
CISA Issues ICS Advisories for Vulnerabilities Affecting Siemens, Schneider Electric, Rapid Software, Horner Automation
CISA has released new advisories concerning security vulnerabilities in Industrial Control Systems (ICS). The focus is on ICS products from Siemens, Schneider Electric, Rapid Software, and Horner Automation. Siemens alone has six distinct advisories, each addressing various ICS equipment. These advisories provide crucial information, prompting users and administrators to carefully review them for suggested mitigations and to promptly secure their ICS environment.
This blog post will particularly highlight critical and high-severity vulnerabilities, those with a CVSS score of at least 8.5, as they typically pose a heightened risk of exploitation.
Siemens SIMATIC Vulnerabilities Could Allow Unauthorized Access, Device Control (CVE-2023-51438, CVE-2023-49621, CVE-2023-49251)
This section outlines vulnerabilities detailed in two CISA advisories dedicated to Siemens ICS products, particularly emphasizing the critical ones. These vulnerabilities impact the critical manufacturing industry, with affected products widely used globally. CISA emphasizes their remote exploitability and low attack complexity. Notably, one of the vulnerabilities reaches the maximum CVSS score of 10.0.
CVE-2023-51438 (CVSS Score: 10.0, Critical): In instances where the Redfish® server is configured for remote system management within default installations of maxView Storage Manager, this vulnerability can lead to unauthorized access.
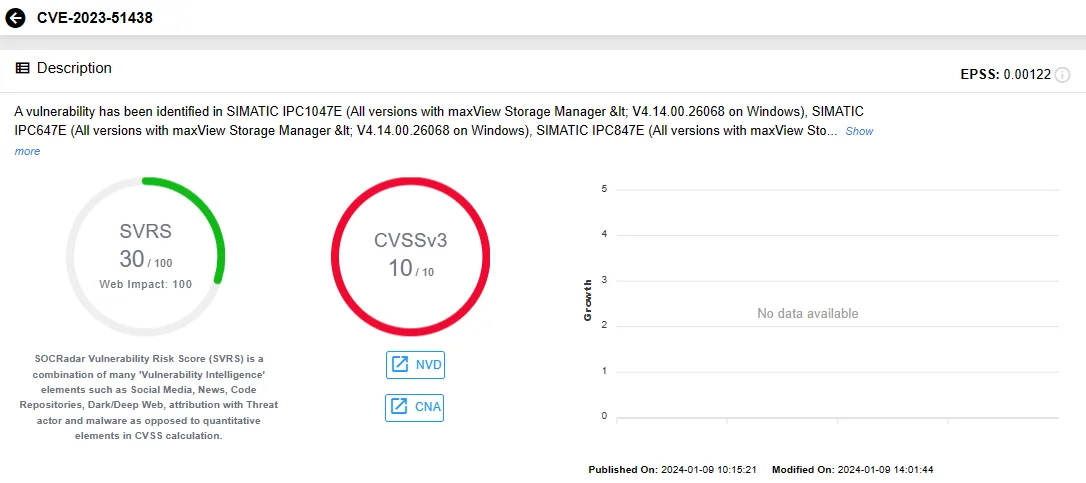
SOCRadar Vulnerability Intelligence: CVE-2023-51438 (Siemens)
The critical vulnerability impacts the following versions of Siemens SIMATIC products with maxView Storage Manager on Windows. Siemens SIMATIC is an ICS product used in the manufacturing industry.:
Affected Siemens SIMATIC products include:
- SIMATIC IPC647E: All versions prior to V4.14.00.26068
- SIMATIC IPC847E: All versions prior to V4.14.00.26068
- SIMATIC IPC1047E: All versions prior to V4.14.00.26068
The vulnerabilities below pertain to another Siemens product, SIMATIC CN 4100, affecting versions preceding V2.7 in the “intermediate installation” system state:
CVE-2023-49621 (CVSS Score: 9.8, Critical): The application uses default credentials with admin privileges. This creates a potential scenario where an attacker could exploit these credentials to gain complete control over the affected device.
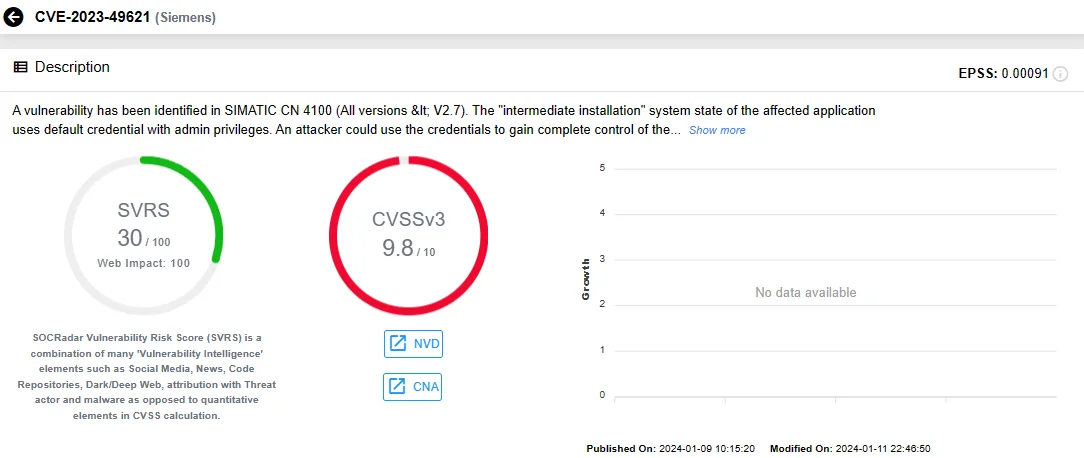
SOCRadar Vulnerability Intelligence: CVE-2023-49621 (Siemens)
CVE-2023-49251 (CVSS Score: 8.8): The application allows an attacker to add their login credentials to the device. Consequently, the attacker could remotely log in as root, maintaining control over the device even after it is fully set up.
Rapid SCADA Vulnerabilities Pose Risks of Unauthorized Access and RCE (CVE-2024-21764, CVE-2024-21852)
Rapid SCADA version 5.8.4 and earlier versions are susceptible to several vulnerabilities, ranging from medium to critical severity. Of particular concern are the following vulnerabilities. It is important to note that these vulnerabilities have low attack complexity and are remotely exploitable.
CVE-2024-21764 (CVSS Score: 9.8): The identified vulnerability arises from the use of hard-coded credentials. Its exploitation may grant unauthorized access to a specific port.
CVE-2024-21852 (CVSS Score: 8.8): This vulnerability leverages a Zip Slip vulnerability in the unpacking routine. Through this, an attacker can introduce a malicious configuration file, achieving Remote Code Execution (RCE).
The severity of these vulnerabilities underlines the necessity for immediate attention and remediation to fortify the security posture of Rapid SCADA installations.
High-Severity Vulnerabilities in Schneider Electric Easergy Studio and Horner Automation Cscape (CVE-2023-7032, CVE-2023-7206)
Schneider Electric faces a significant security concern with a singular high-severity vulnerability impacting Easergy Studio versions preceding v9.3.5. The nature of this vulnerability, coupled with its low attack complexity, accentuates the potential risks associated with it.
CVE-2023-7032 (CVSS Score: 7.8, High): This vulnerability stems from a deserialization of untrusted data. Attackers, operating with user-level account credentials, could exploit this vulnerability to provide a harmful serialized object, consequently gaining elevated privileges within the system.
The Horner Automation advisory also discloses only one high-severity vulnerability, marked by its low attack complexity.
CVE-2023-7206 (CVSS Score: 7.8): This vulnerability affects Horner Automation Cscape versions 9.90 SP10 and earlier. Local attackers can exploit this security loophole by manipulating a user into opening a malicious CSP file, leading to arbitrary code execution.
Recommendations for ICS Security; How Can SOCRadar Help?
In light of the identified vulnerabilities in various ICS products, organizations should adhere to proactive security measures. Here are simple steps to enhance the security of your Industrial Control Systems (ICS) environment:
Update Your Products to Latest Versions:
Ensure prompt updates to the latest versions of your ICS products. This step serves as a proactive defense against potential vulnerabilities, mitigating the risk of cyberattacks.
Visit CISA Advisories:
Visit advisories for information regarding all vulnerabilities and to implement appropriate security measures. In cases where immediate updates are not feasible, the advisories provide mitigation measures for protection.
Embrace Best Practices for Industrial Control Systems:
- Minimize network exposure by isolating control system devices from the internet.
- Implement firewalls to segregate control system networks from business networks.
- Prioritize secure remote access, utilizing robust methods such as VPNs.
Stay Informed and Updated:
Regularly monitor and stay informed about the latest security vulnerabilities affecting your ICS products. Swiftly apply updates to ensure the safety of your systems.
By integrating these recommendations into your cybersecurity practices, you contribute to building a robust and resilient defense against potential threats in the ever-evolving landscape of ICS security.
Furthermore, you can utilize SOCRadar’s Attack Surface Management (ASM) and Vulnerability Intelligence features to fortify your organization against emerging vulnerabilities. Stay one step ahead of potential threats with the following benefits:
Timely Threat Alerts:
Receive proactive and timely alerts on emerging vulnerabilities that may pose a threat to your organization. SOCRadar’s vigilant monitoring ensures you stay informed in real-time.
Vulnerability Intelligence:
Harness the insights provided by Vulnerability Intelligence to monitor trends related to CVEs. Stay updated on the latest developments and potential risks associated with known vulnerabilities.
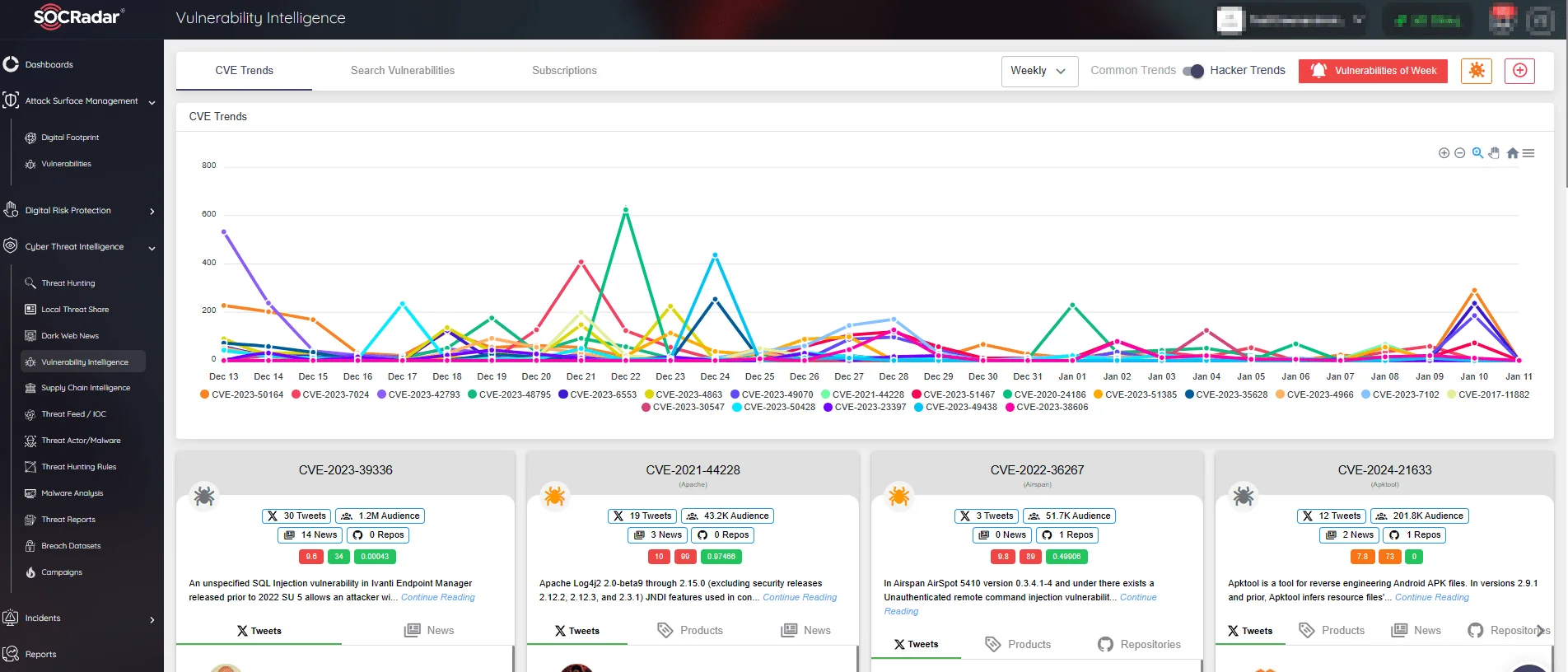
SOCRadar Vulnerability Intelligence’s CVE trends
Detailed Vulnerability Information:
Access comprehensive and detailed information about any known vulnerabilities. SOCRadar’s platform empowers you with the knowledge needed to make informed decisions in managing and mitigating vulnerabilities.
By integrating SOCRadar into your cybersecurity strategy, you gain a valuable ally in navigating the emerging threats. Stay informed, proactive, and resilient against potential risks to your digital infrastructure.




































