
CISA Flags Active Exploitation of Mali GPU Drivers Vulnerability: CVE-2023-4211
In the ever-evolving cybersecurity landscape, adding a vulnerability to CISA’s Known Exploited Vulnerabilities Catalog stands as a significant alarm bell. Recently, a critical vulnerability affecting Mali GPU drivers caught CISA’s attention, emphasizing the active exploitation evidence surrounding this flaw.
The vulnerability on the Mali GPU Driver
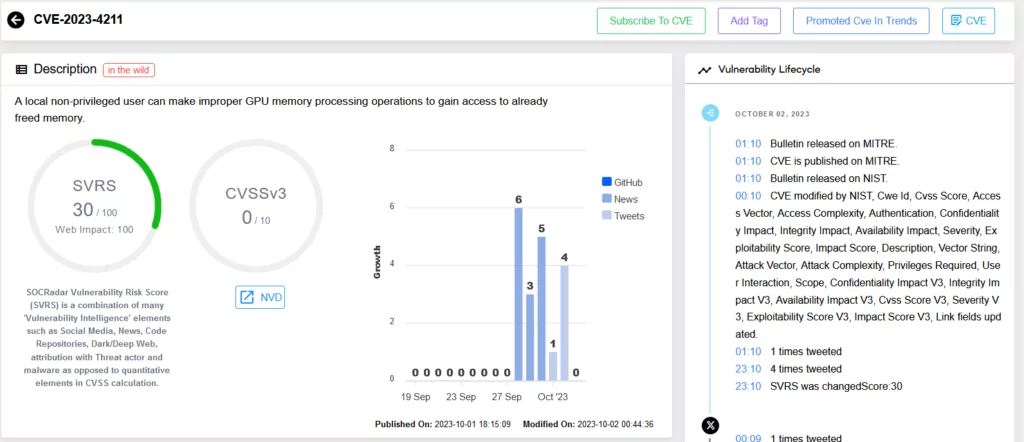
Per Arm’s security advisory today, CVE-2023-4211 enables a local non-privileged user to perform improper GPU memory processing operations, thus accessing already freed memory. At the time of writing, an official CVSS score has not been assigned. Yet, given the active exploitation evidence, the severity cannot be understated.
The Affected Platforms and Resolutions
Arm’s Mali GPU Kernel driver, particular versions, is susceptible to this compromise. To delve into specifics:
- Midgard GPU Kernel Driver: Versions from r12p0 to r32p0
- Bifrost GPU Kernel Driver: Versions from r0p0 to r42p0
- Valhall GPU Kernel Driver: Versions from r19p0 to r42p0
- Arm 5th Gen GPU Architecture Kernel Driver: Versions from r41p0 to r42p0
Given the gravity of the issue, Arm’s advisory indicates fixes in the Bifrost, Valhall, and Arm 5th Gen GPU Architecture Kernel Driver version r43p0. They’ve also highlighted that this vulnerability might be under limited, targeted exploitation, urging users to upgrade if impacted.
Real-world Implications
The vulnerability’s exploitation allows attackers to tamper with device memory data, posing threats to various devices. These include renowned brands like Google Pixels, Chromebooks, and several Linux hardware. Gaining access to system memory no longer in use serves as a launch pad for attackers to insert malicious code, leveraging it to exploit other vulnerabilities or plant malicious payloads, spying on device users. Arm credits the discovery of active exploitations to Maddie Stone of Google’s Threat Analysis Group and Jann Horn of Google Project Zero.
In their advisory, Arm revealed two more vulnerabilities that have since been patched. Both CVE-2023-33200 and CVE-2023-34970 enable a user without elevated privileges to manipulate a race condition, resulting in inappropriate GPU activities that access memory previously released.
SOCRadar Vulnerability Management
Staying ahead in cybersecurity requires proactive intelligence. At SOCRadar, our Vulnerability Intelligence works diligently to keep users informed about such critical vulnerabilities, helping businesses fortify their defenses effectively. As the Mali GPU driver vulnerability unfolds, it is a stern reminder of the necessity of swift action, patching, and staying updated with trusted intelligence sources.

































