
Chinese State-Sponsored Threat Actors Breach U.S. Treasury Department in Major Cybersecurity Incident
[Update] January 7, 2025: “CISA Provides Update on U.S. Treasury Breach”
Chinese state-sponsored threat actors have once again targeted a critical U.S. institution, this time breaching the Treasury Department in a sophisticated cyberattack. The incident, deemed a “major cybersecurity breach” by Treasury officials, is the latest in a string of attacks attributed to Chinese Advanced Persistent Threat (APT) groups that continue to focus on compromising American agencies and infrastructure. Leveraging vulnerabilities in third-party services, these actors demonstrate a growing ability to bypass traditional security measures and access sensitive systems.
What Are the Details of the Treasury Department Breach?
In a letter to lawmakers, the Treasury Department disclosed that it was alerted to the breach on December 8 by BeyondTrust, a vendor providing remote support services. The investigation revealed that the attackers had obtained a stolen API key, allowing them to override security protocols and remotely access departmental systems. BeyondTrust subsequently identified and mitigated two zero-day vulnerabilities—CVE-2024-12356 and CVE-2024-12686—that facilitated the intrusion.
“Based on available indicators, the incident has been attributed to a China state-sponsored Advanced Persistent Threat (APT) actor,” the Treasury’s letter stated. Per departmental policy, any intrusion involving an APT actor is classified as a major cybersecurity incident.
Amid growing concerns over state-sponsored cyberattacks, tools like SOCRadar’s Vulnerability Intelligence play a critical role in helping organizations bolster their defenses.
SOCRadar Vulnerability Intelligence
By providing real-time updates on vulnerabilities, SOCRadar enables security teams to identify and address potential weaknesses before they can be exploited by advanced threat actors. With detailed reports, exploit availability data, and risk prioritization, SOCRadar’s insights ensure organizations can respond proactively to evolving threats.
What Actions Have Been Taken to Mitigate the Cyberattack?
BeyondTrust responded swiftly by shutting down compromised instances of its Remote Support SaaS platform and revoking the stolen API key. The Treasury Department, supported by the FBI and the Cybersecurity and Infrastructure Security Agency (CISA), continues to assess the full impact of the breach. Officials have assured that the attackers no longer have access to Treasury systems.
The incident underscores the increasing threat posed by APT groups targeting trusted third-party service providers. Such methods are part of a broader strategy observed in recent years, aimed at bypassing traditional security defenses.
Broader Context and Implications
This breach follows a series of high-profile cyber incidents attributed to Chinese state-sponsored actors, including recent attacks on U.S. telecommunications companies. Among these, the most notable are recent attacks targeting major U.S. telecommunications companies, reportedly orchestrated by a Chinese Advanced Persistent Threat (APT) group known as Salt Typhoon.
In these telecom breaches, the attackers allegedly gained unauthorized access to sensitive communication data, including text messages, voicemails, and wiretap information. The breaches, which affected prominent providers like Verizon, AT&T, and T-Mobile, also extended to wiretap data from ongoing law enforcement investigations. This unprecedented access enabled the attackers to monitor targeted individuals’ communications, posing significant risks to national security and individual privacy.

Threat actor card of Salt Typhoon
The sophistication of these attacks highlights the increasing capability of Chinese APT groups to exploit vulnerabilities in trusted third-party systems. As these cyber operations grow more advanced, they reinforce the urgent need for stronger defensive measures across both public and private sectors in the United States.
How Has China Responded to the Hacking Allegations?
A spokesperson for the Chinese embassy in Washington dismissed the allegations, labeling them a “smear attack” and asserting that cyber incidents should be analyzed with a “professional and responsible attitude.” The spokesperson further emphasized the difficulty of accurately attributing cyberattacks and rejected claims of Chinese involvement.
CISA Provides Update on U.S. Treasury Breach
On January 6, 2025, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) released an update on the recent cybersecurity breach at the U.S. Department of the Treasury. CISA confirmed that no other federal agencies have been impacted by the breach. The agency continues to monitor the situation closely and is coordinating with relevant authorities to ensure a thorough response.
The breach, attributed to a Chinese state-sponsored Advanced Persistent Threat (APT) actor, involved a compromised BeyondTrust instance at the Treasury Department. The attackers gained access using a stolen Remote Support SaaS API key, primarily targeting the Office of Foreign Assets Control (OFAC). While the Office of Financial Research was also compromised, the full impact is still under assessment, and efforts to mitigate the breach have been underway since it was detected.
With the compromised instance now shut down, CISA is collaborating with the Treasury Department and BeyondTrust to address any remaining risks. The agency has reassured the public that it will continue to provide updates as necessary.
Looking Ahead
As investigations into the Treasury Department breach progress, the agency has committed to delivering a supplemental report to lawmakers within 30 days, aiming to provide deeper clarity on the scope and impact of the attack. This incident underscores the pressing need for robust cybersecurity measures, particularly as state-sponsored hacking campaigns grow increasingly sophisticated and disruptive.
SOCRadar plays a vital role in addressing these challenges with its Threat Actor Intelligence and Supply Chain Intelligence modules.
The Threat Actor Intelligence module delivers actionable insights into the tactics, techniques, and procedures (TTPs) employed by Advanced Persistent Threat (APT) groups, empowering organizations to anticipate and mitigate risks proactively.
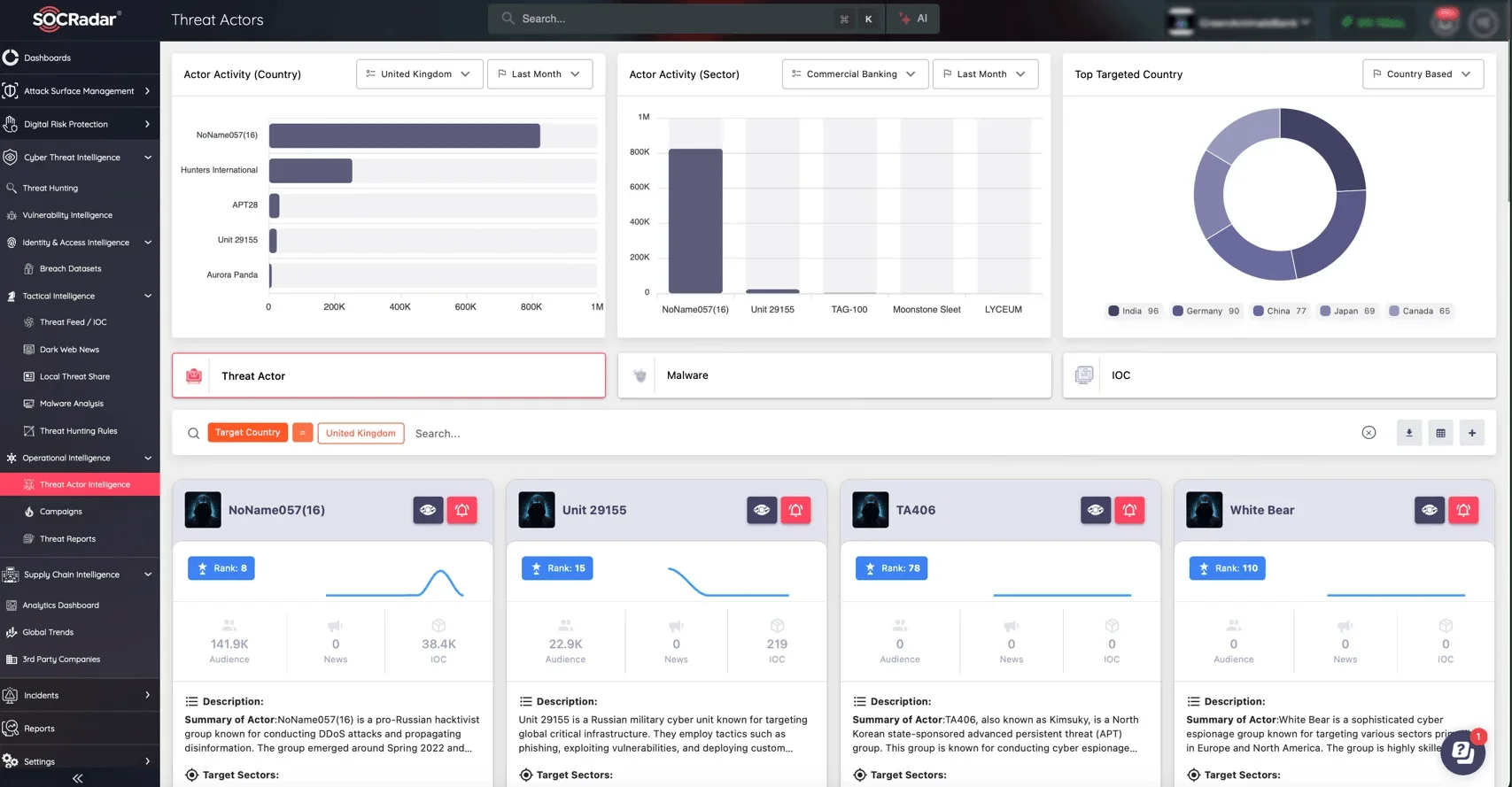
SOCRadar Threat Actor Intelligence
The Supply Chain Intelligence module, on the other hand, identifies vulnerabilities within an organization’s supply chain, providing real-time visibility into third-party risks and potential exploit paths. This dual focus equips organizations to secure their operations from both direct attacks and indirect risks introduced through vendors and partners.
SOCRadar Supply Chain Intelligence
The Treasury Department breach illustrates the critical need for organizations to adopt comprehensive intelligence solutions to enhance their cybersecurity posture. Leveraging SOCRadar’s advanced capabilities, organizations can better understand and counteract sophisticated threat actors while addressing hidden risks in their supply chains. As the digital threat landscape evolves, integrating advanced threat and supply chain intelligence will be central to protecting critical infrastructure and ensuring long-term resilience.




































