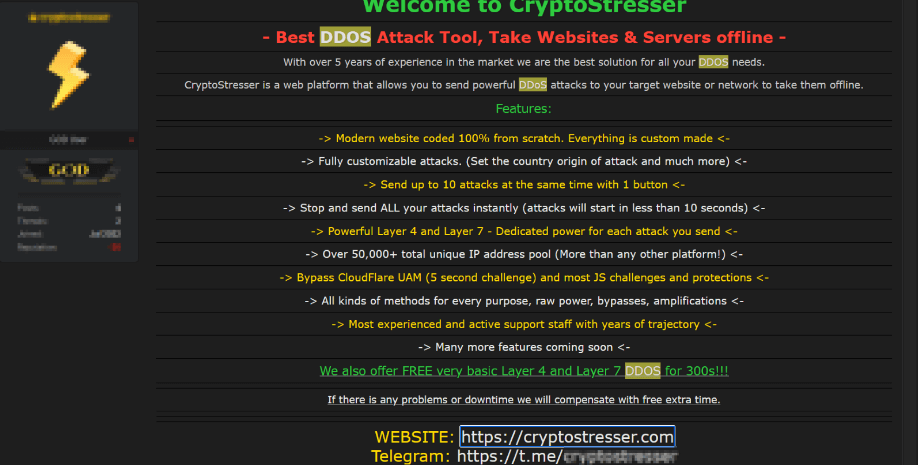
Attackers can also disable the target service by illegally using tools like IP Stresser, which users legitimately use to test their own server causing heavy traffic on someone else’s server. Therefore, target systems may become more vulnerable to attacks.
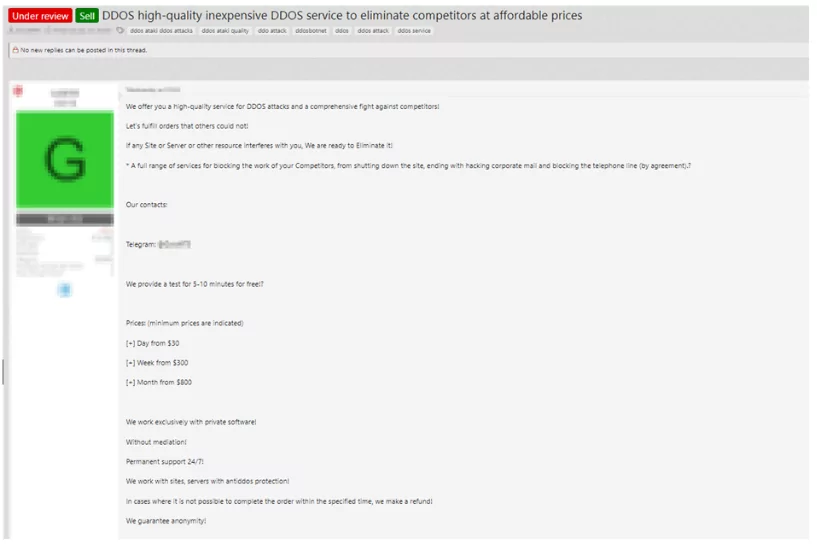
DDoS as a service makes DDoS attacks more accessible and affordable. Therefore, the DDoS service has provided that anyone with the money and time can attack the targeted system. As seen in the figure above, DDoS as a service is put on the dark market at low prices, like 10$ per hour. DDoS attack service providers claim that they can perform a DDoS attack on the desired target for around $30 per day or $5 per hour. In this way, even someone who does not understand computers can attack any target by paying a fee.
How Does It Work?
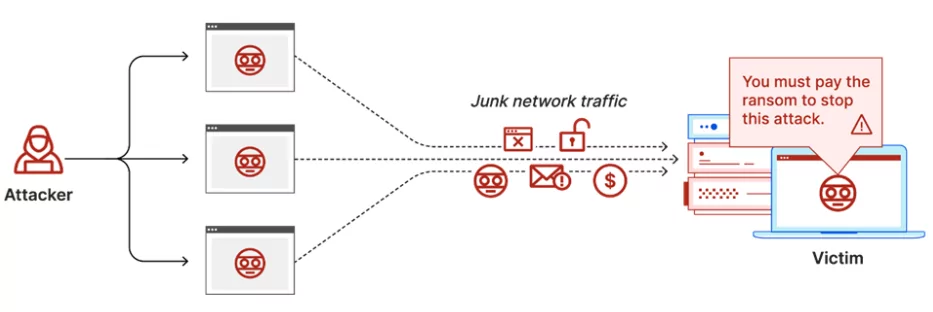
It is an attack that is technically no different from known DDoS attacks. The DDoS attack service users simply determine the target and pay for it. The threat actors who handle the botnet network can carry out this attack.
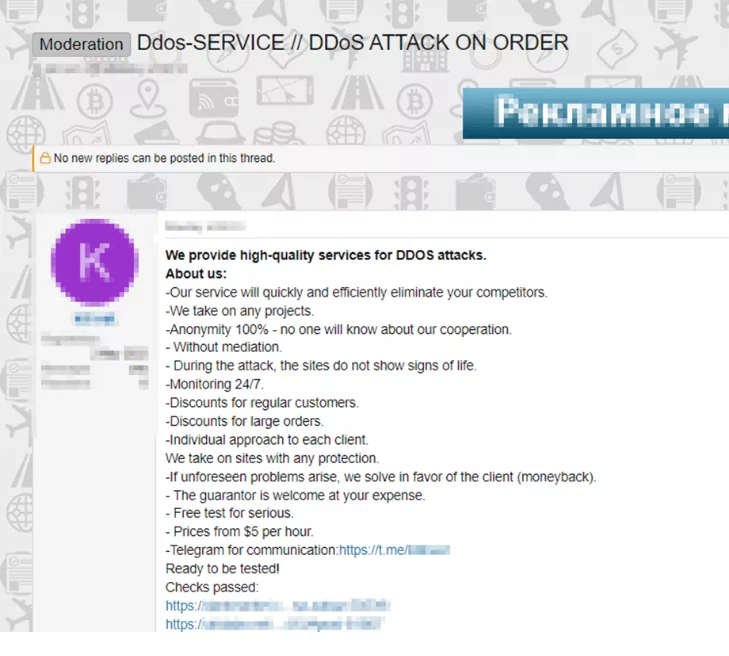
The attacker sends the attack traffic over the botnet network to the target at the desired size and time via the DDoS service. Attack traffic can target layers 3, 4, or 7 of the OSI reference model. This may vary depending on the type of DDoS specified. The targeted application or service can slow down or crash with this attack. The attack is stopped or continued according to the instructions of the attacker from his client.
What Malicious Activities Is It Used For?
In another case, threat actors sometimes use DDoS attacks as just one step of their attack plan. For a large-scale attack, DDoS may be the first step of the attack chain. While the threat actor injects malware into its victim, it may resort to DDoS to cover its tracks up. In addition, sometimes, it may perform a DDoS attack just to intimidate the victim.
Threat actors can blackmail their victims into paying a ransom via a DDoS extortion attack, informing them that the attack will continue unless they pay the ransom. This is also known as a “Ransom DDoS” (RDDoS) attack.
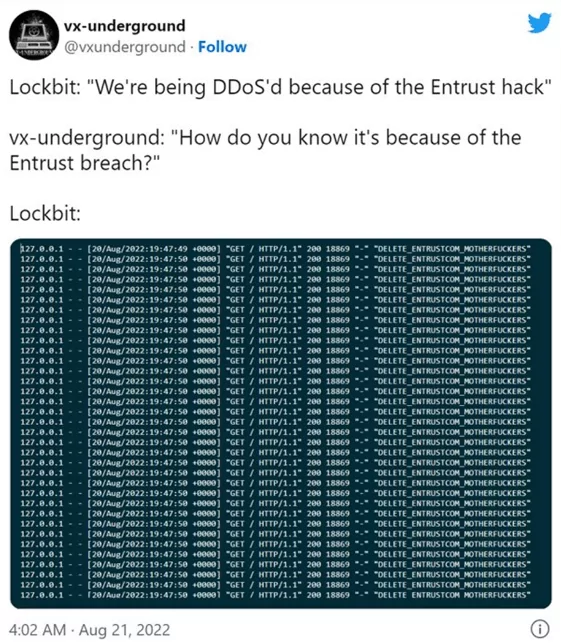
Shot With His Gun!
DDoS attacks, which are frequently used by cyber gangs, are also used against threat actors from time to time. Ransomware groups have also used DDoS attacks to force the victim to pay.
Let’s get into the details of one recent example, the LockBit group’s attack on Entrust. Entrust confirmed it was hacked by the LockBit ransomware group in June 2022 and confirmed that data had been stolen from their internal systems.
Following the DDoS attack that blocked access to Entrust data on the ransomware group’s site, the group said it discovered the triple extortion (encryption + data leak + DDoS) tactic to put more pressure on its victims to pay the ransom. LockBitSupp (general representative of the LockBit ransomware operation) announced that the ransomware operator now wants to use DDoS as an extortion tactic in addition to encrypting and leaking data and looking for someone on the team who can do it for them.
Entrust did not admit the ransom payment, so LockBit announced that it will release all of its stolen data. In the meantime, according to Security research group VX-Underground providing intelligence from LockBitSupp, their Tor site has been attacked by someone believed to be affiliated with Entrust.
This DDoS attack will go down as one of the cyber counter-attacks allegedly performed by ransomware victim organization Entrust. Although the attack affected the LockBit ransomware group website, their 343GB of sensitive data was finally leaked over torrent.
Why Do Threat Actors Prefer DDoS as a Service?
DDoS attacks are one of the most preferred weapons by attackers because they are inexpensive, easier, and more accessible thanks to DDoS as a service. In addition, botnet owners offer advantages such as campaigns, discounts, and loyalty programs for their regular customers. There are even subscription-based DDoS attack services. Another advantage of DDoS attack services is that they provide anonymity, as there is no personal contact between the attacker and the recipient. A dark service like DDoS as a service usually guarantees you anonymity. This is one of the biggest reasons for its popularity.
What is the Role of DDoS Boosters?
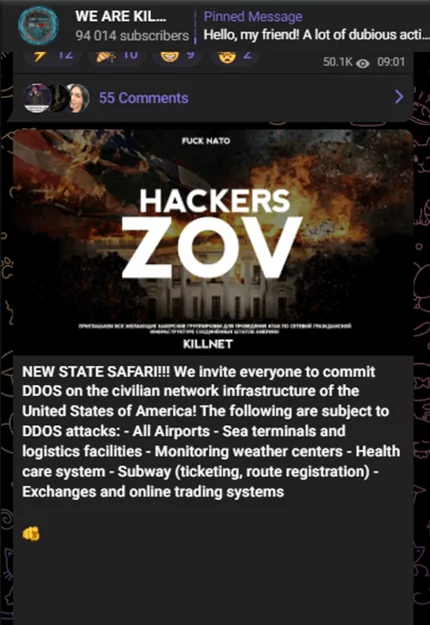

DDoS boosters promise that attacks will be more devastating and long-lasting, and the target will undoubtedly take massive damage. Attackers claim they can disable the target system with 15 million requests per minute and 800,000 botnets, even for DDoS-protected systems like Vshield and Cloudflare.
It is claimed that DDoS attacks against critical targets such as airports, logistics facilities, stock markets, and online trading systems will also be successful. This situation shows that the attackers can have very powerful and large cyber weapons in their hands and that there is a possibility of hitting the desired target, even if it is challenging.
Conclusion
Every user can benefit from these and similar services on the dark web. This situation especially threatens the digital assets of institutions. Attack services, which are becoming more and more accessible and pervasive, are perfectly suited for potential threat actors. As in the case of Ransom-DDoS, cyber criminals put attack models into practice in which attack types are intertwined, making defense difficult.
We need to better understand our digital assets with Attack Surface Management (ASM) and transform them into a more proactive structure than traditional defense methods with Cyber Threat Intelligence (CTI) platforms fed by dark web intelligence.




































