
CISA KEV Timeframe Problems While Prioritizing Vulnerabilities
The escalating number of vulnerabilities in the digital landscape demands a vigilant approach from the cybersecurity community. However, merely identifying vulnerabilities is not enough; understanding which ones have been exploited in the wild is crucial for effective defense strategies.
A prominent resource in this quest for threat intelligence is the Cybersecurity and Infrastructure Security Agency’s (CISA) Known Exploited Vulnerabilities (KEV) Catalog. This catalog serves as a valuable guide, meticulously pinpointing vulnerabilities that cunning threat actors exploit to compromise security. It transcends the role of merely identifying weaknesses; rather, it functions as a strategic roadmap for fortifying our defenses.
We know that swift response is imperative when exploitation of a vulnerability within one’s attack surface is detected – prompt action, even in the absence of immediate remediation, can involve implementing certain workarounds. However, a critical question arises: How expeditiously are exploited vulnerabilities incorporated into the KEV catalog?
CISA, in adherence to stringent inclusion guidelines, occasionally introduces delays in the process. This delay, although rooted in the agency’s commitment to accuracy, can hinder organizations’ responsiveness, for those that only rely on the KEV catalog for threat intelligence.
In this blog post, we will explore the intricacies of CISA’s KEV timeframe, the balance between precision of criteria and speed, as well as how it poses a challenge for timely threat intelligence, and how we can overcome this challenge.
CISA’s Role in Documenting and Categorizing Vulnerabilities
CISA’s Known Exploited Vulnerabilities (KEV) Catalog stands as an invaluable repository, catering to the cybersecurity needs of government entities, businesses, and individuals alike. This centralized resource compiles a comprehensive list of security vulnerabilities and weaknesses that malicious actors have successfully exploited. The catalog employs a meticulous organizational structure, categorizing vulnerabilities by vendor, product, date, and detailed descriptions. Furthermore, it provides actionable recommendations, empowering users to stay well-informed and take proactive measures, such as applying software updates and patches, to fortify their systems against potential threats.
While the KEV catalog serves as an indispensable source of information regarding actively exploited vulnerabilities, it is crucial for organizations to recognize its limitations within the broader context of vulnerability management.
Security Implications of KEV Delays
The time delay between real-world exploitation and updates within the KEV catalog emphasizes its function as an indicator that follows cyber threats in the wild. While KEV remains a valuable component in a robust cybersecurity strategy, exclusive reliance on it for vulnerability prioritization introduces specific risks:
- Delayed Response: Relying solely on KEV may result in delayed responses to emerging threats, as the catalog may not immediately reflect the latest exploited vulnerabilities.
- Incomplete Risk Assessment: A singular focus on KEV might lead to an incomplete understanding of an organization’s overall risk landscape, potentially overlooking vulnerabilities that have not yet made it to the catalog.
- Limited Context: KEV provides rather detailed information, but without broader context, organizations might miss critical nuances and dependencies between vulnerabilities, impacting the efficacy of risk mitigation efforts.
In navigating these risks, organizations are urged to integrate KEV within a multifaceted approach, incorporating diverse threat intelligence sources for a more comprehensive and proactive cybersecurity posture.
Factors Contributing to Variations in KEV Catalog Inclusion Timeframe
CISA operates its Known Exploited Vulnerabilities (KEV) Catalog under the directives of BOD-22-01, a Binding Operational Directive specifically aimed at federal executive civilian branch agencies. This directive mandates a heightened sense of urgency in addressing vulnerabilities, with the KEV serving as a curated list that agencies are required to patch on an accelerated timeline.
The criteria for inclusion in the KEV catalog are as follows:
- CVE ID Requirement: A vulnerability must be assigned a Common Vulnerabilities and Exposures (CVE) ID, establishing a standardized identifier for tracking and communication.
- Evidence of Active Exploitation: CISA adds vulnerabilities to the catalog only when there is credible and reliable evidence that the vulnerability has been actively exploited in the wild, indicating a tangible and immediate threat.
- Clear Remediation Guidance: Inclusion in the KEV catalog necessitates the presence of clear remediation guidance, such as a vendor-provided update. CISA’s vigilant team ensures that federal agencies can take swift and effective action to mitigate the identified vulnerabilities.
This stringent framework ensures that vulnerabilities listed in the KEV catalog meet specific criteria, aligning with CISA’s commitment to providing federal agencies with a timely and actionable resource for enhancing cybersecurity resilience.
CISA diligently updates the KEV catalog within 24 hours of confirming evidence of exploitation, provided there is a remediation solution available for the identified vulnerability. Notably, while Proof-of-Concept (PoC) exploit code availability for listed vulnerabilities may be prevalent, it is not a prerequisite for catalog inclusion.
One significant challenge faced by CISA revolves around determining whether a vulnerability is actively exploited in the wild. Despite activities like vulnerability scanning, exploit research, and PoC code availability, these factors alone do not trigger the “in the wild” criteria. CISA acknowledges the impact of publicized PoC code, recognizing that its availability increases the likelihood of exploitation but does not guarantee it.
On average, PoC exploits become available in the wild just 14 days after a vulnerability is publicly disclosed. This timeframe, coupled with the sharing of the exploit code in shadowy corners of the internet and hacker channels, often leads to increased exploit traffic as researchers and attackers seek to use or scan for the vulnerability. However, the spike in traffic is not a sufficient proof of exploitation, as the PoC may not translate into actual exploitation.
However, even if a vulnerability is confirmed to be exploited, CISA may delay its addition to the KEV if there is no clear remediation guidance – or if it does not even have a CVE identifier in the first place. This requirement aligns with the federal government’s use of the KEV, where every entry comes with a due date for patching, emphasizing the importance of swift action.
Given potential delays, organizations are cautioned against relying solely on the KEV catalog for assessing vulnerability exploitation. While KEV offers insights into actively exploited vulnerabilities, alternative resources and tools, such as the Exploit Prediction Scoring System (EPSS) or Threat Intelligence platforms like SOCRadar, are recommended for a more comprehensive and proactive cybersecurity approach.
SOCRadar’s Vulnerability Intelligence, with its detailed timeline of each identified vulnerability, and the Attack Surface Management module, providing real-time alerts about vulnerabilities affecting digital assets, become invaluable assets in navigating the ever-evolving landscape of cybersecurity threats. These features empower organizations to stay informed, proactive, and resilient in the face of emerging vulnerabilities and potential exploitation by threat actors.
Additionally, SOCRadar’s special scoring mechanism, the SOCRadar Vulnerability Risk Score (SVRS), enhances the Vulnerability Intelligence suite. SVRS rates vulnerabilities from 0 to 100, based on their likelihood of exploitation, drawing insights from diverse sources such as social media, news, and the dark web. It also considers connections to threat actors and malware, serving as a crucial tool for teams, aiding in the prioritization of vulnerabilities that demand swift attention and response.
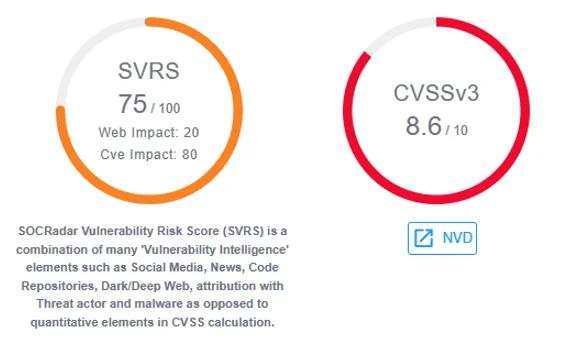
SOCRadar Vulnerability Risk Score (SVRS)
Timeframe Analysis of Vulnerabilities in the KEV Catalog
In an early 2023 VulnCheck research, a comprehensive examination of vulnerabilities added to the CISA KEV Catalog throughout 2022 sheds light on the critical timeframe between the first publicly available exploits of vulnerabilities and their subsequent addition to the catalog.
The research prioritizes the dates of initial publicly known exploits as a reliable metric, as details of exploitation in the wild often lag actual events. Organizations share this information in detailed reports post-incident. Furthermore, a robust public exploit consistently serves as a strong indicator of impending exploitation, as observed repeatedly by researchers.
The accompanying “Time to KEV” graph, encompassing 557 CVEs added to CISA in 2022, delineates the varying timelines for catalog inclusions:
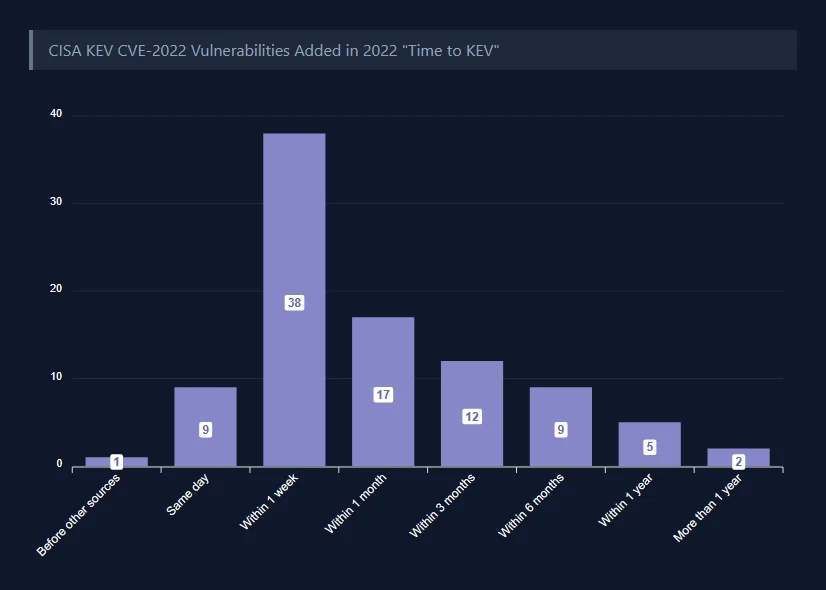
KEV inclusion timeframes for 2022 vulnerabilities (VulnCheck)
11% of KEV entries for CVEs published in 2022 were added on or before the same day as the public release of an exploit or exploitation details. The researchers gave CVE-2022-22047 as an example, where Microsoft’s advisory indicating exploitation in the wild was released on July 12, 2022, and the vulnerability was promptly added to the KEV Catalog within 24 hours.
Approximately 41% of vulnerabilities made their way into the KEV Catalog within a week of public exploit disclosure, exemplified by Fortiguard’s CVE-2022-40684, where Fortiguard’s advisory on October 10 indicated exploitation in the wild, and CISA added the vulnerability to the catalog on October 11.
The remaining 48% of vulnerabilities took more than one week to be added to the KEV Catalog.
The research emphasizes that delays in cataloging vulnerabilities are not solely attributable to CISA. An illustrative example is the Dogwalk vulnerability (CVE-2022-34713), where the first PoC was published in 2020, public reporting indicated exploitation in the wild in early 2022, but Microsoft only addressed the vulnerability and published an advisory in August 2022. CISA swiftly added the vulnerability to KEV post-Microsoft’s advisory, highlighting the complexity and multifaceted nature of such timelines.
In a recent research by journalist Robert Lemos, vulnerabilities identified throughout 2023 further underscore the challenges in timely catalog updates. A use-after-free vulnerability in Adobe’s Acrobat and Reader applications, disclosed by Adobe 10 months prior, saw an exploit developer publishing PoC code on GitHub within a week. CISA, however, added this information to the KEV Catalog almost 10 months later.
Examining the vulnerability card in SOCRadar’s Vulnerability Intelligence reveals that the CVE identifier CVE-2023-21608 was reserved in January 2023; Adobe’s security bulletin for this vulnerability was released in January 23. Upon reviewing the PoC section, you can find that the initial exploit code for this vulnerability became accessible precisely one week later, on January 30.
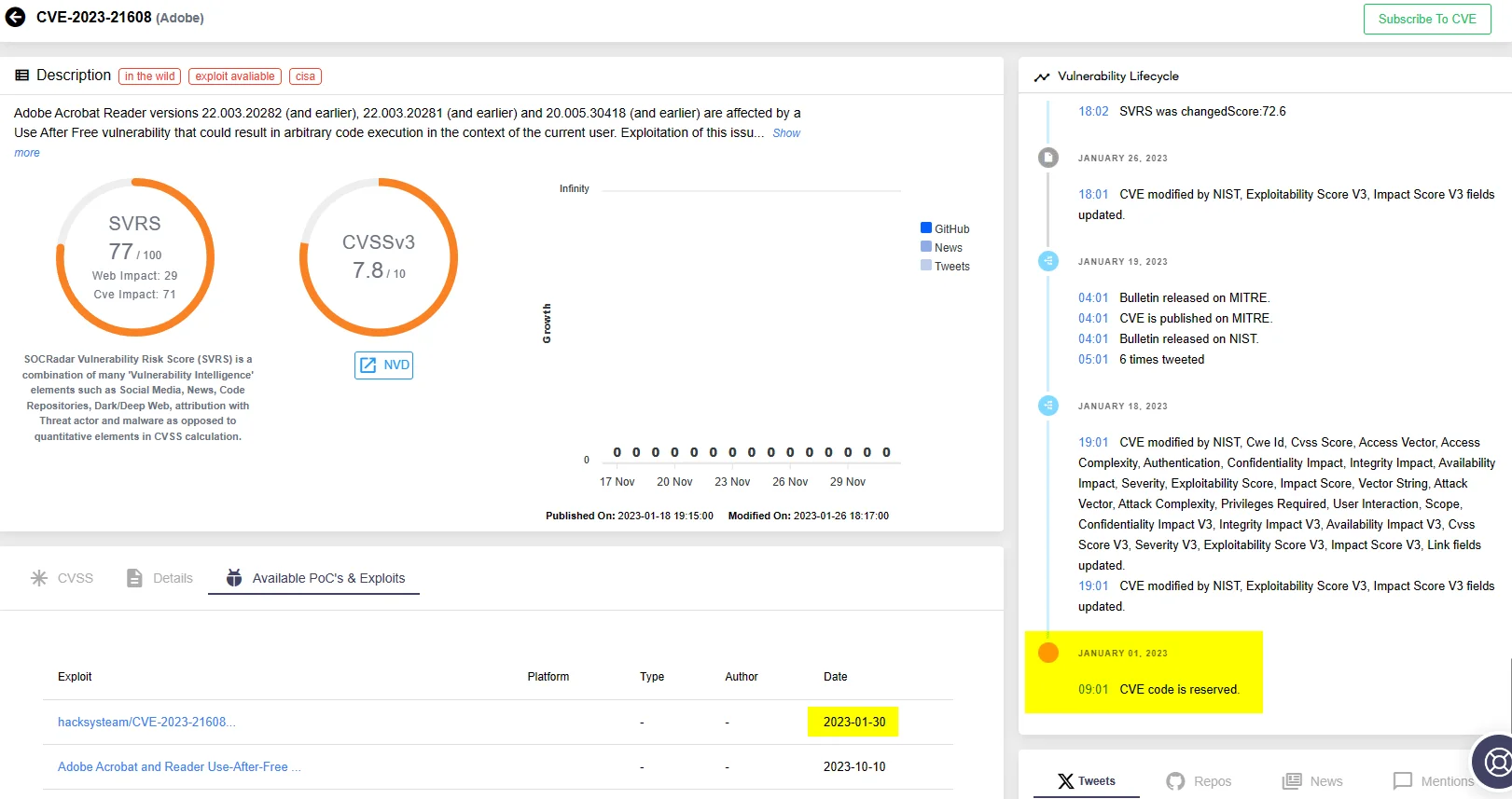
Vulnerability card for CVE-2023-21608 (SOCRadar Vulnerability Intelligence)
Lemos says that, similarly, five issues in Juniper’s EX and SRX series, disclosed publicly in mid-August, were added to the KEV Catalog in November after detection of “exploitation attempts from multiple IPs” by security researchers in late August.
You can stay updated on such news and any mentions of vulnerabilities using SOCRadar’s Vulnerability Intelligence. Let’s search for one of the Juniper vulnerabilities on the platform:
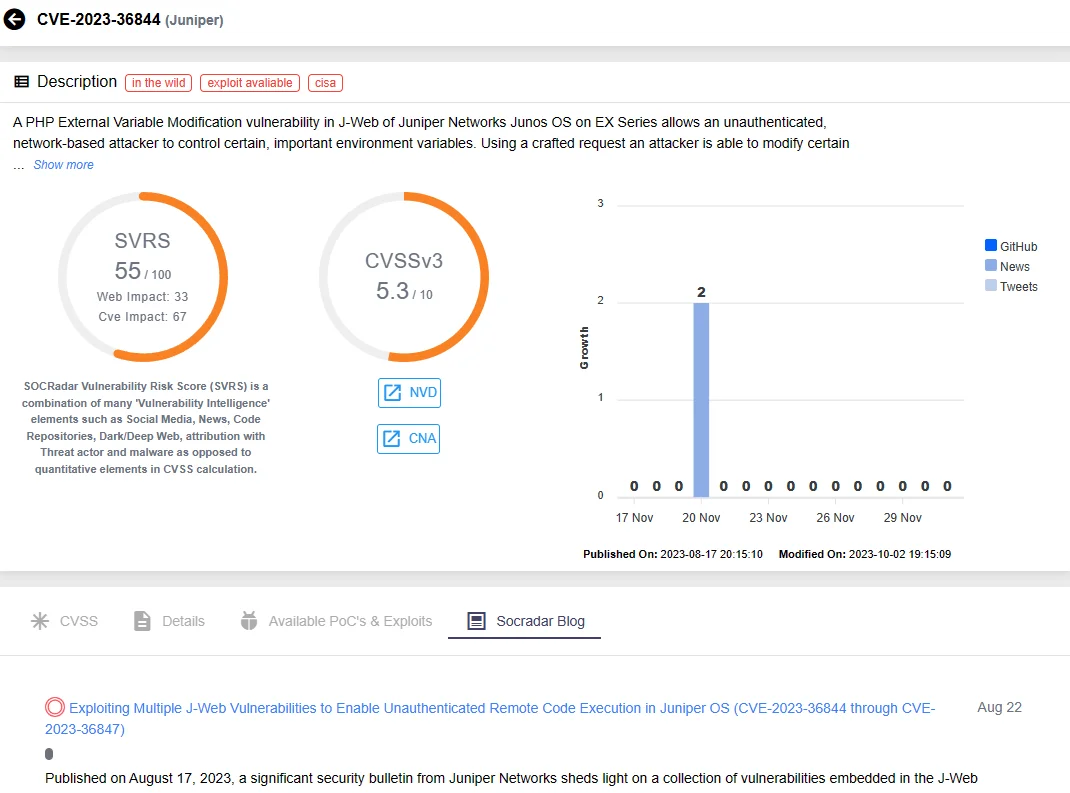
Vulnerability card for CVE-2023-36844 (SOCRadar Vulnerability Intelligence)
Navigate down this page to access the latest Tweets, repositories, news, and mentions related to the vulnerability.
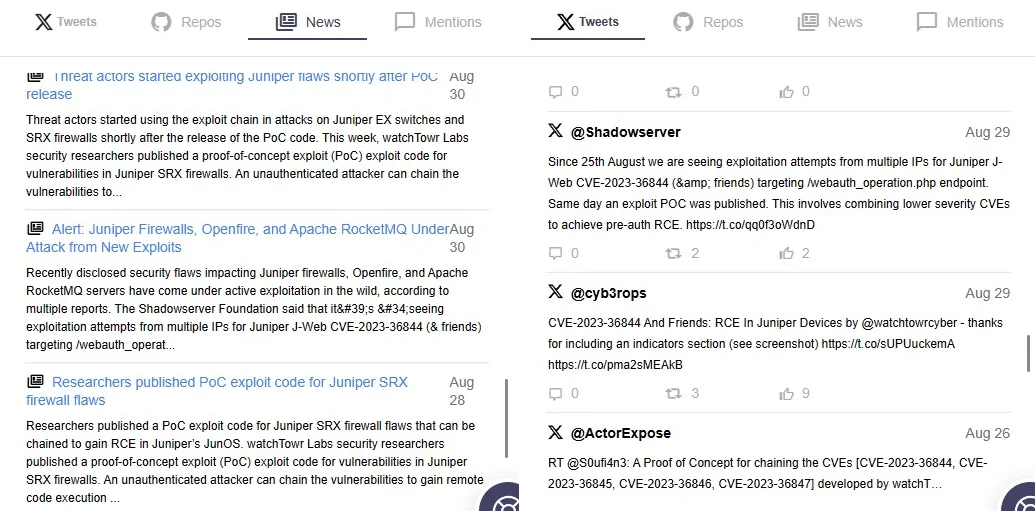
Latest news about the CVE-2023-36844 vulnerability in Juniper
The research also notes a notable delay in incorporating the Veeam Backup & Replication vulnerability. Although disclosed in March and exploited later in the same month, this particular vulnerability was not added to the KEV list until August.
Once more, you can examine the timeline details of the vulnerability using the Vulnerability Intelligence feature:
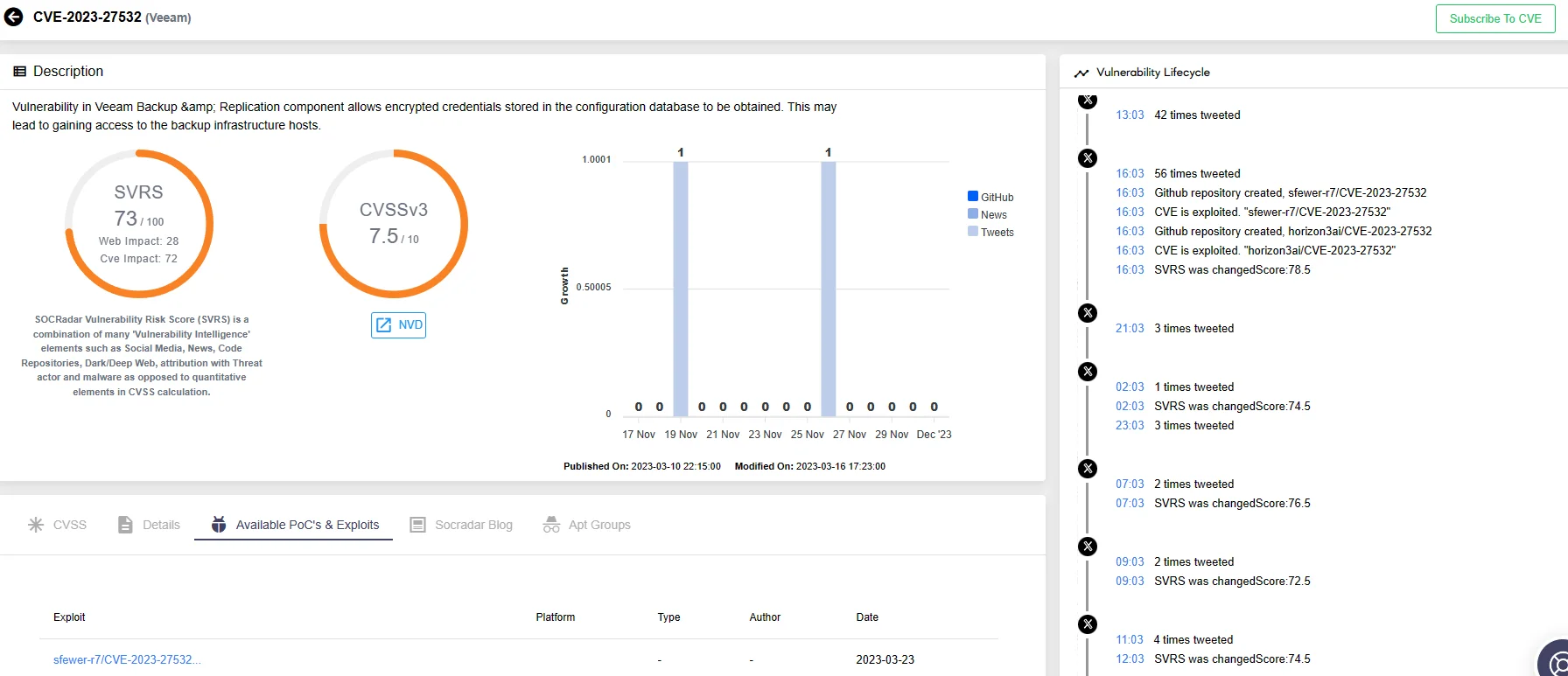
Vulnerability card for CVE-2023-27532 (SOCRadar Vulnerability Intelligence)
These instances highlight the intricate dynamics surrounding vulnerability disclosures, public exploits, and their subsequent cataloging, offering insights into the complexities faced by CISA and the broader cybersecurity community in navigating timely responses to emerging threats.
Conclusion
It is crucial to concentrate on fixing serious vulnerabilities in order to lower the likelihood of cyberattacks. However, the reality is that only a small subset of published vulnerabilities is ever exploited in the wild. To discern which vulnerabilities demand immediate attention, organizations turn to reliable sources that confirm active exploitation.
CISA’s Known Exploited Vulnerabilities (KEV) Catalog stands out as a prominent resource for such crucial information. Yet, it comes with its limitations, particularly when organizations rely exclusively on it for vulnerability management. While KEV remains a valuable component in a robust cybersecurity strategy, its exclusive reliance introduces risks such as delayed response, incomplete vulnerability assessments, and a potential lack of the broader context surrounding the vulnerability.
In navigating these risks, organizations are advised to adopt a multifaceted approach, integrating KEV with diverse threat intelligence sources for a more comprehensive and proactive cybersecurity posture. Threat Intelligence platforms, exemplified by SOCRadar, play a crucial role in this regard.
SOCRadar’s Vulnerability Intelligence provides a detailed timeline of each identified vulnerability, offering insights into when exploitation is observed in the wild and when updates become available. This feature includes comprehensive details such as vulnerability specifics, available Proof-of-Concepts (PoCs), exploits, and mentions. Also, with the SVRS feature, you can gain insights into a vulnerability’s popularity and likelihood of exploitation based on various sources.
Furthermore, SOCRadar’s Attack Surface Management (ASM) module contributes to fortifying an organization’s defenses by delivering real-time alerts about vulnerabilities directly impacting digital assets. This proactive feature, continuously monitoring assets, ensures organizations stay abreast of the latest vulnerabilities and their potential impact. This becomes particularly crucial when threat actors’ activity regarding a vulnerability is on the rise, enabling swift action against potential exploitation.
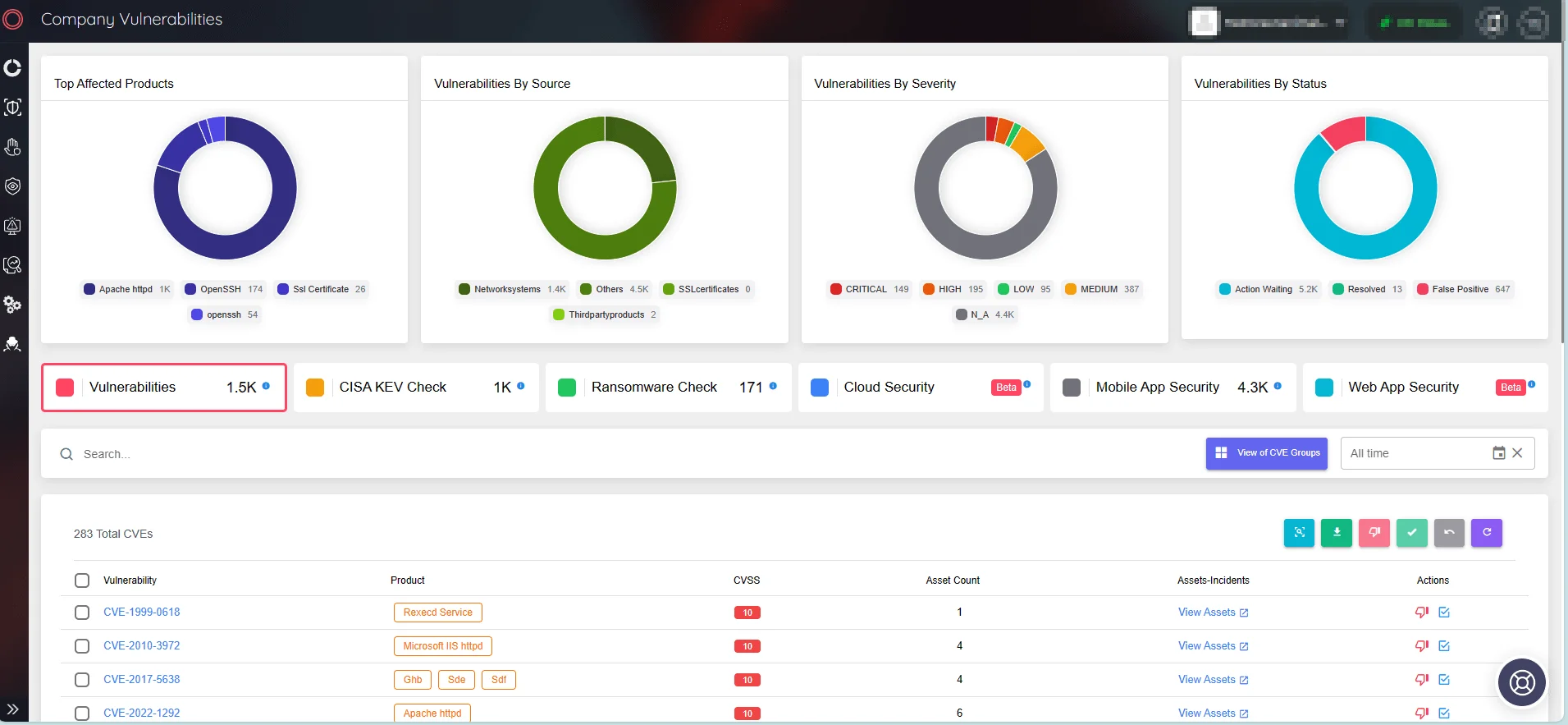
SOCRadar ASM/Company Vulnerabilities
In leveraging SOCRadar, organizations gain the necessary tools and insights to navigate and mitigate emerging threats, fostering a robust and resilient cybersecurity posture in the face of evolving cyber challenges.




































