
Severe Vulnerabilities in Cisco & SonicWall Expose Systems to RCE, DoS, and More: Patch Now
Cisco and SonicWall have recently disclosed a series of critical and high-severity vulnerabilities affecting key network infrastructure and security appliances. The disclosures include unauthenticated Remote Code Execution (RCE) flaws, privilege escalation paths, command injection issues, and other impactful bugs that threaten system integrity and availability.
Cisco’s latest advisories cover a wide range of products, from IOS XE Software and Catalyst Switches to SD-WAN Manager and network orchestration tools, with over two dozen vulnerabilities patched, including two CVEs with a CVSS score of 10.0.
Meanwhile, SonicWall’s SMA 100 series SSL-VPN appliances are affected by post-authentication vulnerabilities that could allow attackers to delete critical files or gain write access to sensitive directories. These flaws pose a serious risk for organizations using remote access technologies.
In this post, we break down the most critical CVEs, identify which systems are affected, and outline what defenders should do next.
Unauthenticated File Upload and RCE Flaws in Cisco IOS XE and Erlang-Based Systems
One of the most urgent vulnerabilities addressed in Cisco’s recent advisories is CVE-2025-20188 (CVSS 10.0), affecting Cisco IOS XE Wireless Controller Software. This vulnerability enables unauthenticated remote attackers to upload arbitrary files and execute commands with root-level privileges, potentially leading to full system compromise.
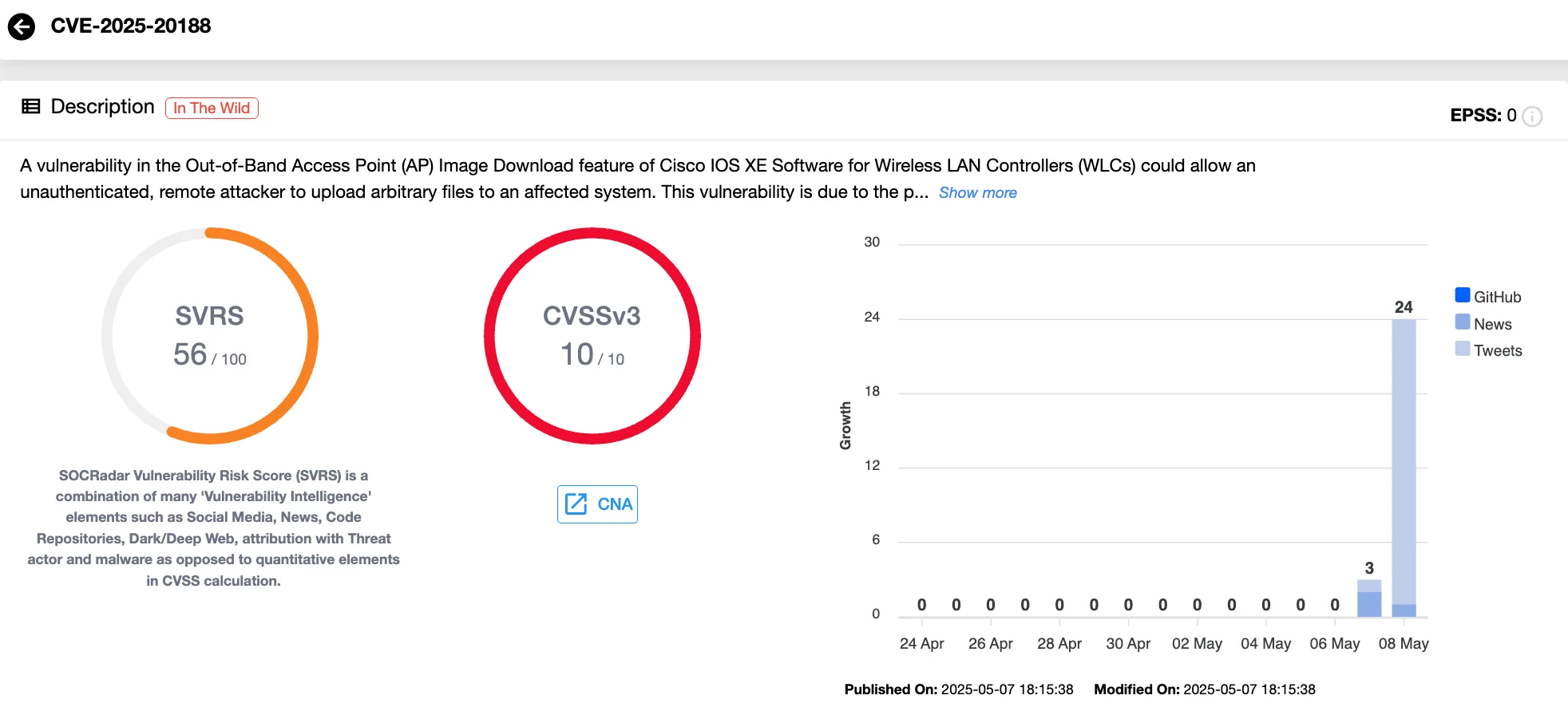
Vulnerability card of CVE-2025-20188 (SOCRadar Vulnerability Intelligence)
The issue lies in a hard-coded JSON Web Token (JWT) tied to the Out-of-Band Access Point (AP) Image Download feature, which is disabled by default. If enabled, however, an attacker can craft malicious HTTPS requests that exploit this feature to perform path traversal and gain complete control over the device.
The vulnerability affects several prominent platforms, including:
- Catalyst 9800-CL Wireless Controllers (Cloud)
- Catalyst 9800 Embedded Wireless Controllers for 9300, 9400, and 9500 switches
- Catalyst 9800 Series Wireless Controllers
- Embedded Wireless Controllers on Catalyst Access Points
Admins can check exposure by running show running-config | include ap upgrade. If the result includes ap upgrade method https, the device is vulnerable and should be patched immediately. There are no workarounds, and Cisco strongly urges affected organizations to update to the fixed software version without delay.
Additional RCE Risk from Erlang/OTP Vulnerability (CVE-2025-32433)
Cisco has also flagged CVE-2025-32433 (CVSS 10.0), a critical Remote Code Execution (RCE) vulnerability in the Erlang/OTP SSH server, which is used in multiple Cisco products. The flaw stems from how SSH messages are handled during the authentication phase and allows unauthenticated attackers to execute arbitrary code remotely.
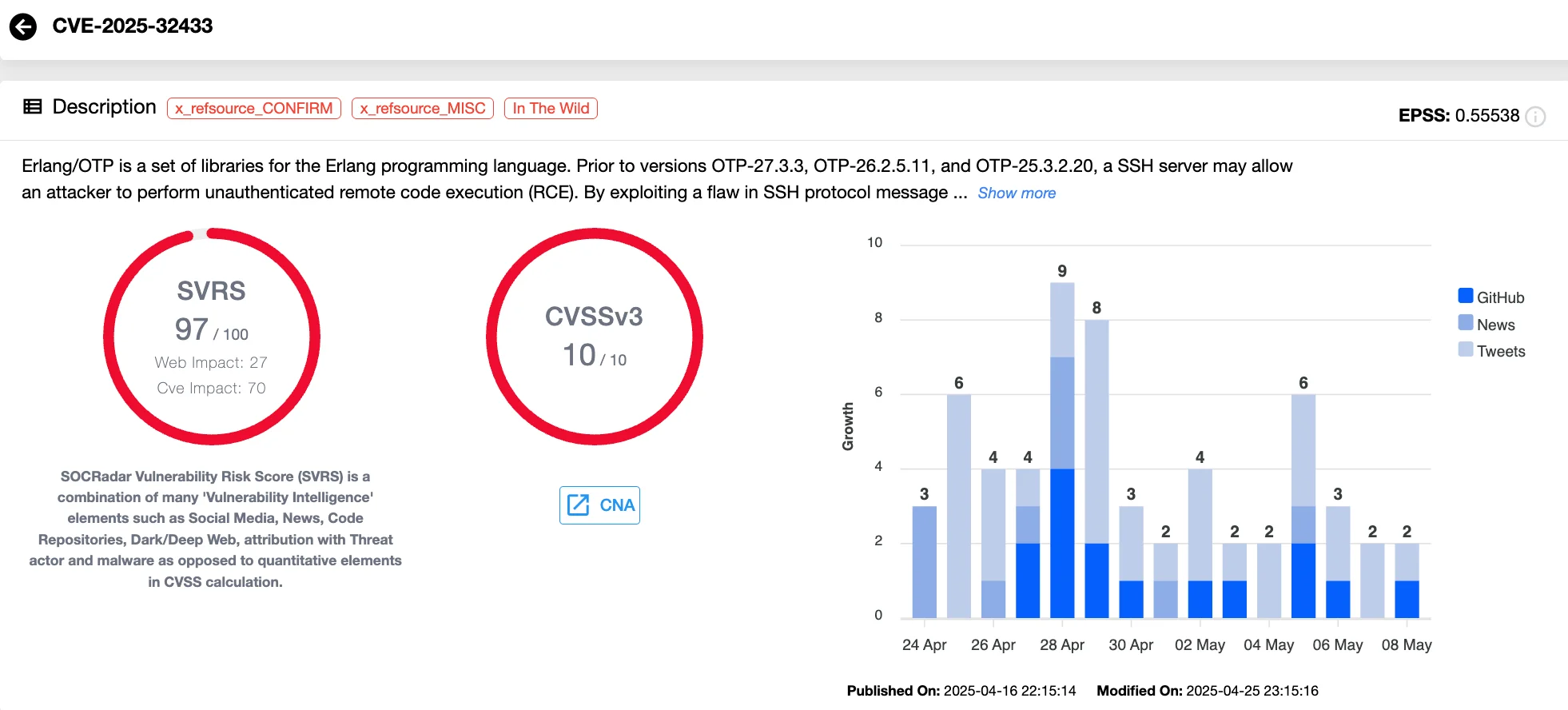
Vulnerability card of CVE-2025-32433 (SOCRadar Vulnerability Intelligence)
Though not all affected systems are vulnerable to full RCE out of the box, depending on configuration, several Cisco technologies are confirmed as impacted. These include:
- ConfD and ConfD Basic
- Network Services Orchestrator (NSO)
- Ultra Cloud Core functions
- Small Business RV Series Routers
- Enterprise NFVIS and iNode Manager
Some of these devices, like the RV Series routers and iNode Manager, have reached end-of-support and will not receive patches. For other products, Cisco has begun rolling out software updates. Since no workarounds are available, patching remains the only reliable form of mitigation. The official Cisco advisory contains the full list of affected products and patch availability timelines.
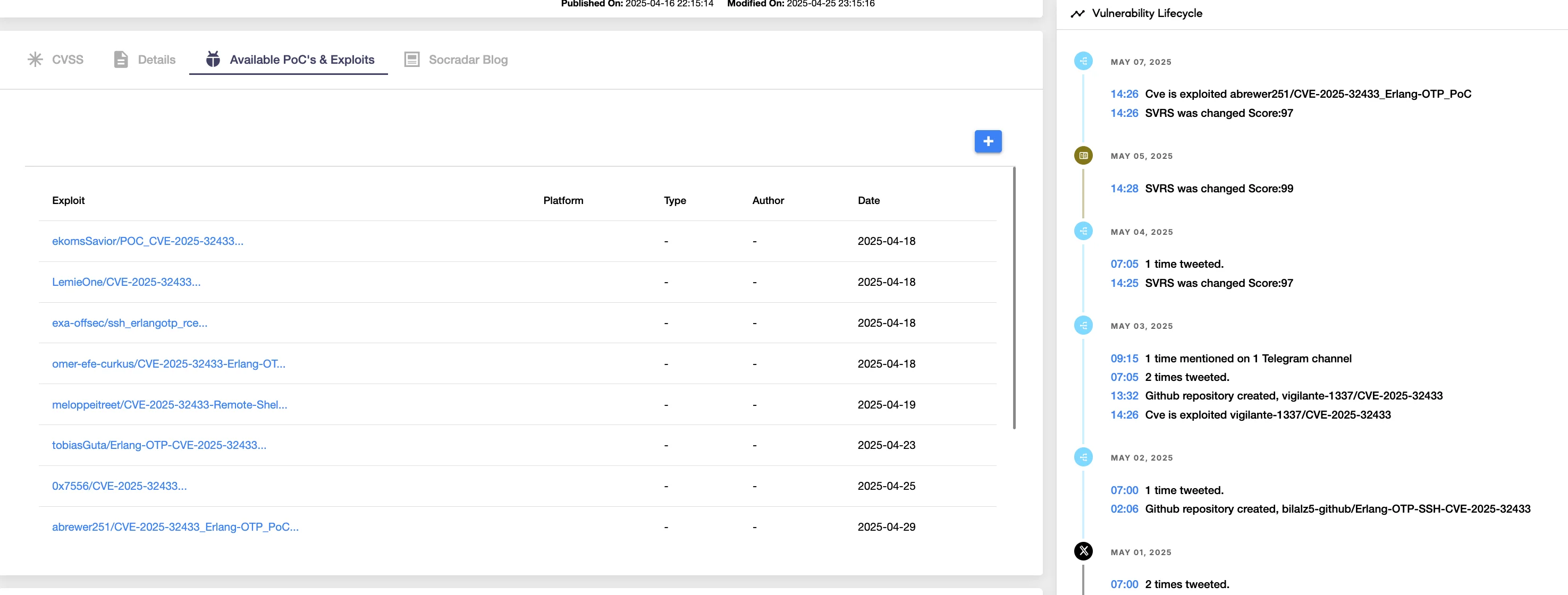
PoC exploits are available for the CVE-2025-32433 vulnerability (SOCRadar Vulnerability Intelligence)
According to the SOCRadar XTI platform, the lifecycle of CVE-2025-32433 has been highly active, with multiple Proof-of-Concept (PoC) exploits released publicly over the past month, amplifying the urgency for organizations to assess exposure and patch quickly.
SOCRadar XTI platform, Attack Surface Management module
With SOCRadar Attack Surface Management (ASM), security teams can gain clarity on what’s exposed, where risk lies, and how to respond – turning unknowns into knowns, and blind spots into actionable insights. SOCRadar ASM supports your organization by:
- Uncovering shadow IT and unauthorized deployments across your digital footprint
- Identifying misconfigured or vulnerable assets before attackers can act
- Sending real-time alerts for exposed services, open ports, and expired certificates
- Continuously tracking changes to your internet-facing infrastructure
High-Severity Cisco Vulnerabilities Span IOS XE, Catalyst, SD-WAN, and More
Beyond the critical RCE flaws, Cisco’s latest advisories include a substantial list of high-severity vulnerabilities that span multiple products and attack surfaces. These bugs could lead to denial-of-service (DoS) conditions, unauthorized access, or privilege escalation, depending on the affected component.
Here’s a list of the high-severity CVEs:
- CVE-2025-20140 – DoS in IOS XE Wireless IPv6 Clients
- CVE-2025-20186 – Command Injection in IOS XE Web Interface
- CVE-2025-20154 – TWAMP DoS in IOS, IOS XE, IOS XR
- CVE-2025-20191 – DHCPv6 DoS in Switch Security Features
- CVE-2025-20122 – Privilege Escalation in Catalyst SD-WAN Manager
- CVE-2025-20182 – IKEv2 DoS in ASA, FTD, IOS, IOS XE
- CVE-2025-20197, CVE-2025-20198, CVE-2025-20199 – Privilege Escalation in IOS XE
- CVE-2025-20192 – IKEv1 DoS in IOS XE
- CVE-2025-20162 – DHCP Snooping DoS in IOS XE
- CVE-2025-20164 – Privilege Escalation in Industrial Ethernet Switches
- CVE-2025-20202 – Cisco Discovery Protocol DoS in WLC
- CVE-2025-20210 – Unauthenticated API Access in Catalyst Center
- CVE-2025-20181 – Secure Boot Bypass in Catalyst Switches
- CVE-2025-20189 – ARP DoS in ASR 903 Routers
As usual, Cisco recommends applying updates promptly and reviewing configurations to minimize exposure.
SonicWall SMA 100 Vulnerabilities Could Lead to File Deletion and Path Control by Attackers
SonicWall has also published a security advisory detailing multiple high-impact vulnerabilities affecting its SMA 100 series SSL-VPN appliances – a widely used remote access solution in enterprise environments.
While these flaws require user authentication to exploit, the risks they pose to system integrity and administrative control are serious, particularly for organizations with misconfigured or weakly secured remote access portals.
Two of the disclosed vulnerabilities are especially concerning due to their CVSS scores over 8.0 and the nature of the access they enable:
- CVE-2025-32819 (CVSS 8.8) allows an authenticated SSL-VPN user to bypass path traversal protections and delete arbitrary files on the device. If key system files are removed, the appliance may reboot to factory defaults, leading to severe disruption.
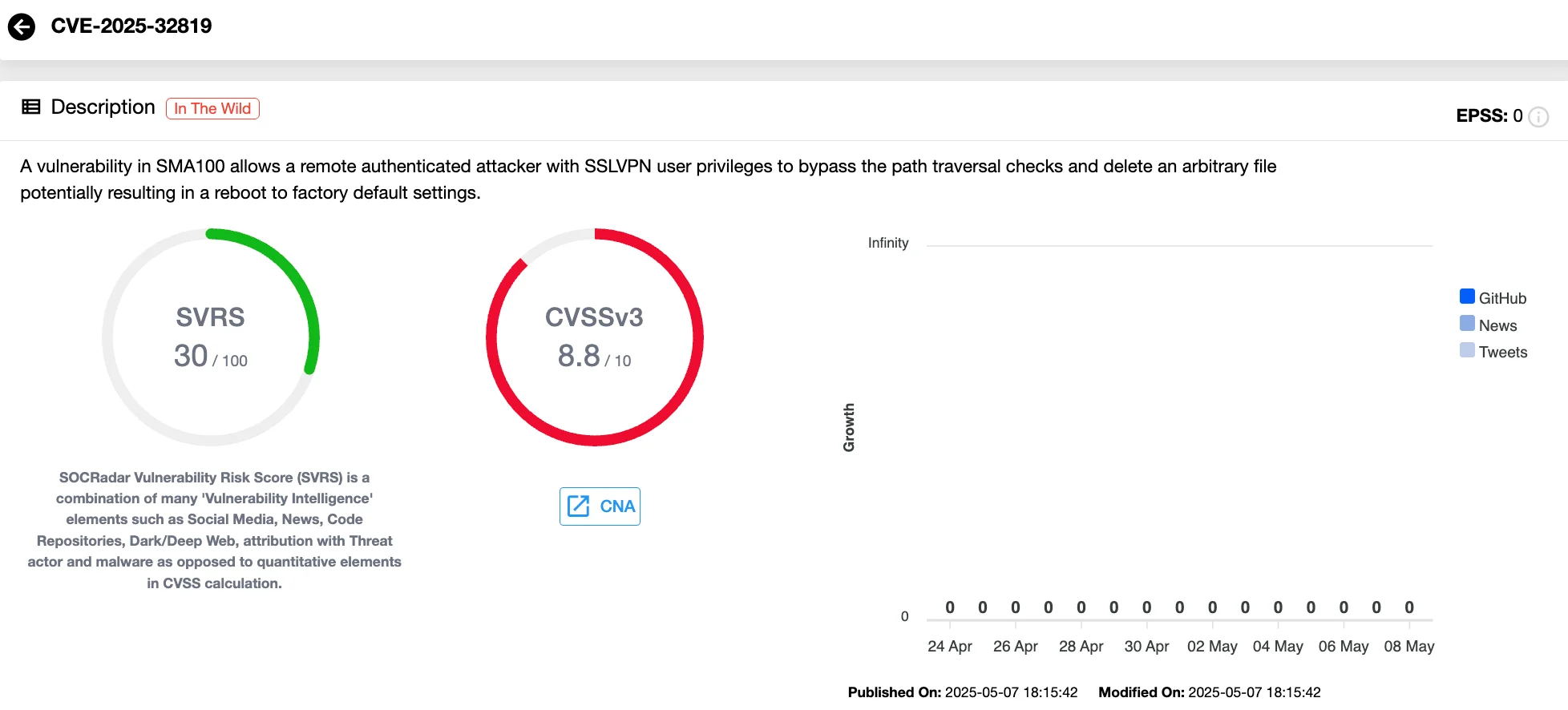
Vulnerability card of CVE-2025-32819 (SOCRadar Vulnerability Intelligence)
- CVE-2025-32820 (CVSS 8.3) permits path traversal that makes any directory writable, effectively giving the attacker the ability to alter critical system areas and potentially escalate access or persistence.
A third vulnerability (CVE-2025-32821) also exists, affecting users with admin-level SSL-VPN access, allowing for remote command injection, though its CVSS score (6.7) places it lower in criticality compared to the others.
SOCRadar XTI platform, Vulnerability Intelligence page
With new vulnerabilities surfacing constantly, it is no longer enough to just track CVEs – you need to know which ones are sought after by attackers. SOCRadar’s Vulnerability Intelligence, offered under the Cyber Threat Intelligence module, helps security teams cut through the noise by delivering:
- Exploit-level insights to identify high-risk vulnerabilities in real time
- Threat actor context to understand who’s behind the attacks and their preferred targets
- Prioritization tools aligned with your organization’s actual technology stack
- Correlated intelligence linking CVEs to malware, campaigns, and TTPs
In fast-moving threat environments, SOCRadar makes sure you’re focused on what’s most urgent, not just what’s most recent.
Affected Products and Remediation Guidance
These vulnerabilities impact all SMA 100 series models, including the SMA 200, 210, 400, 410, and 500v, running firmware versions 10.2.1.14-75sv and earlier.
SonicWall SMA 1000 series appliances are not affected.
To mitigate the risk, SonicWall has released a fixed version (10.2.1.15-81sv) and urges all customers to update as soon as possible. For organizations unable to patch immediately, SonicWall recommends the following interim measures:
- Enable Multi-Factor Authentication (MFA) to reduce the impact of credential compromise
- Activate Web Application Firewall (WAF) protection on the device
- Reset passwords for any users who accessed the appliance through the web interface
The full advisory is available here.
































