
A for APT: Criteria for Classifying Cyber Threats
The term “Advanced Persistent Threat” (APT) has emerged as a critical concept, necessitating a nuanced understanding and accurate classification.
APTs represent a formidable class of cyber threats, characterized by their sophisticated tactics, persistent nature, and, often, significant backing resources from state sponsorships. These groups execute coordinated and covert cyber-attacks, primarily targeting high-value objectives such as state secrets, intellectual property, or important financial assets.
The accurate identification and classification of APT groups are more than an academic exercise; it’s a cornerstone of effective cybersecurity strategy and response. Mislabeling or overestimating a cyber threat as an APT can lead to misallocated resources and a skewed perception of the cyber threat landscape.
Conversely, underestimating or failing to recognize an actual APT can leave organizations and states vulnerable to significant and sustained cyber incursions.
Understanding APTs: Core Characteristics
Advanced Persistent Threats (APTs) are distinguished by a set of defining characteristics that set them apart from other types of cybersecurity threats. Understanding these core characteristics is crucial for accurately identifying APTs and distinguishing them from other types of cyber attacks.
Advanced Techniques and Capabilities: APTs are known for their high level of sophistication. This sophistication is evident in the Techniques, Tactics, and Procedures (TTPs) they employ.
APT groups often use custom-developed malware and zero-day exploits, which are vulnerabilities unknown to the software vendor and the public, thus often having no existing defense measures. Their operations typically demonstrate a deep understanding of cybersecurity and network systems, enabling them to navigate and exploit complex security environments.
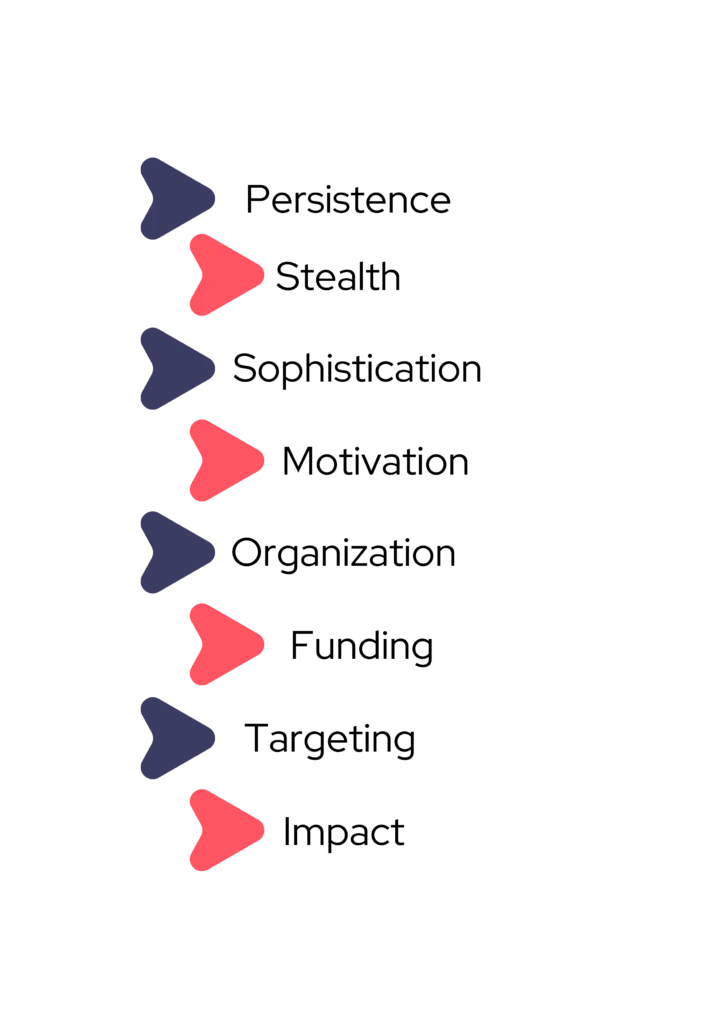
All the main characteristics of an APT, From Zero to Adversary: APTs (SOCRadar)
Persistence: The term’ persistent’ in APTs primarily refers to the duration and determination of the threat actors in achieving their objectives. Unlike opportunistic cybercriminals who seek quick gains, APT actors engage in prolonged operations, sometimes spanning months or even years. Their goal is often to maintain long-term access to the target’s network, allowing them to continuously monitor and extract valuable information over an extended period.
Significant Resources and Backing: APT groups usually have substantial resources at their disposal. This can include advanced technical tools, financial backing, and human resources. The level of resources available to APT groups often suggests state or state-sponsored backing, although this is not always the case. The availability of these resources allows them to develop and deploy a wide range of tools and tactics and to adapt to countermeasures employed by their targets.
Target Selection: APTs typically target high-value organizations, such as government entities, military institutions, and large corporations. Their goals can range from espionage and intellectual property theft to sabotage and disruption of critical operations. The selection of these targets is usually strategic, aligning with broader goals such as political, economic, or military advantage.
Stealth and Evasion Techniques: One of the hallmarks of APTs is their ability to evade detection for long periods. They use a variety of stealth techniques to conceal their activities, including the use of encrypted channels, deletion of logs, and mimicking legitimate network traffic. The ability to remain undetected allows them to gather intelligence and execute their plans without alerting the target or triggering defensive measures.
Adaptability and Evolution: APT groups are known for their adaptability and the evolution of their tactics over time. They continuously refine their methods in response to security developments and countermeasures. This adaptability makes APTs particularly challenging to defend against, as they are constantly changing their approaches to circumvent new security protocols.
Below, we have organized a simple diagram to define an APT:
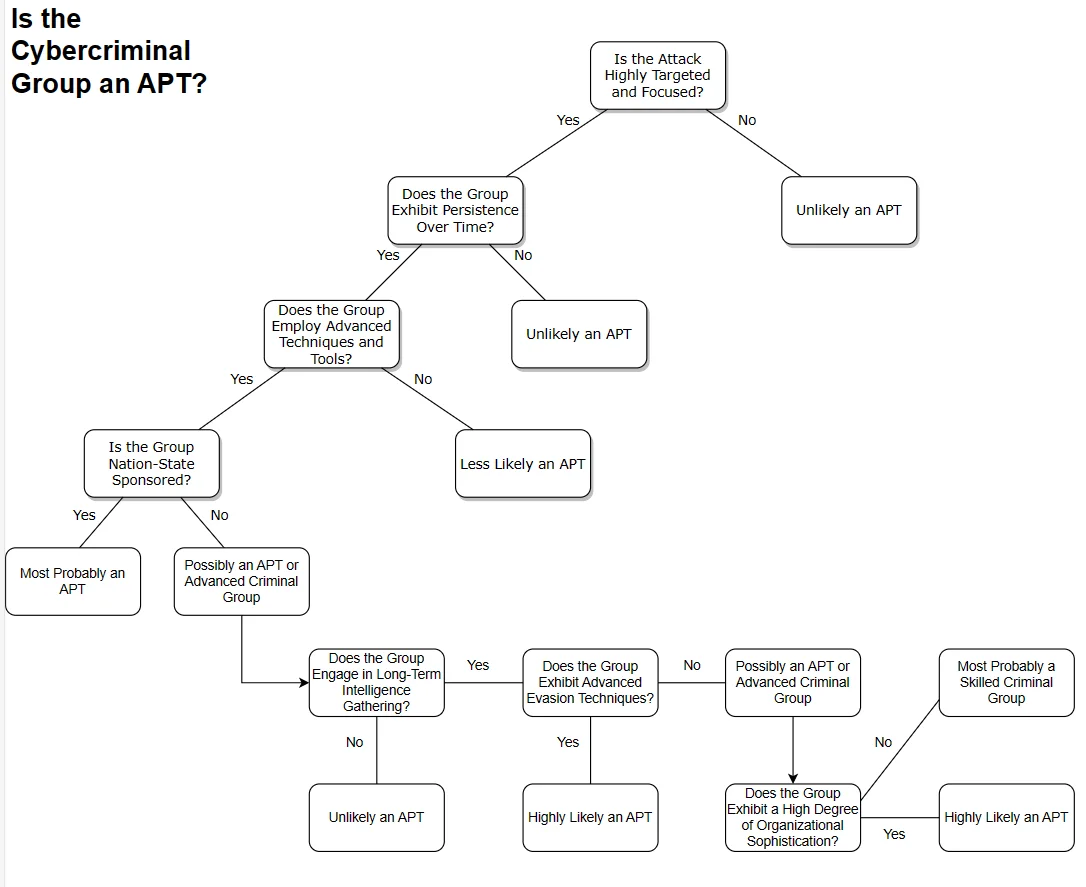
Decision tree for defining an APT
The Twist: Misconceptions and Overclassification
The term “Advanced Persistent Threat” (APT) is often surrounded by misconceptions and a tendency towards overclassification, leading to a skewed understanding of the cyber threat landscape. Addressing these misconceptions is crucial for developing accurate threat assessments and effective cybersecurity strategies.
APT as a Buzzword: One of the most common misconceptions is overusing the term APT to describe almost any sophisticated cyber attack. This misuse stems partly from the term’s inherent ambiguity and its evolution into a buzzword in cybersecurity discussions. Not every sophisticated or targeted attack should be labeled as an APT. The unique combination of advanced techniques, persistence, significant resources, and strategic target selection sets true APTs apart.
State-Sponsorship Assumption: There’s a prevalent assumption that all APTs are state-sponsored or state-affiliated. While many APT groups do have ties to nation-states, this is not a defining characteristic of an APT. The key aspect is their capability and intent, not necessarily their affiliation. Overemphasis on state sponsorship can lead to a narrow view of the threat landscape, overlooking sophisticated actors operating independently.
Overestimating Capabilities: Sometimes, cybersecurity communities and media may overestimate the capabilities of certain groups, prematurely labeling them as APTs. This can happen due to a lack of comprehensive information during the early stages of an attack’s investigation or due to sensationalizing cyber threats. Overestimation can divert attention and resources away from other, potentially more significant threats.
Underestimating Non-APT Threats: Conversely, the focus on APTs can lead to underestimating non-APT threats. Cybercriminals and hacking groups that do not fit the APT profile can still execute highly damaging attacks, especially ransomware groups. By concentrating too heavily on APTs, organizations may neglect other forms of cybersecurity threats that require different defensive strategies.
Mislabeling for Marketing Purposes: In some instances, cybersecurity firms may mislabel certain groups as APTs for marketing purposes to emphasize their capability to handle high-level threats. This commercial angle can muddy the waters of accurate threat classification, leading to a misunderstanding of the actual risk landscape.
Misconceptions and overclassification skew threat perception and impact how organizations prepare for and respond to cyber threats.
State-Sponsorship and APTs
State-sponsorship is a frequently discussed aspect in the realm of Advanced Persistent Threats (APTs), often leading to a conflation between state-sponsored activities and APTs. However, not all state-sponsored cyber activities meet the criteria to be classified as APTs, and not all APTs are necessarily state-sponsored.
Historically, many APTs have been linked to nation-states, either directly or indirectly. This linkage is based on the nature of their targets, the resources required for their operations, and their long-term strategic objectives, which often align with national interests. State-sponsored APTs typically focus on intelligence gathering, political espionage, or disruption of foreign entities that are of national interest.
One of the examples that illustrates this situation is the Scattered Spider. Although it is a group with APT capabilities, it does not have a similar scope organizationally and has no known state funding. In this context, it is mostly considered as a cyber crime group, not APT.
In addition, KillNet, which is thought to be state sponsored according to CISA‘s claim, is not named as such because it is generally at a level of ability that cannot be considered an APT with relatively simple attack methods such as DDoS attack.
True APTs vs. Non-APTs
The Cyber Av3ngers, reportedly linked to Iran’s Islamic Revolutionary Guard Corps, have been known for targeting critical infrastructure, especially in the US and Israel.
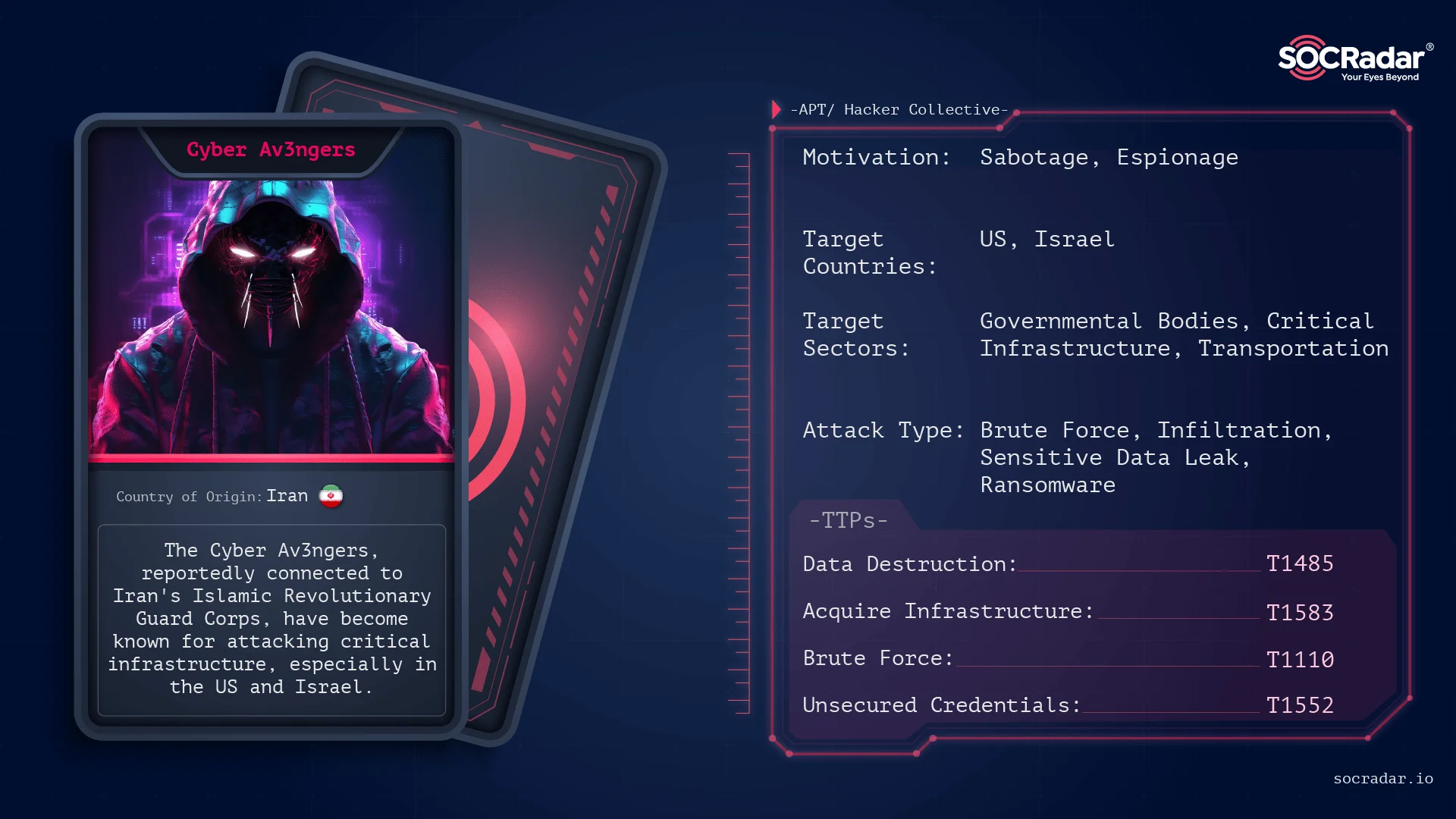
Cyber Av3ngers Threat Actor Card
Their focus is primarily on SCADA systems made by Israeli companies but used globally. While some of their attack claims are questionable, others have been confirmed. They are considered an APT due to their alleged sophisticated techniques and targets.
However, some of their claims, especially regarding compromising Israeli infrastructure, have been disproven, and they may be more accurately described as a state-sponsored hacktivist group rather than a full-fledged APT.
It is likely that they have ties with Iran and are attacking critical infrastructures. Their success in a few attacks allowed them to appear in the mainstream media. However, many institutions they attacked were also using Unitronics products.
Looking at this context, a group that seems to have only one weapon cannot achieve a true APT sophistication in our opinion. False claims, unfounded ransomware allegations, and amateur approaches of other affiliated groups were other factors that supported our opinion.
Consequences of Mislabeling Groups as APTs
Mislabeling groups as Advanced Persistent Threats (APTs) can have significant consequences for cybersecurity defense and intelligence. This section explores the impact of such misclassification on organizations and the broader cyber threat landscape.
Distorted Threat Perception: When groups are incorrectly labeled as APTs, it can lead to a distorted perception of the threat landscape. Organizations may prioritize defenses against perceived high-level threats, potentially overlooking or underestimating other serious threats. This misperception can lead to a misallocation of resources and attention.
Resource Misallocation: One of the most tangible impacts of mislabeling is the misallocation of cybersecurity resources. APTs require sophisticated and often costly countermeasures. If resources are dedicated to combating threats that are not truly APTs, it may leave less critical but more probable threats unaddressed. This misallocation can result in vulnerabilities in areas that might be exploited by less sophisticated, yet still dangerous, cyber adversaries.
Ineffective Cybersecurity Strategies: Building a cybersecurity strategy on a misinformed understanding of threats can render these strategies less effective. If an organization is focused on defending against a misclassified APT, they may implement inappropriate or inadequate security measures that do not align with the actual threats they face.
Complacency in Security Posture: There’s a risk that labeling a less sophisticated group as an APT might lead to complacency once that threat is mitigated. If an organization believes it has successfully defended against an APT, it might assume a level of security and preparedness that is not accurate, potentially lowering its guard against actual APTs or other cyber threats.
Implications for Industry Collaboration: The cybersecurity community relies on sharing accurate threat intelligence. Mislabeling groups as APTs can lead to the dissemination of incorrect information, hampering the effectiveness of collaborative defense efforts. This misinformation can spread across the industry, affecting how various organizations perceive and prepare for cyber threats.
Long-Term Impact on Cybersecurity Evolution: The continual evolution of cybersecurity defenses is partly driven by the threats they aim to mitigate. Misclassification can skew this evolution, potentially leading to the development of tools and practices that are not aligned with the real threat landscape.
Conclusion
In conclusion, the classification of cyber threats, particularly distinguishing between true Advanced Persistent Threats (APTs) and other types of cyber actors, is a critical task in the domain of cybersecurity. This article has examined the core characteristics that define APTs, debunked common misconceptions, and outlined the specific criteria necessary for accurate classification. Through case studies and discussion on the consequences of mislabeling, we have seen the importance of a precise and informed approach to identifying APTs.
The accurate classification of APTs is more than an academic exercise; it is essential for effective cyber defense strategies. Mislabeling or misunderstanding the nature of cyber threats can lead to misallocated resources, ineffective strategies, and a false sense of security. As the cyber threat landscape continues to evolve, the need for vigilance and refinement in classification becomes ever more crucial.
Cybersecurity professionals and organizations must remain agile and informed, constantly updating their understanding of threats and adapting their strategies accordingly. The fight against cyber threats is a dynamic and ongoing challenge, requiring a balanced and comprehensive approach. By maintaining a focus on accurate classification and understanding of APTs, the cybersecurity community can better prepare for and respond to the sophisticated threats that define our digital age.
You can access threat feeds, YARA Rules, Indicators of Compromise (IoCs), and classification by simply searching our Threat Actors page. This allows you to stay updated on their ongoing activities and explore the latest APT-related events through the APT Activity Feed tab.
Additionally, you can access articles about various threat groups, including APT groups, on our blog page for in-depth insights and analysis. We recommend you explore and utilize these valuable resources.
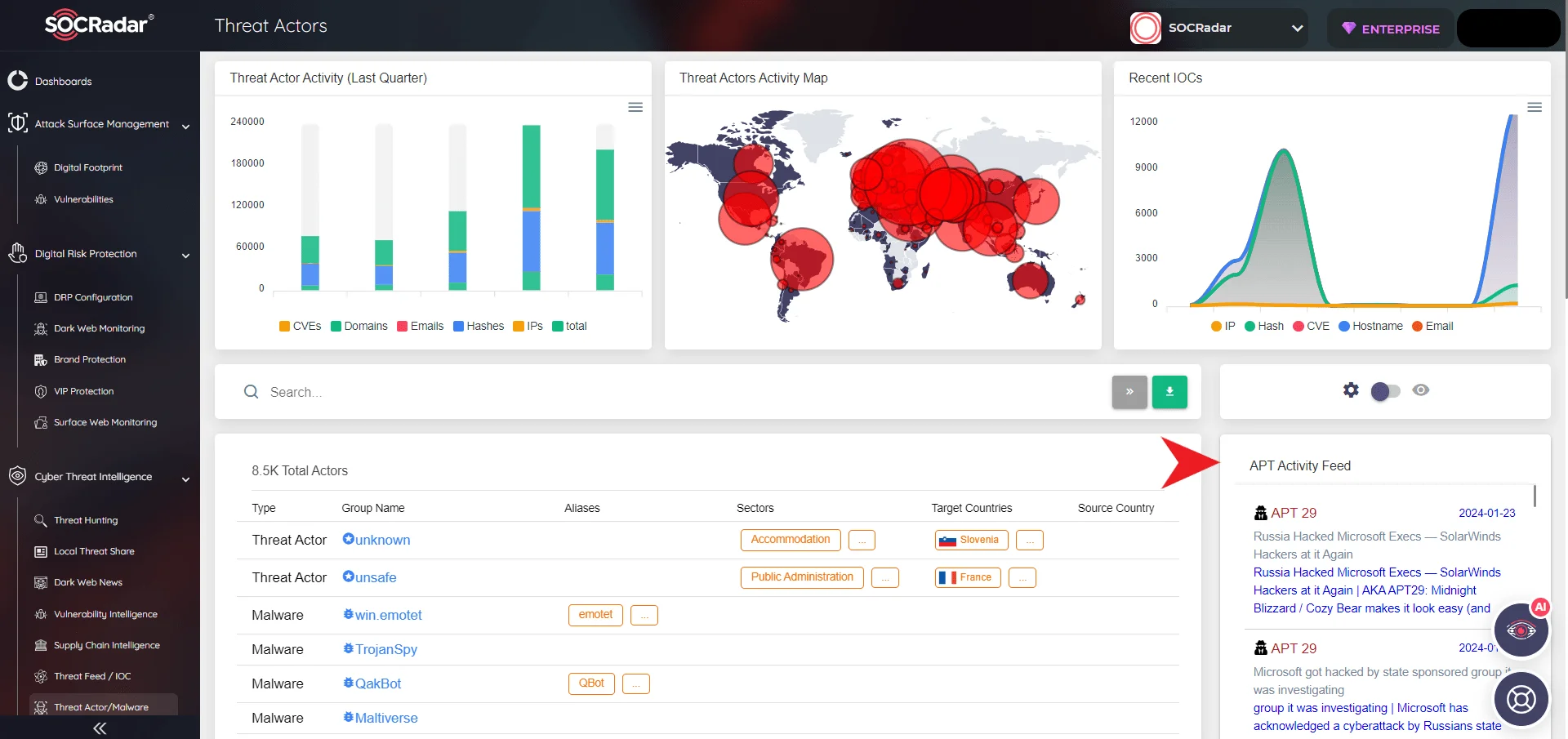
SOCRadar Platform, Threat Actors/Malware
In closing, the key takeaway is the importance of a nuanced approach to cybersecurity. APTs represent a significant and sophisticated threat, but they are just one part of a diverse and complex threat landscape. Recognizing the varied nature of cyber threats and responding with tailored strategies is essential for robust cybersecurity in our interconnected world.




































