
Chrome/Edge Exploit, Aliena Botnet, and Massive Data Breaches Uncovered
Hacker forums monitored by SOCRadar’s Dark Web Team have revealed several alarming cyber threats this week, including the sale of a 0-day RCE vulnerability for Chrome and Edge. Additionally, the source code for the Aliena botnet, a tool targeting financial systems, is being sold. Moreover, the latest breaches include databases from Sólides, Young Living, and ProcessMaker, exposing millions of personal records and sensitive institutional data.
Receive a Free Dark Web Report for Your Organization:
Alleged 0-Day RCE Vulnerability of Chrome and Edge is on Sale

SOCRadar Dark Web Team identified a post on a hacker forum advertising an alleged 0-day Remote Code Execution (RCE) vulnerability for Chrome and Edge.
According to the threat actor, the vulnerability has been discovered but has not yet been disclosed. The actor is seeking a credible bug bounty program that pays in cryptocurrency and does not require personal identification for eligibility. The threat actor has also indicated willingness to sell the vulnerability directly but requires proof of funds or trusted buyer status to avoid scams. The vulnerability is being offered for a starting price of $100,000, with payment accepted exclusively in cryptocurrency.
New Aliena Botnet Source Code is on Sale
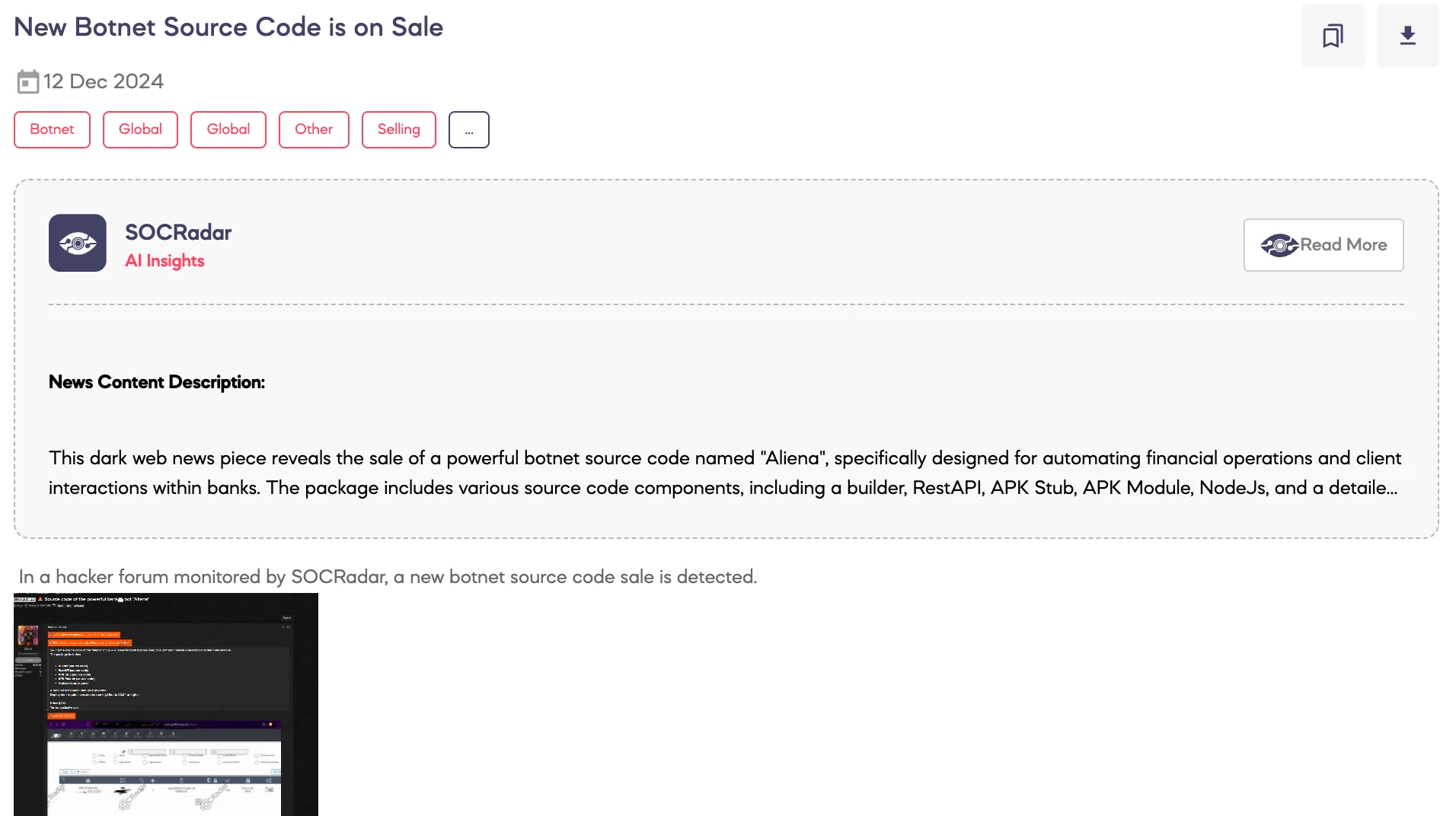
SOCRadar Dark Web Team detected a post on a hacker forum advertising the sale of the source code for a botnet named Aliena.
According to the threat actor, “Aliena” is a highly advanced banking bot designed to automate financial transactions and client interactions. The advertised package includes the following components:
- Source code for the Builder, RestAPI, APK Stub, APK Module, and NodeJs.
- A comprehensive installation manual for setup and deployment.
The deployment requires two servers operating on Ubuntu 20.04 or higher. The threat actor has listed the price at $700 and emphasized that the sale is exclusive. This development highlights a significant risk to financial systems due to the tool’s capabilities and potential misuse.
Alleged Database of Sólides is on Sale
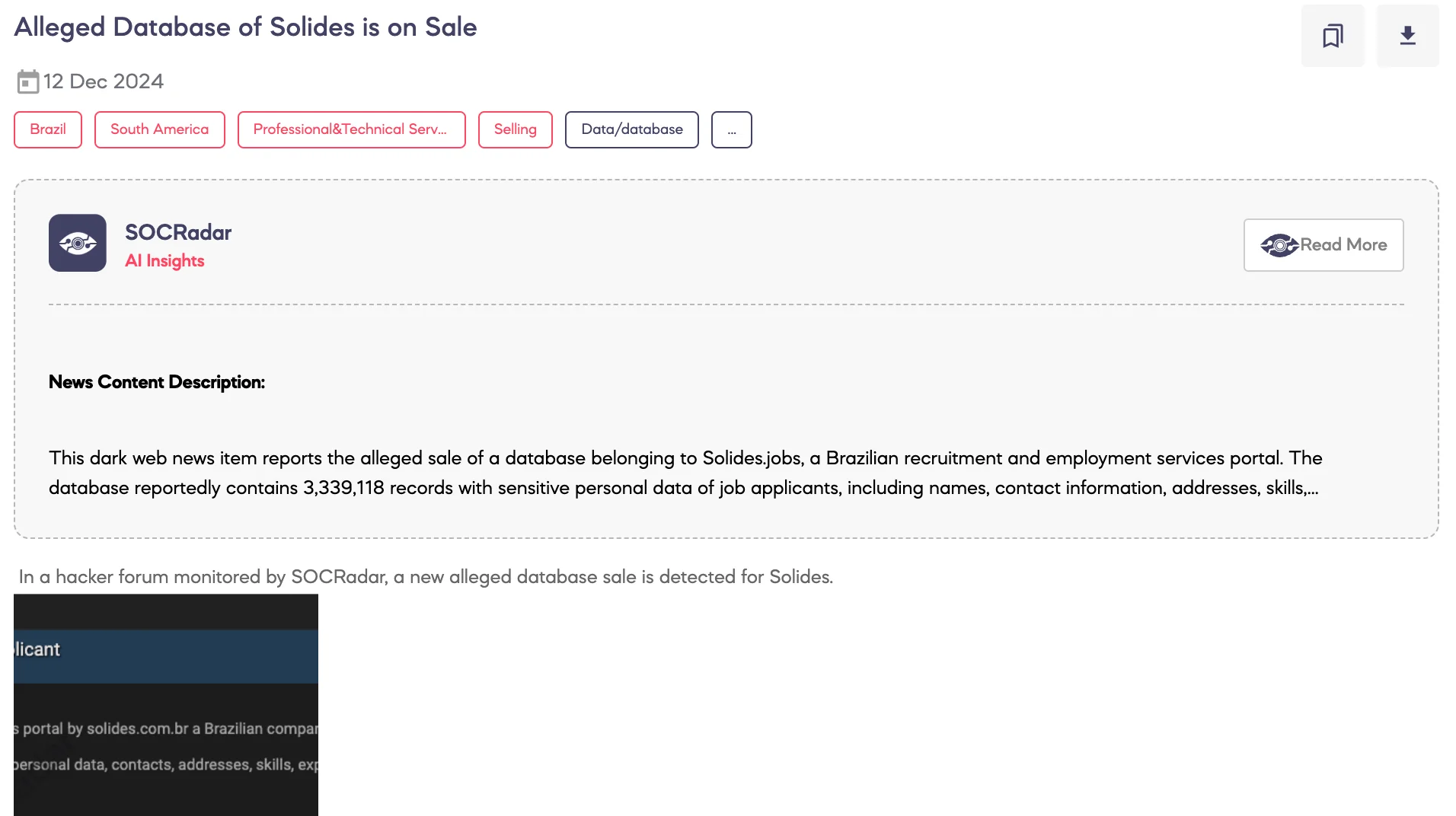
SOCRadar Dark Web Team detected a post on a hacker forum advertising the sale of an alleged database associated with Sólides, a Brazilian company specializing in recruitment and employment services.
According to the threat actor, the database contains detailed information on 3,339,118 applicants, including personal data, contact details, addresses, skills, work experience, and educational courses. This alleged sale poses a significant risk to the privacy and security of the individuals involved.
Alleged Database of Young Living is on Sale
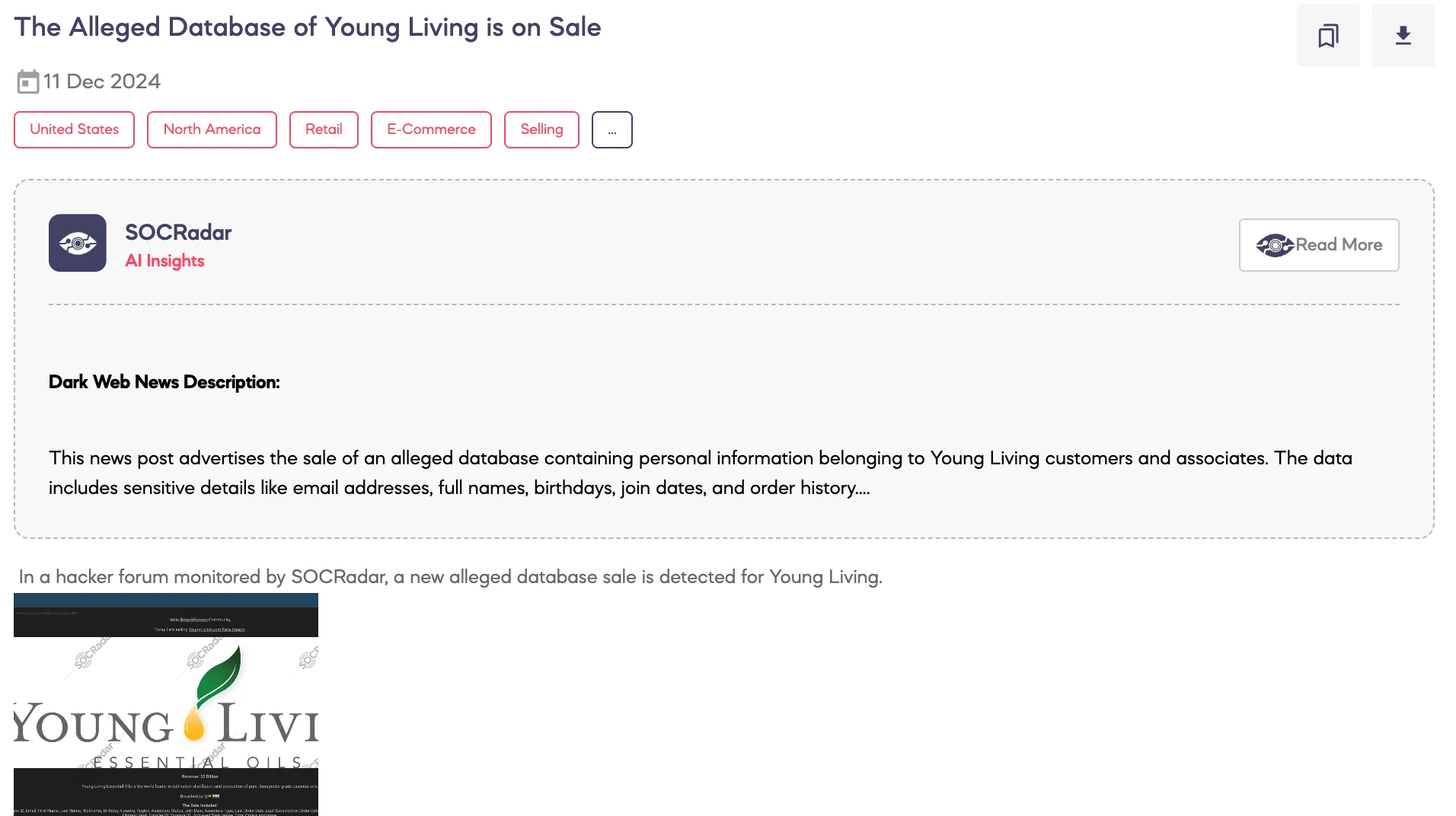
SOCRadar Dark Web Team identified a post on a hacker forum advertising the sale of an alleged database associated with Young Living, a company specializing in the production of essential oils with an annual revenue of approximately $2 billion.
According to the threat actor, the breach involved the exfiltration of sensitive user information, including associate IDs, email addresses, personal details such as names and birthdays, location data, membership status and type, order histories, ranks, and other related information. The dataset is claimed to include records for over 1.1 million unique users.
The actor also alleges that the database contains additional details such as enroller and sponsor IDs, subscription order dates, and language preferences, and has shared a sample to verify the claims.
Alleged Database of ProcessMaker is Leaked
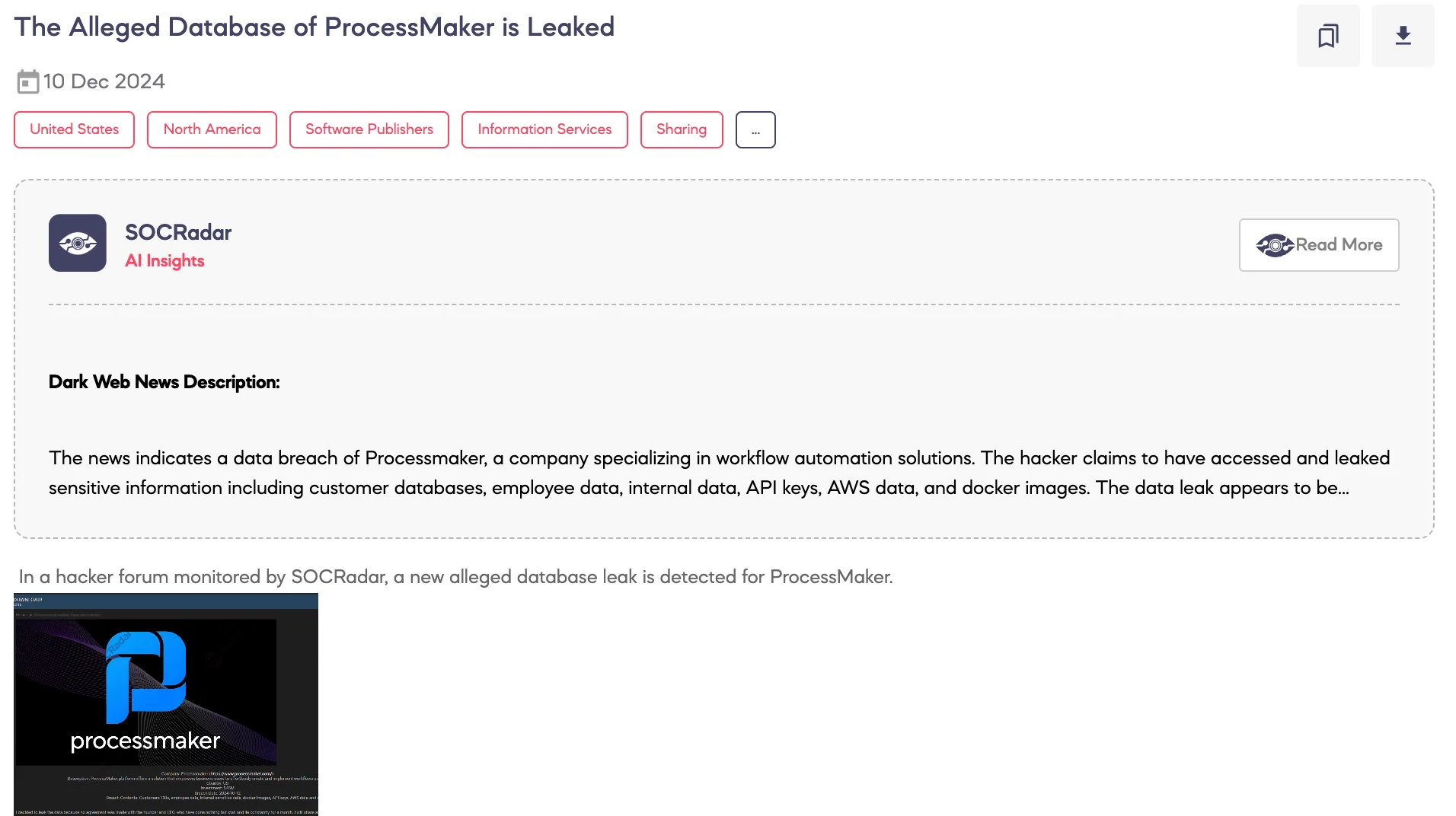
SOCRadar Dark Web Team identified a post on a hacker forum alleging a data breach involving ProcessMaker, a U.S.-based platform specializing in workflow automation solutions.
According to the threat actor, the breach occurred on October 12, 2024, and resulted in the exfiltration of extensive data, including customer databases, employee information, sensitive internal files, Docker images, API keys, and Amazon Web Services (AWS) data. The actor claims the decision to leak the data stems from unsuccessful negotiations with ProcessMaker’s founder and CEO, accusing them of stalling and dishonesty.
The threat actor has announced plans to release at least 30 gigabytes of data daily and provided a detailed list of compromised databases, which include:
- Customer and client-specific databases (e.g., banks, educational institutions, and government entities).
- Internal ProcessMaker systems (e.g., cloud operations, system AI, and performance schemas).
- Various institutional databases from sectors such as banking, education, healthcare, and public administration.
The breach potentially exposes a significant amount of sensitive information across numerous organizations, raising concerns about data security and privacy.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































