
LockBit Allegedly DDoSed After Leaking Entrust’s Data
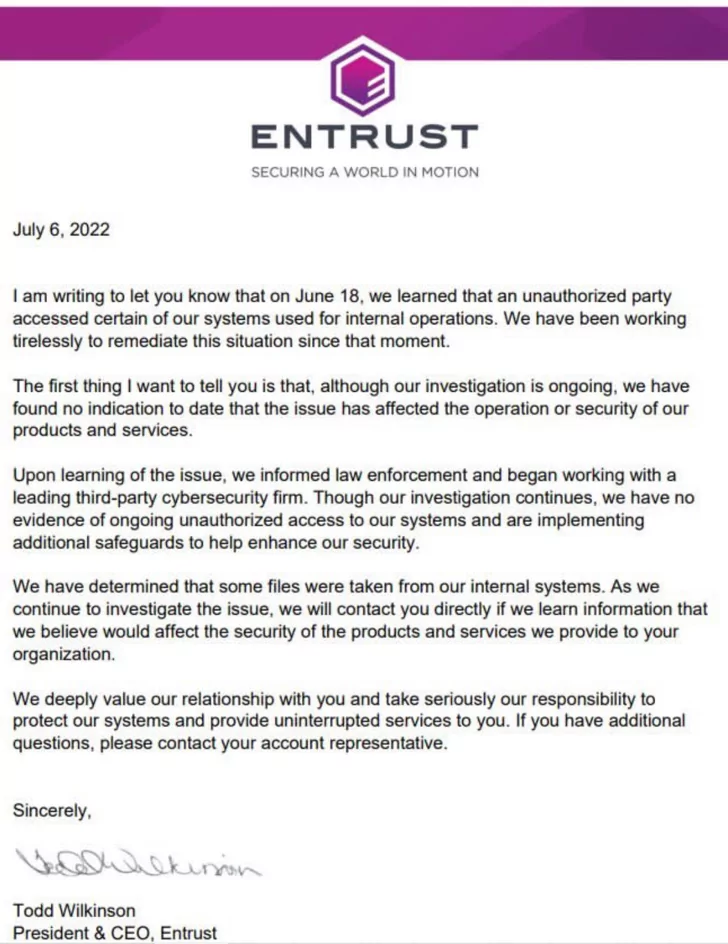
IT security company Entrust suffered a cyberattack on June 18. Attackers gained unauthorized access to the company’s network to reach internal data. Despite the theft of some files, Entrust’s workflow was unaffected. The company later notified their customers about the breach, saying they are still investigating and will provide further information.
LockBit Claimed They Are Behind the Entrust Attack
Dominic Alvieri, a security researcher, reported that LockBit had published a specific data publication page for Entrust on their leak site and promised to expose all of the stolen information the following evening.
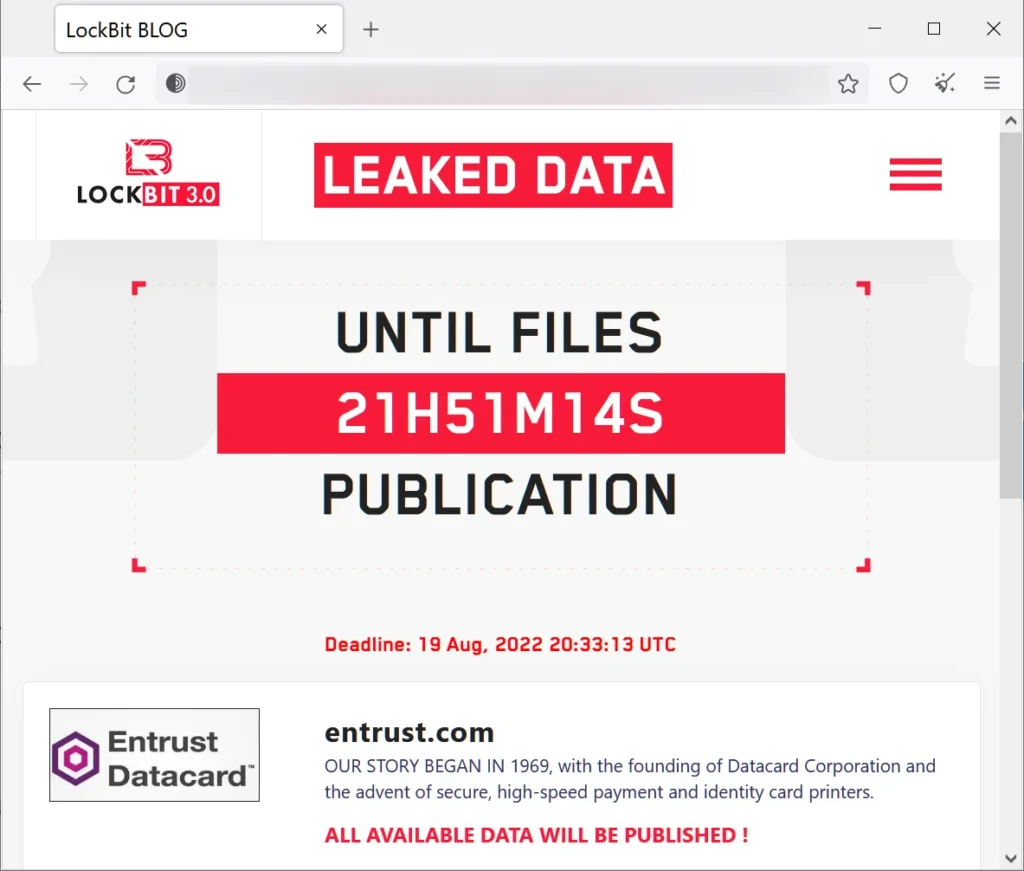
Given that LockBit promises to make all data public, it can be said that Entrust has not engaged in negotiations with the ransomware operation or is unwilling to agree with its demands.
What Has Been Leaked So Far?
On August 9, LockBit began revealing pieces of Entrust’s stolen data. The initial leak was only some screenshots that hinted at the documents that would soon be leaked.
According to Alvieri, who has been monitoring the breach, accounting and legal files and marketing spreadsheets were among the information that was exposed.
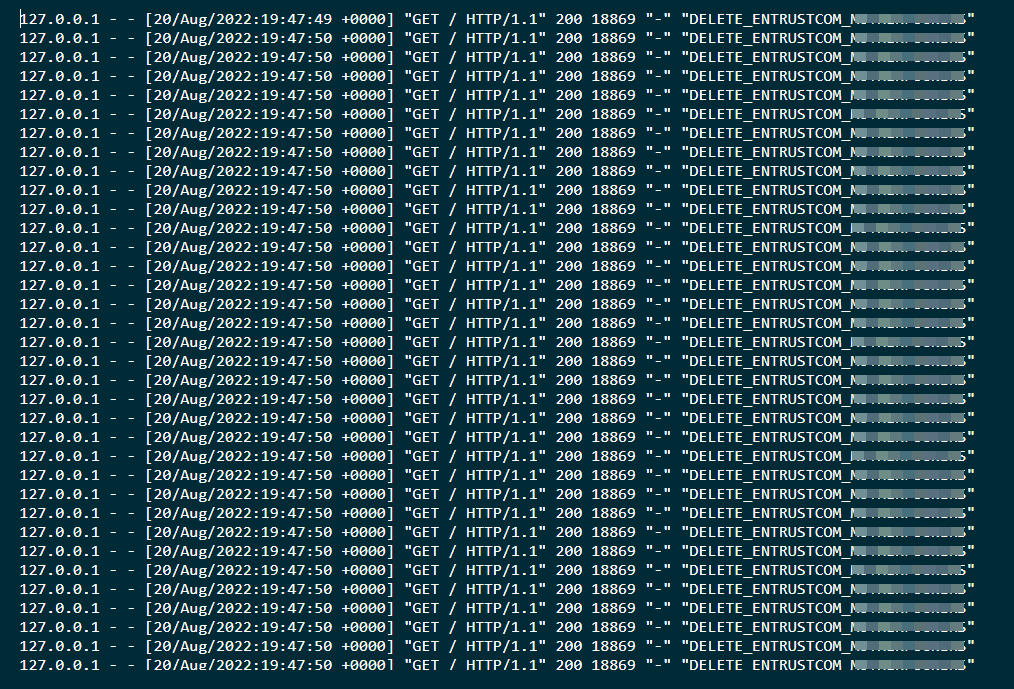
LockBit’s sites went offline a while after they started leaking the data. The threat actors behind the ransomware group claimed it was a DDoS attack related to their controversy with Entrust.
With its public-facing operation LockBitSupp, LockBit is one of the most active ransomware organizations.
LockBit 3.0, which included new encryptors built on the BlackMatter source code, new payment methods, new extortion tactics, and the first ransomware bug bounty program, was launched in June.
Mitigation Methods
It is advised for security and network experts to stay current with the threat actor’s development and TTPs, as well as monitor the software and firmware updates done regularly.
Reviewing accounts and privileges is also necessary. Accounts or privileges that are not required anymore should be removed. Implement security measures and have a dedicated SOC team to increase visibility into all digital assets. Ensure you have a backup plan to prevent a disruption in workflow due to any cyber incident, including ransomware attacks.
LockBit TTPs
- T1107 – File Deletion
- T1055 – Process Injection
- T1112 – Modify Registry
- T1215 – Kernel Modules and Extensions
- T1060 – Registry Run Keys / Start Folder
- T1179 – Hooking
- T1055 – Process Injection
- T1179 – Hooking
- T1124 – System Time Discovery
- T1046 – Network Service Scanning
- T1083 – File and Directory Discovery
- T1016 – System Network Configuration Discovery
- T1012 – Query Registry
- T1082 – System Information Discovery
- T1057 – Process Discovery
- T1063 – Security Software Discovery
- T1047 – Windows Management Instrumentation
- T1035 – Service Execution
- T1075 – Pass the Hash
LockBit IoCs
SHA256:
- 0d38f8bf831f1dbbe9a058930127171f24c3df8dae81e6aa66c430a63cbe0509
- 9a34909703d679b590d316eb403e12e26f73c8e479812f1d346dcba47b44bc6e
- 39c363d01fb5cd0ed3eeb17ca47be0280d93a07dda9bc0236a0f11b20ed95b4c
- 80e8defa5377018b093b5b90de0f2957f7062144c83a09a56bba1fe4eda932ce
- 391a97a2fe6beb675fe350eb3ca0bc3a995fda43d02a7a6046cd48f042052de5
- 506f3b12853375a1fbbf85c82ddf13341cf941c5acd4a39a51d6addf145a7a51
- 742489bd828bdcd5caaed00dccdb7a05259986801bfd365492714746cb57eb55
- a56b41a6023f828cccaaef470874571d169fdb8f683a75edd430fbd31a2c3f6e
- b951e30e29d530b4ce998c505f1cb0b8adc96f4ba554c2b325c0bd90914ac944
- c6cf5fd8f71abaf5645b8423f404183b3dea180b69080f53b9678500bab6f0de
- d61af007f6c792b8fb6c677143b7d0e2533394e28c50737588e40da475c040ee
- f9b9d45339db9164a3861bf61758b7f41e6bcfb5bc93404e296e2918e52ccc10
- fd98e75b65d992e0ccc64e512e4e3e78cb2e08ed28de755c2b192e0b7652c80a





































