
Cleo File Transfer Vulnerabilities (CVE-2024-50623, CVE-2024-55956) – Cl0P’s Latest Attack Vector
[Update] April 8, 2025: “WK Kellogg Confirms Data Breach Tied to Cleo Exploits”
[Update] February 25, 2025: “Cl0p Ransomware Expands Its Victim List with 183 Additional Organizations”
[Update] February 10, 2025: “50 More Companies Exposed”
[Update] January 21, 2025: “Cl0p Ransomware Group Adds 49 More Alleged Victims of Cleo Exploit”
[Update] January 15, 2025: “Cl0P Ransomware Group Intensifies Cleo Attack Extortion Efforts”
[Update] December 30, 2024: “No Connection Between Cleo Flaw and November Breach, Says Blue Yonder”
[Update] December 25, 2024: “Cl0P Ransomware Group Threatens Cleo Data Theft Victims With Public Exposure”
[Update] December 18, 2024: “CISA Adds Cleo CVE-2024-55956 to KEV Catalog”
Recently, vulnerabilities in Cleo’s file transfer software (including Cleo Harmony, VLTrader, and LexiCom) have been actively exploited by cybercriminals. These vulnerabilities, particularly CVE-2024-50623, were discovered to allow unrestricted file uploads and downloads, leading to Remote Code Execution (RCE).
Cleo is a software company specializing in Managed File Transfer (MFT) solutions. Its products, Cleo VLTrader, Cleo Harmony, and Cleo LexiCom, provide secure file transfers, B2B integration, and EDI communications, enhancing data exchange and integration for businesses across various industries.
Although Cleo initially attempted to develop a fix in October 2024, the products remained vulnerable to exploitation, resulting in data theft and widespread attacks. This blog post will outline what happened, the vulnerabilities involved, and what steps organizations must take to secure their systems.
What Happened?
In October 2024, Cleo released version 5.8.0.21 to patch the severe zero-day vulnerability in their file transfer software, CVE-2024-50623, which allowed unauthorized file uploads and downloads leading to Remote Code Execution (RCE). However, security company Huntress later revealed that the patch was incomplete, leaving the products still susceptible to exploitation. It was found that attackers began exploiting this flaw as early as December 3, 2024, using it to upload a Java backdoor that facilitated data theft, command execution, and further network infiltration.
On December 13, CISA confirmed that the vulnerability was being actively used in ransomware attacks and added it to the Known Exploited Vulnerabilities (KEV) catalog. Researchers pointed to the Termite ransomware group as likely behind these attacks, noting the group’s recent targeting of Blue Yonder, a high-profile organization with public-facing Cleo servers.
On the other hand, the Cleo incident is similar to last year’s MOVEit Transfer breaches, raising the possibility that Cl0p is also behind the Cleo attacks. These suspicions were later confirmed when Cl0p posted a statement on their leak site announcing the use of the vulnerability for data theft operations. They also stated that they would delete all data from previous breaches and focus solely on newly compromised victims.
According to researchers, at least 50 Cleo hosts have fallen victim to these attacks.
Attacks Linked to CVE-2024-50623 – Cl0P’s New Target
The exploitation of CVE-2024-50623 has raised significant concerns due to its likely connection with ransomware groups like Termite and Cl0p, both of which have been involved in data theft operations.
Termite was initially suspected of being behind the Cleo attacks, particularly after their recent involvement in a supply chain attack targeting Blue Yonder, a company with public-facing Cleo servers. This attack affected major grocery chains, drawing attention to Termite’s potential use of the vulnerability in Cleo products.
Although Termite was suspected, it has not been fully confirmed whether it was the sole threat group behind the Cleo breaches. However, the exploitation of the Cleo VLTrader, Cleo Harmony, and Cleo LexiCom products for ransomware operations remains clear.
Who openly claimed these attacks was Cl0p, as the notorious ransomware group released a statement on their data leak site, confirming their use of Cleo vulnerabilities for data theft. Cl0p also announced that they would be deleting all previously stolen data from past breaches and would focus solely on new victims from the Cleo exploit.
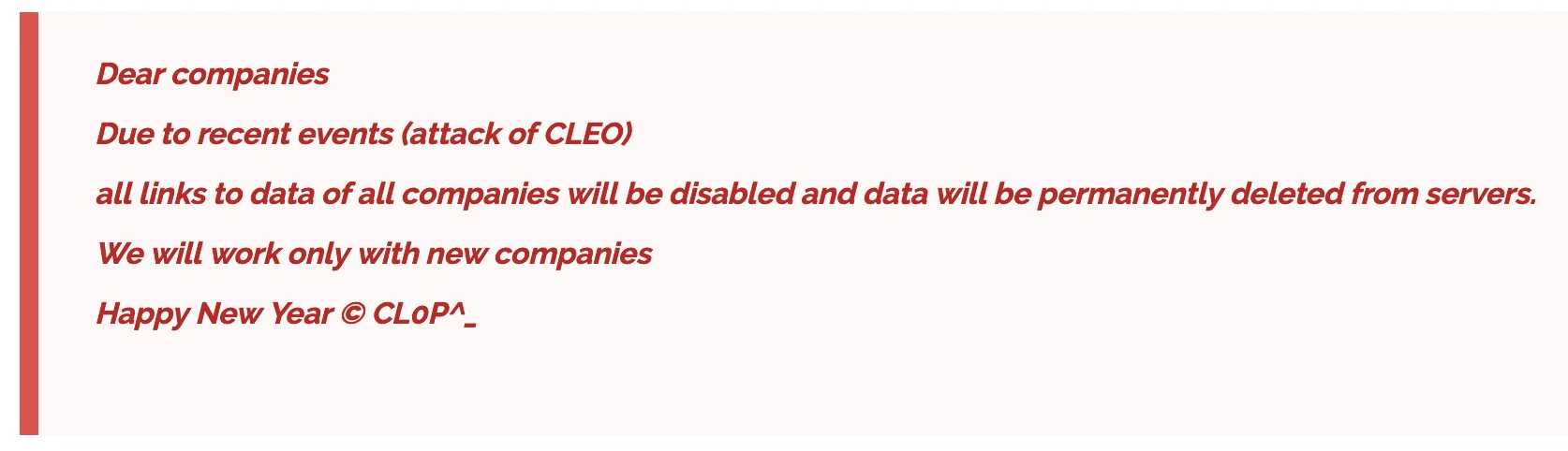
CL0P’s message regarding Cleo attacks
At least 50 Cleo hosts and numerous companies have been affected by the recent exploitation of vulnerabilities in Cleo’s file transfer products, with initial reports confirming at least 10 compromised businesses. This reflects a troubling trend of ransomware groups exploiting file transfer vulnerabilities for widespread data theft and disruption.
For more detailed information on Cl0P ransomware and their activities, check out SOCRadar’s article: Dark Web Threat Profile: Cl0P Ransomware. This detailed resource offers insights into their tactics, techniques, and ransomware campaigns.
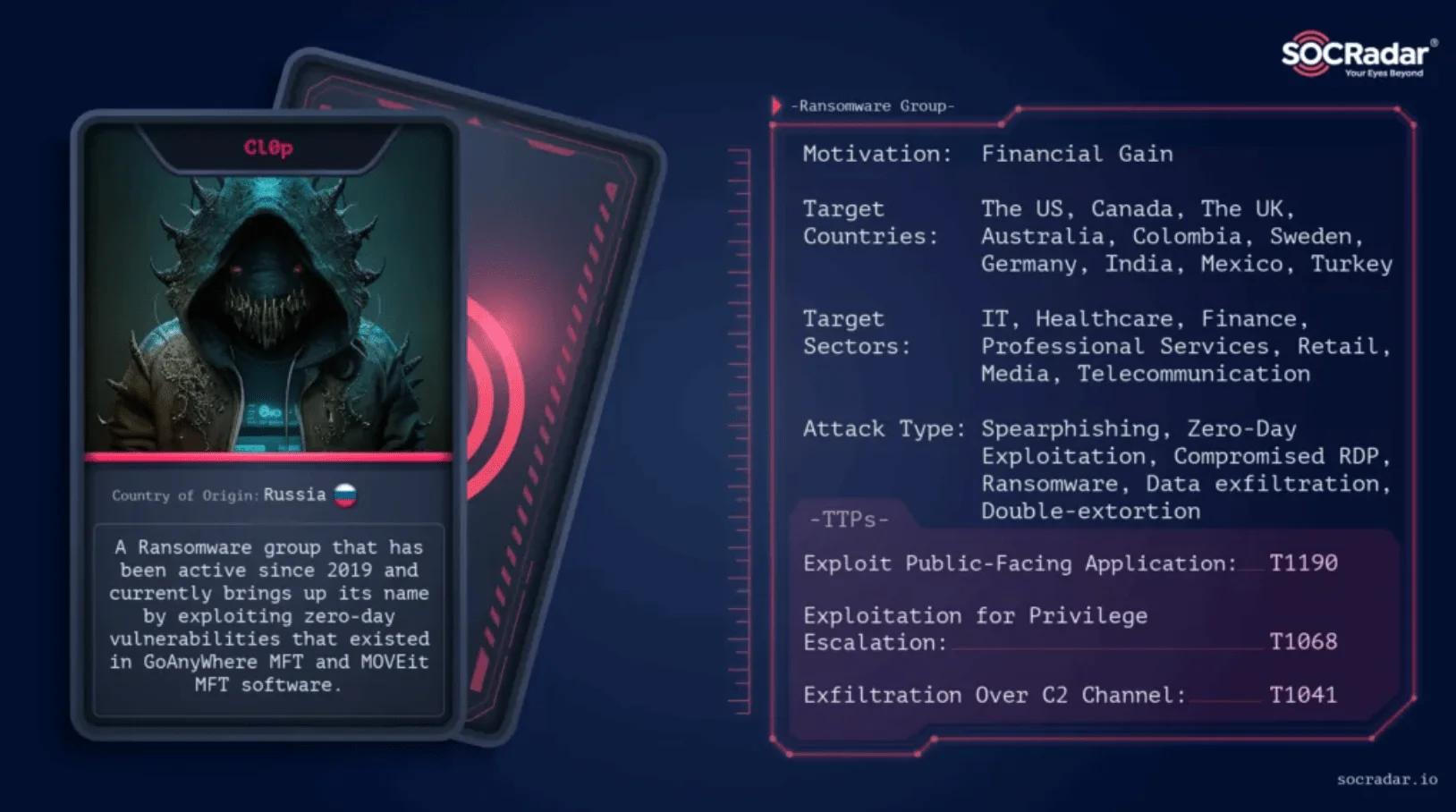
SOCRadar threat actor card: Cl0P Ransomware
What is CVE-2024-50623?
CVE-2024-50623 is a critical zero-day vulnerability found in Cleo’s file transfer software, which allows unrestricted file uploads and downloads. With a CVSS score of 8.8, it enables attackers to achieve Remote Code Execution (RCE).
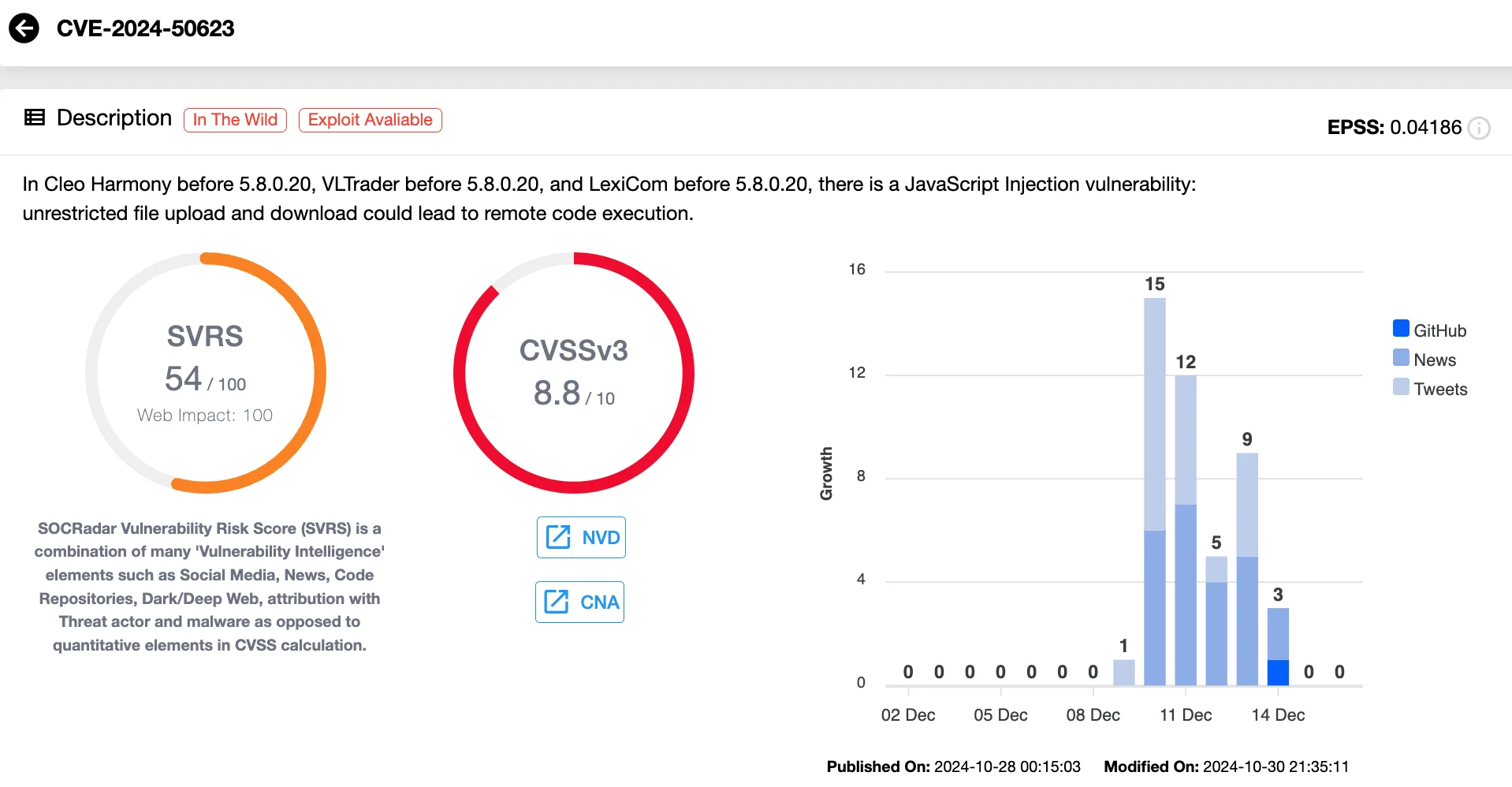
Vulnerability card of CVE-2024-50623 (SOCRadar Vulnerability Intelligence)
The vulnerability arises due to improper handling of file uploads and downloads in the software’s Autorun directory. By leveraging this flaw, attackers can import and execute bash or PowerShell commands without authentication, making it a high-risk security issue. In the attacks observed, the threat actors have attempted to create a reverse shell, allowing them to maintain control over the affected systems.
Reportedly, around 1,342 instances of Cleo’s Harmony, VLTrader, and LexiCom products were exposed to the internet, with the majority (79%) of these instances located in the United States.
The New Critical Vulnerability: CVE-2024-55956
On December 10, another vulnerability, CVE-2024-55956 (CVSS 9.8), was discovered in Cleo’s Autorun directory, complicating the security situation even more.
This flaw is exploited in the same manner, to execute arbitrary bash or PowerShell commands, enabling Remote Code Execution (RCE). In post-exploitation, attackers have deployed modular Java backdoors to maintain access, steal data, and move laterally within networks.
This new, more critical vulnerability, which affects the same Cleo products, has been actively exploited in customer environments, bypassing the patch for CVE-2024-50623.
Identify and Remediate Vulnerabilities Faster with SOCRadar
In today’s fast-paced digital world, staying on top of vulnerabilities is a requirement for any organization. SOCRadar’s Vulnerability Intelligence module equips you with actionable insights to identify, prioritize, and remediate vulnerabilities before they can be exploited by attackers.
SOCRadar’s Vulnerability Intelligence
SOCRadar continuously tracks vulnerabilities across a wide range of sources, from known databases to dark web forums. Our Vulnerability Intelligence module analyzes and correlates this data, providing you with real-time, comprehensive reports on vulnerabilities affecting your environment. With this information, you can quickly assess risk, patch weaknesses, and strengthen your defenses.
Here’s what SOCRadar’s Cyber Threat Intelligence module offers in terms of Vulnerability Management:
- Access to real-time, curated vulnerability data
- Automated risk prioritization based on potential impact
- Actionable insights to streamline remediation processes
- Integration with existing security systems for efficient response
Tackle vulnerabilities with precision and confidence, minimizing the window of opportunity for attackers.
Affected Cleo Products and Versions
These vulnerabilities affect several versions of Cleo’s file transfer software, leaving the following products exposed to exploitation:
- Cleo Harmony (before 5.8.0.24)
- VLTrader (before 5.8.0.24)
- LexiCom (before 5.8.0.24)
Cleo initially addressed CVE-2024-50623 in October 2024 by releasing version 5.8.0.21. However, security researchers pointed out that this patch was insufficient, leaving systems still vulnerable to exploitation. The patch to address CVE-2024-50623, and its patch bypass, was released in version 5.8.0.24.
How Attackers Exploit CVE-2024-50623: Proof of Concept (PoC) Exploit
Researchers have released a Proof-of-Concept (PoC) exploit (available on GitHub) that demonstrates how attackers can exploit the vulnerable /Synchronization endpoint to either read or write files on a compromised server.
- Read Action: The attacker can retrieve files from the server by sending a specially crafted request to the vulnerable endpoint.
- Write Action: The attacker can upload files to the server, exploiting the lack of file validation in the vulnerable system.
The PoC shows how attackers can leverage a weak file access control mechanism, enabling unauthorized file access and potentially allowing the execution of malicious code if an attacker uploads executable files.
CISA Adds CVE-2024-50623 to the Known Exploited Vulnerabilities Catalog
On December 13, 2024, CISA confirmed that the critical vulnerability CVE-2024-50623, affecting Cleo Harmony, VLTrader, and LexiCom file transfer software, is actively being exploited, prompting its addition to the Known Exploited Vulnerabilities (KEV) catalog.
The deadline for compliance is set for January 3, 2024, by which time all affected federal organizations must implement the necessary patches and security measures.
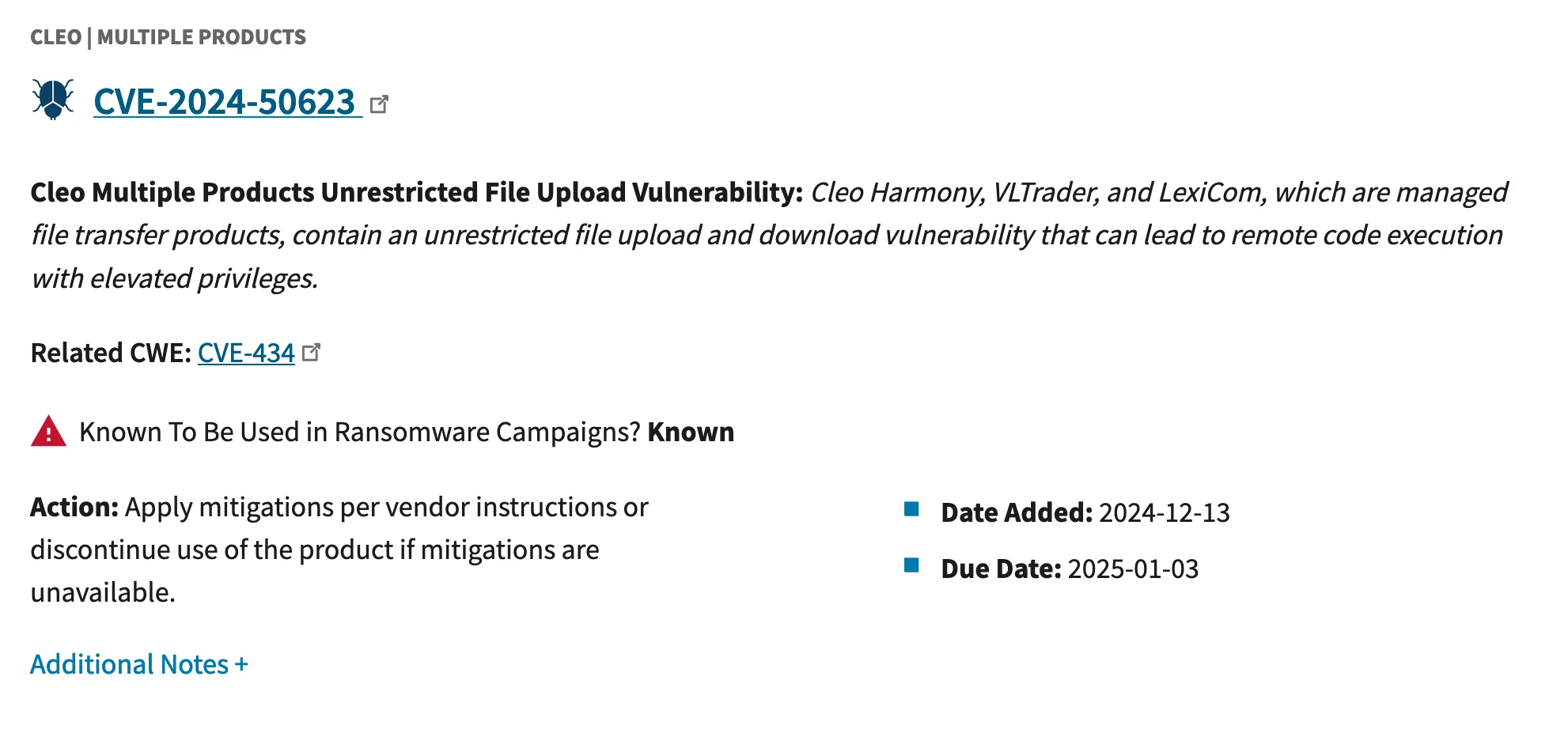
CVE-2024-50623 has been listed in CISA KEV
CISA Adds Cleo CVE-2024-55956 to KEV Catalog
In a new alert, CISA has announced the addition of CVE-2024-55956 to the Known Exploited Vulnerabilities (KEV) catalog, due to active exploitation by ransomware threat actors. This follows closely behind CVE-2024-50623, which was initially added to the KEV catalog on December 13.
CISA urges organizations to apply patches for CVE-2024-55956 by the compliance deadline of January 7, 2025.
Reports of Exploitation; What is Malichus Malware?
Reports from cybersecurity firms such as Huntress, Rapid7, and Sophos confirm that CVE-2024-50623 is actively being exploited across various organizations. Attacks were observed against approximately 1,700 servers, with 10 businesses reporting compromised systems. These attacks were facilitated by the vulnerability, which allowed attackers to bypass security measures and gain unauthorized access to vulnerable servers.
The Java-based malware payload dropped during these attacks was dubbed Malichus. According to researchers, this malware is part of a larger post-exploitation framework, specifically designed for file transfers, command execution, and network communication. Initially detected on Windows devices, Malichus also supports Linux systems, making it a versatile tool for threat actors.
The retail industry is the most affected by these breaches, but others such as food, trucking, and shipping are also affected. The majority of affected organizations are based in North America, particularly the United States.
Researchers also reported seeing post-exploitation activities such as reconnaissance and other tactics for stealing sensitive data. These activities point to the attackers’ ultimate goal of data theft, which they intend to carry out using compromised Cleo systems.
Cl0P Ransomware Group Threatens Cleo Data Theft Victims With Public Exposure
A new update has emerged regarding the Cleo data theft attacks, with the Cl0P ransomware group escalating their threats. After exploiting vulnerabilities in Cleo, the notorious group has ramped up pressure, issuing an urgent demand to numerous organizations they claim have been compromised. They’ve made it clear that these companies must act swiftly or face severe consequences.
The ransomware gang has stated that they possess data from many companies using Cleo, and their teams are actively reaching out to initiate ransom discussions. To further pressure the targets, the group has provided email addresses for companies to verify whether their data has been compromised, urging them to respond quickly.
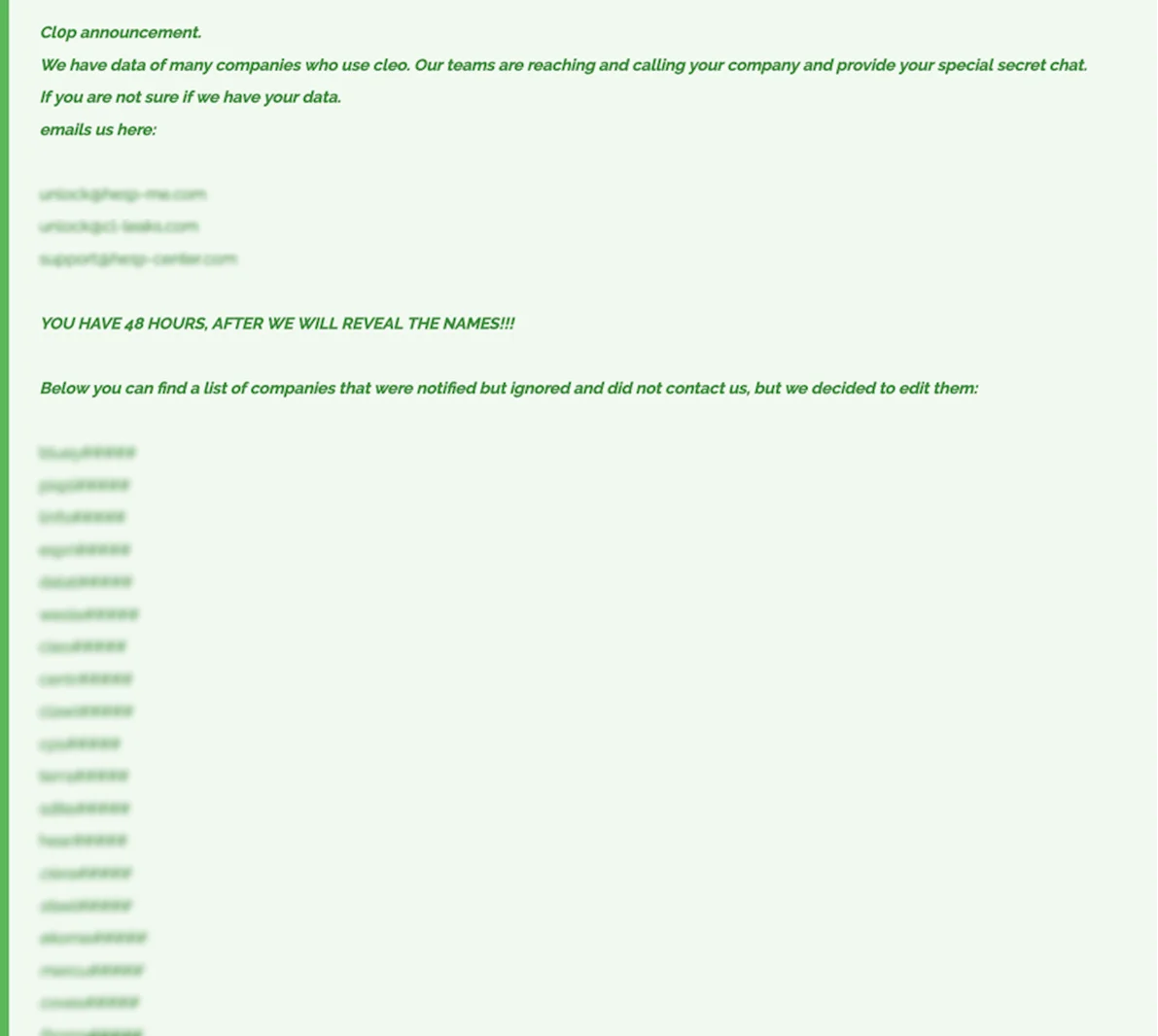
New announcement from Cl0P ransomware lists numerous victims from Cleo data theft attacks
So far, Cl0P has published a list of 66 companies they claim to have breached, though the full names of these organizations remain undisclosed. The group states that they’ve already contacted these companies directly, offering secure communication channels for ransom negotiations.
The threat group has set a 48-hour deadline for ransom negotiations, starting from the time of their announcement. They’ve warned that failure to comply will result in the public exposure of the full names of the affected companies.
It is also important to note that, as the companies listed have yet to engage with Cl0P following their outreach, there is a possibility that other organizations may be affected but are not yet included in the current list.
No Connection Between Cleo Flaw and November Breach, Says Blue Yonder
Blue Yonder is investigating claims made by the Cl0P ransomware group, which linked its recent data theft attacks to a zero-day vulnerability in Cleo. In a statement released on Christmas Eve, Cl0P alleged that it stole data from Blue Yonder, alongside other companies, using this vulnerability. However, Blue Yonder has since emphasized that there is no evidence connecting this new claim to the November ransomware attack, which was attributed to the Termite ransomware group.
Blue Yonder evaluates that the earlier breach, which disrupted services at Starbucks and BIC, is unrelated to the Cleo exploit. As the investigation continues, Blue Yonder assures customers that updates will be provided as new information becomes available.
Cleo, similar to MOVEit, GoAnywhere, and Accellion, is a key player in data transfer operations that has been targeted by Clop. According to the threat group’s claims, 66 organizations have been affected; despite this, Blue Yonder is still the only fully identified victim in Clop’s latest data leak.
Cl0P Ransomware Group Intensifies Cleo Attack Extortion Efforts
The Cl0P ransomware group has released two significant announcements as part of its ongoing extortion campaign targeting organizations allegedly impacted by the Cleo data theft attacks.
New List of Targeted Organizations
In its latest update, Cl0P published the names of several companies, claiming they had been “notified” but failed to respond to their demands. The list includes previously mentioned companies like Blue Yonder and Cleo, among others. The group has threatened that if these companies do not initiate contact by Friday, January 17, their stolen data will be exposed the following day, Saturday, January 18.
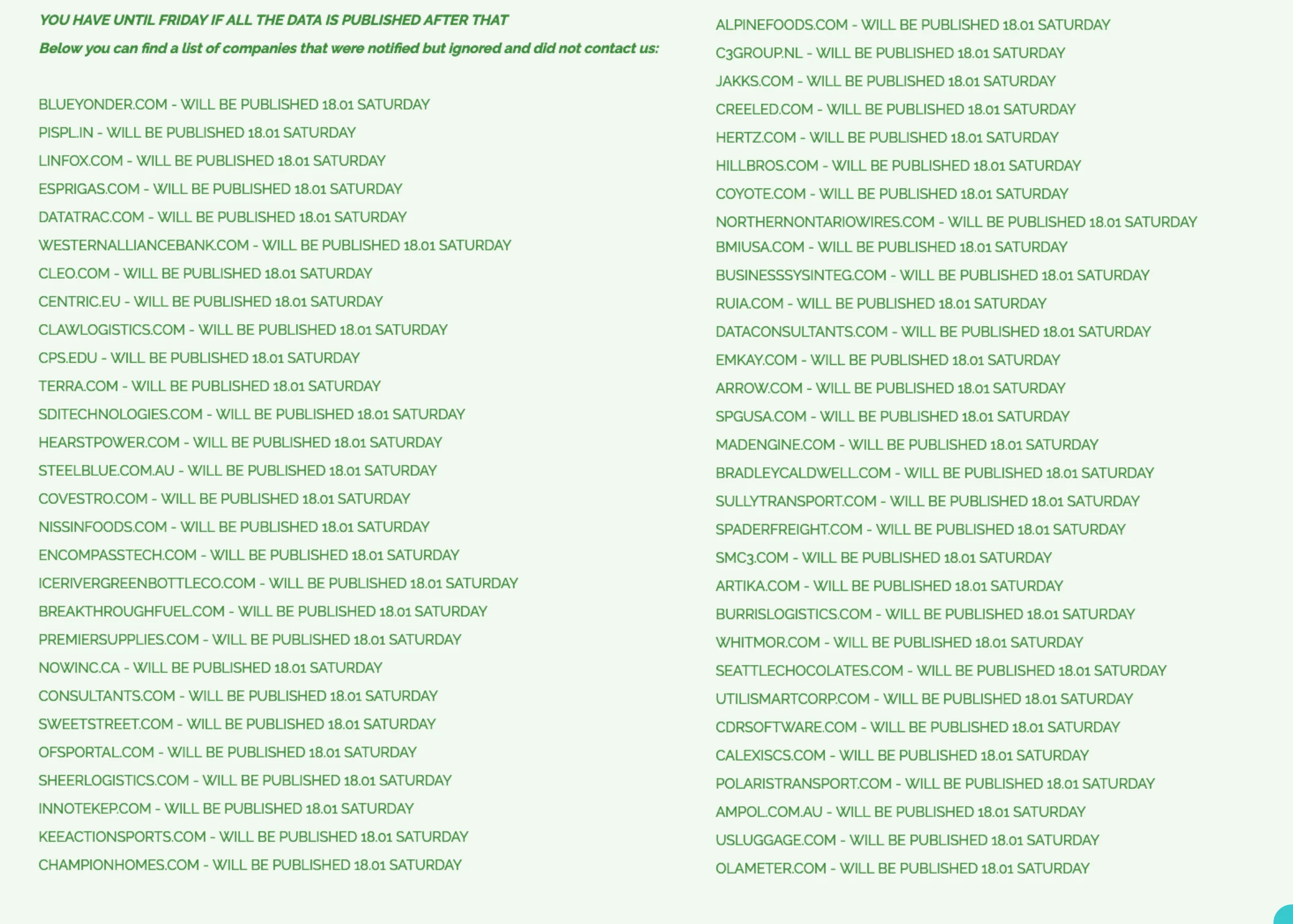
The alleged victim listing of Cl0P Ransomware
Further Threats
In a separate announcement, Cl0P indicated that a new list of companies is set to be released, with partial exposure planned for January 21. This move suggests that the ransomware group will continue its recent tactic of revealing partial lists to pressure victims into compliance – by incrementally building up their extortion campaign, the threat actors aim to maximize the psychological and reputational pressure on affected organizations.
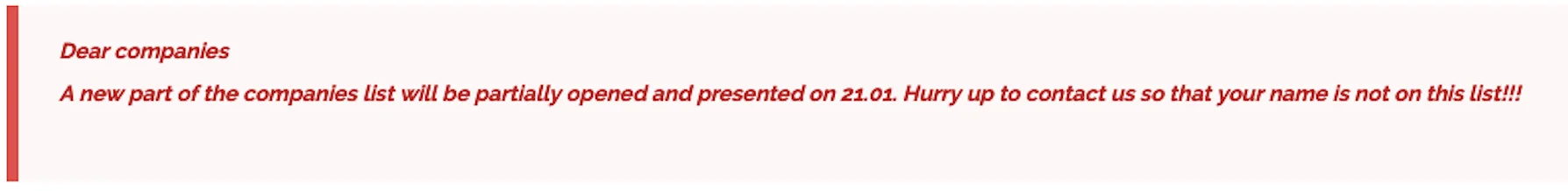
The threat group claims that there will be a new partial announcement soon
Cl0p Ransomware Group Adds 49 More Alleged Victims of Cleo Exploit
Cl0p ransomware has escalated its extortion campaign, publishing claims of 49 additional companies allegedly breached through the exploitation of Cleo software vulnerabilities. As part of their ongoing strategy, the threat actors released partial names of these organizations, a tactic used to pressure victims into engaging with their ransom demands.
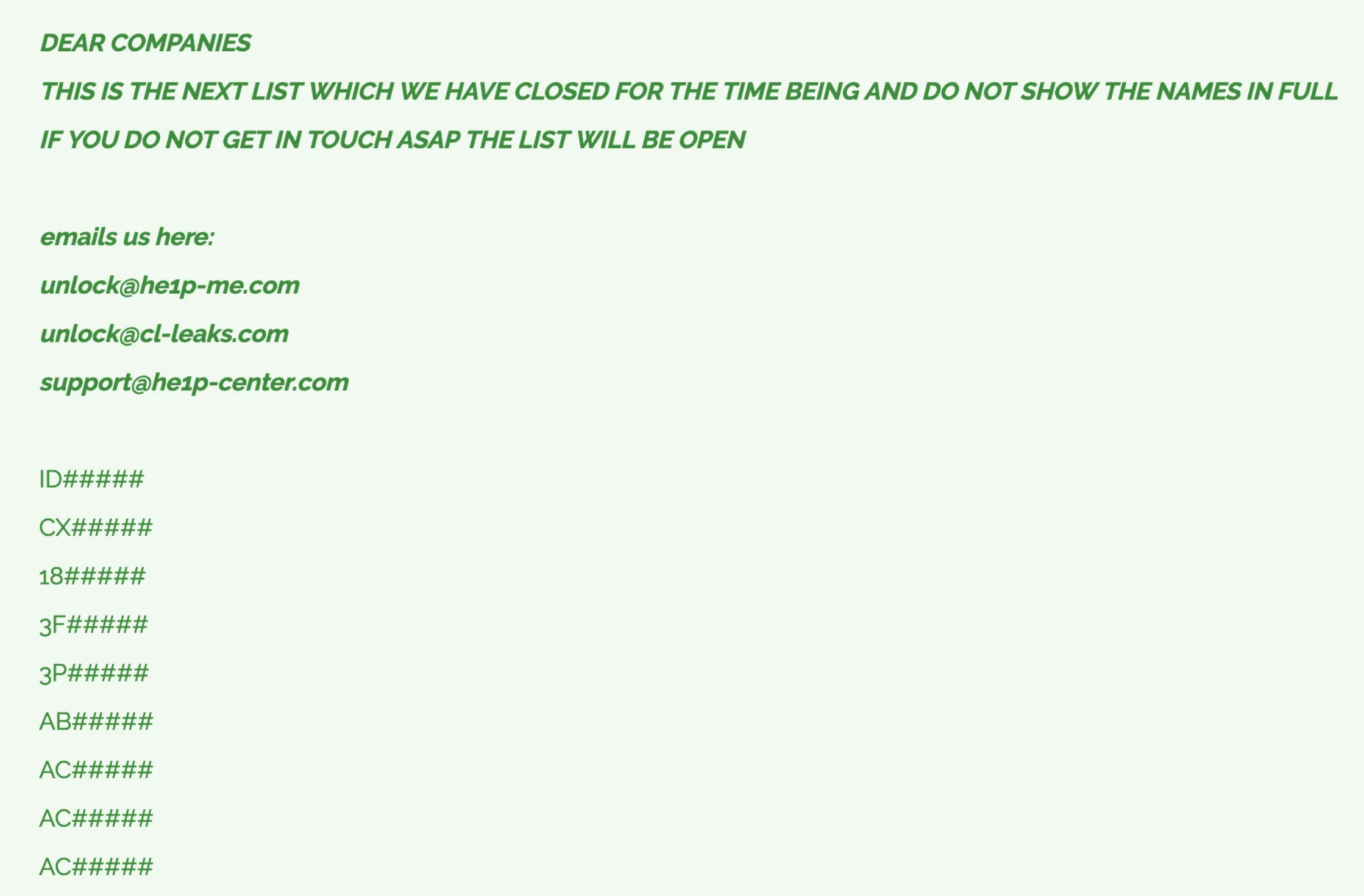
Cl0P has just released partial names for 49 more companies, allegedly breached
This latest update reinforces Cl0p’s established approach of leveraging public exposure as a means to compel organizations to initiate contact. By publishing partial lists, the group intensifies the pressure on affected companies, threatening to reveal more information or data if demands remain unmet.
Organizations allegedly targeted are advised to review their security measures, particularly around Cleo software vulnerabilities, and assess any potential exposure. Proactive communication with law enforcement and cybersecurity experts is essential to navigate this threat.
50 More Companies Exposed
Cl0p ransomware continues to expand its list of alleged victims following the Cleo hacks, most recently revealing 50 more names, listed alphabetically from C to E. The listed companies span a wide range of industries, including technology, food distribution, retail, and logistics. Notable sectors represented include IT services, consumer health, and outdoor equipment.
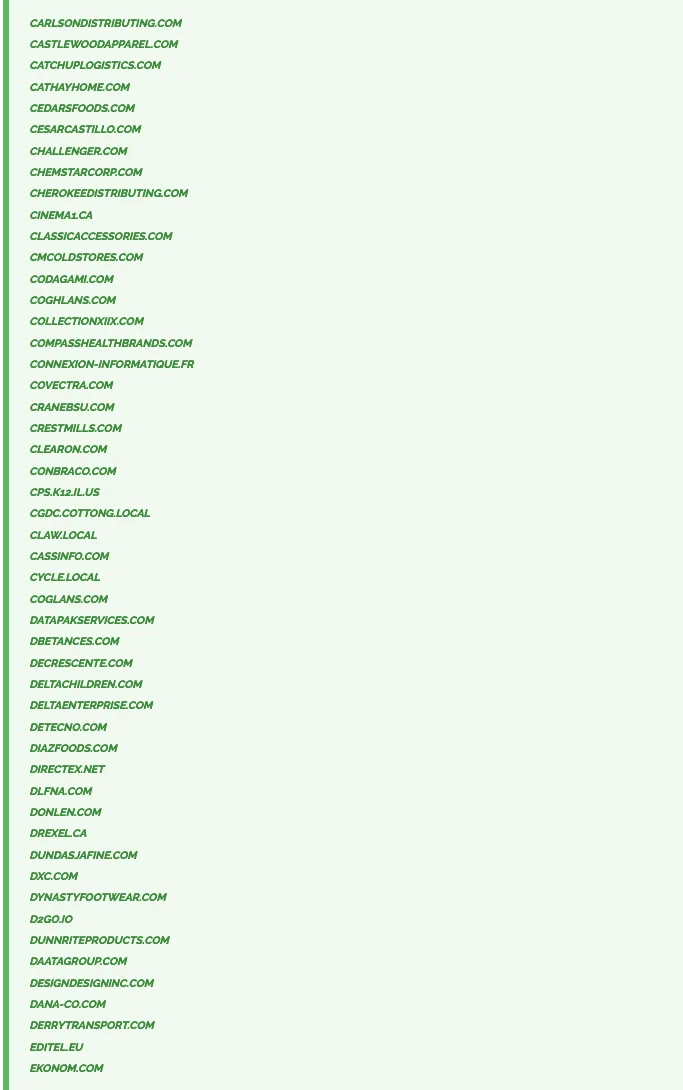
50 more companies were revealed
Cl0p Ransomware Expands Its Victim List with 183 Additional Organizations
Cl0p ransomware has expanded its victim list by adding 183 more organizations as part of the Cleo hacks. In their latest update on the data leak site, the cybercriminal group claims these companies were notified but chose not to engage in ransom negotiations.
The newly added companies span various industries, including notable names like HomeDepot.com.mx, Rackspace.com, Paige.com, and TotalWine.com, across sectors such as retail, logistics, technology, and food distribution. Organizations claimed to be affected should prioritize improving their cybersecurity defenses and take immediate steps to prevent further damage from these attacks.
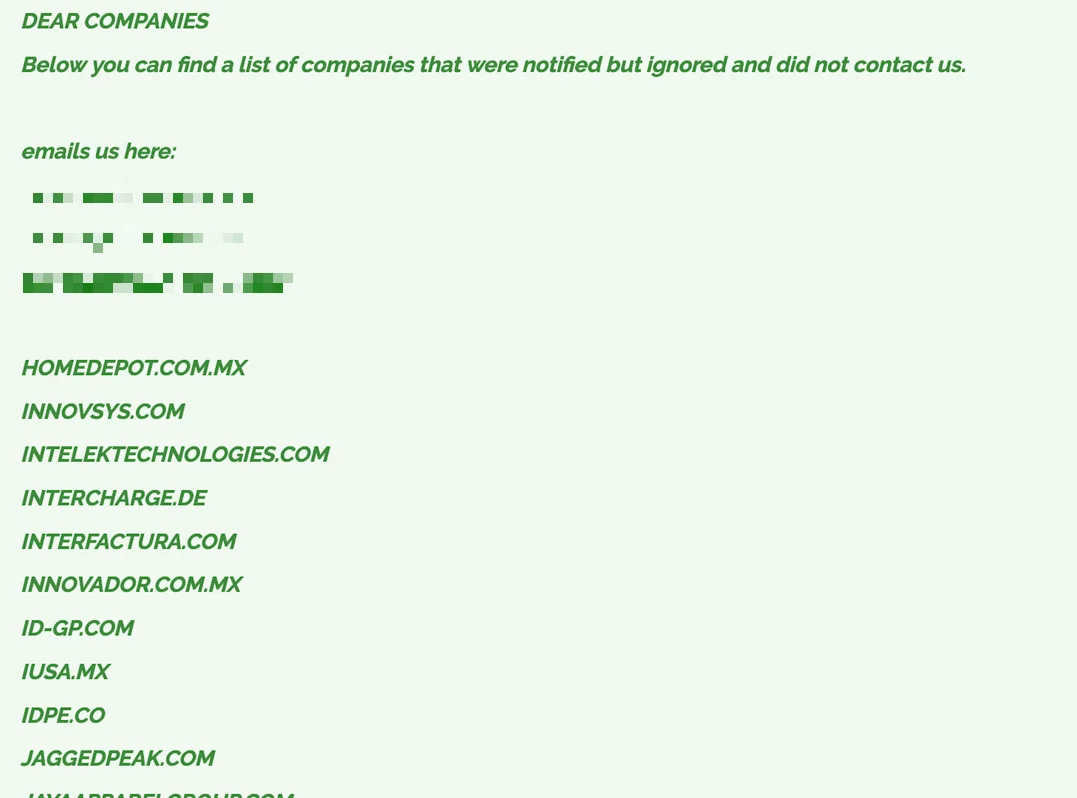
The latest post by the ransomware group
WK Kellogg Confirms Data Breach Tied to Cleo Exploits
WK Kellogg Co has confirmed it was impacted by the 2024 Cleo software breach. In a recent disclosure, the company said an unauthorized party accessed Cleo-hosted servers, exposing personal data.
While WK Kellogg did not name the threat actor, the incident coincides with the Clop ransomware group’s mass exploitation of Cleo vulnerabilities (CVE-2024-50623 and CVE-2024-55956). The timing and a recent listing on Clop’s leak site suggest a likely connection.
The breach notification shared with authorities notes that one individual’s name and Social Security number (SSN) were exposed. In response, the company is offering free identity monitoring through Kroll and is advising impacted parties to consider fraud alerts or credit freezes.
What Can You Do to Protect Your Systems?
To protect your systems from the ongoing exploitation, it’s critical to take immediate action. Here are the key steps to secure your environment:
- Apply Patch Updates
The most important step is to update your Cleo products to version 5.8.0.24, which includes fixes for both vulnerabilities. Ensuring that your systems are running the latest software versions is essential to prevent attackers from exploiting these flaws. - Disable the Autorun Feature
Another critical measure is to disable the Autorun directory feature. This will prevent attackers from executing arbitrary commands when files are uploaded, significantly reducing the attack surface. If an immediate update is not possible, this step can help minimize the risk while waiting for patches. - Improve Firewall and Network Security
It’s also recommended to remove Cleo servers from the public internet and ensure they are protected by firewalls. Limiting external exposure of your servers will significantly reduce the chances of attackers gaining unauthorized access.
By promptly applying patches, disabling risky features, and securing network access, organizations can minimize the impact of these vulnerabilities and strengthen their defenses against future attacks. For more detailed guidance on mitigating these vulnerabilities, Cleo has provided advisories (1, 2) on its support site.
Every organization has a digital footprint that expands across the internet, often unknowingly exposing critical assets to potential threats. SOCRadar’s Attack Surface Management (ASM) module helps you identify, assess, and mitigate risks associated with your digital assets, ensuring that your organization stays protected from emerging threats.
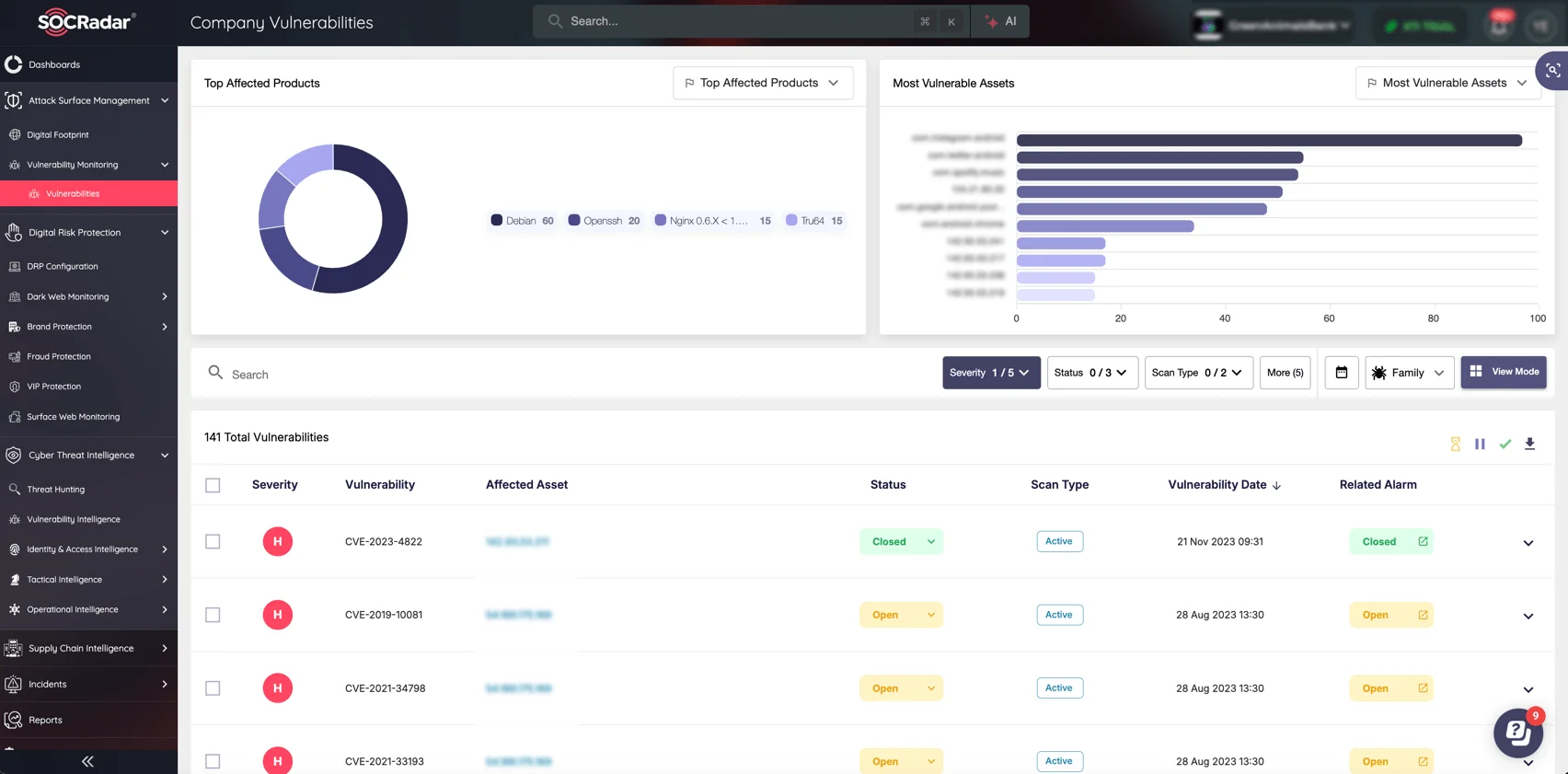
SOCRadar’s ASM continuously monitors the entire attack surface, providing you with real-time visibility into exposed assets, vulnerabilities, and unauthorized access points.
Take control of your organization’s digital presence and secure your assets before attackers can exploit them. With SOCRadar’s Attack Surface Management, you can confidently protect your infrastructure and maintain a strong security posture.
Indicators of Compromise (IOCs) and Post-Exploitation Observations
To help organizations detect ongoing exploitation and monitor for suspicious activity, here are key Indicators of Compromise (IOCs) based on research findings:
Attacker IP Addresses embedded in encoded PowerShell scripts:
- 176.123.5.126
- 5.149.249.226
- 185.181.230.103
- 209.127.12.38
- 181.214.147.164
- 192.119.99.42
Malicious Files:
- 60282967-dc91-40ef-a34c-38e992509c2c.xml: A standard XML file used for post-exploitation preparations.
- healthchecktemplate.txt or healthcheck.txt: Malicious files that are typically used in post-exploitation activity to gather information from compromised systems.
- Malicious autorun files: Files that exploit the Autorun feature to enable unauthorized command execution.
Monitoring for these IOCs is critical in identifying potential exploitation attempts and post-exploitation activities, allowing organizations to take swift action and mitigate further damage.


































